 Defense
Defense
Sensational Press or Cyber War Mongering?
I do not know Mr Martin, but I would assume that his role at NCSC and GCHQ would have given him a good insight into the realities of cybercrime, cyber terrorism, nation state affairs and how to effectively defend against cyber criminals (and other threat actors) so please read this blog as it is intended, it’s an analysis on the quoted statements and reporting style and general view of mine about current cyber war rhetoric, not an analysis of the person. Why am I writing this? Well, I am seeing an increased level of FUD, snake oil and cyber war rhetoric and I wanted to share some of my thoughts, opinions, and ideas in this space. For it is far too easy to call for war and in cyberspace do we even know what that means?
In a recent Telegraph article Mr Martin has been quoted and the headlines (sensational?) is as follows:
“Former spy chief calls for military cyber-attacks on ransomware hackers”
My View on quoted statements
Firstly, I need to consider that these are likely quotes from a far more detailed interview, and these have been selected for impact.
Mr Martin said: “I actually think that disruption of infrastructure, what you might call a cyber-attack, is justified.”
- We already disrupt the infrastructure, we take down c2 servers, we take down pwn3d servers through legal abuse requests. We get criminal infra added to block lists.
“GCHQ or the military could use their own hacking abilities to shut down the servers and tools used by the most determined and damaging criminal groups”
- Criminal groups do not require military intervention in domestic scenarios. What makes this any different? Aside from the resources, skills and complexity of the scenarios, do we send the military in when someone’s mobile phone is stolen or a house is burgled?
The use of cyber-attacks should not be the Government’s initial response to ransomware incidents, Mr Martin said, but should be considered if other options have failed.
- We already do this do we not?
“The use of disruptive attacks against ransomware is for the really big scale operations, the ones you just can’t take down.
- Recently we’ve seen law enforcement have massive wins in taking these down through policing.
You will not be able to do it on every ransomware gang and if you did, you’d probably start making mistakes. You’d probably start hitting innocent people.”
- Not probably, definitely. The infra that we see hitting organisations is victim infrastructure or benign infrastructure being used for malicious purposes. They have access to vast networks or cross organisational resources.
