 Threat Intel
Threat Intel
I’ve not blogged in a while, but I wanted to put down a note of some useful tools people can use to help them combat cyber crime.
This isn’t going to be an in depth look at each tool, however I do want to, in the near future, try and do some demos/videos etc. of how to investigate potential/suspected or identified threats. I’ll drop a list of some of the useful tools below and also do a quick demo of investigating an event (from this blog)
Some Useful Tools
https://certstream.calidog.io/
https://urlhaus.abuse.ch/browse/
https://www.telerik.com/fiddler
https://ransomwatch.telemetry.ltd/
https://dashboard.shadowserver.org/
https://www.gov.uk/get-information-about-a-company
https://talosintelligence.com/reputation_center
https://www.winitor.com/download
https://gchq.github.io/CyberChef/
https://github.com/smicallef/spiderfoot
(thanks Jake for reminding me to put Cyberchef!)
An example analysis
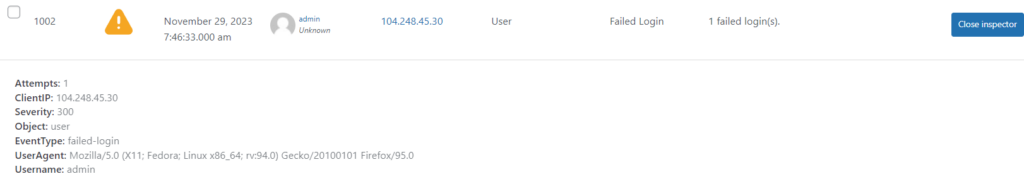
Ok, so what better example than someone trying to log into this site! So let’s look at a recently failed login (to a valid account 
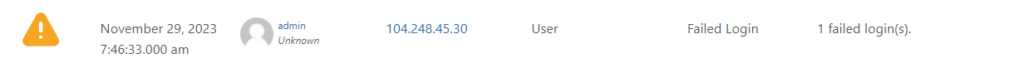
So we can see someone has tried to login to account “admin” from here:
104.248.45.30
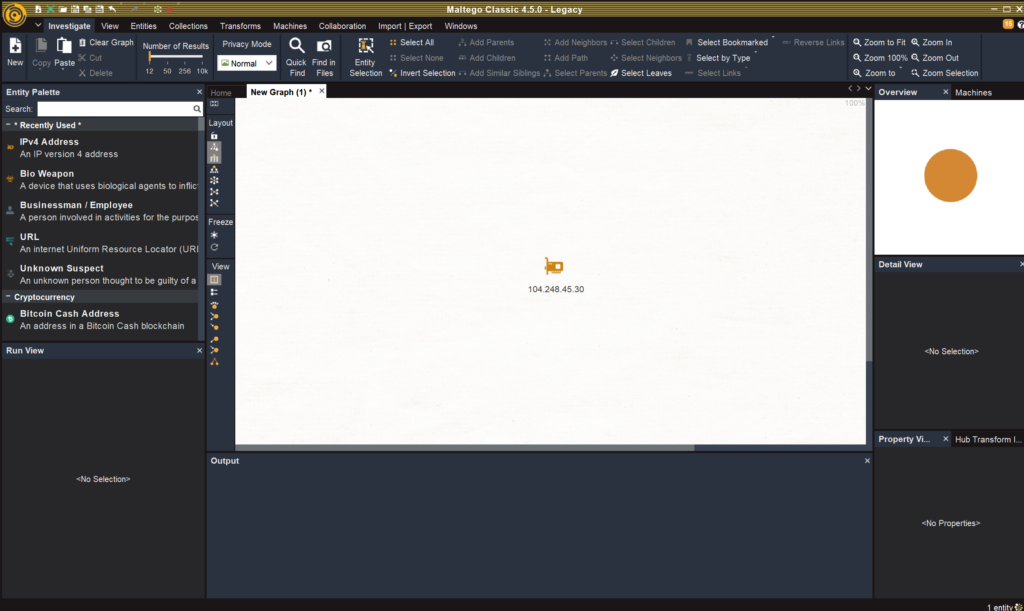
So we fire up Maltego and we paste in the IP address, we then want to enrich. We can do this using built in or third party transforms (with APIs), you can see here that I have Censys, GreyNoise, AlientVault OTX, Ipinfo and Shodan loaded:
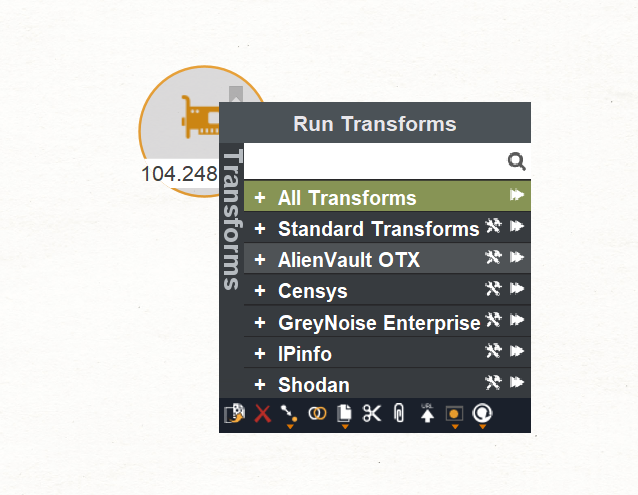
To start we are going to enrich with IPinfo:
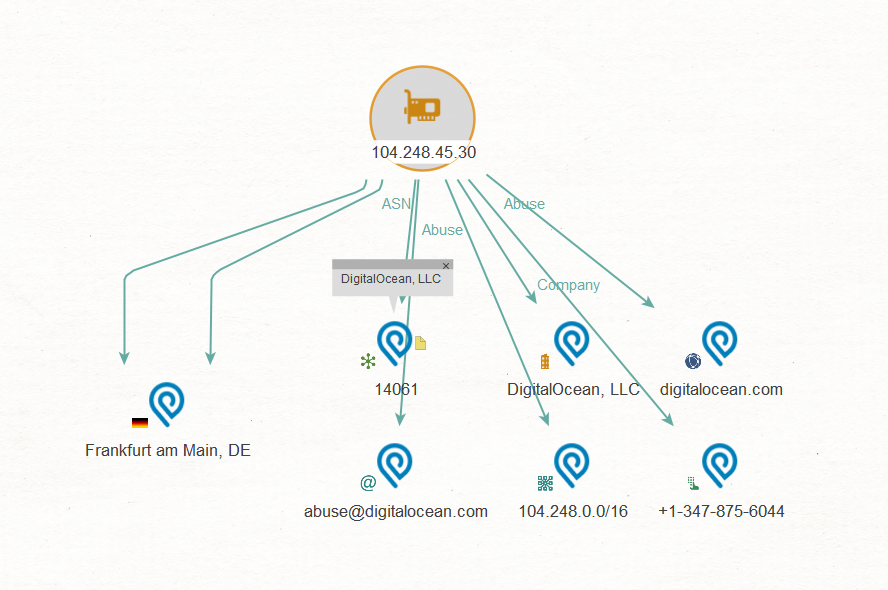
This shows this IP is believed to be in Germany (IPInfo have some really cool location tech) and the IP appears to be hosted on digital ocean!
