 Vulnerabilities
Vulnerabilities
Exchange Emergency Mitigation (EM) service
Yesterday I created a honeypot running Exchange 2019 in the lab. I configured very little and setup a test rule as per the MS blog to stop the SSRF from the “Autodiscover” endpoint to the Powershell function call. I put a custom response with some humour (coz why not!) but I disabled the rule:
This rule was placed in the Autodiscover virtual directory which in Exchange by default is here:
C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\autodiscover\web.config
My custom rule:
Read more: Exchange Emergency Mitigation (EM) service|
<rewrite> <rules> <rule name=”RequestBlockingRule1″ enabled=”false” patternSyntax=”Wildcard” stopProcessing=”true”> <match url=”*” /> <conditions> <add input=”{REQUEST_URI}” pattern=”.*autodiscover\.json.*\@.*Powershell.*” /> </conditions> <action type=”CustomResponse” statusCode=”403″ statusReason=”No Hacks for You” statusDescription=”Say no to exploits!” /> </rule> </rules> </rewrite> |
This morning I checked the Honeypot, and I found the following:
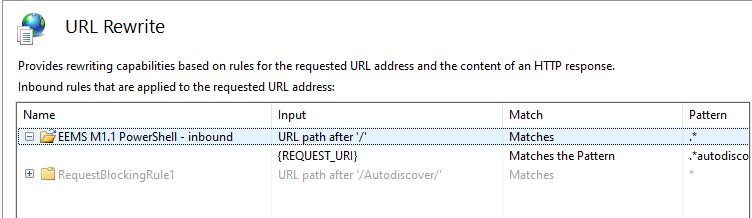
This rule is hosted in:
C:\inetpub\wwwroot\web.config
|
<rewrite> <rules> <rule name=”EEMS M1.1 PowerShell – inbound” stopProcessing=”true”> <match url=”.*” /> <conditions> <add input=”{REQUEST_URI}” pattern=”.*autodiscover\.json.*\@.*Powershell.*” /> </conditions> <action type=”AbortRequest” /> </rule> </rules> </rewrite> |
As you can see this was modified at 03:21 01/10/2022
This comes from:
Exchange Emergency Mitigation Service (Exchange EM Service) | Microsoft Learn
“Exchange Emergency Mitigation (EM) service”
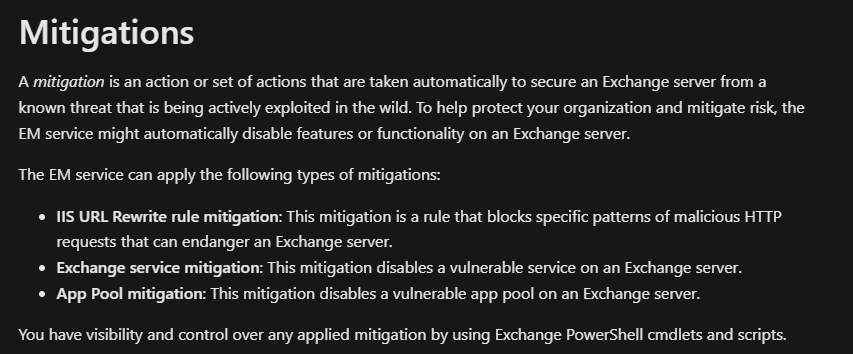
You can check if this is enabled by running the following PowerShell:
Add-PSSnapin Microsoft.Exchange.Management.PowerShell.SnapIn;
Get-OrganizationConfig | Select-Object MitigationsEnabled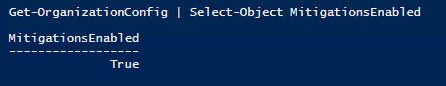
So here we can see that with this enabled, the Exchange server will download and deploy the HTTP re-write rules automatically (if the server has the required version/config etc.)
You can enable or disable it with the following:
Set-OrganizationConfig -MitigationsEnabled $true
Set-OrganizationConfig -MitigationsEnabled $falseYou can check this feature works using the following (modify path as required for relevent exchange version)
. "C:\Program Files\Microsoft\Exchange Server\V15\Scripts\Test-MitigationServiceConnectivity.ps1"
Check the MS docs and check your Exchange Server version to see if you have this feature etc.
GCM exsetup |%{$_.Fileversioninfo}You learn something new everyday!