 Education
Education
Some friends and I did some testing this evening with TOX clients. We wanted to take a look at PERSEC/OPSEC considerations for using TOX. I also had a sneaky suspicion that it might out of the box leak more than people would appreciate (just a hunch and you don’t know until you test right!).
So, we setup a test. In the test we had:
- Windows 11 VM with uTOX
- Andorid with aTOX Client
- Linux with uTOX
- Windows with qTOX
Testing
We setup a VM, deployed wireshark and SYSINTERNALs and then ran uTOX cient.
We then had multiple clients connect.
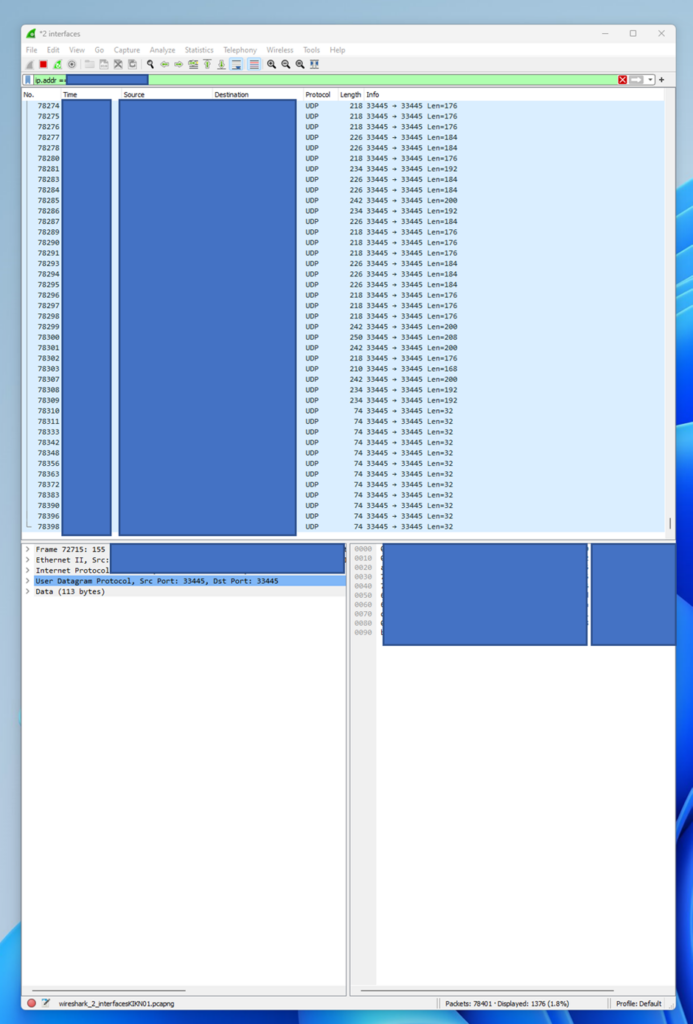
We could see that when using:
- uTOX
- qTOX
The egress IPv4 addresses were leaking (via UDP). It may also leak in other configurations e.g. via IPv6 or via TCP (not tested these)
When using aTOX (Android client) the traffic was routed via the TOR network
Countermeasures
You have a range of options, you could:
- Use a VPN
- Use a forced TOR connection (physical or software)
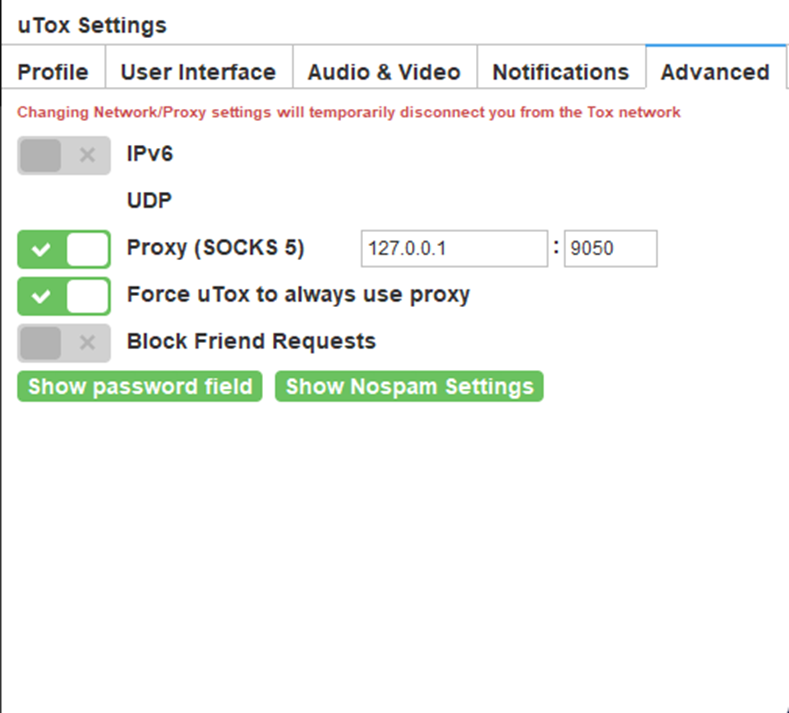
- Configure TOX to always use a proxy and Proxy via TOR
- Configure a local TOR SOCKS proxy.