 Defense
Defense
Hafnium / Exchange Marauder High Level IR Help
Ok so John and I have been working on this for a while. We have been working with both customers and industry profesionals and there’s a common theme. Understranding the events from this incident are quite challenging because:
- We don’t have sample log output for known bad traffic
- The vulns can be used for data theft and/or backdoors (and further actions on target)
Getting guidance out so far on this has been challenging becuase:
- There is not a public full kill chain POC to do comaprisons to (i’m ok with that)
- We don’t have a pw3d server that has all the indicators from all the routes on
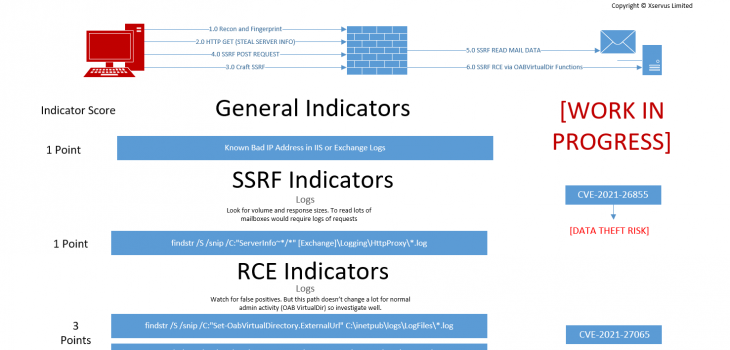
So to try and help people we have made a diagram which we will update as we go.
Essentially you need to perform a weighted analysis to understand if:
- You had recon only
- You had some SSRF
- YOu had SSRF that led to data theft
- You had a webshell planted