Education
Education
There’s thousand of vulnerabilities, but do you ever struggle work out what ones might actually be useful to you if you are defending or attacking?
Well don’t worry I’ve started to document some things that might help you both attack and defend in CYBERSPACE!
CVE ID
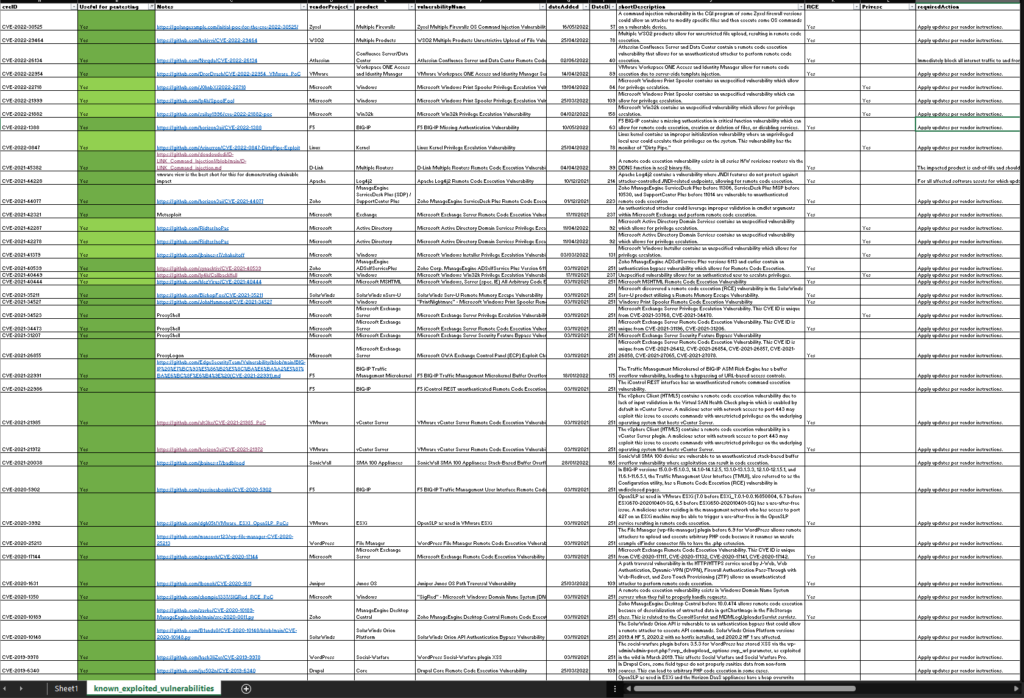
Now this is a snipped of what I’m working on, but I wanted to at least start the ball rolling. If you have any of these in your environment you probably want to be getting them bumped up the priority list ASAP.
- CVE-2022-30525
- CVE-2022-29464
- CVE-2022-26134
- CVE-2022-22954
- CVE-2022-22718
- CVE-2022-21999
- CVE-2022-21882
- CVE-2022-1388
- CVE-2022-0847
- CVE-2021-45382
- CVE-2021-44228
- CVE-2021-44077
- CVE-2021-42321
- CVE-2021-42287
- CVE-2021-42278
- CVE-2021-41379
- CVE-2021-40539
- CVE-2021-40449
- CVE-2021-40444
- CVE-2021-35211
- CVE-2021-34527
- CVE-2021-34523
- CVE-2021-34473
- CVE-2021-31207
- CVE-2021-26855
- CVE-2021-22991
- CVE-2021-22986
- CVE-2021-21985
- CVE-2021-21972
- CVE-2021-20038
- CVE-2020-5902
- CVE-2020-3992
- CVE-2020-25213
- CVE-2020-17144
- CVE-2020-1631
- CVE-2020-1350
- CVE-2020-10189
- CVE-2020-10148
- CVE-2019-9978
- CVE-2019-6340
- CVE-2019-5544
- CVE-2019-3398
- CVE-2019-3396
- CVE-2019-19781
- CVE-2019-1579
- CVE-2019-11581
