 News
News
According to the Belfast Telegraph:
The Incident is reported by them as “RANSOMWARE” and features Lockbit (Lockbit is RaaS, they recently (end of 2022 lost their ransomware payload builder) so the use of Lockbit software and the fact Lockbit is RaaS means this doesn’t prove attribution). (Attribution is hard, for most people what matters is their own network security posture, rather than who pwn3d royal mail)
An interesting journey of wording if you analyse Royal Mail saying “cyber incident” vs cyber attack. In all fairness I tend to go down a journey of: EVENT, SUSPECTED INCIDENT, INCIDENT – the word attack is a bit “HYPE” (often I use this word in jest). What kind of impact does this have on data subjects? What kind of impact will this have on Royal Mail? No idea really myself.
What does knowing it’s reported to have been LOCKBIT tell us? Well that is probably for another blog!
Cyber Who Done it! (and how?)
If you like Who Done its? are interested in vectors for cyber attacks, Matt posted a really interesting one
That might be a slightly novel vector for ransomware if that’s the case… it would be more interesting than
“highly sophisticated” phish, creds, remote access, domain admin, exfil, destroy backups and crypto all the things (Group policy object/Scheduled task etc.)
Updated 1725 12/01/2023.
Earlier Post Below
Fast Publish (expect potential errors and changes as the situation unfolds)
Earlier I posted a bit of a click bate post to help promote people focusing on their own security postures, when cyber incidents are in the news they can consume good amounts of time, they can promote people to worry if they will also fall victim to the same fate. I’m seeing some things on social media which seem to link the Royal Mail (post office) tracking system cyber incident to the FAA service outage etc. so I thought I would post another blog on what we know right now:
https://personal.help.royalmail.com/app/answers/detail/a_id/12556
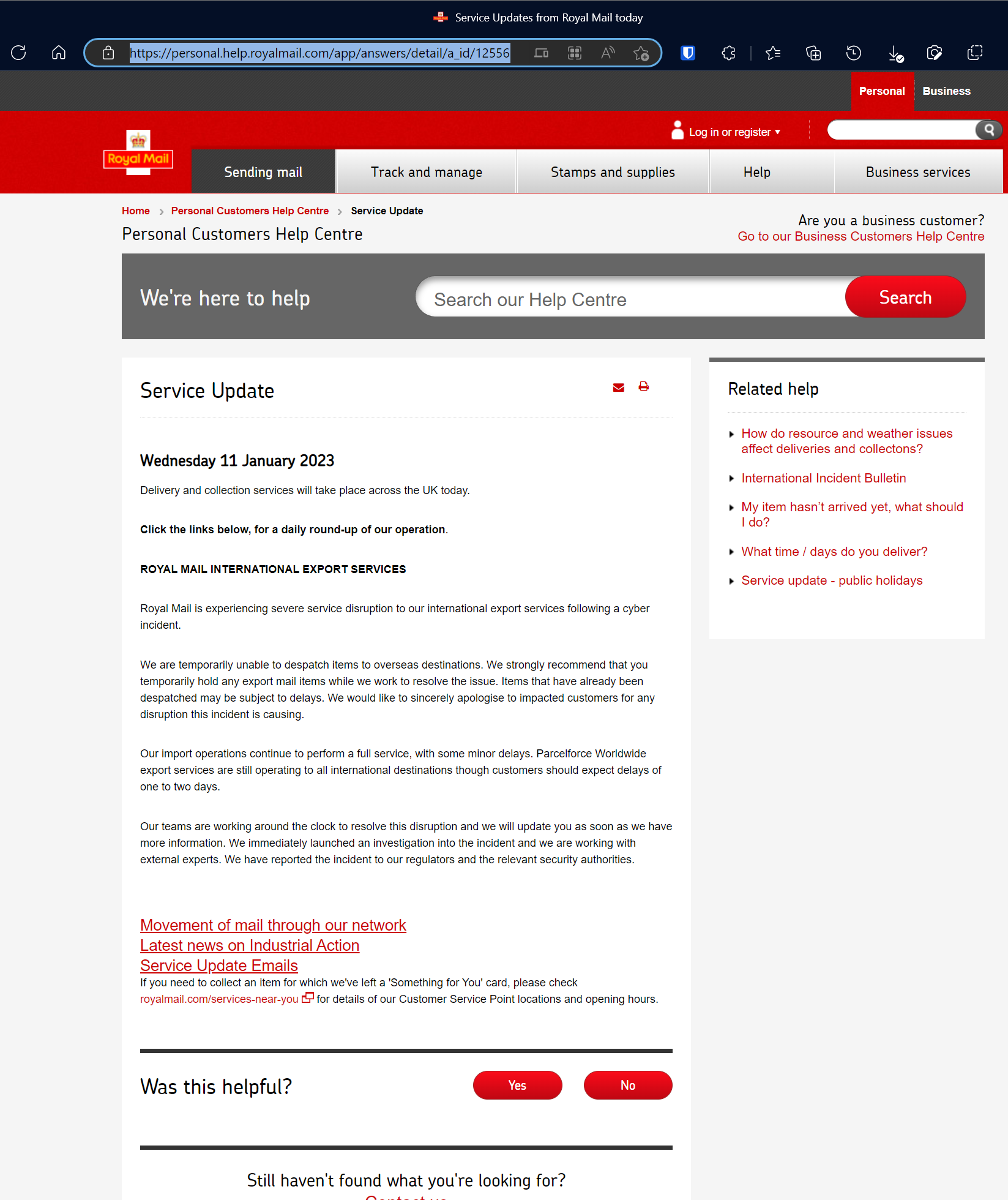
Update 12/01/2023
What we know (11/01/2023 09:04)
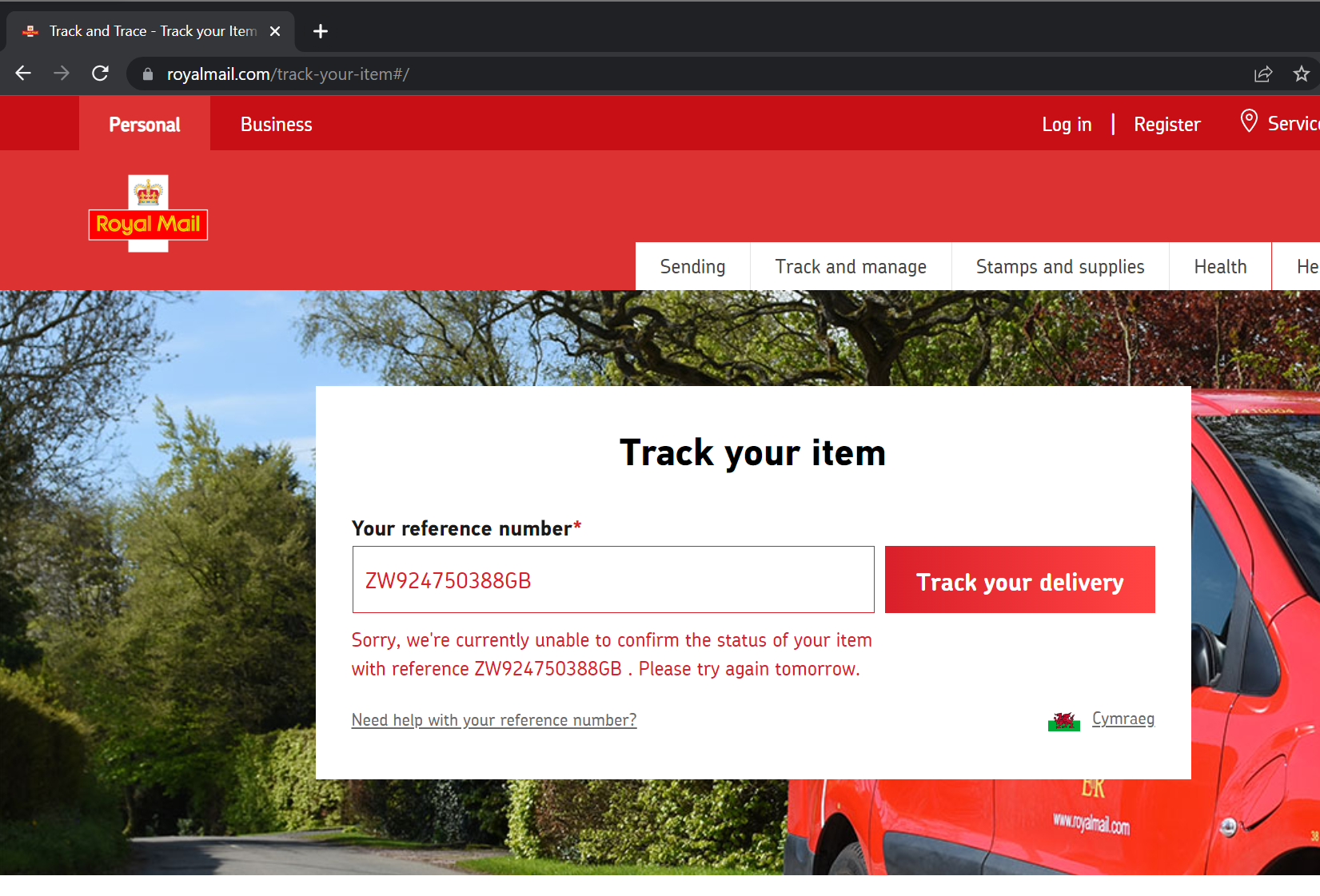
Royal mail’s tracking application has an issue and customers have been updated to say there is an active Cyber incident (not an attack).
