 Threat Intel
Threat Intel
Update 30-10-2023 (fast publish)
This is a fast publish. Based on honeypot data from @SI_FalconTeam we can make some analysis:
- The webshell has an authorisation header is 40 characters long. (it is unknown how this was generated)
- The user agent in the sample: User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3729.169 Safari/537.36
- The source IP: 192.3.101.11
- The stages:
- Check for webshell
- If not in place:
- Bypass Authentication (CVE-2023-20198
- Create a local LEVEL 15 User AccountSet IP HTTP/HTTPS SERVER and Enable Local Authentication (AAA)Use this account to conduct a device inventory.
- Inventory the System
- Kill the created Level 15 account
In the lab we have attacked HTTP and HTTPS and have been able to get AUTH bypass. (thanks @leak_ix)
Inventory Example
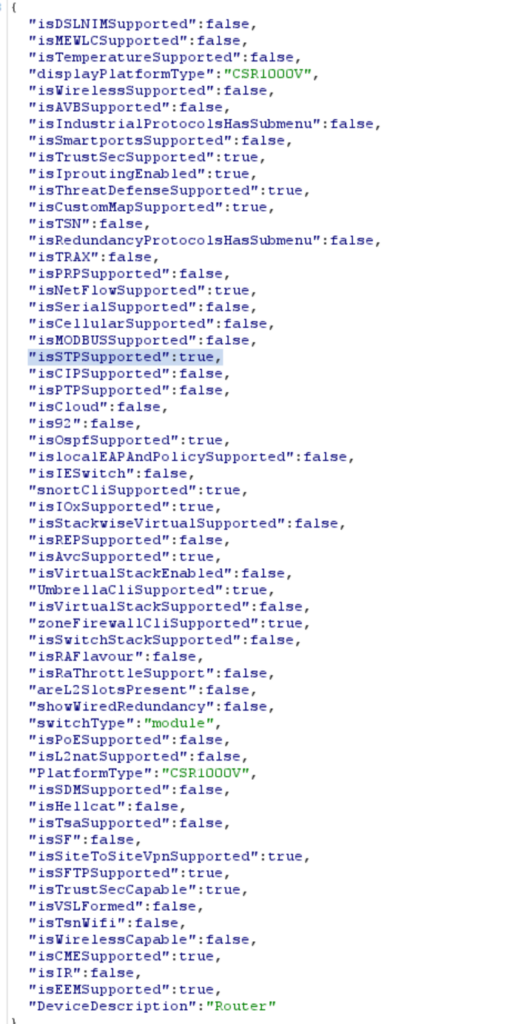
Resources
https://github.com/fox-it/cisco-ios-xe-implant-detection
IP Analysis
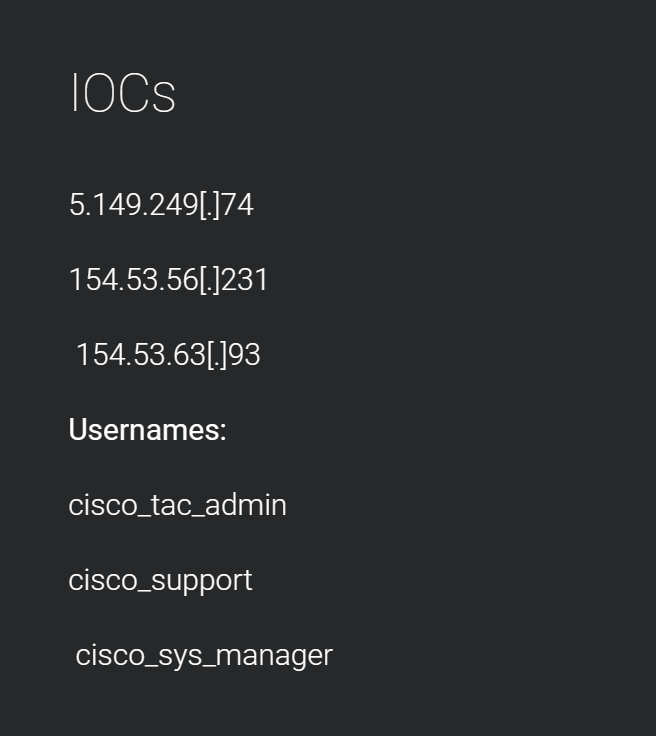
The IP has been taken from a live exploitation. We should also note the following IOCs from CISCO:
https://viz.greynoise.io/ip/192.3.101.11
Shodan
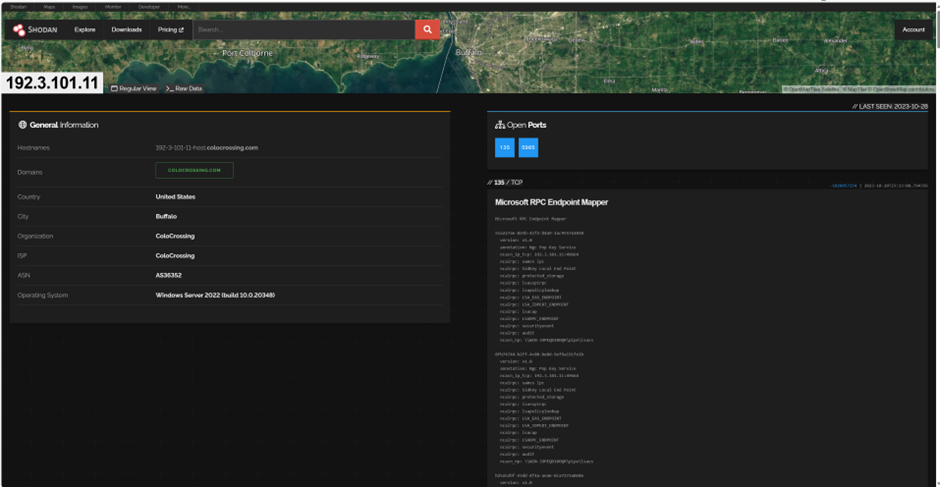
Exposed services
- WINRM
- NETBIOS
Recommendations
Follow vendor guidance:
See guidance from the UK NCSC
https://www.ncsc.gov.uk/news/cisco-ios-xe-vulnerabilities
- If you have a webshell you should probably invoke Incident Response processes.
- If you do not you should ensure your management ports are not exposed to the internet or use ACLs etc. and should apply the vendor updates.
Theory
When conducting infrastructure analysis… I found some of the infra to be very unique… so much so that I have a theory that the threat actors may have tried to misdirect by coping someone’s server config:
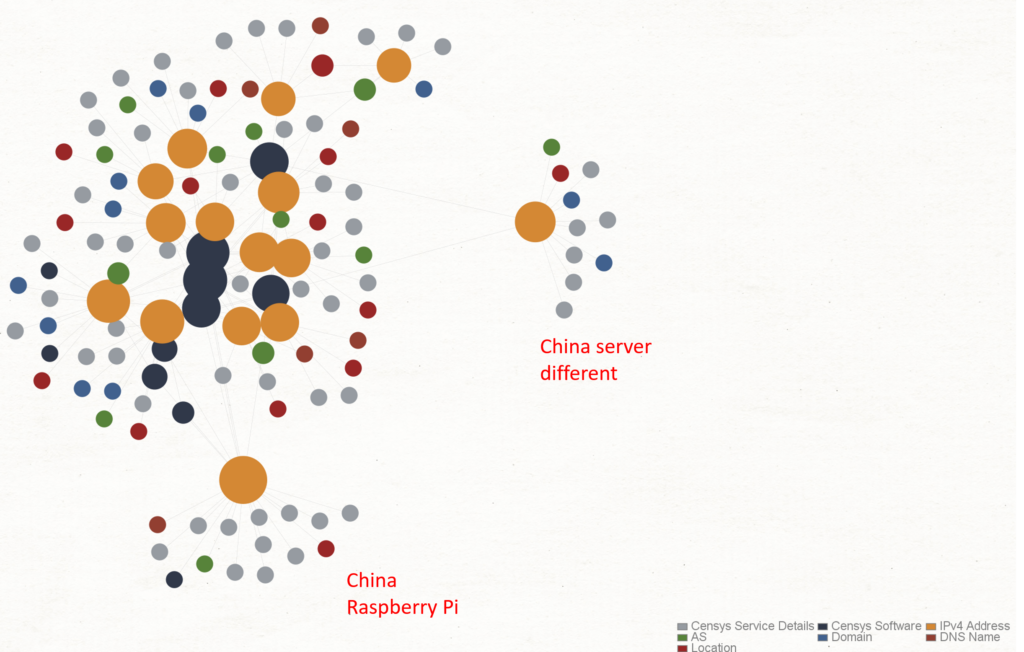
It may be that the threat actors and this “China” based infra are linked… but honestly… it doesn’t feel that way… I look at a lot of infra and this feels like someone trying to misdirect.
(this is just a theory but I have HUMINT to make this theory not seem so mad!) (sorry for the trust me bro reference… )
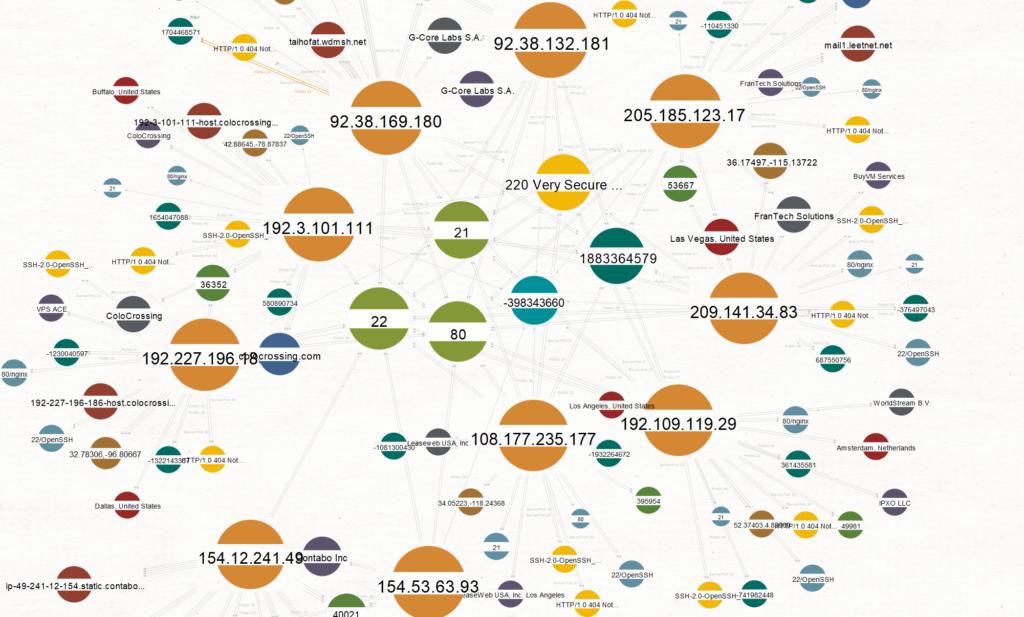
We can see similarities based on unique fingerprints in the infrastructure.
