
Cracking an SSH key with John the Ripper (JTR)
This is a super-fast blog to show how to crack sshkeys with JohnTheRipper from Kali VM.
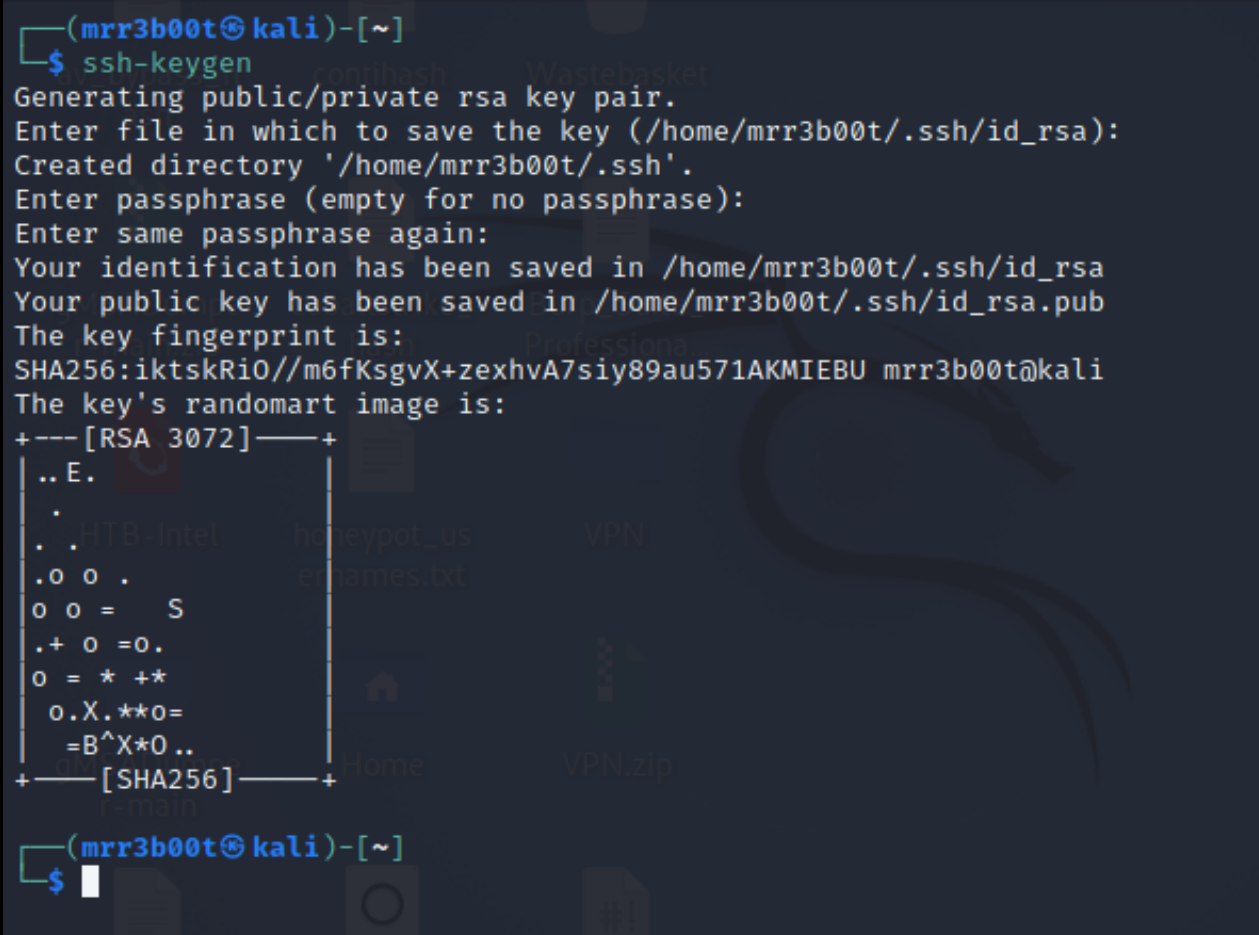
Create a key
ssh-keygen Read more “Cracking an SSH key with John the Ripper (JTR)”

This is a super-fast blog to show how to crack sshkeys with JohnTheRipper from Kali VM.

Create a key
ssh-keygen Read more “Cracking an SSH key with John the Ripper (JTR)” →

Ever wanted to run honeypots all over the world but don’t want to deploy actual servers, or psudo servers everywhere? Ever wanted to run a C2 server but don’t want to expose your own IP and want a pool of redirectors? Well here’s a quick look at using SOCAT to forward HTTPS traffic from a VPS to a backend web server.
