 Leadership
Leadership
Ok a bit dramatic, but that’s often what you might feel if you spend lots of time in the vulnerability space (which if you work in cyber security.. you probably do!). We often hear about the NEXT: STUXNET, HEARTBLEED, WANNACRY/ETERNAL BLUE, LOG4J etc. but actually when it comes to it… the number of times we have word endangering unauthenticated remote code execution that is a danger to global society is far less than when we have other vulnerabilities. It’s the exception not the rule.
This brings in the fact that as an industry, I feel we are not great at:
- Threat Modelling
- Understanding Risk from different perspectives
CVSS – one SCORE to RULE them ALL!
Here in lies part of the problem. A vulnerability scoring system has focus on: a single vulnerable asset.
But that’s not how the world works is it. We have ~4.8 Billion IPv4 addresses on the internet in a world of BILLIONS of devices and people with millions and millions of organisations etc.
So what is really important? Context! Context is KEY! But so often this is lacking when ‘the media’ (or others) report on a vulnerability. THE SKY IS FALLING DOWN (except mostly it isn’t!! – Exchange ProxyShell was an example of when it was really bad! and when it was discovered the threat actors went even harder at exploiting globally! that was a bit rare that!)
So is there another way?
So I was thinking about if we could codify a method that people can use. Let’s not pretend I’m making something earth shattering here, this is a simple risk assessment methodology. But let’s take a look at how I might assess a vulnerability/threat. Partly the way I do it is to ensure I get as much contextual intelligence as possible. I combine this with the fact that I want to consider multiple perspectives;
- Attacker (Threat)
- The single asset (a vulnerable one)
- An organisation
- A country
- The world
So I have created an example (and it’s just that an example, a model, it’s not right or wrong!):
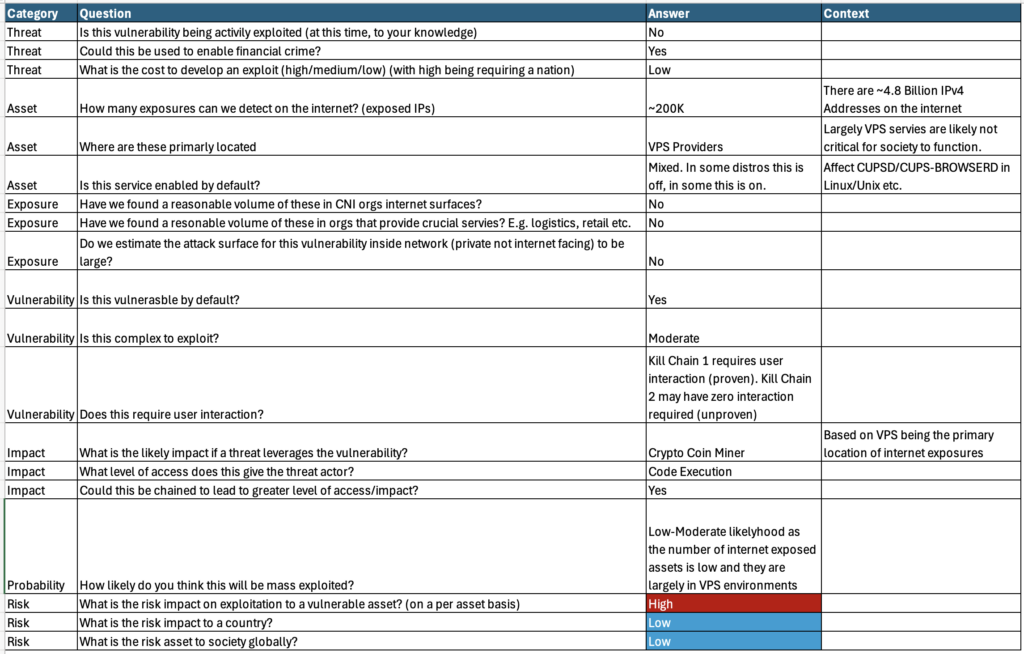
Here I’ve used a recent set of vulnerabilities in CUPS-BROWSED and CUPS libraries to show some of my thinking as to how I have personally assessed the RISK.
What if I told you?
You can have an impact to asset that is HIGH but an impact to society that’s LOW? I know madness right. It’s almost like we need to consider things in complex ways (because they are complex!) so that we don’t abstract our way into Fear Uncertainty and Doubt (FUD)
The common risk assessment formala is like this:
Probability of Occurrence x Impact = Risk Score
This is simply too abstract when working across multiple perspectives. It doesn’t include anywhere near enough context and it certainly doesn’t cater for multiple viewpoints. Sure you can run this once per viewpoint (which is basically what I’ve done above) but you need to be armed with: INTELLIGENCE
If you don’t have the right INTEL then you won’t be able to make a reasonable assessment. We must also remember that assessments are subject to change, which in the fast paced world of cyber comes with a reality: we will sometimes not be ‘right’ – our assessment must be allowed to evolve and change as new information (intelligence) is available.
Anyway hopefully this gives some insight into how I look into vulnerabilities ‘AT SCALE’ to help steer the response efforts (which ranges from doing nothing through to standing up honeypots, writing blogs, creating exploits and defensive tools etc. etc.)
I also (this is an edit) want to show another way I start to look at risk:
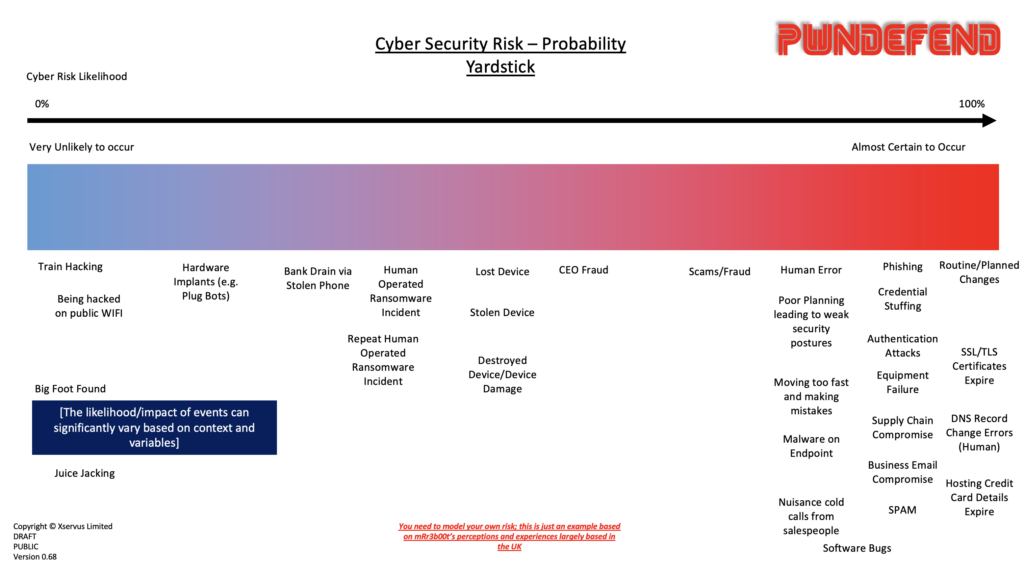
This again is a model (all models are broken/wrong – some are useful!) but it looks to see from a likelihood point of view the risks I see. There’s a good UK Risk report that’s worth looking at:
So again, remember, lots of viewpoints and lots of views. Just because something can happen does not mean it will, just because it’s low likelihood doesn’t mean you should ignore it. But as with most things in life, balance is required! We all have constraints, we can’t eliminate all risk!