https://www.shodan.io/search?query=http.html_hash%3A-398343660
For example this HTML hash: -398343660
This is a hash for:
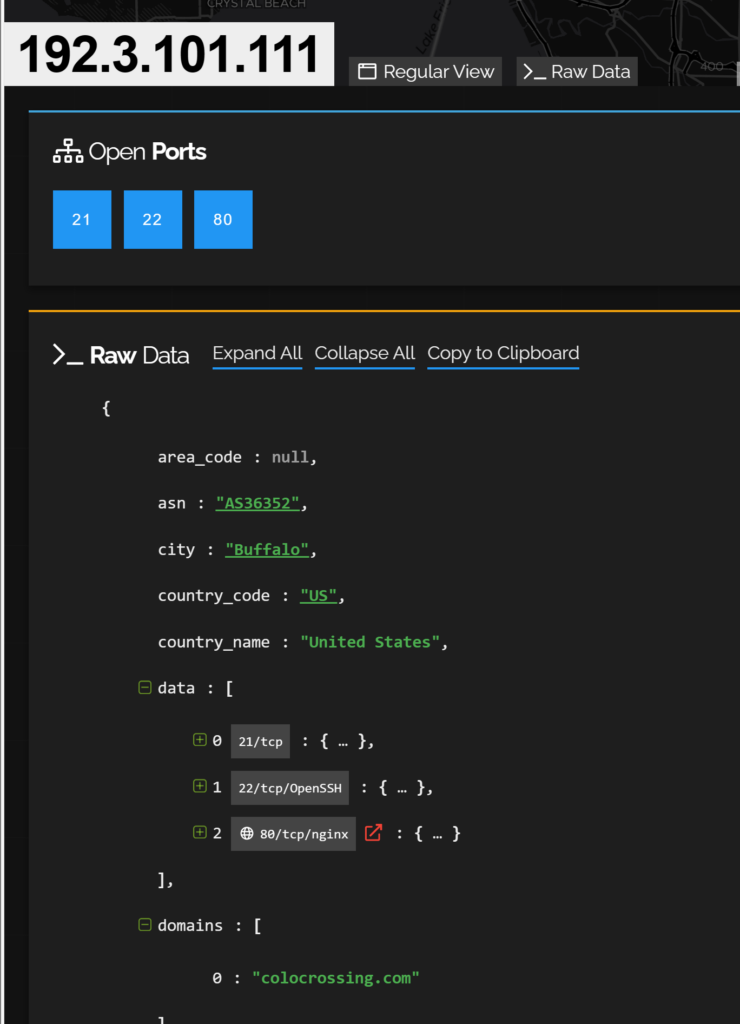
It should be noted that this IP has changed since when this screenshot was taken:
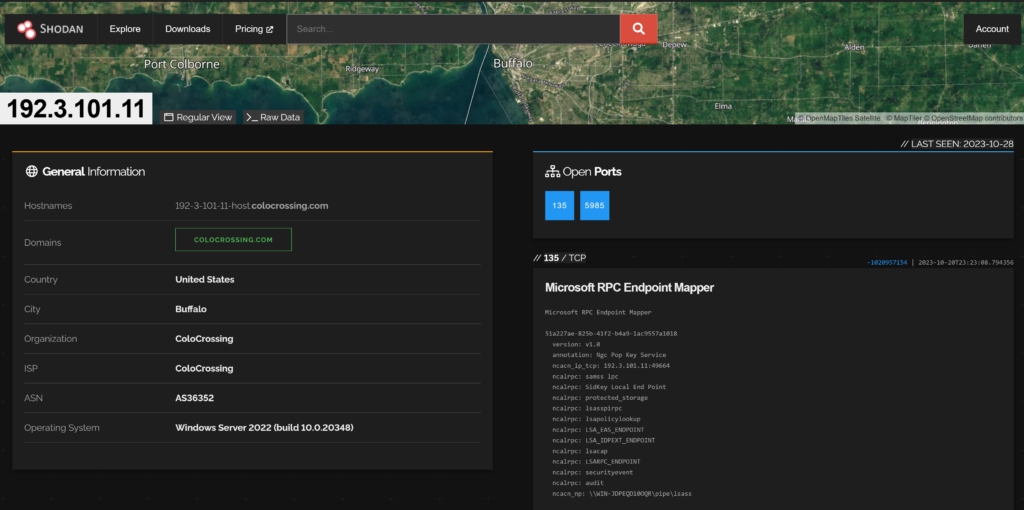
It should be noted that due to the dynamic nature of VPS and Cloud IaaS providers etc. that this is very possible to have:
- been re-deployed to a new customer
- had the OS changed by the threat actor (less likely)
- something else (if port forwarding is used etc. it could simply have been re-directed)
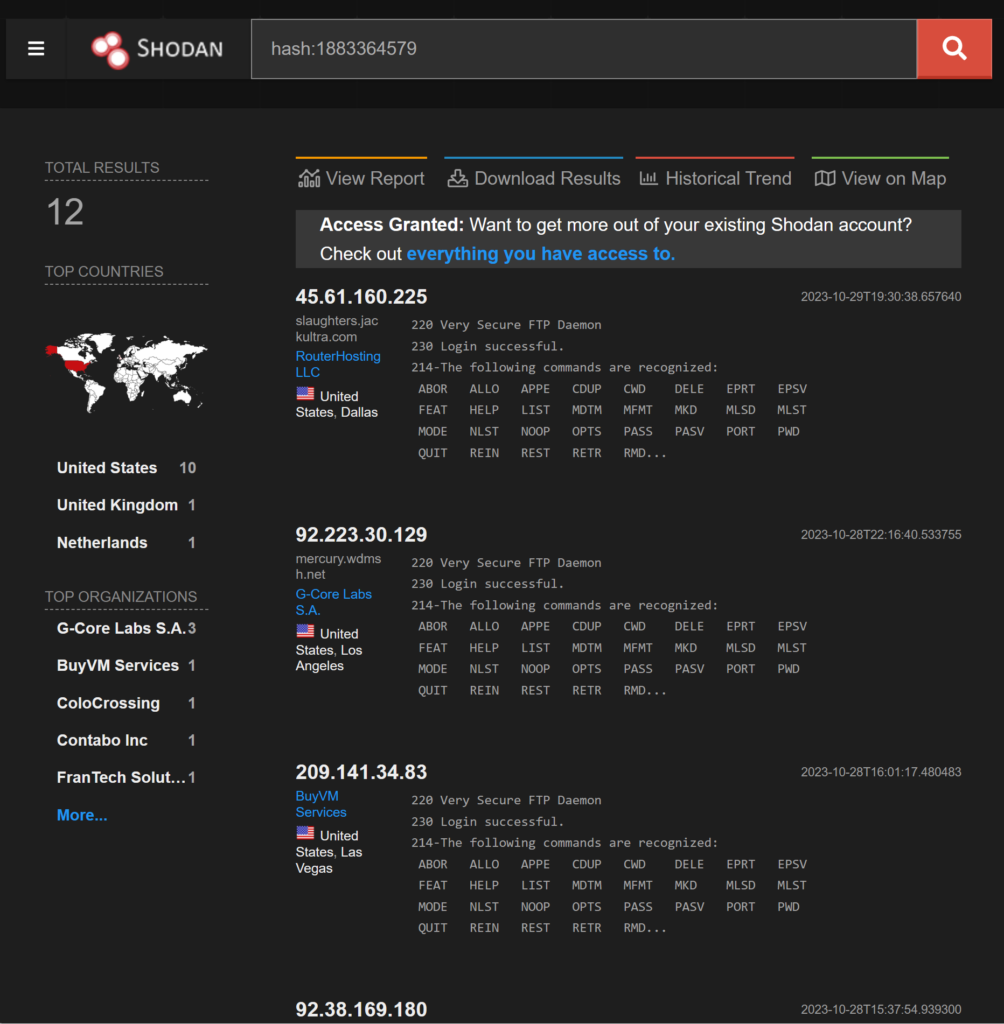
If we pivot from the FTP service hash we have only 12 IPs in Shodan (this is rare!)
What is really rare is this FTP banner: 220 Very Secure FTP Daemon
https://www.shodan.io/search?query=hash%3A1883364579
Now we can use Shodan’s trend feature:
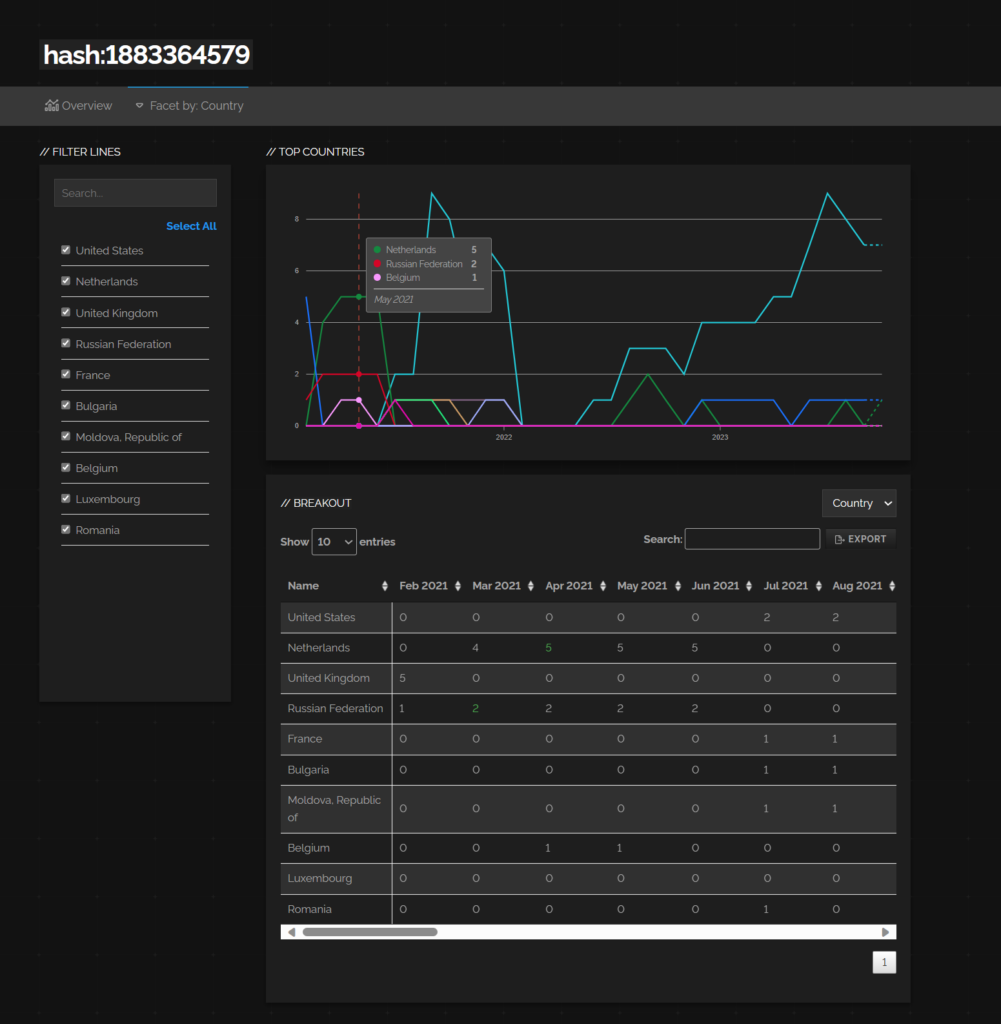
https://trends.shodan.io/search?query=hash:1883364579#facet/country
We can see here this is a rare fingerprint and can see if being used in a range of countries over time.
We can also see every IP that has had this hash over time:
209.141.37.176
192.3.101.111
95.168.191.172
92.38.132.181
137.74.75.69
23.108.57.149
209.141.50.193
172.86.123.115
154.53.56.231
87.251.70.29
92.38.149.128
93.174.89.36
185.153.196.30
82.118.235.109
23.81.246.230
107.172.93.3
107.172.93.29
108.177.235.177
92.38.169.180
209.141.34.83
89.248.168.72
94.102.50.143
94.102.59.7
185.163.47.176
108.62.118.70
213.227.154.70
209.141.51.4
94.102.50.156
80.82.79.180
93.174.89.40
94.102.49.35
94.102.49.104
199.195.249.223
199.195.249.22
107.189.12.103
173.234.155.154
192.109.119.16
5.8.41.70
192.109.119.29
192.227.196.186
109.94.164.64
109.94.164.56
93.174.89.226
85.204.116.121
66.94.98.137
142.234.157.233
205.185.123.17
92.223.30.129
We can then enrich these with other data sources e.g. Alien Vault OTX

This area of investigation is challenging. Finding matching hashes, hostnames, certificates etc. is great. but confirming linkage is not always easy.
This leads us to a range of questions:
What occurred in the kill chains?

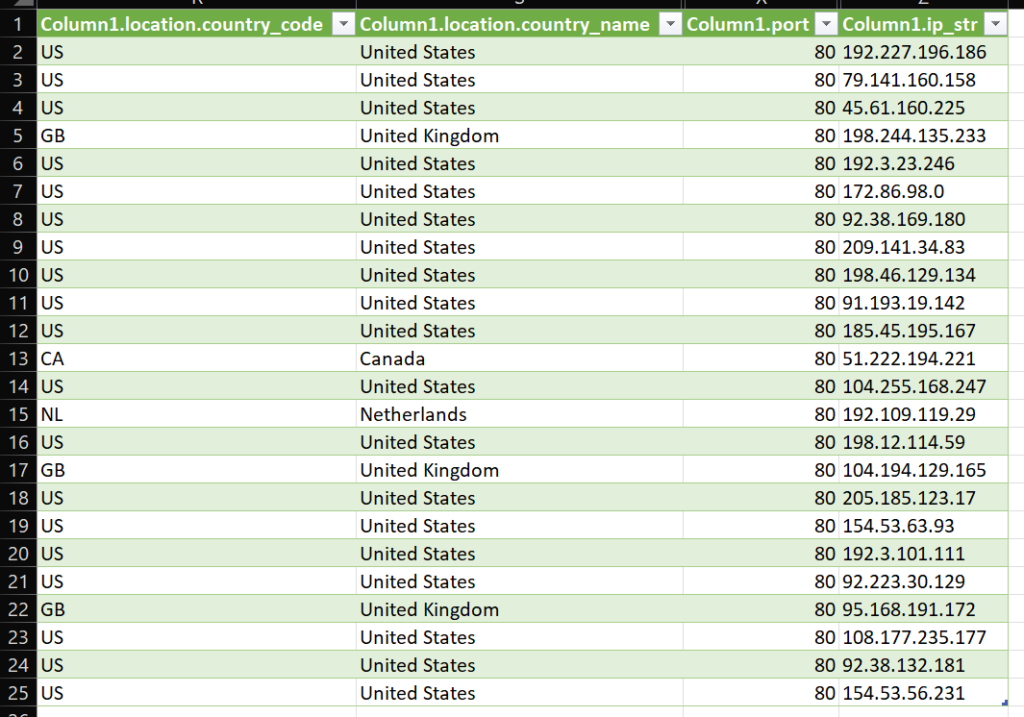
We can see the following IPs with this HTML Hash: -398343660
192.227.196.186
79.141.160.158
45.61.160.225
198.244.135.233
192.3.23.246
172.86.98.0
92.38.169.180
209.141.34.83
198.46.129.134
91.193.19.142
185.45.195.167
51.222.194.221
104.255.168.247
192.109.119.29
198.12.114.59
104.194.129.165
205.185.123.17
154.53.63.93
192.3.101.111
92.223.30.129
95.168.191.172
108.177.235.177
92.38.132.181
154.53.56.231
The hash is from a NGINX not found page. So that might be a bit wide. It is however a very rare hash when looking in Shodan.
