


Human Interface Devices is the science way of saying (in this case) keyboard! Now that doesn’t sound amazing but then we look at the details. What we are talking about here is a wireless remote controlled programable keyboard emulator disguised as a USB cable or a cable between a real USB keyboard (must be detachable). This provides attack opportunities to both key log and hijack inputs to PC devices covertly and remotely (within WIFI range). Just imagine what you could do with one of these.
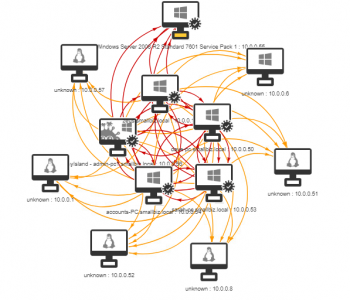
Have you ever wanted to see what would occur in an environment if a worm was a make its way in? I often work with customers to show them about lateral movement from a human operated perspective however sometimes it’s useful for people to visualise this better and to demonstrate what could occur if a worm was set loose. A great tool to help with this is Infection Monkey from Guardicore (https://www.guardicore.com/
The process steps are as follows:

I do not know Mr Martin, but I would assume that his role at NCSC and GCHQ would have given him a good insight into the realities of cybercrime, cyber terrorism, nation state affairs and how to effectively defend against cyber criminals (and other threat actors) so please read this blog as it is intended, it’s an analysis on the quoted statements and reporting style and general view of mine about current cyber war rhetoric, not an analysis of the person. Why am I writing this? Well, I am seeing an increased level of FUD, snake oil and cyber war rhetoric and I wanted to share some of my thoughts, opinions, and ideas in this space. For it is far too easy to call for war and in cyberspace do we even know what that means? Read more “Combating Cyber Crime: Should we really be charging to cyber war?” →

For years you might have heard to have a complex password you change regularly (like every 30 days to keep you safe from the hax0rs) but well… let us not lie, it is bloody terrible advice.
Password cracking, brute force attacks, credential stuffing and well mad human things like writing passwords down on post it notes under keyboards are hugely prevalent still. The other day I managed to see a password used on a corporate system which was “Thursday49”. Yep, I know I know we all know that a weak easily guessable, easily crack able password is not a good idea yet honestly, humans like things that work and are simple vs remember their 6 favourite books in reverse order with a complex character and capital letter. Read more “Password Managers – The Good the Bad and the Ugly” →

At the heart of most organisations are a Windows server active directory domain (or multiple of these), yet one of the most common findings when we review organisations security postures are there are significant weaknesses in their active directory deployments, both from an architectural, operational and security perspectives.
Active directory provides a range of functionality to organisations, from authentication, authorisation as well as supporting services such as printer and share listing, DNS, people/information lookups and integration for 3rd party services. It’s the very hub that links most modern networked systems together and now it’s expanded beyond the corporate walls into the cloud with integration into Azure Directory Services as part of Azure or Office 365.
Essentially Active Directory can be considered a castle whereby crown jewels are held! This may be in the form of credentials/identity or by nature of granting access to business systems that hold sensitive data (such as using AD integration to log into an HR or Finance system). Read more “Active Directory Security: Securing the crown jewels with PingCastle 2.8.0.0” →

In this latest room (box) we take on Skynet! This box has a cool theme and was fun to play through.
https://tryhackme.com/room/skynet
This room starts to move away from the guided path and has far fewer flags, but it retains more than just a two-task approach to keep the person thinking about the types of vulnerability. I’m thinking it might be cool to ask defensive questions as well (something I might add into my room I’m building).
Well we don’t have time to waste, the machines might rise up and judgement day occur so let’s get pwning! Read more “Try Hack Me – Part 6: Rise of the Machines” →

Today we look at a vulnerable web application room based upon the Hitman series!
https://tryhackme.com/room/gamezone
This is a fun room where we see an old but common vulnerability in untrusted user input lead to sensitive information disclosure (hashed credentials) which results in a threat actor gaining initial access. From here we then discover there is a weak security configuration (in effective network segmentation) and a vulnerable unpatched service. This chain leads to total system compromise. Read more “Try Hack Me: Part 5 – Game Zone” →


Welcome back everyone! Today we are posting a walkthrough of the ALFRED room on TryHackThis!
https://tryhackme.com/room/alfred
This is a fun room; it’s got real world technology deployed and the paths are exactly what you might find IRL! Attacking commonly deployed enterprise products is something that I really enjoy seeing on a learning platform and CTF as I think this equips people for realistic scenarios both from an offensive and defensive perspective! Right, so let’s hop to it! “Alfred I need a laptop and some tea!” Read more “Try Hack Me part 4: Alfred” →

Off the back of running the BSIDES Leeds CTF, I’m back in the lab trying to work out my arrangements for work and trying to recover from the con and I stumbled across this on twitter: Read more “Reviewing ‘Try Hack Me’ – Part 1 – A New Hacky Adventure by mRr3b00t” →