Understanding your business from a new perspective
In today’s modern digital and mobility enabled world there are great opportunities for business through digital channels, partnerships to deliver new and engaging customer experiences. This digital world however has created a range of challenges from a technology management and cyber security perspective.
We see two major areas of challenge modern businesses face:
- Technology and Mobility Management
- Current and evolving cyber threats
Technology Management
Whilst the idea of technology deployment to increase efficiency and to enable businesses to operate across boarding and at scale brings a great many advantages, it also brings with it a range of challenges, such as:
- Technology Sprawl
- Increasing demand for a greater range of digital enabled services
- Managing a mobile workforce
- Data privacy and protection challenges
- Complexity and scale
- Legacy Modernisation
- The requirement for a digital enabled and skilled workforce
Technology management is a challenge for a range of businesses. Tacking what we call “technical debt” whilst balancing business demands for new services, combined with the fast pace of technology creates a scenario where a range of businesses are struggling to keep up. This is without considering how the expanding deployments of technology and mobility change the business risk profile.
Cyber Threat Landscape
Along with the explosion of technology in businesses, people’s personal lives are transformed. Almost every modern life experience involves a direct in near linkage to technology. From getting a bus ride to ordering the groceries through to global video conferences with company boards and investors, technology is everywhere.
As has always been there are also modern threats, whilst once crime was focused on the physical world, the modern cybercriminal world allows cross border, global reach for criminal organisations to conduct operations such as:
- Ransomware
- Business Email Compromise
- Fraud
- Scams
- Identify Theft
- Corporate Espionage
- IP Theft
The global cybercrime market is booming, with attacks on people and organisations skyrocketing over the last decade. Organisations now face a battle on two fronts, how to enable the business in a digital world, but also how to keep their systems, staff and customers safe.
Modern Day Business Demands
When looking at organisational challenges today organisations are now understanding the kind of questions the board need to be focusing on, these are now including a significant focus on cyber security risks and ensuring their businesses have the capabilities, tools, people and processes in place to identify, protect, detect respond and recover from a broad spectrum of both technology incidents and cyber risks.
Common Challenges
We work with a range of organisations and generally speaking there’s often a unique perspective that each organisation has when it comes to understanding their cyber risk portfolio. We do however see common themes which we’ve taken a selection from:
- Are we suitable prepared to respond and recover from a significant ransomware incident?
- How do we ensure that our brand is protected from the impact of a major cyber incident?
- We know we’ve invested, and we think we are ok, but what aren’t we seeing, what’s there that might impact us? (the unknown knowns/unknowns)
- We know we have gaps, but we’ve been unable to secure resources to tackle these. How do we make a good business case and get the buy in we need?
- We are ISO27001 accredited but we want to know if we really stand up when it comes to how effective our controls are.
- We’ve recently recovered from a major cyber incident; we want to make sure we are suitable protected and have the right detection capabilities to prevent both a recurrence but also protect against the range of common cyber threats. How do we understand our position and where do we need to focus our efforts?
We work during the sales process to gain a high-level understanding of your specific requirements, challenges and business objectives. As such we’ve designed our security posture assessment service to help organisation understand their current state posture, identify areas of strength, weakness and develop a roadmap to enable them to enable a digital defence strategy that:
- Is aligned with their business
- Supports their existing investments
- Enables and expands their team’s knowledge and capabilities
- Enabled and supports compliance objectives
- Promotes good practises
- Reduces business risk and exposures
The key here is that whilst we take an independent view, we truly believe that strong security posture come from within. Good practises security is driven by an enabled, informed, and capable team.
Our Approach
Our approach to consulting services is based on a tried and tested approach. We leverage a project deliver framework that focuses on:
- Enabling a formal project capability to manage the consulting engagement
- Giving the project team insight and understanding of your organisation
- Conducts a range of activities to:
- Understand the business landscape
- Understand your people
- Understand your processes
- Gain a view on your cyber security capability maturity
- Take deep views on technology services and solutions
- Develops a tailored service to take both a broad and deep view to identify:
- Tactical Actions
- Strategic Initiatives
- Provides actional insights, findings, and recommendations to maximise impact, reduce time to value and help close down short- and long-term vulnerabilities.
- Provides a strategic plan for a security improvement programme
- Develops long lasting principles which support your business
We achieve this through a range of project activities including:
- Evidence Collection
- Interviews
- Maturity Assessments
- Technical Assessments
- Deep dive views across a broad range of your technology landscape
- Real world cyber simulation activity
- Hands on knowledge sharing with your teams
- Workshops and Meetings
The PwnDefend Cyber Assessment Framework
Based on leading good practises, we’ve developed an in-house toolset to review organisations cyber security maturity capabilities. The cyber assessment framework has its roots in traditional maturity assessments; however, we’ve made what we feel is a good balance between breadth and depth.