We can correlate all this:
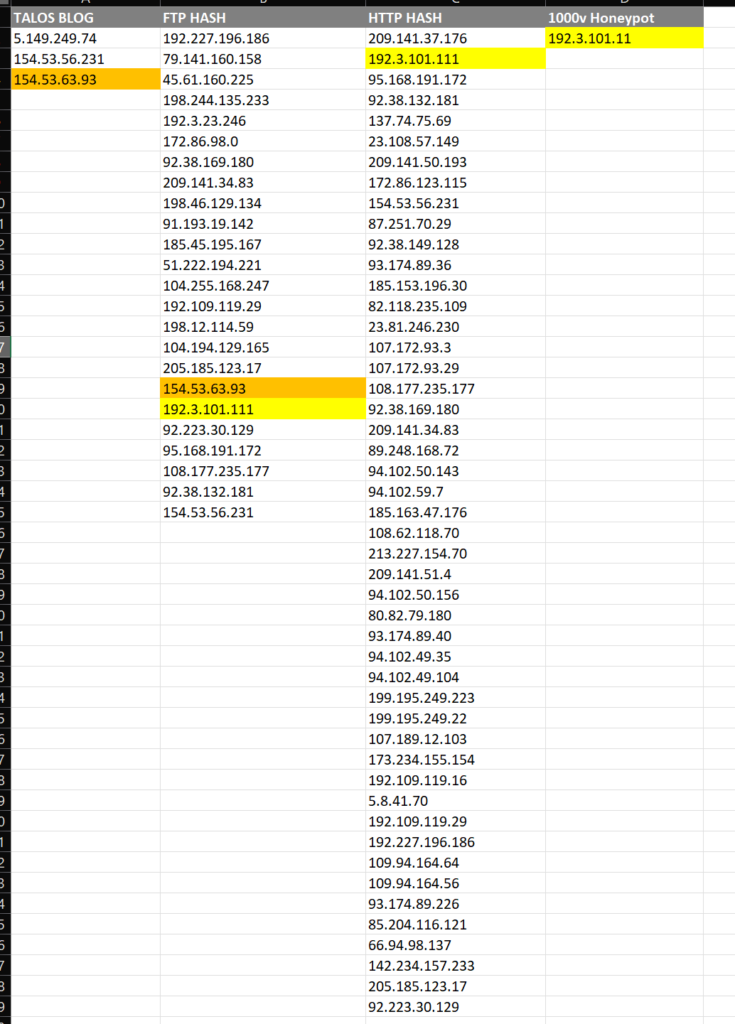
you will however have to appreciate that infrastructure changes.
We can also show an anlysis of all these IPs using GreyNoise:
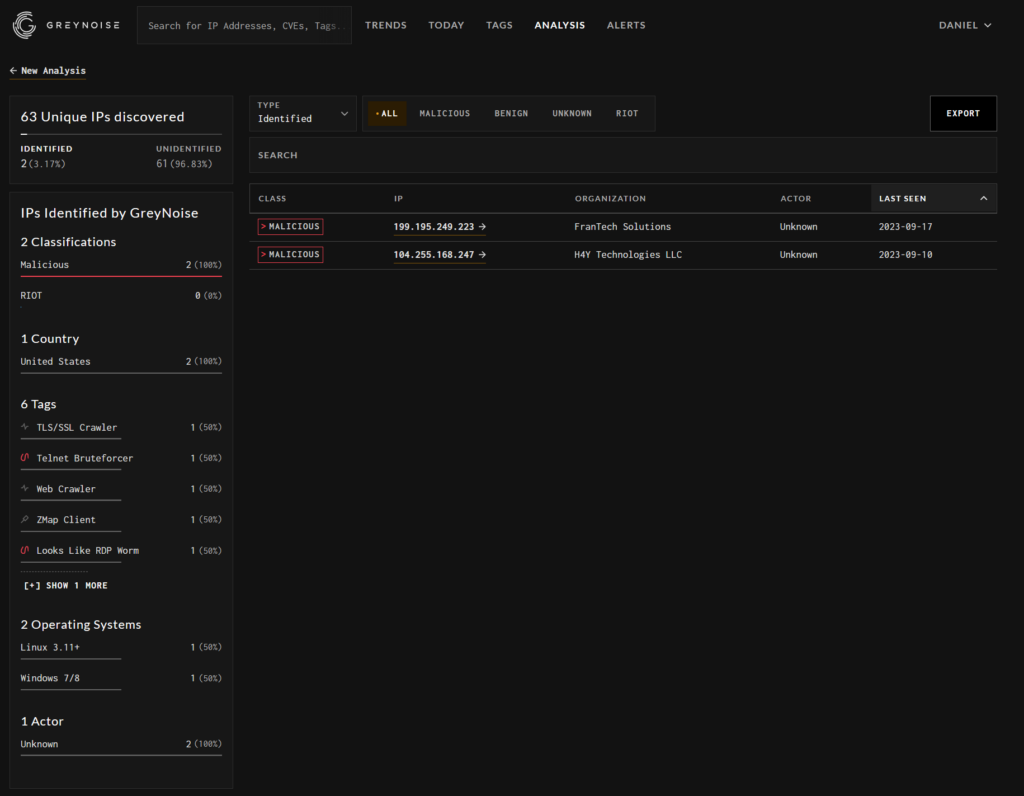
This shows activity from:
199.195.249.223
104.255.168.247
Host Shodan JSON
{"area_code":null,"asn":"AS36352","city":"Buffalo","country_code":"US","country_name":"United States","data":[{"_shodan":{"crawler":"e15fd8f613780213727556a9cb02788d26131443","id":"1783ea42-cc91-449f-8035-7e04cd2fa07e","module":"ms-portmap-tcp","options":{},"ptr":true,"region":"na"},"asn":"AS36352","data":"Microsoft RPC Endpoint Mapper\n\n51a227ae-825b-41f2-b4a9-1ac9557a1018\n version: v1.0\n annotation: Ngc Pop Key Service\n ncacn_ip_tcp: 192.3.101.11:49664\n ncalrpc: samss lpc\n ncalrpc: SidKey Local End Point\n ncalrpc: protected_storage\n ncalrpc: lsasspirpc\n ncalrpc: lsapolicylookup\n ncalrpc: LSA_EAS_ENDPOINT\n ncalrpc: LSA_IDPEXT_ENDPOINT\n ncalrpc: lsacap\n ncalrpc: LSARPC_ENDPOINT\n ncalrpc: securityevent\n ncalrpc: audit\n ncacn_np: \\\\WIN-JDPEQD10OQR\\pipe\\lsass\n\n8fb74744-b2ff-4c00-be0d-9ef9a191fe1b\n version: v1.0\n annotation: Ngc Pop Key Service\n ncacn_ip_tcp: 192.3.101.11:49664\n ncalrpc: samss lpc\n ncalrpc: SidKey Local End Point\n ncalrpc: protected_storage\n ncalrpc: lsasspirpc\n ncalrpc: lsapolicylookup\n ncalrpc: LSA_EAS_ENDPOINT\n ncalrpc: LSA_IDPEXT_ENDPOINT\n ncalrpc: lsacap\n ncalrpc: LSARPC_ENDPOINT\n ncalrpc: securityevent\n ncalrpc: audit\n ncacn_np: \\\\WIN-JDPEQD10OQR\\pipe\\lsass\n\nb25a52bf-e5dd-4f4a-aea6-8ca7272a0e86\n version: v2.0\n annotation: KeyIso\n ncacn_ip_tcp: 192.3.101.11:49664\n ncalrpc: samss lpc\n ncalrpc: SidKey Local End Point\n ncalrpc: protected_storage\n ncalrpc: lsasspirpc\n ncalrpc: lsapolicylookup\n ncalrpc: LSA_EAS_ENDPOINT\n ncalrpc: LSA_IDPEXT_ENDPOINT\n ncalrpc: lsacap\n ncalrpc: LSARPC_ENDPOINT\n ncalrpc: securityevent\n ncalrpc: audit\n ncacn_np: \\\\WIN-JDPEQD10OQR\\pipe\\lsass\n\n12345778-1234-abcd-ef00-0123456789ac\n version: v1.0\n protocol: [MS-SAMR]: Security Account Manager (SAM) Remote Protocol\n provider: samsrv.dll\n ncacn_ip_tcp: 192.3.101.11:49664\n ncalrpc: samss lpc\n ncalrpc: SidKey Local End Point\n ncalrpc: protected_storage\n ncalrpc: lsasspirpc\n ncalrpc: lsapolicylookup\n ncalrpc: LSA_EAS_ENDPOINT\n ncalrpc: LSA_IDPEXT_ENDPOINT\n ncalrpc: lsacap\n ncalrpc: LSARPC_ENDPOINT\n ncalrpc: securityevent\n ncalrpc: audit\n ncacn_np: \\\\WIN-JDPEQD10OQR\\pipe\\lsass\n\nd95afe70-a6d5-4259-822e-2c84da1ddb0d\n version: v1.0\n protocol: [MS-RSP]: Remote Shutdown Protocol\n provider: wininit.exe\n ncacn_ip_tcp: 192.3.101.11:49665\n ncalrpc: WindowsShutdown\n ncacn_np: \\\\WIN-JDPEQD10OQR\\PIPE\\InitShutdown\n ncalrpc: WMsgKRpc056F20\n\n76f226c3-ec14-4325-8a99-6a46348418af\n version: v1.0\n provider: winlogon.exe\n ncalrpc: WindowsShutdown\n ncacn_np: \\\\WIN-JDPEQD10OQR\\PIPE\\InitShutdown\n ncalrpc: WMsgKRpc056F20\n ncalrpc: WMsgKRpc0598D1\n ncalrpc: WMsgKRpc01FA6523D3\n\nfc48cd89-98d6-4628-9839-86f7a3e4161a\n version: v1.0\n ncalrpc: dabrpc\n ncalrpc: csebpub\n ncalrpc: LRPC-78e0c783ca581d4a13\n ncalrpc: LRPC-6e4b72e1a87bdf102d\n ncalrpc: LRPC-1f2b273cae7d51a86f\n ncalrpc: LRPC-646b462ef693e6aacc\n ncalrpc: OLE26552A490A5B48973A5FE9A74FC2\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n\nd09bdeb5-6171-4a34-bfe2-06fa82652568\n version: v1.0\n ncalrpc: csebpub\n ncalrpc: LRPC-78e0c783ca581d4a13\n ncalrpc: LRPC-6e4b72e1a87bdf102d\n ncalrpc: LRPC-1f2b273cae7d51a86f\n ncalrpc: LRPC-646b462ef693e6aacc\n ncalrpc: OLE26552A490A5B48973A5FE9A74FC2\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n ncalrpc: LRPC-6e4b72e1a87bdf102d\n ncalrpc: LRPC-1f2b273cae7d51a86f\n ncalrpc: LRPC-646b462ef693e6aacc\n ncalrpc: OLE26552A490A5B48973A5FE9A74FC2\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n ncalrpc: LRPC-1f2b273cae7d51a86f\n ncalrpc: LRPC-646b462ef693e6aacc\n ncalrpc: OLE26552A490A5B48973A5FE9A74FC2\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n ncalrpc: LRPC-3ff12db1c383fea653\n ncalrpc: LRPC-08ba6c6c94be8f43dc\n\n697dcda9-3ba9-4eb2-9247-e11f1901b0d2\n version: v1.0\n ncalrpc: LRPC-78e0c783ca581d4a13\n ncalrpc: LRPC-6e4b72e1a87bdf102d\n ncalrpc: LRPC-1f2b273cae7d51a86f\n ncalrpc: LRPC-646b462ef693e6aacc\n ncalrpc: OLE26552A490A5B48973A5FE9A74FC2\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n\n9b008953-f195-4bf9-bde0-4471971e58ed\n version: v1.0\n ncalrpc: LRPC-6e4b72e1a87bdf102d\n ncalrpc: LRPC-1f2b273cae7d51a86f\n ncalrpc: LRPC-646b462ef693e6aacc\n ncalrpc: OLE26552A490A5B48973A5FE9A74FC2\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n\n0d47017b-b33b-46ad-9e18-fe96456c5078\n version: v1.0\n ncalrpc: umpo\n\n95406f0b-b239-4318-91bb-cea3a46ff0dc\n version: v1.0\n ncalrpc: umpo\n\n4ed8abcc-f1e2-438b-981f-bb0e8abc010c\n version: v1.0\n ncalrpc: umpo\n\n0ff1f646-13bb-400a-ab50-9a78f2b7a85a\n version: v1.0\n ncalrpc: umpo\n\n6982a06e-5fe2-46b1-b39c-a2c545bfa069\n version: v1.0\n ncalrpc: umpo\n\n082a3471-31b6-422a-b931-a54401960c62\n version: v1.0\n ncalrpc: umpo\n\nfae436b0-b864-4a87-9eda-298547cd82f2\n version: v1.0\n ncalrpc: umpo\n\ne53d94ca-7464-4839-b044-09a2fb8b3ae5\n version: v1.0\n ncalrpc: umpo\n\n178d84be-9291-4994-82c6-3f909aca5a03\n version: v1.0\n ncalrpc: umpo\n\n4dace966-a243-4450-ae3f-9b7bcb5315b8\n version: v2.0\n ncalrpc: umpo\n\n1832bcf6-cab8-41d4-85d2-c9410764f75a\n version: v1.0\n ncalrpc: umpo\n\nc521facf-09a9-42c5-b155-72388595cbf0\n version: v0.0\n ncalrpc: umpo\n\n2c7fd9ce-e706-4b40-b412-953107ef9bb0\n version: v0.0\n ncalrpc: umpo\n\n88abcbc3-34ea-76ae-8215-767520655a23\n version: v0.0\n ncalrpc: LRPC-646b462ef693e6aacc\n ncalrpc: OLE26552A490A5B48973A5FE9A74FC2\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n\n76c217bc-c8b4-4201-a745-373ad9032b1a\n version: v1.0\n ncalrpc: LRPC-646b462ef693e6aacc\n ncalrpc: OLE26552A490A5B48973A5FE9A74FC2\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n\n55e6b932-1979-45d6-90c5-7f6270724112\n version: v1.0\n ncalrpc: LRPC-646b462ef693e6aacc\n ncalrpc: OLE26552A490A5B48973A5FE9A74FC2\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n\n857fb1be-084f-4fb5-b59c-4b2c4be5f0cf\n version: v1.0\n ncalrpc: OLE26552A490A5B48973A5FE9A74FC2\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n\n20c40295-8dba-48e6-aebf-3e78ef3bb144\n version: v2.0\n ncalrpc: OLE26552A490A5B48973A5FE9A74FC2\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n\n2513bcbe-6cd4-4348-855e-7efb3c336dd3\n version: v2.0\n ncalrpc: OLE26552A490A5B48973A5FE9A74FC2\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n\n0d3e2735-cea0-4ecc-a9e2-41a2d81aed4e\n version: v1.0\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n\nc605f9fb-f0a3-4e2a-a073-73560f8d9e3e\n version: v1.0\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n\n1b37ca91-76b1-4f5e-a3c7-2abfc61f2bb0\n version: v1.0\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n\n8bfc3be1-6def-4e2d-af74-7c47cd0ade4a\n version: v1.0\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n\n2d98a740-581d-41b9-aa0d-a88b9d5ce938\n version: v1.0\n ncalrpc: LRPC-b72d5e7e5d6e2b0f1d\n ncalrpc: actkernel\n ncalrpc: umpo\n\ndd59071b-3215-4c59-8481-972edadc0f6a\n version: v1.0\n ncalrpc: actkernel\n ncalrpc: umpo\n\n0361ae94-0316-4c6c-8ad8-c594375800e2\n version: v1.0\n ncalrpc: umpo\n\n5824833b-3c1a-4ad2-bdfd-c31d19e23ed2\n version: v1.0\n ncalrpc: umpo\n\nbdaa0970-413b-4a3e-9e5d-f6dc9d7e0760\n version: v1.0\n ncalrpc: umpo\n\n3b338d89-6cfa-44b8-847e-531531bc9992\n version: v1.0\n ncalrpc: umpo\n\n8782d3b9-ebbd-4644-a3d8-e8725381919b\n version: v1.0\n ncalrpc: umpo\n\n085b0334-e454-4d91-9b8c-4134f9e793f3\n version: v1.0\n ncalrpc: umpo\n\n4bec6bb8-b5c2-4b6f-b2c1-5da5cf92d0d9\n version: v1.0\n ncalrpc: umpo\n\nc9ac6db5-82b7-4e55-ae8a-e464ed7b4277\n