Create a linux virtual machine in a cloud services provider: Read more “Redirecting Traffic with SOCAT” →
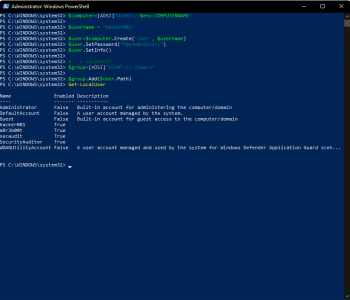
Are you like me and always end up searching for easy stuff that you know but you just can’t remember the syntax all the time?
Well don’t worry I’ve got your back
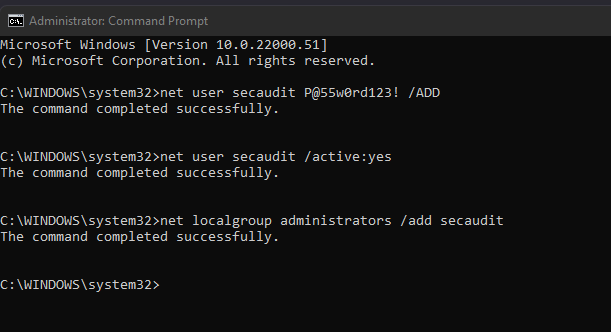 Read more “Windows admin 101 – Adding a local administrator account from the command line” →
Read more “Windows admin 101 – Adding a local administrator account from the command line” →
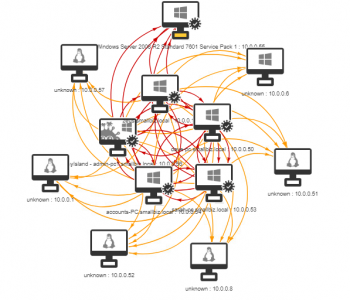
Have you ever wanted to see what would occur in an environment if a worm was a make its way in? I often work with customers to show them about lateral movement from a human operated perspective however sometimes it’s useful for people to visualise this better and to demonstrate what could occur if a worm was set loose. A great tool to help with this is Infection Monkey from Guardicore (https://www.guardicore.com/
The process steps are as follows:
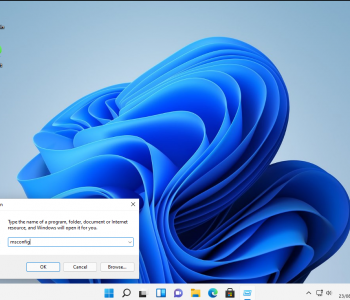
Ok these are a really simple UAC bypass from a userland GUI perspective. This is about increasing process integrity levels – it’s not about performing LPE from low integrity to high/SYSTEM with no interaction. These clearly work in older version of Windows as well but since Windows 11 will be the current version in the near future I thought it was fun to re-visit these!
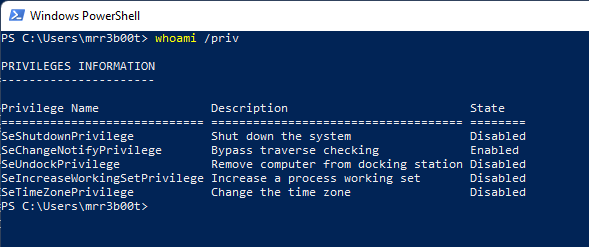
And just to be clear, a medium integrity process as an administrator user will have the following privileges:
What we are talking about here is to move to a high integrity process without knowing credentials or having the secure desktop launch. Read more “Windows 11 Privilege Escalation via UAC Bypass (GUI based)” →
“And I looked and behold a pale horse: and his name that sat on him was Death, and Hell followed with him.”
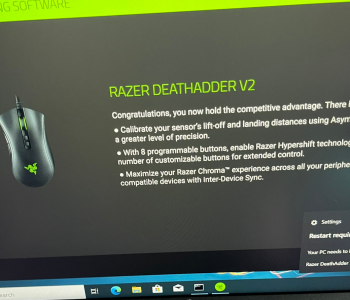
Firstly, Kudos to @j0nh4t for finding this!
I woke up this morning to see twitter fun with a LPE discovered in the Razer driver installation. Basically, when you plug a Razer mouse into a Windows machine, it will download (via windows update) and execute a process as system which has user interaction. This interface includes an install path selector, with this a right click + SHIFT (LULZ) on whitespace will allow you to launch a command prompt/PowerShell window (as SYSTEM).