Next I’m going to enrich with Greynoise’s API
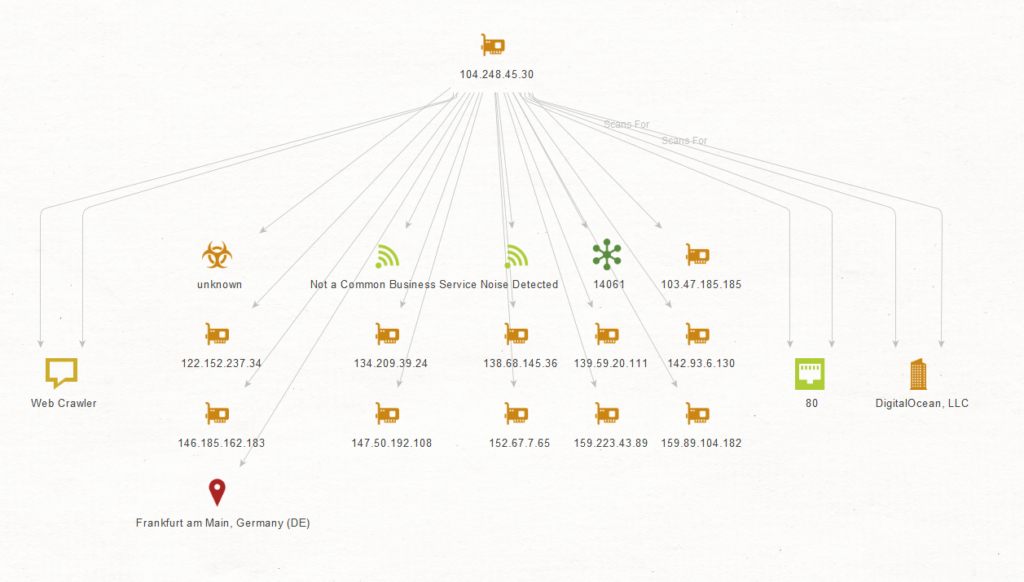
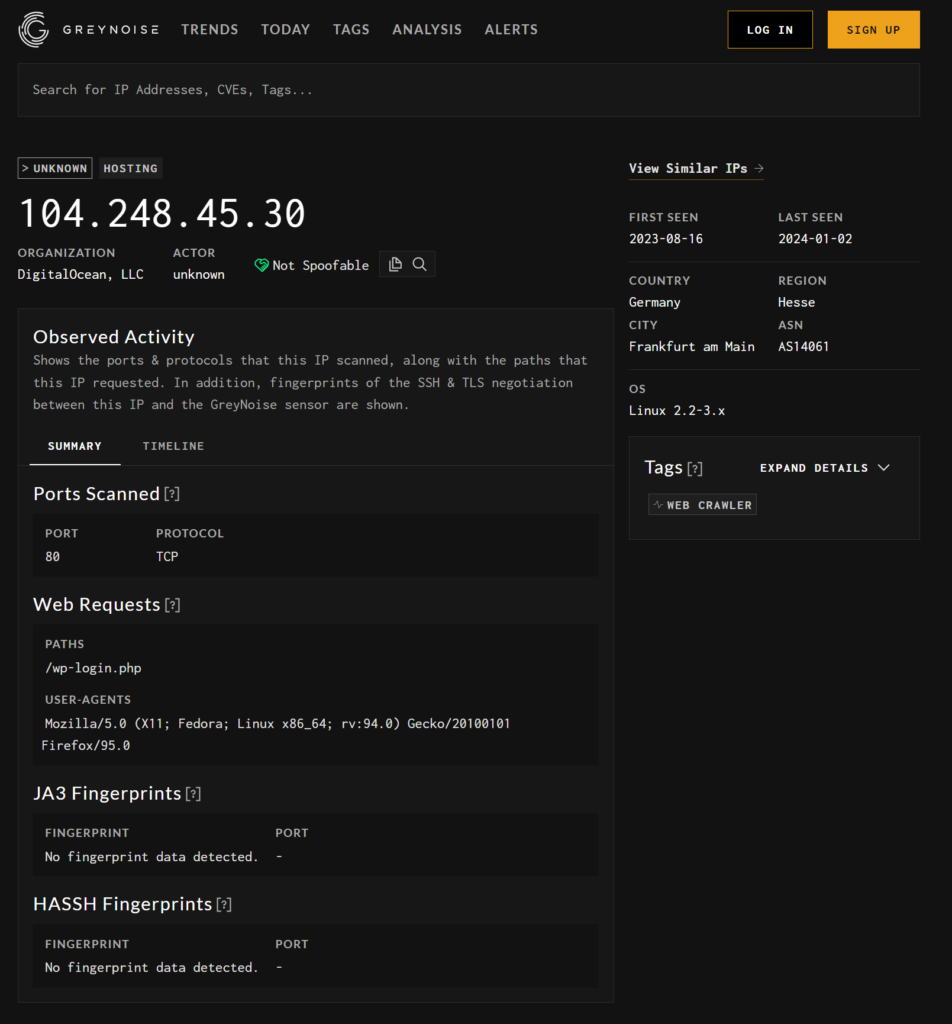
You can use the web tool (honestly I use a mixture of code, maltego and web UIs)
https://viz.greynoise.io/ip/104.248.45.30
We can see they were looking for /wp-login.php endpoints!
The user agent from our website login failure attempt = Mozilla/5.0 (X11; Fedora; Linux x86_64; rv:94.0) Gecko/20100101 Firefox/95.0 which matches what Greynoise has seen!