- We know the tracking service has been down for > 24 hours.
- We know that the NCA, NCSC and ICO have been contacted.
- This makes the likelihood of it being a glitch much less
- There’s RUMOUR it was a cyber attack that was ‘destructive’
What we don’t know
- We have no IOCs
- We don’t know if this is a “Cyber Attack”
- It is obviously concerning as the NCA, NCSC (part of GCHQ) and the ICO are involved
- It’s not confirmed as “RANSOMWARE” (but probably is)
- We have nothing to suggest it’s related to the FAA incident (Reuters are reporting the FAA systems are coming back online)
- US Aviation Computer Outage: FAA Lifts Ground Stop On Flights Following Computer Outage (outlookindia.com)
- Not only is there nothing to suggest it, it’s now reported that it was routine maintenance:
This may just be a computer glitch ( in the above article a power failure is mentioned). It’s very unlikely this was a CYBER incident and it’s INCREDIBLY UNLIKELY the Royal Mail incident has anything to do with the FAA (suspected Power Outage)- The FAA Incident is reported as a human error/computer fault (Which given the Royal Mail links to NCA, NCSC, ICO means they aren’t related. they just both related to computers…. #awkward)
Here’s LBC appearing to link the FAA, Royal Mail and if you watch closely we have Russia and WannaCry thrown into the video (what about the kitchen sink?)
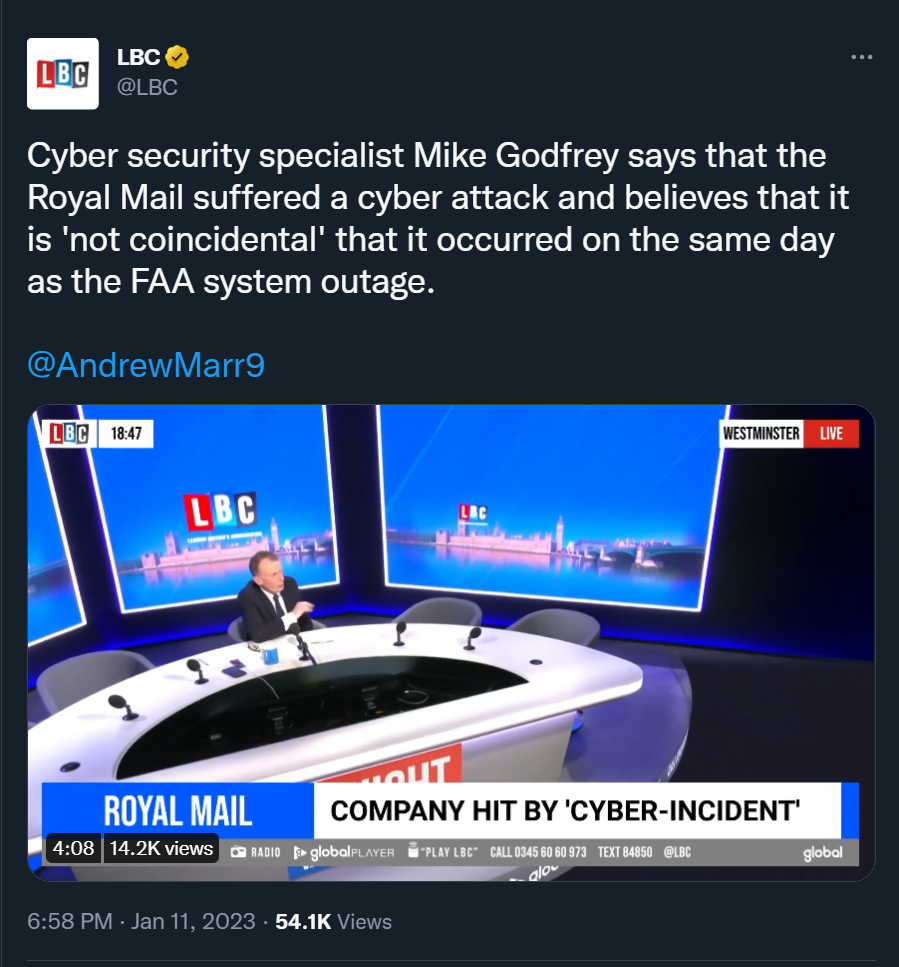
Interestingly there is mention of a Printer printing ransom notes (how accurate that is I can’t say) however let’s see – who is known for printing ransom notes?
Actors Known for Printing Ransom Notes
- Egregor
- Cobalt Mirage
- APT35
- Charming Kitten
- Phosphorus
- TA453
But as a friend and I are talking about, it’s anyone that can /code “print” so basically anyone could print something 😀
The Tracking Services
https://www.royalmail.com/royal-mail-you/intellectual-property-rights/linking-our-website
https://www.royalmail.com/track-your-item#/
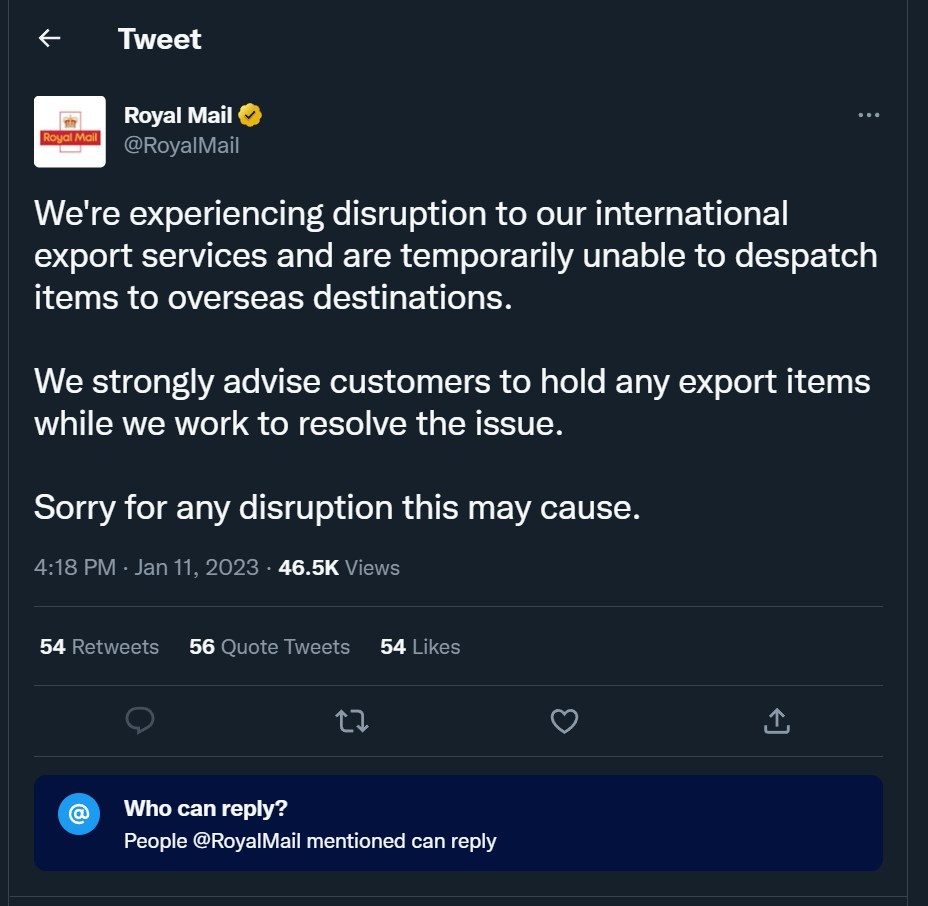
Post Office Tweets
They disabled replies:
Tweet from the NCSC UK & the ICO
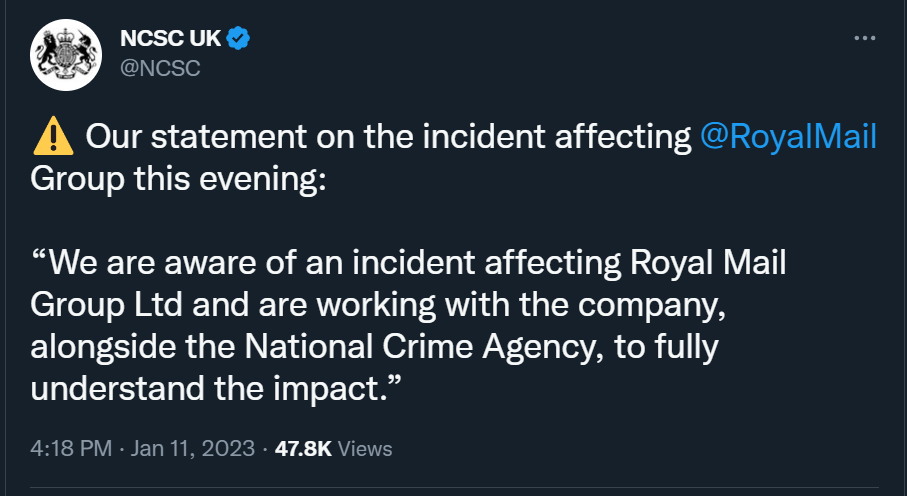
https://www.ncsc.gov.uk/news/royal-mail-group-incident