version: v1.0\n annotation: Impl friendly name\n provider: sysntfy.dll\n ncalrpc: LRPC-ed3bfbab191b42498b\n ncalrpc: IUserProfile2\n ncalrpc: LRPC-c216e136a8aaafcbbf\n ncalrpc: LRPC-359df7f63f413f67e7\n ncalrpc: senssvc\n ncalrpc: LRPC-a2983dfd98bcee3bdf\n\ne40f7b57-7a25-4cd3-a135-7f7d3df9d16b\n version: v1.0\n ncalrpc: LRPC-9214777306fb7397f9\n\n880fd55e-43b9-11e0-b1a8-cf4edfd72085\n version: v1.0\n annotation: KAPI Service endpoint\n ncalrpc: LRPC-22b6d9ccfafa8d9eab\n ncalrpc: OLEFE843B2897F64996B90902879156\n ncalrpc: LRPC-3ff12db1c383fea653\n\n5222821f-d5e2-4885-84f1-5f6185a0ec41\n version: v1.0\n ncalrpc: LRPC-7259cef2221e98cf0f\n\na500d4c6-0dd1-4543-bc0c-d5f93486eaf8\n version: v1.0\n ncalrpc: LRPC-cd0c17746235190007\n ncalrpc: LRPC-08ba6c6c94be8f43dc\n\nf6beaff7-1e19-4fbb-9f8f-b89e2018337c\n version: v1.0\n annotation: Event log TCPIP\n protocol: [MS-EVEN6]: EventLog Remoting Protocol\n provider: wevtsvc.dll\n ncacn_ip_tcp: 192.3.101.11:49666\n ncacn_np: \\\\WIN-JDPEQD10OQR\\pipe\\eventlog\n ncalrpc: eventlog\n\n2eb08e3e-639f-4fba-97b1-14f878961076\n version: v1.0\n annotation: Group Policy RPC Interface\n provider: gpsvc.dll\n ncalrpc: LRPC-4ab6531290c6b7c417\n\n7ea70bcf-48af-4f6a-8968-6a440754d5fa\n version: v1.0\n annotation: NSI server endpoint\n provider: nsisvc.dll\n ncalrpc: LRPC-e3f0c96f6cacf958df\n\n3a9ef155-691d-4449-8d05-09ad57031823\n version: v1.0\n ncacn_ip_tcp: 192.3.101.11:49667\n ncalrpc: LRPC-c48ba608c62c3e1dad\n ncalrpc: ubpmtaskhostchannel\n ncacn_np: \\\\WIN-JDPEQD10OQR\\PIPE\\atsvc\n ncalrpc: LRPC-381eba15863cf8884e\n\n86d35949-83c9-4044-b424-db363231fd0c\n version: v1.0\n protocol: [MS-TSCH]: Task Scheduler Service Remoting Protocol\n provider: schedsvc.dll\n ncacn_ip_tcp: 192.3.101.11:49667\n ncalrpc: LRPC-c48ba608c62c3e1dad\n ncalrpc: ubpmtaskhostchannel\n ncacn_np: \\\\WIN-JDPEQD10OQR\\PIPE\\atsvc\n ncalrpc: LRPC-381eba15863cf8884e\n\n33d84484-3626-47ee-8c6f-e7e98b113be1\n version: v2.0\n ncalrpc: LRPC-c48ba608c62c3e1dad\n ncalrpc: ubpmtaskhostchannel\n ncacn_np: \\\\WIN-JDPEQD10OQR\\PIPE\\atsvc\n ncalrpc: LRPC-381eba15863cf8884e\n\n378e52b0-c0a9-11cf-822d-00aa0051e40f\n version: v1.0\n protocol: [MS-TSCH]: Task Scheduler Service Remoting Protocol\n provider: taskcomp.dll\n ncacn_np: \\\\WIN-JDPEQD10OQR\\PIPE\\atsvc\n ncalrpc: LRPC-381eba15863cf8884e\n\n1ff70682-0a51-30e8-076d-740be8cee98b\n version: v1.0\n protocol: [MS-TSCH]: Task Scheduler Service Remoting Protocol\n provider: taskcomp.dll\n ncacn_np: \\\\WIN-JDPEQD10OQR\\PIPE\\atsvc\n ncalrpc: LRPC-381eba15863cf8884e\n\n0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53\n version: v1.0\n provider: schedsvc.dll\n ncalrpc: LRPC-381eba15863cf8884e\n\n3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5\n version: v1.0\n annotation: DHCP Client LRPC Endpoint\n provider: dhcpcsvc.dll\n ncalrpc: dhcpcsvc\n ncalrpc: dhcpcsvc6\n\n3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6\n version: v1.0\n annotation: DHCPv6 Client LRPC Endpoint\n provider: dhcpcsvc6.dll\n ncalrpc: dhcpcsvc6\n\n30adc50c-5cbc-46ce-9a0e-91914789e23c\n version: v1.0\n annotation: NRP server endpoint\n provider: nrpsrv.dll\n ncalrpc: LRPC-c467cacde3ecd79b78\n ncalrpc: DNSResolver\n\n30b044a5-a225-43f0-b3a4-e060df91f9c1\n version: v1.0\n provider: certprop.dll\n ncalrpc: LRPC-4b0bbfe5bf7417f471\n\n7f1343fe-50a9-4927-a778-0c5859517bac\n version: v1.0\n annotation: DfsDs service\n ncacn_np: \\\\WIN-JDPEQD10OQR\\PIPE\\wkssvc\n ncalrpc: LRPC-25a6a189e765527b5e\n\neb081a0d-10ee-478a-a1dd-50995283e7a8\n version: v3.0\n annotation: Witness Client Test Interface\n ncalrpc: LRPC-25a6a189e765527b5e\n\nf2c9b409-c1c9-4100-8639-d8ab1486694a\n version: v1.0\n annotation: Witness Client Upcall Server\n ncalrpc: LRPC-25a6a189e765527b5e\n\n13560fa9-8c09-4b56-a1fd-04d083b9b2a1\n version: v1.0\n ncalrpc: LRPC-b9d95700f03f1b212f\n\nc2d1b5dd-fa81-4460-9dd6-e7658b85454b\n version: v1.0\n ncalrpc: LRPC-b9d95700f03f1b212f\n\nf44e62af-dab1-44c2-8013-049a9de417d6\n version: v1.0\n ncalrpc: LRPC-b9d95700f03f1b212f\n\nb37f900a-eae4-4304-a2ab-12bb668c0188\n version: v1.0\n ncalrpc: LRPC-b9d95700f03f1b212f\n\nabfb6ca3-0c5e-4734-9285-0aee72fe8d1c\n version: v1.0\n ncalrpc: LRPC-b9d95700f03f1b212f\n\n29770a8f-829b-4158-90a2-78cd488501f7\n version: v1.0\n ncacn_ip_tcp: 192.3.101.11:49668\n ncacn_np: \\\\WIN-JDPEQD10OQR\\pipe\\SessEnvPublicRpc\n ncalrpc: SessEnvPrivateRpc\n ncalrpc: LRPC-a2983dfd98bcee3bdf\n\n3f787932-3452-4363-8651-6ea97bb373bb\n version: v1.0\n annotation: NSP Rpc Interface\n ncalrpc: LRPC-f93641e66d38260bc4\n ncalrpc: OLE67A3F599661ABAAC8AF2CD052E0D\n\n0d3c7f20-1c8d-4654-a1b3-51563b298bda\n version: v1.0\n annotation: UserMgrCli\n ncalrpc: LRPC-d61b86c8581c05470f\n ncalrpc: OLEB50ECFD719BA2A503F10C86D42D3\n\nb18fbab6-56f8-4702-84e0-41053293a869\n version: v1.0\n annotation: UserMgrCli\n ncalrpc: LRPC-d61b86c8581c05470f\n ncalrpc: OLEB50ECFD719BA2A503F10C86D42D3\n\n2fb92682-6599-42dc-ae13-bd2ca89bd11c\n version: v1.0\n annotation: Fw APIs\n provider: MPSSVC.dll\n ncalrpc: LRPC-7107eac8a5e8d1859a\n ncalrpc: LRPC-8378a945b60099208e\n ncalrpc: LRPC-8ea279f95192b4af8d\n ncalrpc: LRPC-9292668da800f2840a\n\nf47433c3-3e9d-4157-aad4-83aa1f5c2d4c\n version: v1.0\n annotation: Fw APIs\n ncalrpc: LRPC-8378a945b60099208e\n ncalrpc: LRPC-8ea279f95192b4af8d\n ncalrpc: LRPC-9292668da800f2840a\n\n7f9d11bf-7fb9-436b-a812-b2d50c5d4c03\n version: v1.0\n annotation: Fw APIs\n provider: MPSSVC.dll\n ncalrpc: LRPC-8ea279f95192b4af8d\n ncalrpc: LRPC-9292668da800f2840a\n\ndd490425-5325-4565-b774-7e27d6c09c24\n version: v1.0\n annotation: Base Firewall Engine API\n provider: BFE.DLL\n ncalrpc: LRPC-9292668da800f2840a\n\n76f03f96-cdfd-44fc-a22c-64950a001209\n version: v1.0\n protocol: [MS-PAR]: Print System Asynchronous Remote Protocol\n provider: spoolsv.exe\n ncacn_ip_tcp: 192.3.101.11:49670\n ncalrpc: LRPC-a31fbc6a63f9414c61\n\n4a452661-8290-4b36-8fbe-7f4093a94978\n version: v1.0\n provider: spoolsv.exe\n ncacn_ip_tcp: 192.3.101.11:49670\n ncalrpc: LRPC-a31fbc6a63f9414c61\n\nae33069b-a2a8-46ee-a235-ddfd339be281\n version: v1.0\n protocol: [MS-PAN]: Print System Asynchronous Notification Protocol\n provider: spoolsv.exe\n ncacn_ip_tcp: 192.3.101.11:49670\n ncalrpc: LRPC-a31fbc6a63f9414c61\n\n0b6edbfa-4a24-4fc6-8a23-942b1eca65d1\n version: v1.0\n protocol: [MS-PAN]: Print System Asynchronous Notification Protocol\n provider: spoolsv.exe\n ncacn_ip_tcp: 192.3.101.11:49670\n ncalrpc: LRPC-a31fbc6a63f9414c61\n\n12345678-1234-abcd-ef00-0123456789ab\n version: v1.0\n protocol: [MS-RPRN]: Print System Remote Protocol\n provider: spoolsv.exe\n ncacn_ip_tcp: 192.3.101.11:49670\n ncalrpc: LRPC-a31fbc6a63f9414c61\n\nc49a5a70-8a7f-4e70-ba16-1e8f1f193ef1\n version: v1.0\n annotation: Adh APIs\n ncalrpc: TeredoControl\n ncalrpc: TeredoDiagnostics\n ncalrpc: LRPC-0297fce2640379526d\n\nc36be077-e14b-4fe9-8abc-e856ef4f048b\n version: v1.0\n annotation: Proxy Manager client server endpoint\n ncalrpc: TeredoControl\n ncalrpc: TeredoDiagnostics\n ncalrpc: LRPC-0297fce2640379526d\n\n2e6035b2-e8f1-41a7-a044-656b439c4c34\n version: v1.0\n annotation: Proxy Manager provider server endpoint\n ncalrpc: TeredoControl\n ncalrpc: TeredoDiagnostics\n ncalrpc: LRPC-0297fce2640379526d\n\n552d076a-cb29-4e44-8b6a-d15e59e2c0af\n version: v1.0\n annotation: IP Transition Configuration endpoint\n provider: iphlpsvc.dll\n ncalrpc: LRPC-0297fce2640379526d\n\na398e520-d59a-4bdd-aa7a-3c1e0303a511\n version: v1.0\n annotation: IKE/Authip API\n provider: IKEEXT.DLL\n ncalrpc: LRPC-87953a9d5d220c7fce\n\n1a0d010f-1c33-432c-b0f5-8cf4e8053099\n version: v1.0\n annotation: IdSegSrv service\n ncalrpc: LRPC-86371bf1350d57c0fd\n\n98716d03-89ac-44c7-bb8c-285824e51c4a\n version: v1.0\n annotation: XactSrv service\n provider: srvsvc.dll\n ncalrpc: LRPC-86371bf1350d57c0fd\n\n367abb81-9844-35f1-ad32-98f038001003\n version: v2.0\n protocol: [MS-SCMR]: Service Control Manager Remote Protocol\n provider: services.exe\n ncacn_ip_tcp: 192.3.101.11:49671\n\n98cd761e-e77d-41c8-a3c0-0fb756d90ec2\n version: v1.0\n ncalrpc: LRPC-5bc32e2d2f4087aa4f\n ncalrpc: OLEE0E105CEBDC539FFDBD1F448045D\n\nd22895ef-aff4-42c5-a5b2-b14466d34ab4\n version: v1.0\n ncalrpc: LRPC-5bc32e2d2f4087aa4f\n ncalrpc: OLEE0E105CEBDC539FFDBD1F448045D\n\ne38f5360-8572-473e-b696-1b46873beeab\n version: v1.0\n ncalrpc: LRPC-5bc32e2d2f4087aa4f\n ncalrpc: OLEE0E105CEBDC539FFDBD1F448045D\n\n95095ec8-32ea-4eb0-a3e2-041f97b36168\n version: v1.0\n ncalrpc: LRPC-5bc32e2d2f4087aa4f\n ncalrpc: OLEE0E105CEBDC539FFDBD1F448045D\n\nfd8be72b-a9cd-4b2c-a9ca-4ded242fbe4d\n version: v1.0\n ncalrpc: LRPC-5bc32e2d2f4087aa4f\n ncalrpc: OLEE0E105CEBDC539FFDBD1F448045D\n\n4c9dbf19-d39e-4bb9-90ee-8f7179b20283\n version: v1.0\n ncalrpc: LRPC-5bc32e2d2f4087aa4f\n ncalrpc: OLEE0E105CEBDC539FFDBD1F448045D\n\nd4051bde-9cdd-4910-b393-4aa85ec3c482\n version: v1.0\n ncalrpc: LRPC-5bc32e2d2f4087aa4f\n ncalrpc: OLEE0E105CEBDC539FFDBD1F448045D\n\n7df1ceae-de4e-4e6f-ab14-49636e7c2052\n version: v1.0\n ncalrpc: LRPC-30c96d8e06acfcc529\n\nf3f09ffd-fbcf-4291-944d-70ad6e0e73bb\n version: v1.0\n ncalrpc: LRPC-a6bfb4eea34a4ccc23\n ncalrpc: LRPC-5b8696222a82714d33\n\n650a7e26-eab8-5533-ce43-9c1dfce11511\n version: v1.0\n annotation: Vpn APIs\n ncalrpc: LRPC-e1d8102a1766e6ff1d\n ncalrpc: VpnikeRpc\n ncalrpc: RasmanLrpc\n ncacn_np: \\\\WIN-JDPEQD10OQR\\PIPE\\ROUTER\n\n509bc7ae-77be-4ee8-b07c-0d096bb44345\n version: v1.0\n ncalrpc: LRPC-09b73b8cefa46d5038\n ncalrpc: OLE0B54C468CC03F7440F105B69ECE1\n\nb58aa02e-2884-4e97-8176-4ee06d794184\n version: v1.0\n provider: sysmain.dll\n ncalrpc: LRPC-116e5fbe7842eb7192\n\n6b5bdd1e-528c-422c-af8c-a4079be4fe48\n version: v1.0\n annotation: Remote Fw APIs\n protocol: [MS-FASP]: Firewall and Advanced Security Protocol\n provider: FwRemoteSvr.dll\n ncacn_ip_tcp: 192.3.101.11:49672\n ncalrpc: ipsec\n\nd249bd56-4cc0-4fd3-8ce6-6fe050d590cb\n version: v0.0\n ncalrpc: LRPC-9d0232a1fd77b31d65\n\nd8140e00-5c46-4ae6-80ac-2f9a76df224c\n version: v0.0\n ncalrpc: LRPC-9d0232a1fd77b31d65\n\n906b0ce0-c70b-1067-b317-00dd010662da\n version: v1.0\n protocol: [MS-CMPO]: MSDTC Connection Manager:\n provider: msdtcprx.dll\n ncalrpc: LRPC-ef1df0ed30b96c82a8\n ncalrpc: LRPC-ef1df0ed30b96c82a8\n ncalrpc: LRPC-ef1df0ed30b96c82a8\n\n0767a036-0d22-48aa-ba69-b619480f38cb\n version: v1.0\n annotation: PcaSvc\n provider: pcasvc.dll\n ncalrpc: LRPC-d9e6420a1b8276b070\n\na4b8d482-80ce-40d6-934d-b22a01a44fe7\n version: v1.0\n annotation: LicenseManager\n ncalrpc: LicenseServiceEndpoint\n\nbf4dc912-e52f-4904-8ebe-9317c1bdd497\n version: v1.0\n ncalrpc: LRPC-e59bd6493fcd65389d\n ncalrpc: OLE6953FF04EF70DA2ECFD92F123A30\n\n58e604e8-9adb-4d2e-a464-3b0683fb1480\n version: v1.0\n annotation: AppInfo\n provider: appinfo.dll\n ncalrpc: LRPC-9712c111fa3a8ba8d7\n\nfd7a0523-dc70-43dd-9b2e-9c5ed48225b1\n version: v1.0\n annotation: AppInfo\n provider: appinfo.dll\n ncalrpc: LRPC-9712c111fa3a8ba8d7\n\n5f54ce7d-5b79-4175-8584-cb65313a0e98\n version: v1.0\n annotation: AppInfo\n provider: appinfo.dll\n ncalrpc: LRPC-9712c111fa3a8ba8d7\n\n201ef99a-7fa0-444c-9399-19ba84f12a1a\n version: v1.0\n annotation: AppInfo\n provider: appinfo.dll\n ncalrpc: LRPC-9712c111fa3a8ba8d7\n\n0497b57d-2e66-424f-a0c6-157cd5d41700\n version: v1.0\n annotation: AppInfo\n ncalrpc: LRPC-9712c111fa3a8ba8d7\n\n0dd94748-2ff1-11ee-be56-0242ac120002\n version: v2.0\n ncalrpc: LRPC-ab5fa032c54eaf4a34\n ncalrpc: OLE0AE6DC61EBA54B9AAD09EE9094BB\n\n12e65dd8-887f-41ef-91bf-8d816c42c2e7\n version: v1.0\n annotation: Secure Desktop LRPC interface\n provider: winlogon.exe\n ncalrpc: WMsgKRpc01FA6523D3\n\nb1ef227e-dfa5-421e-82bb-67a6a129c496\n version: v0.0\n ncalrpc: LRPC-c38b7f7f939bf683ef\n ncalrpc: OLEBD9E33F1563526D374965B9337DB\n\n0fc77b1a-95d8-4a2e-a0c0-cff54237462b\n version: v0.0\n ncalrpc: LRPC-c38b7f7f939bf683ef\n ncalrpc: OLEBD9E33F1563526D374965B9337DB\n\n8ec21e98-b5ce-4916-a3d6-449fa428a007\n version: v0.0\n ncalrpc: LRPC-c38b7f7f939bf683ef\n ncalrpc: OLEBD9E33F1563526D374965B9337DB\n\n43890c94-bfd7-4655-ad6a-b4a68397cdcb\n version: v0.0\n ncalrpc: LRPC-3d06b375facfca802e\n\nc8ba73d2-3d55-429c-8e9a-c44f006f69fc\n version: v0.0\n ncalrpc: LRPC-3d06b375facfca802e\n\ne8748f69-a2a4-40df-9366-62dbeb696e26\n version: v0.0\n ncalrpc: LRPC-3d06b375facfca802e\n\n3473dd4d-2e88-4006-9cba-22570909dd10\n version: v5.256\n annotation: WinHttp Auto-Proxy Service\n ncalrpc: a7bf55df-3cd7-4036-b9e8-77f769394aa4\n ncalrpc: LRPC-50d9494e48ee4ada88\n","domains":["colocrossing.com"],"hash":-1020957154,"hostnames":["192-3-101-11-host.colocrossing.com"],"ip":3221447947,"ip_str":"192.3.101.11","isp":"ColoCrossing","location":{"area_code":null,"city":"Buffalo","country_code":"US","country_name":"United States","latitude":42.88645,"longitude":-78.87837,"region_code":"NY"},"msrpc":{"actual_count":324,"towers":{"0361ae94-0316-4c6c-8ad8-c594375800e2":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"0497b57d-2e66-424f-a0c6-157cd5d41700":{"annotation":"AppInfo","bindings":[{"ncalrpc":"LRPC-9712c111fa3a8ba8d7"}],"version":"1.0"},"0767a036-0d22-48aa-ba69-b619480f38cb":{"annotation":"PcaSvc","bindings":[{"ncalrpc":"LRPC-d9e6420a1b8276b070"}],"provider":"pcasvc.dll","version":"1.0"},"082a3471-31b6-422a-b931-a54401960c62":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"085b0334-e454-4d91-9b8c-4134f9e793f3":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53":{"bindings":[{"ncalrpc":"LRPC-381eba15863cf8884e"}],"provider":"schedsvc.dll","version":"1.0"},"0b6edbfa-4a24-4fc6-8a23-942b1eca65d1":{"bindings":[{"ncacn_ip_tcp":"192.3.101.11:49670"},{"ncalrpc":"LRPC-a31fbc6a63f9414c61"}],"protocol":"[MS-PAN]: Print System Asynchronous Notification Protocol","provider":"spoolsv.exe","version":"1.0"},"0d3c7f20-1c8d-4654-a1b3-51563b298bda":{"annotation":"UserMgrCli","bindings":[{"ncalrpc":"LRPC-d61b86c8581c05470f"},{"ncalrpc":"OLEB50ECFD719BA2A503F10C86D42D3"}],"version":"1.0"},"0d3e2735-cea0-4ecc-a9e2-41a2d81aed4e":{"bindings":[{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"}],"version":"1.0"},"0d47017b-b33b-46ad-9e18-fe96456c5078":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"0dd94748-2ff1-11ee-be56-0242ac120002":{"bindings":[{"ncalrpc":"LRPC-ab5fa032c54eaf4a34"},{"ncalrpc":"OLE0AE6DC61EBA54B9AAD09EE9094BB"}],"version":"2.0"},"0fc77b1a-95d8-4a2e-a0c0-cff54237462b":{"bindings":[{"ncalrpc":"LRPC-c38b7f7f939bf683ef"},{"ncalrpc":"OLEBD9E33F1563526D374965B9337DB"}],"version":"0.0"},"0ff1f646-13bb-400a-ab50-9a78f2b7a85a":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"12345678-1234-abcd-ef00-0123456789ab":{"bindings":[{"ncacn_ip_tcp":"192.3.101.11:49670"},{"ncalrpc":"LRPC-a31fbc6a63f9414c61"}],"protocol":"[MS-RPRN]: Print System Remote Protocol","provider":"spoolsv.exe","version":"1.0"},"12345778-1234-abcd-ef00-0123456789ac":{"bindings":[{"ncacn_ip_tcp":"192.3.101.11:49664"},{"ncalrpc":"samss lpc"},{"ncalrpc":"SidKey Local End Point"},{"ncalrpc":"protected_storage"},{"ncalrpc":"lsasspirpc"},{"ncalrpc":"lsapolicylookup"},{"ncalrpc":"LSA_EAS_ENDPOINT"},{"ncalrpc":"LSA_IDPEXT_ENDPOINT"},{"ncalrpc":"lsacap"},{"ncalrpc":"LSARPC_ENDPOINT"},{"ncalrpc":"securityevent"},{"ncalrpc":"audit"},{"ncacn_np":"\\pipe\\lsass","netbios":"\\\\WIN-JDPEQD10OQR"}],"protocol":"[MS-SAMR]: Security Account Manager (SAM) Remote Protocol","provider":"samsrv.dll","version":"1.0"},"12e65dd8-887f-41ef-91bf-8d816c42c2e7":{"annotation":"Secure Desktop LRPC