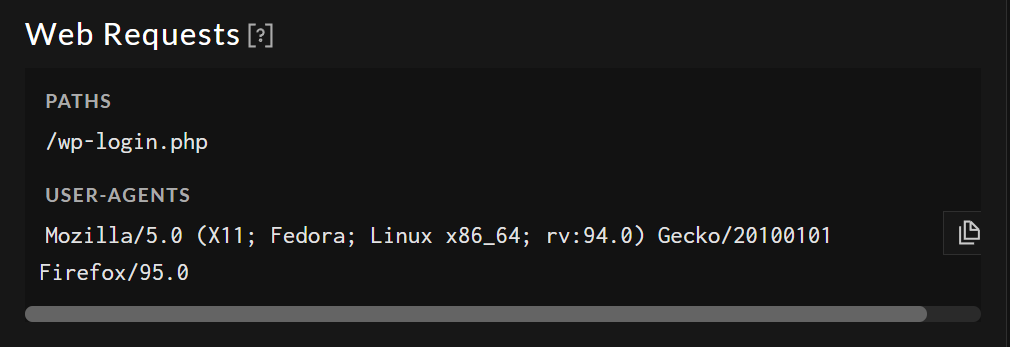
OK so it was one attempt, this looks like someone spraying for a weak credential on user admin. But ;et’ssee what is running on that IP, so let’s head to shodan.io
https://www.shodan.io/host/104.248.45.30
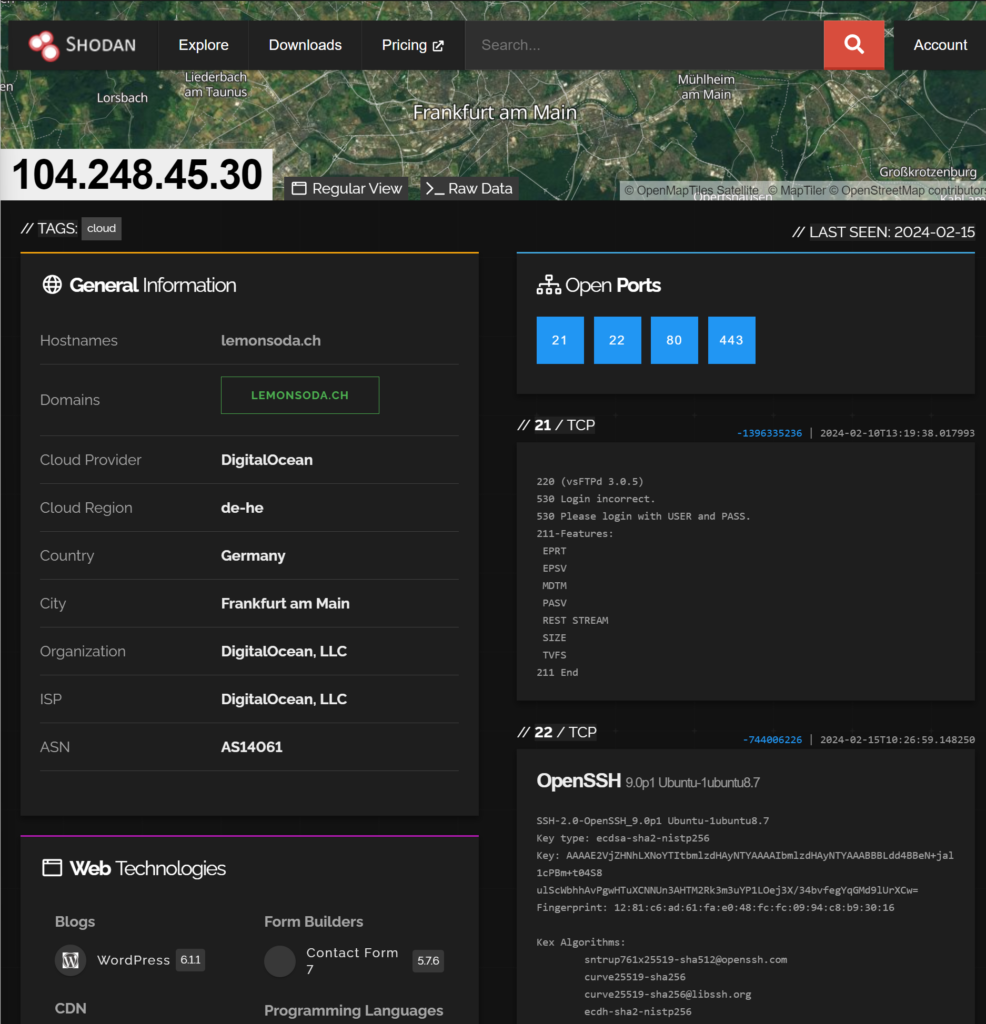
We can see here that the site is running a range of services, including: vsFTPd SSH, and then WordPress 6.1.1 running on an Ubuntu server. The server shows the following wordpress info:

“Offizielle Crodo Lemon Soda Schweizer Seite”
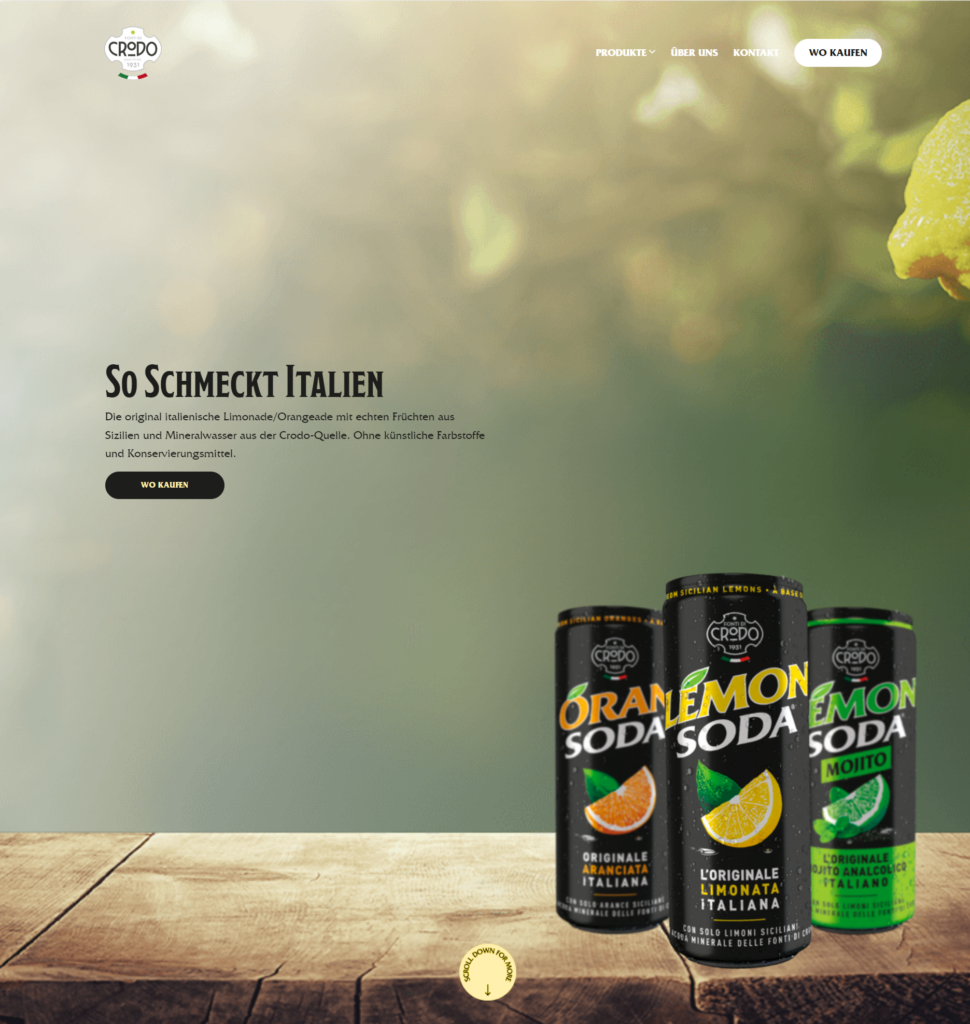
Could this be spoofed? Not that likely. We take the IPs from cloudflare. It’s possible. Either way you can see here