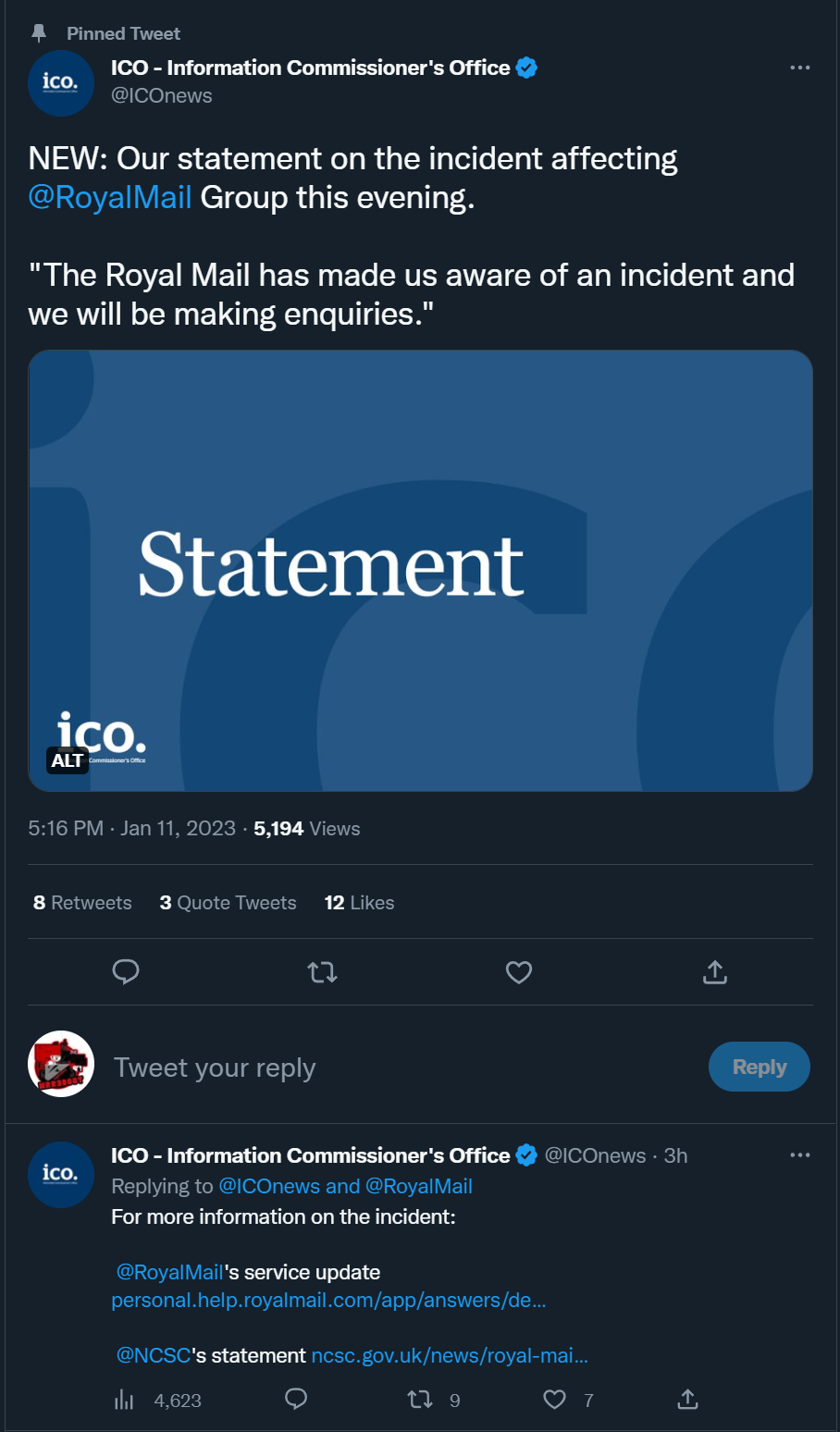
Media Links
https://www.bbc.co.uk/news/business-64231473
Nice work Joe!
BBC being nice and sensible! Also the bleeping computers article is also seemingly sensible:
and Reuters…
The FT article.. not as much…
Royal Mail unable to dispatch overseas packages after ‘cyber incident’ | Financial Times
Reasons you might attack Royal Mail from a threat actor perspective
- Logistics and Postal Services are prime targets for nation states, you can tell a lot about someone from details of their mail/deliveries
- You can also do things like intercept or coerce interception of packages/good etc.
- For crime there are all the usual reasons
- Money!
List of Media Publications
This list is clearly not exhaustive but here’s a collection:
Jan 11th
https://news.sky.com/story/royal-mail-unable-to-despatch-items-abroad-after-cyber-incident-12784457
https://www.ncsc.gov.uk/news/royal-mail-incident
(The ransomware note was published in public – obfuscated)
Jan 12th
https://www.lbc.co.uk/news/russia-linked-hackers-behind-royal-mail-attack/
https://www.computerweekly.com/news/252529173/LockBit-cartel-suspected-of-Royal-Mail-cyber-attack
https://www.bbc.co.uk/news/business-64244121
Jan 13th
Keep Calm and Carry on Cybering
It’s very easy in this game to jump to conclusions, it’s also very easy to panic. It’s also easy to miss things. When we have high profile events/incidents/breaches I “try” and stay calm. I try and see what we can find out, I try and promote ensuring we as a community and industry speak to the public/media/press in a way that:
- Is clear
- Is factual
- Does not promote FUD
- Is helpful
I clearly won’t always get this right but I do even have internal company slides and decision diagrams to help focus thoughts etc. I personally think how we communicate with the world matters (but that’s just my opinion).
The details in cyber incidents are rarely known accurately fast, incidents of any size can be complex, fast paced and are usually evolving. I’ll try and update this as new intel comes in, I still maintain the important thing for most people to do is focus on their own security postures. Let’s see where this goes.