interface","bindings":[{"ncalrpc":"WMsgKRpc01FA6523D3"}],"provider":"winlogon.exe","version":"1.0"},"13560fa9-8c09-4b56-a1fd-04d083b9b2a1":{"bindings":[{"ncalrpc":"LRPC-b9d95700f03f1b212f"}],"version":"1.0"},"178d84be-9291-4994-82c6-3f909aca5a03":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"1832bcf6-cab8-41d4-85d2-c9410764f75a":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"1a0d010f-1c33-432c-b0f5-8cf4e8053099":{"annotation":"IdSegSrv service","bindings":[{"ncalrpc":"LRPC-86371bf1350d57c0fd"}],"version":"1.0"},"1b37ca91-76b1-4f5e-a3c7-2abfc61f2bb0":{"bindings":[{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"}],"version":"1.0"},"1ff70682-0a51-30e8-076d-740be8cee98b":{"bindings":[{"ncacn_np":"\\PIPE\\atsvc","netbios":"\\\\WIN-JDPEQD10OQR"},{"ncalrpc":"LRPC-381eba15863cf8884e"}],"protocol":"[MS-TSCH]: Task Scheduler Service Remoting Protocol","provider":"taskcomp.dll","version":"1.0"},"201ef99a-7fa0-444c-9399-19ba84f12a1a":{"annotation":"AppInfo","bindings":[{"ncalrpc":"LRPC-9712c111fa3a8ba8d7"}],"provider":"appinfo.dll","version":"1.0"},"20c40295-8dba-48e6-aebf-3e78ef3bb144":{"bindings":[{"ncalrpc":"OLE26552A490A5B48973A5FE9A74FC2"},{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"}],"version":"2.0"},"2513bcbe-6cd4-4348-855e-7efb3c336dd3":{"bindings":[{"ncalrpc":"OLE26552A490A5B48973A5FE9A74FC2"},{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"}],"version":"2.0"},"29770a8f-829b-4158-90a2-78cd488501f7":{"bindings":[{"ncacn_ip_tcp":"192.3.101.11:49668"},{"ncacn_np":"\\pipe\\SessEnvPublicRpc","netbios":"\\\\WIN-JDPEQD10OQR"},{"ncalrpc":"SessEnvPrivateRpc"},{"ncalrpc":"LRPC-a2983dfd98bcee3bdf"}],"version":"1.0"},"2c7fd9ce-e706-4b40-b412-953107ef9bb0":{"bindings":[{"ncalrpc":"umpo"}],"version":"0.0"},"2d98a740-581d-41b9-aa0d-a88b9d5ce938":{"bindings":[{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"}],"version":"1.0"},"2e6035b2-e8f1-41a7-a044-656b439c4c34":{"annotation":"Proxy Manager provider server endpoint","bindings":[{"ncalrpc":"TeredoControl"},{"ncalrpc":"TeredoDiagnostics"},{"ncalrpc":"LRPC-0297fce2640379526d"}],"version":"1.0"},"2eb08e3e-639f-4fba-97b1-14f878961076":{"annotation":"Group Policy RPC Interface","bindings":[{"ncalrpc":"LRPC-4ab6531290c6b7c417"}],"provider":"gpsvc.dll","version":"1.0"},"2fb92682-6599-42dc-ae13-bd2ca89bd11c":{"annotation":"Fw APIs","bindings":[{"ncalrpc":"LRPC-7107eac8a5e8d1859a"},{"ncalrpc":"LRPC-8378a945b60099208e"},{"ncalrpc":"LRPC-8ea279f95192b4af8d"},{"ncalrpc":"LRPC-9292668da800f2840a"}],"provider":"MPSSVC.dll","version":"1.0"},"30adc50c-5cbc-46ce-9a0e-91914789e23c":{"annotation":"NRP server endpoint","bindings":[{"ncalrpc":"LRPC-c467cacde3ecd79b78"},{"ncalrpc":"DNSResolver"}],"provider":"nrpsrv.dll","version":"1.0"},"30b044a5-a225-43f0-b3a4-e060df91f9c1":{"bindings":[{"ncalrpc":"LRPC-4b0bbfe5bf7417f471"}],"provider":"certprop.dll","version":"1.0"},"33d84484-3626-47ee-8c6f-e7e98b113be1":{"bindings":[{"ncalrpc":"LRPC-c48ba608c62c3e1dad"},{"ncalrpc":"ubpmtaskhostchannel"},{"ncacn_np":"\\PIPE\\atsvc","netbios":"\\\\WIN-JDPEQD10OQR"},{"ncalrpc":"LRPC-381eba15863cf8884e"}],"version":"2.0"},"3473dd4d-2e88-4006-9cba-22570909dd10":{"annotation":"WinHttp Auto-Proxy Service","bindings":[{"ncalrpc":"a7bf55df-3cd7-4036-b9e8-77f769394aa4"},{"ncalrpc":"LRPC-50d9494e48ee4ada88"}],"version":"5.256"},"367abb81-9844-35f1-ad32-98f038001003":{"bindings":[{"ncacn_ip_tcp":"192.3.101.11:49671"}],"protocol":"[MS-SCMR]: Service Control Manager Remote Protocol","provider":"services.exe","version":"2.0"},"378e52b0-c0a9-11cf-822d-00aa0051e40f":{"bindings":[{"ncacn_np":"\\PIPE\\atsvc","netbios":"\\\\WIN-JDPEQD10OQR"},{"ncalrpc":"LRPC-381eba15863cf8884e"}],"protocol":"[MS-TSCH]: Task Scheduler Service Remoting Protocol","provider":"taskcomp.dll","version":"1.0"},"3a9ef155-691d-4449-8d05-09ad57031823":{"bindings":[{"ncacn_ip_tcp":"192.3.101.11:49667"},{"ncalrpc":"LRPC-c48ba608c62c3e1dad"},{"ncalrpc":"ubpmtaskhostchannel"},{"ncacn_np":"\\PIPE\\atsvc","netbios":"\\\\WIN-JDPEQD10OQR"},{"ncalrpc":"LRPC-381eba15863cf8884e"}],"version":"1.0"},"3b338d89-6cfa-44b8-847e-531531bc9992":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5":{"annotation":"DHCP Client LRPC Endpoint","bindings":[{"ncalrpc":"dhcpcsvc"},{"ncalrpc":"dhcpcsvc6"}],"provider":"dhcpcsvc.dll","version":"1.0"},"3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6":{"annotation":"DHCPv6 Client LRPC Endpoint","bindings":[{"ncalrpc":"dhcpcsvc6"}],"provider":"dhcpcsvc6.dll","version":"1.0"},"3f787932-3452-4363-8651-6ea97bb373bb":{"annotation":"NSP Rpc Interface","bindings":[{"ncalrpc":"LRPC-f93641e66d38260bc4"},{"ncalrpc":"OLE67A3F599661ABAAC8AF2CD052E0D"}],"version":"1.0"},"43890c94-bfd7-4655-ad6a-b4a68397cdcb":{"bindings":[{"ncalrpc":"LRPC-3d06b375facfca802e"}],"version":"0.0"},"4a452661-8290-4b36-8fbe-7f4093a94978":{"bindings":[{"ncacn_ip_tcp":"192.3.101.11:49670"},{"ncalrpc":"LRPC-a31fbc6a63f9414c61"}],"provider":"spoolsv.exe","version":"1.0"},"4bec6bb8-b5c2-4b6f-b2c1-5da5cf92d0d9":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"4c9dbf19-d39e-4bb9-90ee-8f7179b20283":{"bindings":[{"ncalrpc":"LRPC-5bc32e2d2f4087aa4f"},{"ncalrpc":"OLEE0E105CEBDC539FFDBD1F448045D"}],"version":"1.0"},"4dace966-a243-4450-ae3f-9b7bcb5315b8":{"bindings":[{"ncalrpc":"umpo"}],"version":"2.0"},"4ed8abcc-f1e2-438b-981f-bb0e8abc010c":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"509bc7ae-77be-4ee8-b07c-0d096bb44345":{"bindings":[{"ncalrpc":"LRPC-09b73b8cefa46d5038"},{"ncalrpc":"OLE0B54C468CC03F7440F105B69ECE1"}],"version":"1.0"},"51a227ae-825b-41f2-b4a9-1ac9557a1018":{"annotation":"Ngc Pop Key Service","bindings":[{"ncacn_ip_tcp":"192.3.101.11:49664"},{"ncalrpc":"samss lpc"},{"ncalrpc":"SidKey Local End Point"},{"ncalrpc":"protected_storage"},{"ncalrpc":"lsasspirpc"},{"ncalrpc":"lsapolicylookup"},{"ncalrpc":"LSA_EAS_ENDPOINT"},{"ncalrpc":"LSA_IDPEXT_ENDPOINT"},{"ncalrpc":"lsacap"},{"ncalrpc":"LSARPC_ENDPOINT"},{"ncalrpc":"securityevent"},{"ncalrpc":"audit"},{"ncacn_np":"\\pipe\\lsass","netbios":"\\\\WIN-JDPEQD10OQR"}],"version":"1.0"},"5222821f-d5e2-4885-84f1-5f6185a0ec41":{"bindings":[{"ncalrpc":"LRPC-7259cef2221e98cf0f"}],"version":"1.0"},"552d076a-cb29-4e44-8b6a-d15e59e2c0af":{"annotation":"IP Transition Configuration endpoint","bindings":[{"ncalrpc":"LRPC-0297fce2640379526d"}],"provider":"iphlpsvc.dll","version":"1.0"},"55e6b932-1979-45d6-90c5-7f6270724112":{"bindings":[{"ncalrpc":"LRPC-646b462ef693e6aacc"},{"ncalrpc":"OLE26552A490A5B48973A5FE9A74FC2"},{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"}],"version":"1.0"},"5824833b-3c1a-4ad2-bdfd-c31d19e23ed2":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"58e604e8-9adb-4d2e-a464-3b0683fb1480":{"annotation":"AppInfo","bindings":[{"ncalrpc":"LRPC-9712c111fa3a8ba8d7"}],"provider":"appinfo.dll","version":"1.0"},"5f54ce7d-5b79-4175-8584-cb65313a0e98":{"annotation":"AppInfo","bindings":[{"ncalrpc":"LRPC-9712c111fa3a8ba8d7"}],"provider":"appinfo.dll","version":"1.0"},"650a7e26-eab8-5533-ce43-9c1dfce11511":{"annotation":"Vpn APIs","bindings":[{"ncalrpc":"LRPC-e1d8102a1766e6ff1d"},{"ncalrpc":"VpnikeRpc"},{"ncalrpc":"RasmanLrpc"},{"ncacn_np":"\\PIPE\\ROUTER","netbios":"\\\\WIN-JDPEQD10OQR"}],"version":"1.0"},"697dcda9-3ba9-4eb2-9247-e11f1901b0d2":{"bindings":[{"ncalrpc":"LRPC-78e0c783ca581d4a13"},{"ncalrpc":"LRPC-6e4b72e1a87bdf102d"},{"ncalrpc":"LRPC-1f2b273cae7d51a86f"},{"ncalrpc":"LRPC-646b462ef693e6aacc"},{"ncalrpc":"OLE26552A490A5B48973A5FE9A74FC2"},{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"}],"version":"1.0"},"6982a06e-5fe2-46b1-b39c-a2c545bfa069":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"6b5bdd1e-528c-422c-af8c-a4079be4fe48":{"annotation":"Remote Fw APIs","bindings":[{"ncacn_ip_tcp":"192.3.101.11:49672"},{"ncalrpc":"ipsec"}],"protocol":"[MS-FASP]: Firewall and Advanced Security