 Leadership
Leadership
Introduction
I’ve been around a bit now, I started ‘playing’ with technology very young as a kid! Wolf 3D/Doom era etc (ok even before that but whatever) …
In my professional career I’ve worked with literally hundreds of companies, from mega to small, from household names that sell games consoles through to orgs that sell you yummy food! I’ve worked across loads of industries from government through to manufacturing. I’ve dealt with major incidents for the finance sector, healthcare but also, I’ve been inside a range of networks for some time.
So hopefully what I’m about to say now will make sense! Did you want to hear about the most common incidents I’ve seen over my travels? Scary APTs and spy chases? Get out of here! This is going to be far duller! This is going to walk you through the typical things I see!
Common Events that I see turn into incidents
These are in order of prevalence in my world! Yours may differ!
Phishing
247 365 phishing and spam is hitting everyone. It’s the most common alert I see anywhere other than in honeypots and web servers. Phishing is a headache, especially when organisations don’t have MFA, EDR and any of the other generally mandatory controls for a modern organisation (in 2024)
Business Email Compromise
You know when someone makes a payment based on a payment details change from a ‘trusted’ email address? Business Email compromise and supply chain compromises occur on a really frequent basis!
Authentication Attacks
So yes, if you have a service exposed to the internet it is probably getting bad packets send to it 247 365 days a year. Sometimes these are successful!
Emails/Documents sent/shared with the wrong people
God this is not very interesting is it, but it happens all the time! This one is hard to prevent, humans make mistakes!
Sharing Passwords
We tell everyone not to, but I often find people sharing credentials
Insecure Credential Storage
Again, everyone knows they shouldn’t, but they still often do it!
HVAC/Environment Issues
Server rooms overheating and power issue (and sometimes water in the DC/Server room) – if something can go wrong it probably will! And a UPS doesn’t always save the day!
Damaged/Destroyed Laptops/Mobiles
Honestly, I’ve done this myself more than once! Humans love to drop laptops or throw fizzy or hot drinks over them!
Lost/Stolen Laptops
Laptops go walking! Typically, I’ve seen more losses than thefts!
Lost/Stolen Mobile Devices
These I see both get stolen and go walk about
Unauthorised/Unacceptable Computer Usage
The HR department get called, proxy/network access/device logs are requested etc. This covers staff watching content such as pornography through to workplace bullying and intellectual property theft
Accidental Data Deletion
Someone accidently deletes data and needs it restored from a backup I know very 1337 this one!
Unpatched Vulnerable Exposed Interface
A number of times I’ve seed edge/exposed devices/services exploited during zero day and mass exploitation attacks. Usually, it’s because the organisation hasn’t patched fast enough, but sometimes the criminals have got hold of a zero day and got in before the vendor even knows about it!
Malware
Now this gets complicated because most malware I see if blocked either by email security or by device protections. Sometimes however something does get through.
Shadow IT/Unauthorised Cloud Services Usage
This one, is difficult. Sometimes staff/management etc decide without discussing with anyone to go and start putting data into unauthorised systems! This varies loads, but often you can find someone has unknowing broken a contractual requirement with a downstream customer/supplier etc. so incidents occur!
Seriously, that does not sound very fun! Where’s the Hollywood style hacks?
Ok so now let’s talk about the less common incidents, way less frequent on a per organisation basis I’ve seen (in no particular order)
- Ransomware
- Nation State Actors/IP Theft
- Breach and Leak
- Mass Exploitation Events
- DDoS/Denial Of Service Attacks (these are relatively common when considering a country or world)
- Missing Authentication (e.g. open buckets)
- Malicious Insider Threat (Data theft)
- Contractors plugging in HUBS/Routers and causing DoS
- Infected Laptops being plugged into corporate networks
- Rarely I see malware on a USB device (it’s always been some crappy keygen/PUP or some torrent related thing vs mad hacks!)
What I have never seen a real-life criminal do!
- USB Keys left in car parks for random people to pick up
- Laptops hacked on trains
- Public Wifi use leading to anything other than an expense claim!