Ever needed to test active directory in a hurry? Well, here’s some common commands to test active directory domain services. In this post today we are going to focus on DNS and username enumeration, there are however a range of weaknesses you want to look for:
Port Scanning and Service Fingerprinting
nmap -p- -sC -sV -Pn -v -A -oA ecorp.local.txt 192.168.1.22
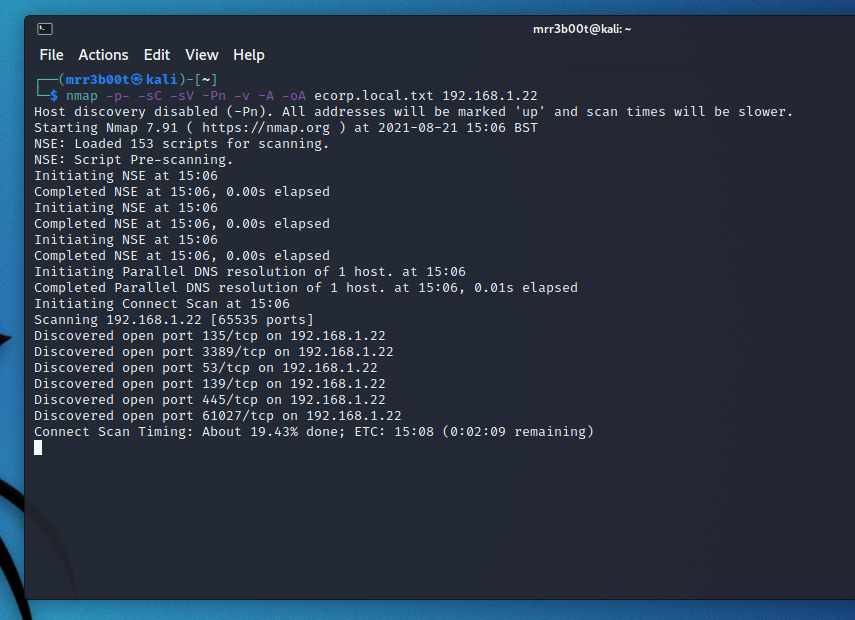
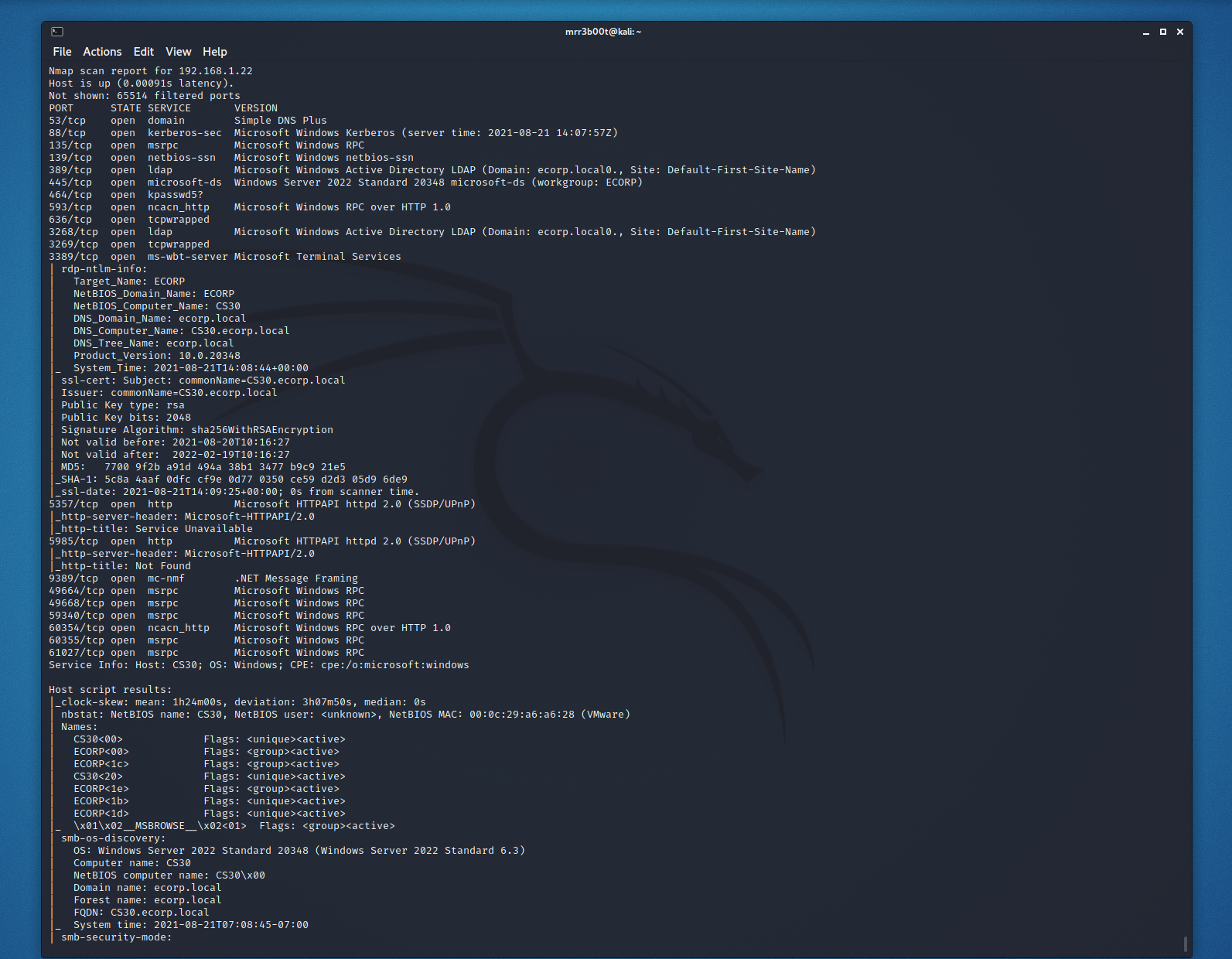
Read more “Rapid Active Directory Security Testing of Windows Server 2022 and Kali Linux” →

WIndows Server 2022 is RTM! I love new operating systems, but also with the new, what is old? There will be loads of new blogs and articles on new features of Server 2022 however I wanted to see what mischief we can have with it! So I’ve decided to start looking at common vectors and exploits (from the fun to the serious) so that we can see how much of the world has changed (or not!)
So let’s take a look. The first thing I did was to offline replace stickykeys with cmd.exe – yes this method still works. But as lots of people will realise, you neeed physical access to the disk (well you don’t if you have access to someone’s vcenter you don’t!) but also the reg key methods also work! We can still backdoor RDP – here’s a script to disable NLA, Enable RDP, configure the firewall rules and set the registry keys to backdoor the system (clearly for lab use only!)
https://github.com/mr-r3b00t/RDP_Backdoor