- CVE-2019-11580
- CVE-2019-11510
- CVE-2019-0708
- CVE-2018-6961
- CVE-2018-13379
- CVE-2017-5689
- CVE-2017-0146
- CVE-2017-0143
This is just the start, I’m going to look at how we can do more with this:
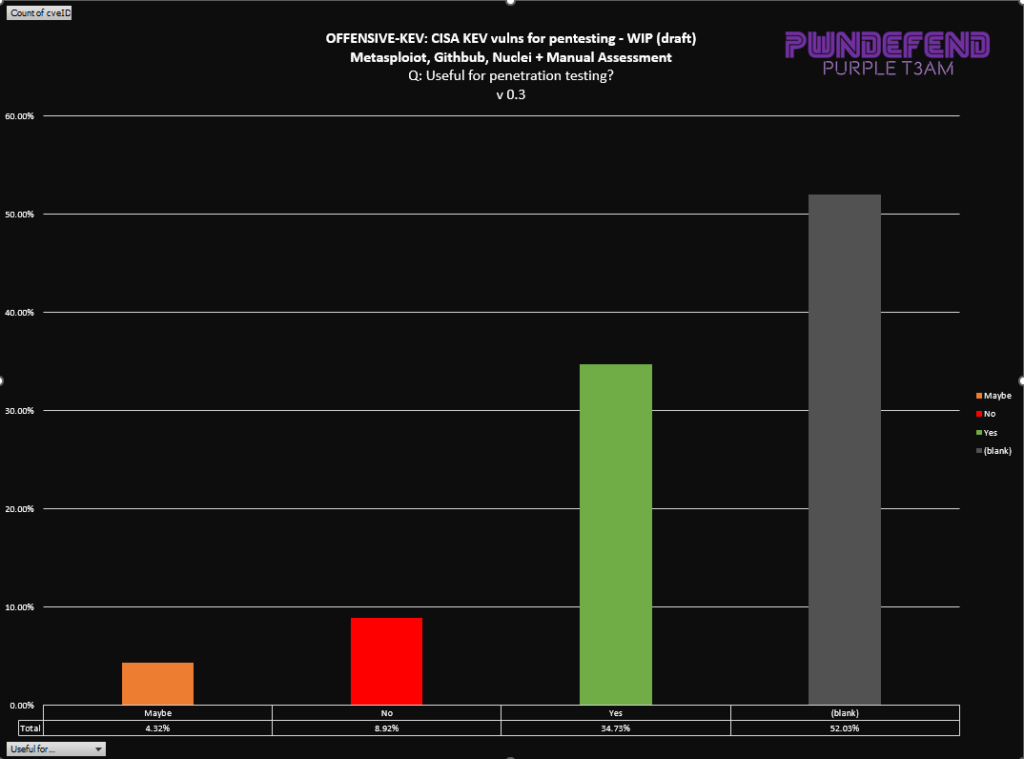
Hopefully this gives some idea that even though there are thousands of vulns, and over 700 in CISA KEV, you might find some need more attention than others!
The CVSS score of a vuln is one thing, knowing if there is a public exploit, a private one and how much of a target it is for exploit developes, nation states and cybercriminals helps guide this.
Criteria for Offensive KEV
The way I’m looking at this is:
- Is a public exploit available?
- Is the product in question largely deploed globally?
- Is this RCE or Privesc?
- How old is it?
- Is the exploit “probably” useful for an attacker?
if it’s NOT on my list it doesn’t mean don’t remediate, patch, mitigate ect. I’m just looking at this from a pentesters perspective to try and work out what I probably can leverage vs it existing.
Latest Update – 09-08-2022
So far we have now added in:
- Metasploit modules where there is a CVE referenced.
- Nuclei templates
- Manual additions where a public POC is mentioned
- Manual Limited assessment of data to see if the vuln would likely be useful for a pentestration test