Recent Articles on the press about Cyber War and Hacking Back
Strangely these are published by the same author on the same day. The second article whilst headline is in my view sensationalist actually paints a slightly more balanced view, it includes more quotes from Mr Martin that for me show a fare more nuanced view. I suspect that he has been quoted in a way to suit the narrative but who knows that’s pure speculation on my part.
Google Trends
Because I am very conscious that my view on the world is just that, a single grain of sand in the world view, so I think it is good to explore, I talk to people, watch videos and read articles to try and get some balance in the world.
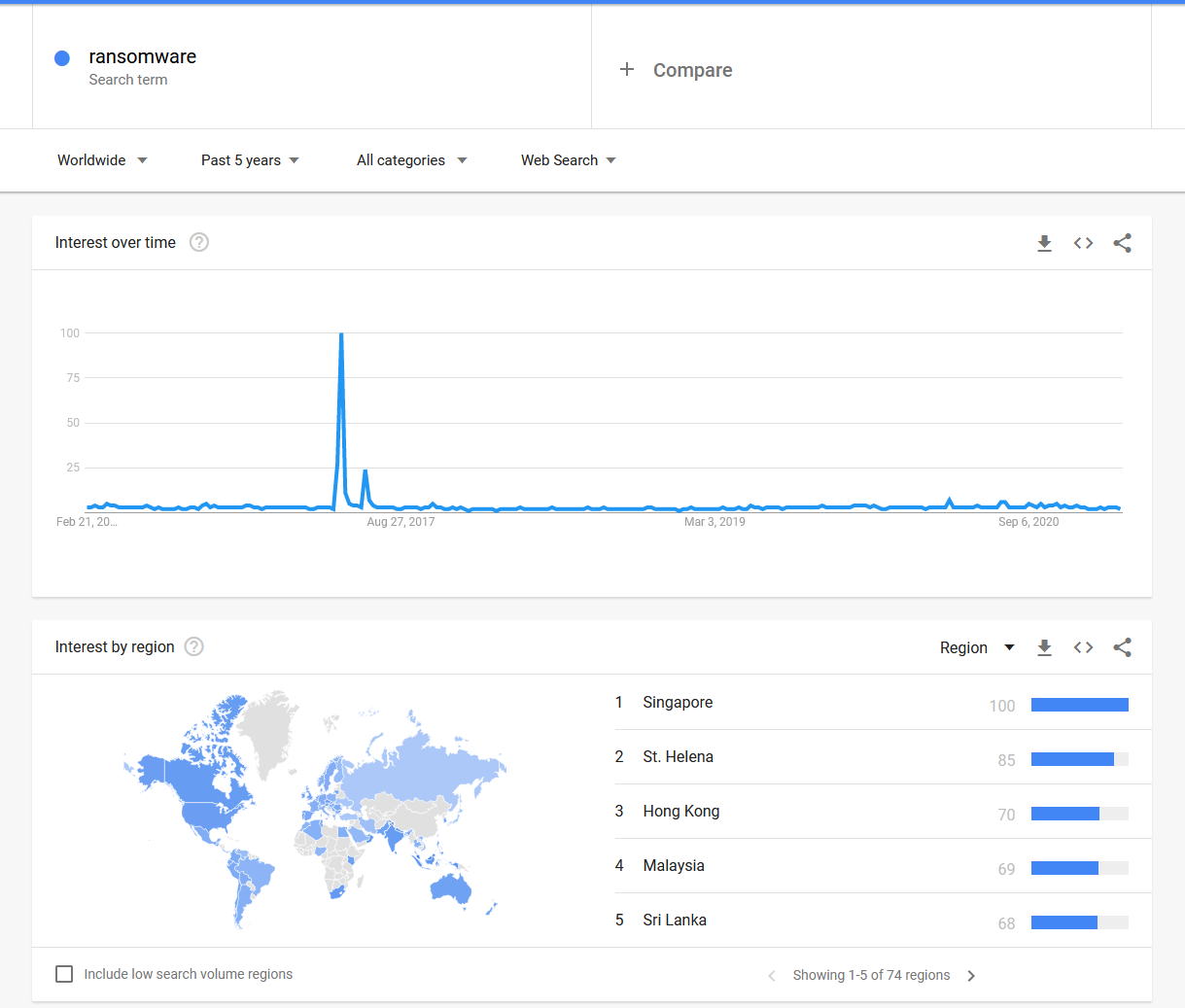
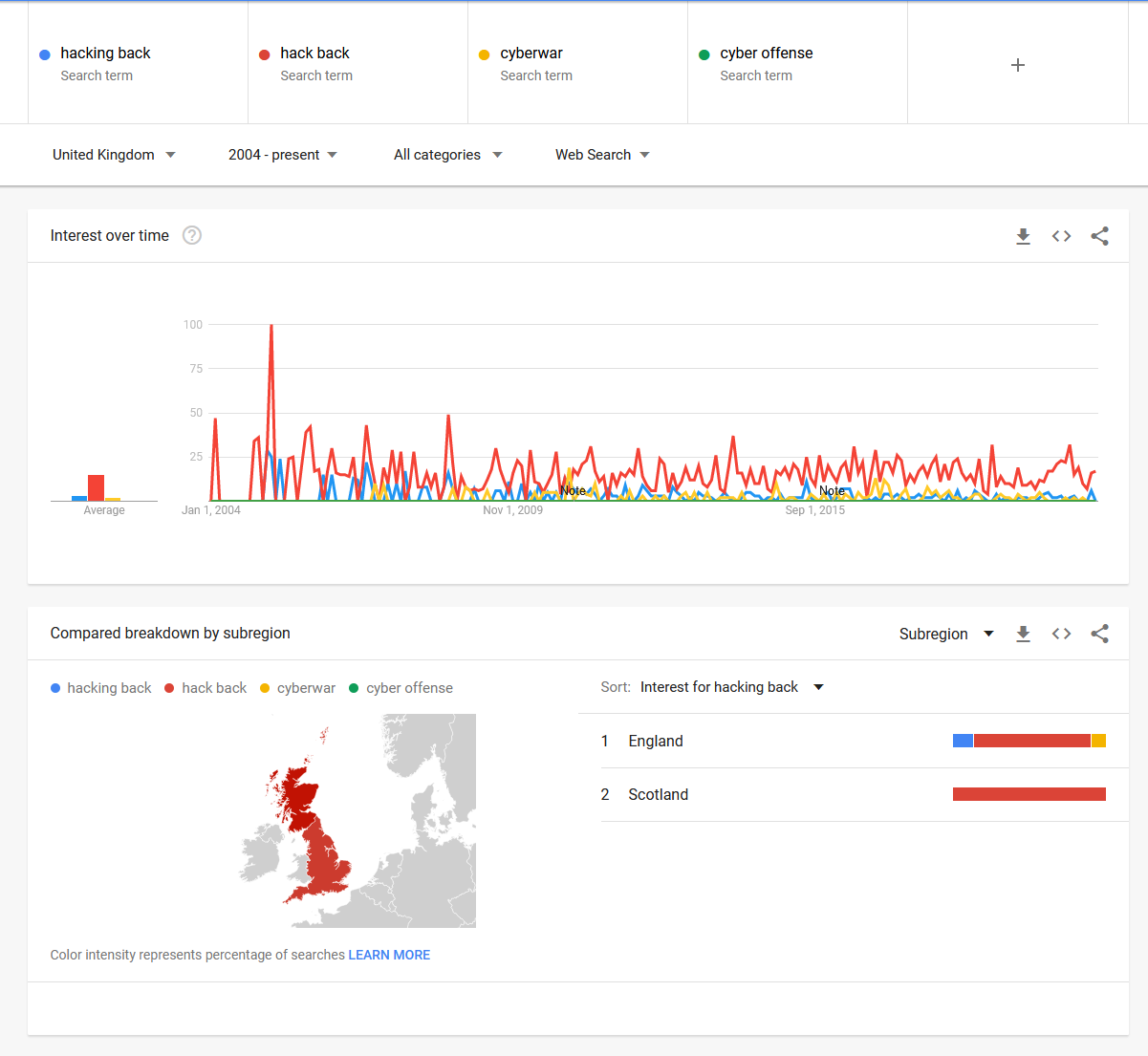
My feeling here is that it is a topical point in my sector and that with cybercrime and cyber events being far more mainstream now it might be partly due to my bubble. It something however that I think more and more people are starting to become aware of, so to me it is key that we educate and enable people in ways to promote awareness, learning and share the wisdom we have gained so far not only in cyberspace but also from other areas of conflict.
A view on my experience in cyber defence
I have been exposed to a range of incidents over time, from human error through to credential stuffing via a 300k+ node rotating proxy service. I have dealt with major worms back in the day such as Nachi and MSBlaster, I went into an NHS trust to support the WannaCry response and I have helped with smaller events for businesses which involve incidents such as business email compromise and ransomware.
On top of incidents, I have planned, designed, and build technology services for a range of organisations over the years from small SaaS providers, specialist organisations, large global enterprises through to public sector, government, and military organisations. (do not get star struck I am not Jason Bourne and I have most certainly not seen everything.) I’ve been working in technology for 20 years and can see myself doing so for the next twenty of my career. On top of defensive work, I also conduct offensive security activities and not only participate in CTF events but also build and run CTF games. So, I have some knowledge of this space, it however complex, it is not just about cyber, it is economics, politics and legal, so I think a team sport in all in all. (I am not clever enough to understand every single nuance of all the domains).
Cyber War