Read more “Hacking Windows Server 2022” →
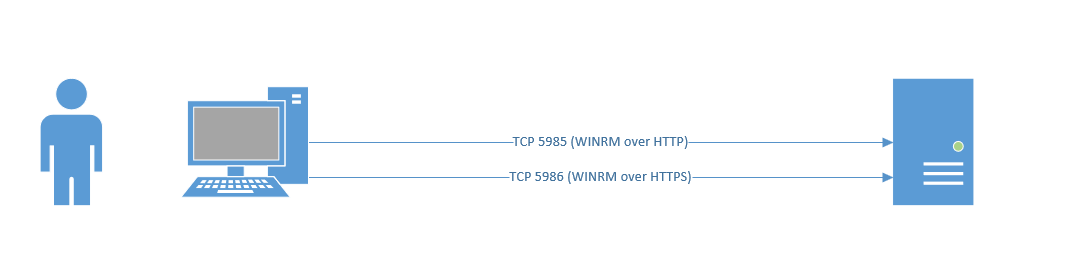
Windows Remote Management is easy if you are using a domain joined machine and have a CA. But what if you are off the domain and you want to connect to WINRM that has an HTTPS listener? (by default WINRM uses HTTP on TCP 5985, you can clearly chop out the TLS related configs in the example scripts and they will work for plain old WINRM)
This is useful from a sysadmin and penetration testing/red team perspective. Now obviously you could export the certificates and import them into your store, however that’s more work. So, let’s look at how we ignore revocation, CA name and Computer Name checks.

Recently I decided to do the Red Team Operator: Privilege Escalation in Windows Course by Sektor7 (thanks for the recommendation Justin!). I thought I’d write some notes but also create a quick blog covering some of the Windows fundamental areas. It’s easy to actually forget how this stuff is at a detailed level so figured it helps both myself and the world to share a snippet. I’m litterally listening to the course as I type this, I’ve just imported an OVA to vmware workstation so this is litterally live! (I’m 7 video modules in!)
There’s some key parts around Windows Security Architecture that is important to know, the course does cover this off at the start so I thought I’d share a tiny bit of my notes. Read more “Windows Security Fundamentals & LPE” →