 Hacking
Hacking
My friend Lars and I were just talking about some of the research areas we are working on and randomly the conversation turned into “what shall we call it?” and then LDAPNomNom came up! So I whilst laughing (coz the name is lulz) with my buddy I downloaded and ran LDAPNomNom against a lab vm quickly! (Lars also fixed an error with readme.md that I pointed out coz my debug skillz ROCK! 
So here we have me doing username enumeration via LDAP Ping using LDAPNOMNOM!
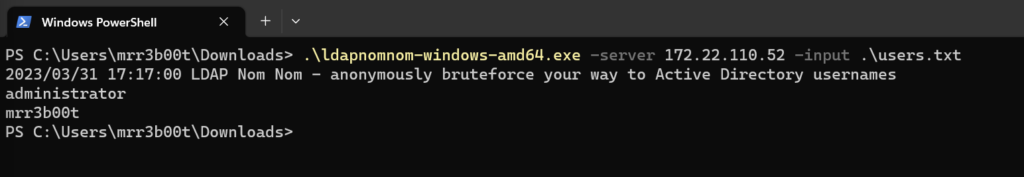
Look see I found myself!
So what does this tool do?
Well it uses the LDAP PING feature to enumerate valid usernames. Lars wrote this on GO so it’s super fast and the best part, this doesn’t generate any log entries! woohoo stealth mode username enumeration for when you are testing Active Directory from an routable position to LDAP on a Domain Controller and you are sitting in the cold without any credentials!
To run this simply download the binary (or compile from source) and input a list of usernames!
.\ldapnomnom-windows-amd64.exe -server 172.22.110.52 -input .\users.txt
This will slam LDAP with a load of requests and valid usernames will fall out! Wonderful stuff right!
You can obviously combine this with nmap to dump some domain information as well:
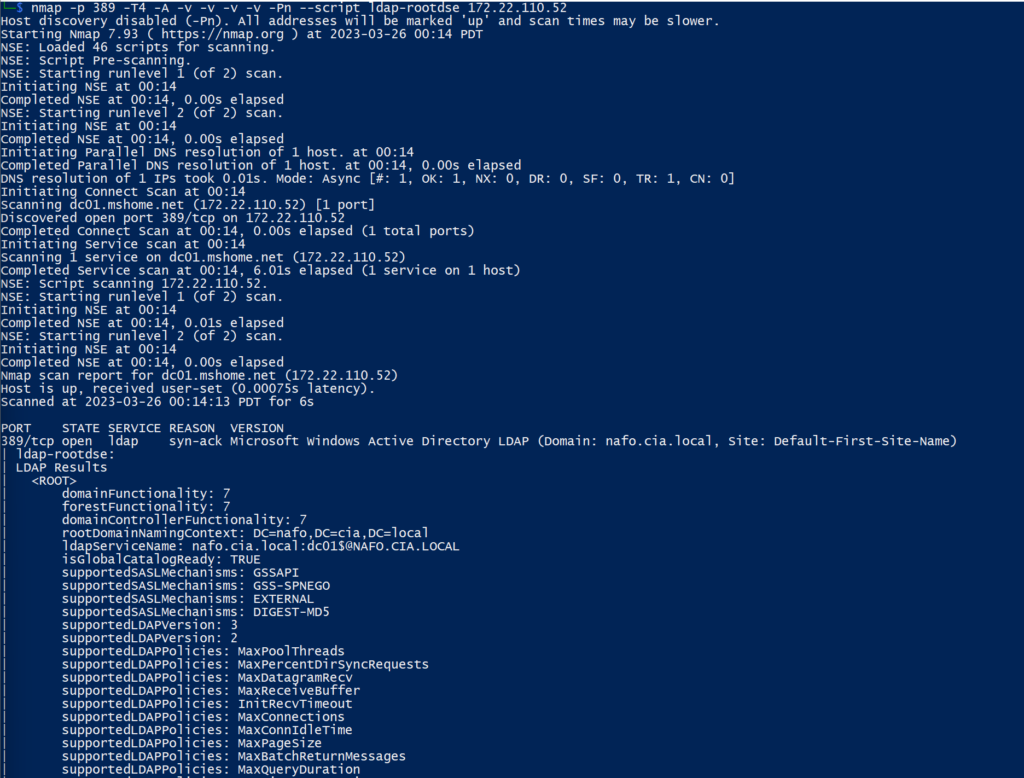
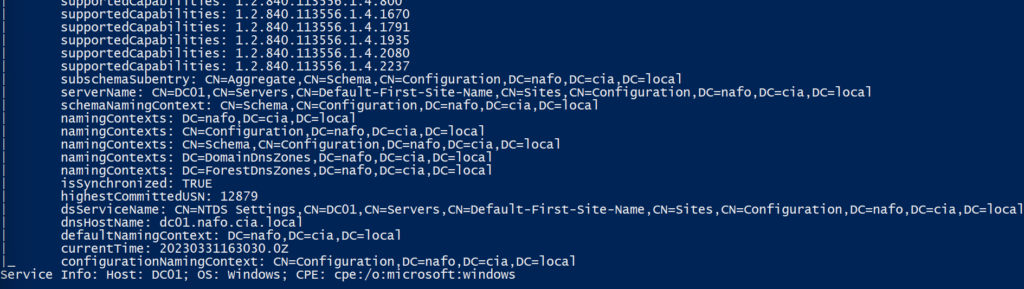
So from here we have the:
Domain Name
Hostname Information
Partition Information
and with LDAPNomNom we now have some valid usernames!
Loads of fun and a fun name to boot! (plus it’s stealthy!) – get adding this to your Active Directory Testing toolkits if it isn’t there already!