I have seen a steady increase in cyber war rhetoric and comments from people who look rather unskilled in this space. Hell, I am just a nerd who has defensive and offensive skills and experience, but I am not a cyber war promoter. Last year I was called as having a Cyber Militia, yet that is so far from the truth it is unreal, it has however given me some insight into attack surface mapping at a country scale. Do I think we should conduct cyber/espionage as we have done since time began? Sure 100%. Do I think we need escalation and aggression in cyberspace? I think we need capabilities as a nation, I do not think we need them to be very overt, I do not think that “going offensive” is the key to solving the challenges and I think that even if that was a good idea (I do not) you do not go to war when your armour is in pieces on the floor. If we increase aggression rather than following political, economic and law enforcement means then we will simply increase the level of retaliation.
So, here are my points, in summary:
- Understanding your attackers is incredible hard
- A vast array of cyber incidents uses vast proxies, victim infrastructure and are conducted by a range of threat actors
- The primary motivation for cybercrime is financial
- You do not poke a bear with a stick
- If you cannot defend well then you sure as hell do not want to start a fight
- Even if your systems are well defended your neighbours probably are not
- It is a legal nightmare (I am not a solicitor etc. but given the CMA etc. and cross border activity it is almost certainly insanely complicated).
- Having a big stick does not deter cyber criminals, they just change their tactics.
- Most breaches I see are due to stupid decision making and lack of planning and preparation.
- If the people promoting cyber war have anything to do with products that say bank grade, PKI management, military grade of quantum they probably are just trying to sell you something snake oil based.
- A strong defines comes from a strong defence but from an offense.
- If we can’t as a race/country/sector get the foundations nailed (we haven’t so far) then going advanced on the offensive outside of what we have been doing anyway seems like the wrong focus areas.
- Communication is the greatest cyber weapon we have; we should focus on that before thinking technology will save us. The more we educate the more we enable, the better we defend the less impact there is from crime (and hopefully we keep people on the right track to start with)
Hopefully, this gives some food for thought to people, remember, be safe, backup your data and may the force be with you.








