Vulnerabilities
Vulnerabilities
There appears to be a new RCE out for Fortinet devices as per this post (it’s against FortiNAC as far I am aware so this is probably a much smaller exposure footprint than all fortinet devices):
https://www.fortiguard.com/psirt/FG-IR-22-300
There’s also this in FortiWeb (and well they released 40 odd fixes to various bits)
https://www.fortiguard.com/psirt/FG-IR-21-186
When we consider security edge devices and the risks these may pose to organizations and society as a whole it’s important to understand that these are no trivial matter. These are “security” appliances that are there to protect your organizations, to provide remote access as well as protect network egress etc.
Fortinet are not the only vendor to suffer from these types of vulnerability (Remote Code Execution – RCE) however there do appear to have been quite a few of these when looking historically.
https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=Fortinet
https://cve.mitre.org/cgi-bin/cvename.cgi?name=2022-27482
Once we understand there is a vulnerability, and we understand the severity and potential impact (for this it’s an unauthenticated remote code execution) the next thing to consider are questions such as:
- Is my organizations at risk?
- Is this being actively exploited?
- Is the exploit or Proof of Concept Publicly available?
The advise would be:
- Follow vendor guidance
- Remediate/Mitigate the vulnerabilities
- Conduct an investigation to ensure you have not been compromised (assume breach mindset etc.)
Look to improve processes and procedures to ensure you are aware of vulnerabilities but also have appropriate controls/defenses in place (including monitoring)
Thinking beyond the single organization
Great so each org should ensure they are aware and remediate or mitigate, but what about if we wanted to act as a responsible cyber citizen?
The kind of questions we might consider are like the following:
- Is my country at risk?
- What services are at risk?
- How many vulnerable devices are there?
- Are there any critical services at risk that might have slipped through the cracks?
- Should we try and locate these and advise people?
There are a range of ways people can go about doing this the first phase of Discovery, is actually the simplest.
We can use either ACTIVE packets or PASSIVE data to search for technology fingerprints and identify components to a varying degree of criticality. The map below shows some Fortinet devices exposed to the internet (that is largely their purpose!) (note the vuln in the CVE in the title of this post is against only specific versions of FortiNAC – you may need a different query for these 
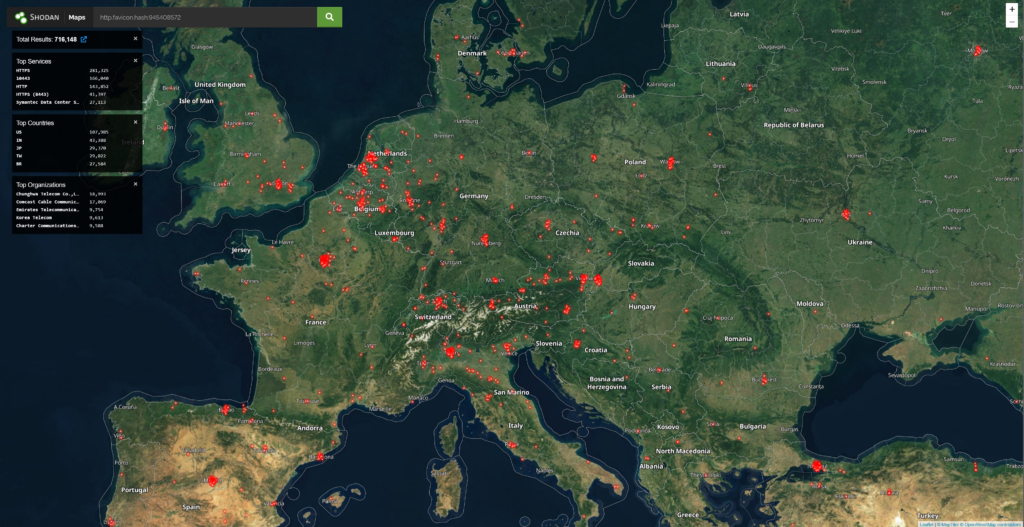
The next phase would be to understand if by passive or legal means you can identify the software versions.
Now you would also want to be able to identify who owns these, for without knowing the owner, you can’t communicate (we could however contact the media/press or post online to raise awareness of the issue, so it’s not a binary position).
- Reporting vulnerabilities is a very complex (and can be rather risky) I recommend that people do considerable thinking about
- Is the risk of accusation worth the risk of reporting?
- Do they have a plan for reporting directly?
- Do you report anon or as yourself?
- They could consider reporting to the countries CERT as well which can make the process simpler in some senses, but may delay comms to the affected org.
You can hopefully see here that this is not a simple position, it’s complex. One of the reasons I want the UK Computer Misuse Act to be reformed is because I think there should be:
A law that enables Law Enforcement and Governments/Intelligence Services to be able to operate to PURSUE criminals (think ransomware actors, fraudsters, credit card thieves, crypto miners)
but also a law that PROTECTS and ENABLES:
- Industry
- Professionals
- Researchers
- Academics
from conducting legitimate, useful, required and good faith/legal activities.
The idea that the world has omnipotent and unlimited CYBER resources and CAPABILITIES might work in Hollywood but in reality it doesn’t work this way.
As part of my professional work, the CV19 initiative (that still operates, all be it in a very specific manner) and as a researcher and (in my opinion) a good cyber citizen (ok it’s a bit cringe but I think society needs this capability and type of model) I conduct a range of activity to try and help people, I am by far alone, there is a community of people around the world that collaborate across borders with Governments, Law Enforcement, Intelligence Services, Academia, Industry, and Citizens to help defend them in cyberspace as well as pursue cyber criminals.
I might have gone slightly on a slight tangent but I think it’s important that people recognize that our society is increasingly dependent and potentially vulnerable to cyber threats. The Fortinet RCE is one of many across a wide range of vendors and products, it’s not the first, and certainly is not the last. To combat the evolving threat we need an all of society approach, we need the right policies, laws, standards and PEOPLE. The people part to me is key, they are our greatest asset for creating a safe cyber society!
 (@cyb3rops)
(@cyb3rops)