Protocol","provider":"FwRemoteSvr.dll","version":"1.0"},"76c217bc-c8b4-4201-a745-373ad9032b1a":{"bindings":[{"ncalrpc":"LRPC-646b462ef693e6aacc"},{"ncalrpc":"OLE26552A490A5B48973A5FE9A74FC2"},{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"}],"version":"1.0"},"76f03f96-cdfd-44fc-a22c-64950a001209":{"bindings":[{"ncacn_ip_tcp":"192.3.101.11:49670"},{"ncalrpc":"LRPC-a31fbc6a63f9414c61"}],"protocol":"[MS-PAR]: Print System Asynchronous Remote Protocol","provider":"spoolsv.exe","version":"1.0"},"76f226c3-ec14-4325-8a99-6a46348418af":{"bindings":[{"ncalrpc":"WindowsShutdown"},{"ncacn_np":"\\PIPE\\InitShutdown","netbios":"\\\\WIN-JDPEQD10OQR"},{"ncalrpc":"WMsgKRpc056F20"},{"ncalrpc":"WMsgKRpc0598D1"},{"ncalrpc":"WMsgKRpc01FA6523D3"}],"provider":"winlogon.exe","version":"1.0"},"7df1ceae-de4e-4e6f-ab14-49636e7c2052":{"bindings":[{"ncalrpc":"LRPC-30c96d8e06acfcc529"}],"version":"1.0"},"7ea70bcf-48af-4f6a-8968-6a440754d5fa":{"annotation":"NSI server endpoint","bindings":[{"ncalrpc":"LRPC-e3f0c96f6cacf958df"}],"provider":"nsisvc.dll","version":"1.0"},"7f1343fe-50a9-4927-a778-0c5859517bac":{"annotation":"DfsDs service","bindings":[{"ncacn_np":"\\PIPE\\wkssvc","netbios":"\\\\WIN-JDPEQD10OQR"},{"ncalrpc":"LRPC-25a6a189e765527b5e"}],"version":"1.0"},"7f9d11bf-7fb9-436b-a812-b2d50c5d4c03":{"annotation":"Fw APIs","bindings":[{"ncalrpc":"LRPC-8ea279f95192b4af8d"},{"ncalrpc":"LRPC-9292668da800f2840a"}],"provider":"MPSSVC.dll","version":"1.0"},"857fb1be-084f-4fb5-b59c-4b2c4be5f0cf":{"bindings":[{"ncalrpc":"OLE26552A490A5B48973A5FE9A74FC2"},{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"}],"version":"1.0"},"86d35949-83c9-4044-b424-db363231fd0c":{"bindings":[{"ncacn_ip_tcp":"192.3.101.11:49667"},{"ncalrpc":"LRPC-c48ba608c62c3e1dad"},{"ncalrpc":"ubpmtaskhostchannel"},{"ncacn_np":"\\PIPE\\atsvc","netbios":"\\\\WIN-JDPEQD10OQR"},{"ncalrpc":"LRPC-381eba15863cf8884e"}],"protocol":"[MS-TSCH]: Task Scheduler Service Remoting Protocol","provider":"schedsvc.dll","version":"1.0"},"8782d3b9-ebbd-4644-a3d8-e8725381919b":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"880fd55e-43b9-11e0-b1a8-cf4edfd72085":{"annotation":"KAPI Service endpoint","bindings":[{"ncalrpc":"LRPC-22b6d9ccfafa8d9eab"},{"ncalrpc":"OLEFE843B2897F64996B90902879156"},{"ncalrpc":"LRPC-3ff12db1c383fea653"}],"version":"1.0"},"88abcbc3-34ea-76ae-8215-767520655a23":{"bindings":[{"ncalrpc":"LRPC-646b462ef693e6aacc"},{"ncalrpc":"OLE26552A490A5B48973A5FE9A74FC2"},{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"}],"version":"0.0"},"8bfc3be1-6def-4e2d-af74-7c47cd0ade4a":{"bindings":[{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"}],"version":"1.0"},"8ec21e98-b5ce-4916-a3d6-449fa428a007":{"bindings":[{"ncalrpc":"LRPC-c38b7f7f939bf683ef"},{"ncalrpc":"OLEBD9E33F1563526D374965B9337DB"}],"version":"0.0"},"8fb74744-b2ff-4c00-be0d-9ef9a191fe1b":{"annotation":"Ngc Pop Key Service","bindings":[{"ncacn_ip_tcp":"192.3.101.11:49664"},{"ncalrpc":"samss lpc"},{"ncalrpc":"SidKey Local End Point"},{"ncalrpc":"protected_storage"},{"ncalrpc":"lsasspirpc"},{"ncalrpc":"lsapolicylookup"},{"ncalrpc":"LSA_EAS_ENDPOINT"},{"ncalrpc":"LSA_IDPEXT_ENDPOINT"},{"ncalrpc":"lsacap"},{"ncalrpc":"LSARPC_ENDPOINT"},{"ncalrpc":"securityevent"},{"ncalrpc":"audit"},{"ncacn_np":"\\pipe\\lsass","netbios":"\\\\WIN-JDPEQD10OQR"}],"version":"1.0"},"906b0ce0-c70b-1067-b317-00dd010662da":{"bindings":[{"ncalrpc":"LRPC-ef1df0ed30b96c82a8"},{"ncalrpc":"LRPC-ef1df0ed30b96c82a8"},{"ncalrpc":"LRPC-ef1df0ed30b96c82a8"}],"protocol":"[MS-CMPO]: MSDTC Connection Manager:","provider":"msdtcprx.dll","version":"1.0"},"95095ec8-32ea-4eb0-a3e2-041f97b36168":{"bindings":[{"ncalrpc":"LRPC-5bc32e2d2f4087aa4f"},{"ncalrpc":"OLEE0E105CEBDC539FFDBD1F448045D"}],"version":"1.0"},"95406f0b-b239-4318-91bb-cea3a46ff0dc":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"98716d03-89ac-44c7-bb8c-285824e51c4a":{"annotation":"XactSrv service","bindings":[{"ncalrpc":"LRPC-86371bf1350d57c0fd"}],"provider":"srvsvc.dll","version":"1.0"},"98cd761e-e77d-41c8-a3c0-0fb756d90ec2":{"bindings":[{"ncalrpc":"LRPC-5bc32e2d2f4087aa4f"},{"ncalrpc":"OLEE0E105CEBDC539FFDBD1F448045D"}],"version":"1.0"},"9b008953-f195-4bf9-bde0-4471971e58ed":{"bindings":[{"ncalrpc":"LRPC-6e4b72e1a87bdf102d"},{"ncalrpc":"LRPC-1f2b273cae7d51a86f"},{"ncalrpc":"LRPC-646b462ef693e6aacc"},{"ncalrpc":"OLE26552A490A5B48973A5FE9A74FC2"},{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"}],"version":"1.0"},"a398e520-d59a-4bdd-aa7a-3c1e0303a511":{"annotation":"IKE/Authip API","bindings":[{"ncalrpc":"LRPC-87953a9d5d220c7fce"}],"provider":"IKEEXT.DLL","version":"1.0"},"a4b8d482-80ce-40d6-934d-b22a01a44fe7":{"annotation":"LicenseManager","bindings":[{"ncalrpc":"LicenseServiceEndpoint"}],"version":"1.0"},"a500d4c6-0dd1-4543-bc0c-d5f93486eaf8":{"bindings":[{"ncalrpc":"LRPC-cd0c17746235190007"},{"ncalrpc":"LRPC-08ba6c6c94be8f43dc"}],"version":"1.0"},"abfb6ca3-0c5e-4734-9285-0aee72fe8d1c":{"bindings":[{"ncalrpc":"LRPC-b9d95700f03f1b212f"}],"version":"1.0"},"ae33069b-a2a8-46ee-a235-ddfd339be281":{"bindings":[{"ncacn_ip_tcp":"192.3.101.11:49670"},{"ncalrpc":"LRPC-a31fbc6a63f9414c61"}],"protocol":"[MS-PAN]: Print System Asynchronous Notification Protocol","provider":"spoolsv.exe","version":"1.0"},"b18fbab6-56f8-4702-84e0-41053293a869":{"annotation":"UserMgrCli","bindings":[{"ncalrpc":"LRPC-d61b86c8581c05470f"},{"ncalrpc":"OLEB50ECFD719BA2A503F10C86D42D3"}],"version":"1.0"},"b1ef227e-dfa5-421e-82bb-67a6a129c496":{"bindings":[{"ncalrpc":"LRPC-c38b7f7f939bf683ef"},{"ncalrpc":"OLEBD9E33F1563526D374965B9337DB"}],"version":"0.0"},"b25a52bf-e5dd-4f4a-aea6-8ca7272a0e86":{"annotation":"KeyIso","bindings":[{"ncacn_ip_tcp":"192.3.101.11:49664"},{"ncalrpc":"samss lpc"},{"ncalrpc":"SidKey Local End Point"},{"ncalrpc":"protected_storage"},{"ncalrpc":"lsasspirpc"},{"ncalrpc":"lsapolicylookup"},{"ncalrpc":"LSA_EAS_ENDPOINT"},{"ncalrpc":"LSA_IDPEXT_ENDPOINT"},{"ncalrpc":"lsacap"},{"ncalrpc":"LSARPC_ENDPOINT"},{"ncalrpc":"securityevent"},{"ncalrpc":"audit"},{"ncacn_np":"\\pipe\\lsass","netbios":"\\\\WIN-JDPEQD10OQR"}],"version":"2.0"},"b37f900a-eae4-4304-a2ab-12bb668c0188":{"bindings":[{"ncalrpc":"LRPC-b9d95700f03f1b212f"}],"version":"1.0"},"b58aa02e-2884-4e97-8176-4ee06d794184":{"bindings":[{"ncalrpc":"LRPC-116e5fbe7842eb7192"}],"provider":"sysmain.dll","version":"1.0"},"bdaa0970-413b-4a3e-9e5d-f6dc9d7e0760":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"bf4dc912-e52f-4904-8ebe-9317c1bdd497":{"bindings":[{"ncalrpc":"LRPC-e59bd6493fcd65389d"},{"ncalrpc":"OLE6953FF04EF70DA2ECFD92F123A30"}],"version":"1.0"},"c2d1b5dd-fa81-4460-9dd6-e7658b85454b":{"bindings":[{"ncalrpc":"LRPC-b9d95700f03f1b212f"}],"version":"1.0"},"c36be077-e14b-4fe9-8abc-e856ef4f048b":{"annotation":"Proxy Manager client server endpoint","bindings":[{"ncalrpc":"TeredoControl"},{"ncalrpc":"TeredoDiagnostics"},{"ncalrpc":"LRPC-0297fce2640379526d"}],"version":"1.0"},"c49a5a70-8a7f-4e70-ba16-1e8f1f193ef1":{"annotation":"Adh APIs","bindings":[{"ncalrpc":"TeredoControl"},{"ncalrpc":"TeredoDiagnostics"},{"ncalrpc":"LRPC-0297fce2640379526d"}],"version":"1.0"},"c521facf-09a9-42c5-b155-72388595cbf0":{"bindings":[{"ncalrpc":"umpo"}],"version":"0.0"},"c605f9fb-f0a3-4e2a-a073-73560f8d9e3e":{"bindings":[{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"}],"version":"1.0"},"c8ba73d2-3d55-429c-8e9a-c44f006f69fc":{"bindings":[{"ncalrpc":"LRPC-3d06b375facfca802e"}],"version":"0.0"},"c9ac6db5-82b7-4e55-ae8a-e464ed7b4277":{"annotation":"Impl friendly