- Juice Jacking!
- Public Charger Interference
- Wifi hacking from the company car park!
- Incidents caused by weak TLS (other than a PCI non compliance finding!)
- Incidents caused by a lack of DNSSEC
Some of these are more possible/achievable than others! Juice jacking, I mean god, it sounds awfully fun and exciting but it affects android devices from pre-2016 or something and it was patched immediately and there are no known public instance of this. In the industry we laugh when people mention this. But I have broken into orgs from car parks during pentesting so just because I haven’t seen that outside of a pentest doesn’t mean it can’t happen. Targeting an organisations campus/site WIFI is much simpler (I have found) than say someone’s home! (at least in recent years!)
Summary
Hopefully this is useful for CIO/CISOs/CTOs/IT Managers etc. It’s the total opposite of most organisations marketing hype, but these are the common types of incidents I see in organisations over longer time periods (e.g. not just doing IR with people).
I did some work on this previously in a blog (wow that’s a few years ago now!)
I also have published a number of time the PwnDefend Cyber Probability Yardstick! (which people might find useful! it’s an example you have to still do some work I’m afraid!)
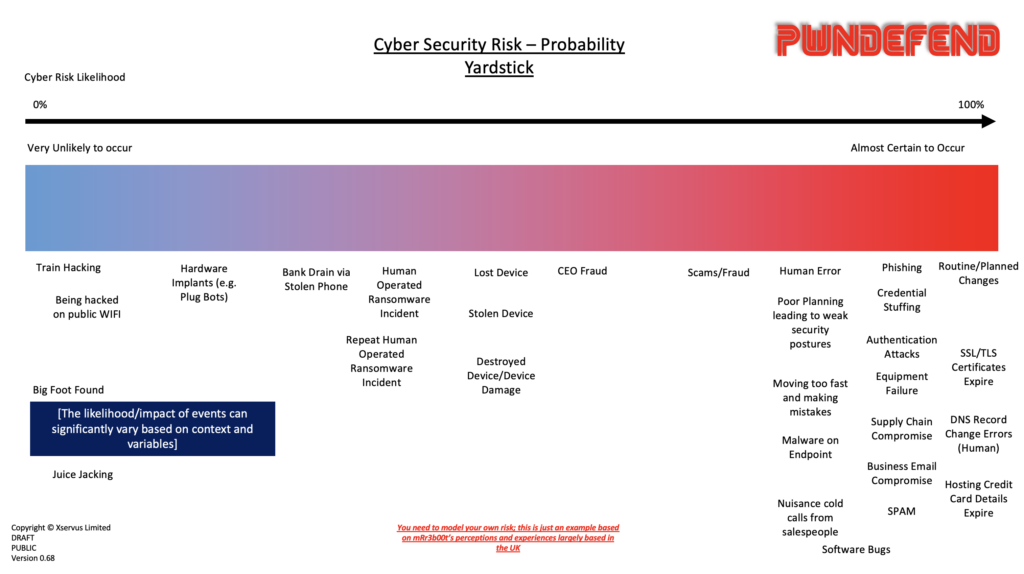
The aim of this blog was to show people what I have seen, this isn’t very exciting I know (I have worked on some very exciting incidents for sure and found some way bad stuff during penetration testing etc.) but this is what I see in reasonably well managed environments (vs totally unmanaged ones).
Your major incidents stories will make this blog seem boring as hell, and well, so they should! The reason I’m showing this is to try and give people an idea of the common things I see vs the exceptional things! You will of course need to develop your own risk appetite/tolerance statements, threat models, risk models which are relevant and contextual to your organisations. However hopefully this gives some food for thought with regard to how you may wish to prioritise (that being said 100% prioritise ransomware defence, by doing so you will cover off not only that but a vast array of other threats!).
You will notice I haven’t gone into countermeasures/controls! That my friends is for another day, but if you start with Cyber Essentials and making sure you have ‘safe’ backups you will be making a great start!









