 Defense
Defense
Scams, Disinformation & Supply Chain Compromise
Now this might come to a shock to some of you but I’m not actually (as my LinkedIn profile currently says) Tony Stark! I know, shocking but it’s true. Why I’m experimenting with this will hopefully be apparent after reading this post (although this isn’t an explanation specifically). What I’m looking at is how deception is used from a range of perspectives from marketing, cybercrime and how we can use deception in a positive way, to actively defend ourselves from the cyber criminals!
Clarity in a digital world
When we think about risks both or personal and organisational nature, whilst the fundamental principles of crime and deception haven’t changed, I’d say the tools of the trade and effectiveness have. What we see and hear we can trust, right? Unfortunately, it doesn’t quite work like that, and the landscape of deception is advancing, we now have:
- Machine Generated Photos
- Machine Altered Videos (deepfakes)
The barrier to entry to conduct deceptive acts is now more than ever low, marketing techniques used by legitimate organisations now sometimes are a mirror of criminal actors, I’ll give you some personal examples (I’ll spare the blushes from the sending organisations):
- I get emails from companies using names of people in the FROM field to show generic emails are coming from known industry names such as Microsoft Most Valued Professionals.
- Whitepapers and reports are hidden behind data walls (often you must submit your email address and some company information)
- I get emails from suppliers/service providers congratulating me on winning the opportunity to apply to things.
I’ll be honest It feels like the social engineering fatigue for me is from the “goodies” rather than the baddies as it were. Alas that however isn’t a fairly reflection, my spam filters and personal limitation of email use give me a bias in that respect. I do however have an immersed view in technology and cyber security so hopefully my inputs are reliable.
Life of Crime
How much of a problem do scams, phishing, and disinformation pose? From stealing your credentials through to swaying elections this risk landscape is huge. But how does this work on a day-to-day basis?
Monitoring fake news, deception etc. is beyond the scope of this post, but knowing what’s real and what is not certainly to me isn’t so simple:
- Phishing Emails (Deception)
- Typo squatting (Deception)
- Account Takeovers/Supply Chain Compromise
These are all lots more, we see SMS, Postal Mail and telephones used by both organisations and businesses to enable communication with their customers/victims.
Well according to Kaspersky 23.7% of “attacks” use malicious email (Incident Response Analyst Report 2021)
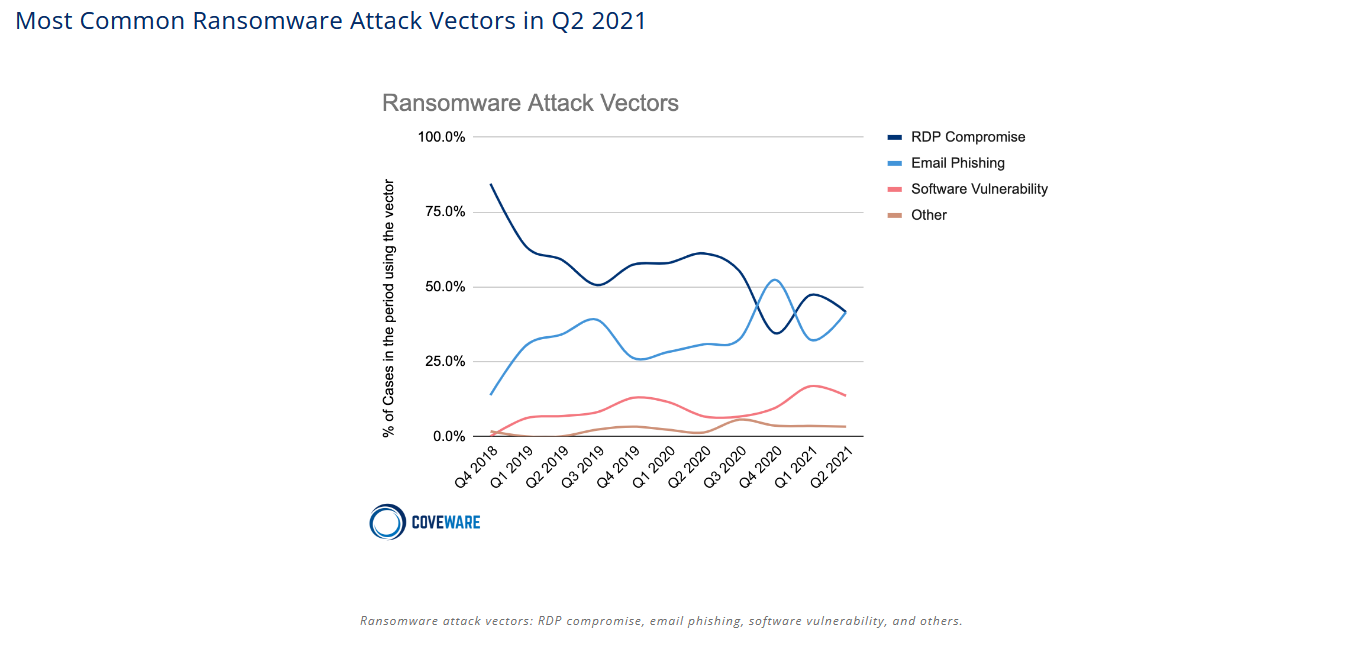
I don’t like using just one data source so let’s turn to Coveware to look at Ransomware analysis. Email is certainly a big part of the cybercrime game and as such part of the deception game, however you might not agree that marketing emails fall into the category of deception but from my pov some of them certainly look deceptive to me.
Regardless of that view, one particular risk that I see affect organisations is supply chain compromise in the form of “Business Email Compromise” (BEC) and on social media specifically we see account takeovers abused by scammers.
In these scenarios both the affected person, organisation and downstream recipients can be affected. Earlier in the year I was dealing with a failed BEC scenario where a supplier was compromised, they used the compromised mailbox to credential harvest (phish/steal credentials) from one of their customers. Then the threat actor pivoted to attempt fraud to a customer of the customer. All these things involve some form of deception and spotting them isn’t always “simple”.
So, from my point of view deception is a key ingredient used by both marketing and criminals to conduct activities.
Defensive Deception
So, both goodies and baddies use social engineering and deception in their toolkits, however what we’ve looked at so far is marketing and crime. What about if we think about deception from a more active cyber defence perspective?
Common scenarios for defensive cyber deception include:
- Honeypots /Decoys – systems used to attract, and resource consume attackers/to gain Cyber Threat Intelligence data
- Canaries – Crafted alerts to monitor for specific activity e.g., embedding a canary account or document in a system to “alarm” on access.
An area that also exists is disinformation for defensive purposes. Essentially leveraging social media and internet services to deploy virtual “chaff” into the world. Now these are often deployed for research, but less so do I see these techniques widely adopted across organisations for active cyber defence (outside of the CTI world)
So, when we consider cyber posture maturity, once we’ve deployed network-based systems etc. A natural evolution of this could be to deploy digital chaff (I’m not a fan of over militarization of terms but this to me works – feel free to offer other analogies).
When we conduct OSINT against organisations, we often find a vast level of sensitive and useful data that aids attackers, it may be wise as we continue in this cyber world for these deception techniques to gain wider adoption.
Luckily I’m not the only one that thinks like this – check out: https://www.cyberdeception.org.uk/ they are doing some cool work in this space!
Because as we know, what you see and hear, well it’s not always real! Time to get back to Stark Labs! 