name","bindings":[{"ncalrpc":"LRPC-ed3bfbab191b42498b"},{"ncalrpc":"IUserProfile2"},{"ncalrpc":"LRPC-c216e136a8aaafcbbf"},{"ncalrpc":"LRPC-359df7f63f413f67e7"},{"ncalrpc":"senssvc"},{"ncalrpc":"LRPC-a2983dfd98bcee3bdf"}],"provider":"sysntfy.dll","version":"1.0"},"d09bdeb5-6171-4a34-bfe2-06fa82652568":{"bindings":[{"ncalrpc":"csebpub"},{"ncalrpc":"LRPC-78e0c783ca581d4a13"},{"ncalrpc":"LRPC-6e4b72e1a87bdf102d"},{"ncalrpc":"LRPC-1f2b273cae7d51a86f"},{"ncalrpc":"LRPC-646b462ef693e6aacc"},{"ncalrpc":"OLE26552A490A5B48973A5FE9A74FC2"},{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"},{"ncalrpc":"LRPC-6e4b72e1a87bdf102d"},{"ncalrpc":"LRPC-1f2b273cae7d51a86f"},{"ncalrpc":"LRPC-646b462ef693e6aacc"},{"ncalrpc":"OLE26552A490A5B48973A5FE9A74FC2"},{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"},{"ncalrpc":"LRPC-1f2b273cae7d51a86f"},{"ncalrpc":"LRPC-646b462ef693e6aacc"},{"ncalrpc":"OLE26552A490A5B48973A5FE9A74FC2"},{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"},{"ncalrpc":"LRPC-3ff12db1c383fea653"},{"ncalrpc":"LRPC-08ba6c6c94be8f43dc"}],"version":"1.0"},"d22895ef-aff4-42c5-a5b2-b14466d34ab4":{"bindings":[{"ncalrpc":"LRPC-5bc32e2d2f4087aa4f"},{"ncalrpc":"OLEE0E105CEBDC539FFDBD1F448045D"}],"version":"1.0"},"d249bd56-4cc0-4fd3-8ce6-6fe050d590cb":{"bindings":[{"ncalrpc":"LRPC-9d0232a1fd77b31d65"}],"version":"0.0"},"d4051bde-9cdd-4910-b393-4aa85ec3c482":{"bindings":[{"ncalrpc":"LRPC-5bc32e2d2f4087aa4f"},{"ncalrpc":"OLEE0E105CEBDC539FFDBD1F448045D"}],"version":"1.0"},"d8140e00-5c46-4ae6-80ac-2f9a76df224c":{"bindings":[{"ncalrpc":"LRPC-9d0232a1fd77b31d65"}],"version":"0.0"},"d95afe70-a6d5-4259-822e-2c84da1ddb0d":{"bindings":[{"ncacn_ip_tcp":"192.3.101.11:49665"},{"ncalrpc":"WindowsShutdown"},{"ncacn_np":"\\PIPE\\InitShutdown","netbios":"\\\\WIN-JDPEQD10OQR"},{"ncalrpc":"WMsgKRpc056F20"}],"protocol":"[MS-RSP]: Remote Shutdown Protocol","provider":"wininit.exe","version":"1.0"},"dd490425-5325-4565-b774-7e27d6c09c24":{"annotation":"Base Firewall Engine API","bindings":[{"ncalrpc":"LRPC-9292668da800f2840a"}],"provider":"BFE.DLL","version":"1.0"},"dd59071b-3215-4c59-8481-972edadc0f6a":{"bindings":[{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"}],"version":"1.0"},"e38f5360-8572-473e-b696-1b46873beeab":{"bindings":[{"ncalrpc":"LRPC-5bc32e2d2f4087aa4f"},{"ncalrpc":"OLEE0E105CEBDC539FFDBD1F448045D"}],"version":"1.0"},"e40f7b57-7a25-4cd3-a135-7f7d3df9d16b":{"bindings":[{"ncalrpc":"LRPC-9214777306fb7397f9"}],"version":"1.0"},"e53d94ca-7464-4839-b044-09a2fb8b3ae5":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"e8748f69-a2a4-40df-9366-62dbeb696e26":{"bindings":[{"ncalrpc":"LRPC-3d06b375facfca802e"}],"version":"0.0"},"eb081a0d-10ee-478a-a1dd-50995283e7a8":{"annotation":"Witness Client Test Interface","bindings":[{"ncalrpc":"LRPC-25a6a189e765527b5e"}],"version":"3.0"},"f2c9b409-c1c9-4100-8639-d8ab1486694a":{"annotation":"Witness Client Upcall Server","bindings":[{"ncalrpc":"LRPC-25a6a189e765527b5e"}],"version":"1.0"},"f3f09ffd-fbcf-4291-944d-70ad6e0e73bb":{"bindings":[{"ncalrpc":"LRPC-a6bfb4eea34a4ccc23"},{"ncalrpc":"LRPC-5b8696222a82714d33"}],"version":"1.0"},"f44e62af-dab1-44c2-8013-049a9de417d6":{"bindings":[{"ncalrpc":"LRPC-b9d95700f03f1b212f"}],"version":"1.0"},"f47433c3-3e9d-4157-aad4-83aa1f5c2d4c":{"annotation":"Fw APIs","bindings":[{"ncalrpc":"LRPC-8378a945b60099208e"},{"ncalrpc":"LRPC-8ea279f95192b4af8d"},{"ncalrpc":"LRPC-9292668da800f2840a"}],"version":"1.0"},"f6beaff7-1e19-4fbb-9f8f-b89e2018337c":{"annotation":"Event log TCPIP","bindings":[{"ncacn_ip_tcp":"192.3.101.11:49666"},{"ncacn_np":"\\pipe\\eventlog","netbios":"\\\\WIN-JDPEQD10OQR"},{"ncalrpc":"eventlog"}],"protocol":"[MS-EVEN6]: EventLog Remoting Protocol","provider":"wevtsvc.dll","version":"1.0"},"fae436b0-b864-4a87-9eda-298547cd82f2":{"bindings":[{"ncalrpc":"umpo"}],"version":"1.0"},"fc48cd89-98d6-4628-9839-86f7a3e4161a":{"bindings":[{"ncalrpc":"dabrpc"},{"ncalrpc":"csebpub"},{"ncalrpc":"LRPC-78e0c783ca581d4a13"},{"ncalrpc":"LRPC-6e4b72e1a87bdf102d"},{"ncalrpc":"LRPC-1f2b273cae7d51a86f"},{"ncalrpc":"LRPC-646b462ef693e6aacc"},{"ncalrpc":"OLE26552A490A5B48973A5FE9A74FC2"},{"ncalrpc":"LRPC-b72d5e7e5d6e2b0f1d"},{"ncalrpc":"actkernel"},{"ncalrpc":"umpo"}],"version":"1.0"},"fd7a0523-dc70-43dd-9b2e-9c5ed48225b1":{"annotation":"AppInfo","bindings":[{"ncalrpc":"LRPC-9712c111fa3a8ba8d7"}],"provider":"appinfo.dll","version":"1.0"},"fd8be72b-a9cd-4b2c-a9ca-4ded242fbe4d":{"bindings":[{"ncalrpc":"LRPC-5bc32e2d2f4087aa4f"},{"ncalrpc":"OLEE0E105CEBDC539FFDBD1F448045D"}],"version":"1.0"}}},"opts":{"raw":"05000c03100000003c00000001000000b810b810e443000004003133350000000100000000000000045d888aeb1cc9119fe808002b10486002000000"},"org":"ColoCrossing","os":null,"port":135,"product":"Microsoft RPC Endpoint Mapper","timestamp":"2023-10-20T23:23:08.794356","transport":"tcp"},{"_shodan":{"crawler":"cdd92e2d835a37d2798fa6c7105171f4d214012f","id":"520fbbc3-8a31-48da-b8d0-3402bc866540","module":"http-simple-new","options":{},"ptr":true,"region":"eu"},"asn":"AS36352","data":"HTTP/1.1 404 Not Found\r\nContent-Type: text/html; charset=us-ascii\r\nServer: Microsoft-HTTPAPI/2.0\r\nDate: Sat, 28 Oct 2023 09:58:51 GMT\r\nConnection: close\r\nContent-Length: 315\r\n\r\n\nWinRM NTLM Info:\n OS: Windows Server 2022\n OS Build: 10.0.20348\n Target Name: WIN-JDPEQD10OQR\n NetBIOS Domain Name: WIN-JDPEQD10OQR\n NetBIOS Computer Name: WIN-JDPEQD10OQR\n DNS Domain Name: WIN-JDPEQD10OQR\n FQDN: WIN-JDPEQD10OQR\n","domains":["colocrossing.com"],"hash":-623361125,"hostnames":["192-3-101-11-host.colocrossing.com"],"http":{"components":{},"headers_hash":1163425937,"host":"192.3.101.11","html":"<!DOCTYPE HTML PUBLIC \"-//W3C//DTD HTML 4.01//EN\"\"http://www.w3.org/TR/html4/strict.dtd\">\r\n<HTML><HEAD><TITLE>Not Found</TITLE>\r\n<META HTTP-EQUIV=\"Content-Type\" Content=\"text/html; charset=us-ascii\"></HEAD>\r\n<BODY><h2>Not Found</h2>\r\n<hr><p>HTTP Error 404. The requested resource is not found.</p>\r\n</BODY></HTML>\r\n","html_hash":1489525118,"location":"/","redirects":[],"robots":null,"robots_hash":null,"securitytxt":null,"securitytxt_hash":null,"server":"Microsoft-HTTPAPI/2.0","sitemap":null,"sitemap_hash":null,"status":404,"title":"Not Found"},"ip":3221447947,"ip_str":"192.3.101.11","isp":"ColoCrossing","location":{"area_code":null,"city":"Buffalo","country_code":"US","country_name":"United States","latitude":42.88645,"longitude":-78.87837,"region_code":"NY"},"ntlm":{"dns_domain_name":"WIN-JDPEQD10OQR","fqdn":"WIN-JDPEQD10OQR","netbios_computer_name":"WIN-JDPEQD10OQR","netbios_domain_name":"WIN-JDPEQD10OQR","os":["Windows Server 2022"],"os_build":"10.0.20348","target_realm":"WIN-JDPEQD10OQR","timestamp":133429607319335490},"opts":{},"org":"ColoCrossing","os":"Windows Server 2022 (build 10.0.20348)","port":5985,"product":"WinRM","timestamp":"2023-10-28T09:58:51.375624","transport":"tcp"}],"domains":["colocrossing.com"],"hostnames":["192-3-101-11-host.colocrossing.com"],"ip":3221447947,"ip_str":"192.3.101.11","isp":"ColoCrossing","last_update":"2023-10-28T09:58:51.375624","latitude":42.88645,"longitude":-78.87837,"org":"ColoCrossing","os":"Windows Server 2022 (build 10.0.20348)","ports":[5985,135],"region_code":"NY","tags":[]}CISCO IOCs (from Talos Blog)
5.149.249.74
154.53.56.231
154.53.63.93
Usernames:
cisco_tac_admin
cisco_support
cisco_sys_manager
All Suspected TA IPs
5.149.249.74
192.227.196.186
209.141.37.176
192.3.101.11
154.12.241.49
154.53.56.231
79.141.160.158
192.3.101.111
154.53.63.93
45.61.160.225
95.168.191.172
198.244.135.233
92.38.132.181
192.3.23.246
137.74.75.69
172.86.98.0
23.108.57.149
92.38.169.180
209.141.50.193
209.141.34.83
172.86.123.115
198.46.129.134
91.193.19.142
87.251.70.29
185.45.195.167
92.38.149.128
51.222.194.221
93.174.89.36
104.255.168.247
185.153.196.30
192.109.119.29
82.118.235.109
198.12.114.59
23.81.246.230
104.194.129.165
107.172.93.3
205.185.123.17
107.172.93.29
108.177.235.177
92.223.30.129
89.248.168.72
94.102.50.143
94.102.59.7
185.163.47.176
108.62.118.70
213.227.154.70
209.141.51.4
94.102.50.156
80.82.79.180
93.174.89.40
94.102.49.35
94.102.49.104
199.195.249.223
199.195.249.22
107.189.12.103
173.234.155.154
192.109.119.16
5.8.41.70
109.94.164.64
109.94.164.56
93.174.89.226
85.204.116.121
66.94.98.137
142.234.157.233