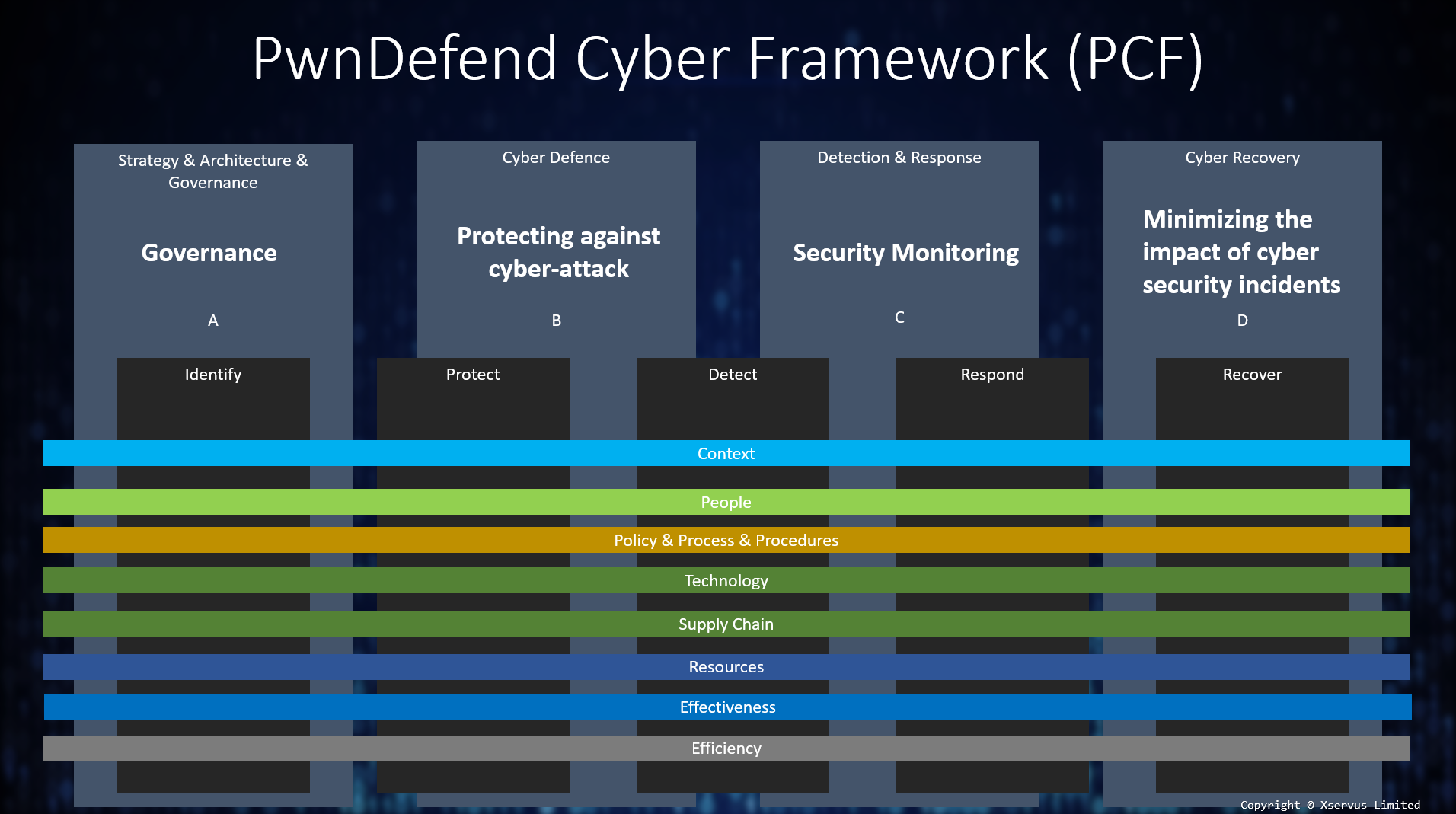
Technical Audits and Activates
To gain a deep understanding of your environment we leverage a range of activities which includes:
- Network, Asset and Service Discovery
- Risk Assessments
- Data Flow Modelling
- Crown Jewel and Sensitive Data Analysis
- Vulnerability Assessments
- Configuration and Control Audits
- Offensive Security Practises
- Purple team simulations
- Incident Response Workshops
- Backup and Recovery Reviews
Solutions you know and trust
To conduct the technical assessments, we use both in house developed toolsets alongside industry leading products and services such as:
- Nessus
- Pingcastle
- Burp Suite
- Kali Linux
- Azure Service Map
- Map Toolkit
- Bloodhound
- Maltego
- Shodan
- Greynoise
- RiskIQ
- Infection Monkey
- GoPhish
- Open-Source Software and Toolsets
Aligning with Good Practise Guidance and Frameworks
Whilst we use some of our bespoke, experienced based on developed IP, we build upon solid foundations leveraging industry good practise standards, guidance and frameworks including:
- ITIL
- ISO27001:2013
- NCSC Guidance & NCSC CAF
- NIST
- CMMC
- CREST
- TOGAF
If your organisation has existing framework investments, we tailor the service to suit your environment and align to ensure a common reference is used.
Bringing it all together
During the discovery and assessment phases we gather data from a range of viewpoints to enable us to create a heatmap of your current state. We work with your leadership and operational teams to analyse your strengths and weaknesses, then we develop a prioritised business aligned future state roadmap.
One our primary objectives with this service, is to not only provide a report with insights, findings, and recommendations, but to also enable knowledge sharing, solution innovation but also to support the development of your business capabilities and people to support your efforts to have a robust, resilient, and capable cyber security capability.
To complete the engagement, we deliver a debriefing with the team to enable collaboration and to ensure the team are aligned, the initiatives understood, and the future activates supported both by the leadership team and hands on people. The best cyber defence comes from within, your people enable your business, your people are the key to enabling cyber security.
Customer Feedback
“Engaging the PwnDefend team not only improved out understanding, our security posture was visibly enhanced but also we enabled our business to reduce compliance and assurance complexity” – SaaS Product Director
“You opened our eyes to the security vulnerabilities we weren’t even aware of, better still you helped us come up with a plan for rapid and contextualised remedial activities” – CIO
“Fantastic job, you uncovered things past assessments didn’t even consider investigating” – SIRO
Next Steps
If you’re looking to understand your current security posture, develop a security improvement roadmap, identify gaps in your defences or simply validate your position and cyber risk profile, please contact the sales team and we will be glad to support your business.