that we’ve gone from a single event through to analysis using Maltego with Shodan, Ipinfo and Greynoise. From here we have identified a pattern of activity, and identified the likely source. We have to remmeber this event from was November in 2023. We can use other tools in the list in this blog like Alien Vault OTX to look for other sources of intel:
https://otx.alienvault.com/indicator/ip/104.248.45.30
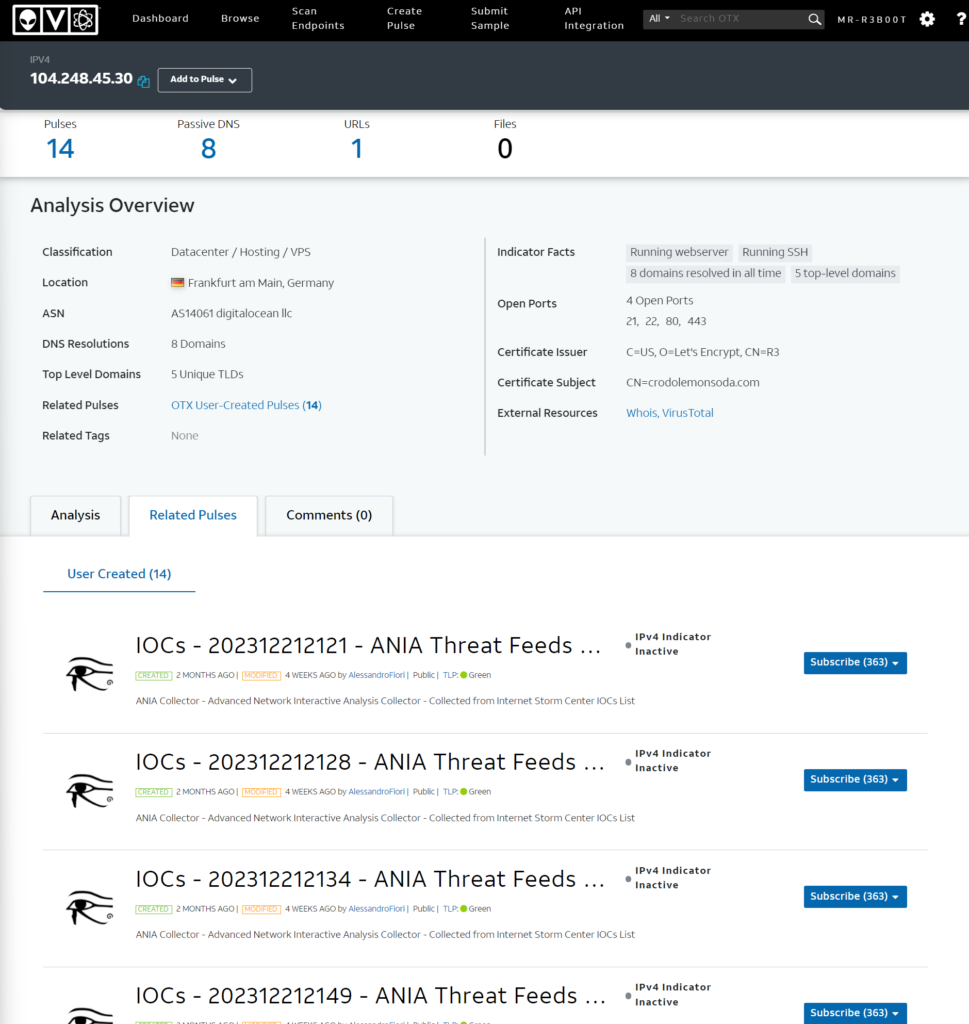
So here we can see activity from a few months ago! So a key thing to remember, time is an important consideration when investigating.
Hopefully this quick (random) demo is useful to show people how to take a small amount of data (IP, Date/Time, User Agent and Activity/Context (failed logon on a WordPress site) and to start investigating using some of the tools! In this event you can see that, the login failed (great) and that it came from what looks like a legitimate web server back in November. There’s not really any defender action to take, we could notify the org (encase this was from a compromised host). If we expose services to the internet, attempts to login will be made (that’s almost a certainty) and this is why we have multiple controls such as CDN, WAF, Logging, automatic updates, secure config, alerting and we have people who can analyse and respond (me in this instance).








