 Education
Education
Port Forwarding with WSL2
have you ever wanted to port forward from a Windows Host to a WSl2 KALI VM when you are using a NAT’d virtual switch configuraiton with WSL2?
Read more “Port Forwarding with WSL2” Education
Education
have you ever wanted to port forward from a Windows Host to a WSl2 KALI VM when you are using a NAT’d virtual switch configuraiton with WSL2?
Read more “Port Forwarding with WSL2” → Guides
Guides
Penetration testing, adversary simulation, red teaming, purple teaming, rainbow teaming, call if what you like, the security outcome we are working towards is:
This is to support the organisations mission, vision, goals, and objectives. Cyber security is to support and enable the organisation’s capability to execute digital services in a safe manner.
Read more “Practical Security Assurance” → Guides
Guides
Have you ever wanted to run a quick test of egress ports from userland from a windows machine?
Well worry not, I didn’t even have to write anything, the nice people at Black Hills security have done it for us. However I did decide that there’s a few other things we might want to do, so I made a quick modification, now we have colours, randomisation and some sleeps.
Read more “Testing Risky Egress Ports” →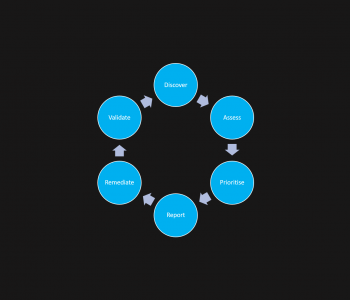 Defense
Defense
Someone tells you they have fixed something, now go and check! You might find that it is not actually fixed, or that the ‘fix’ made the issue worse (or makes new vulnerabilities appear). You might however also find that the vuln is gone.
Wow so many options, but the reality is with this space is that you have to keep checking, you also need to validate.
Validation is key, people do not say that think it is fixed because they have not done something, we all have scenarios where we make a change, assume it works and then find out later that maybe a bit more testing would have helped (I have this too!). Read more “Vulnerability Management Realities” →