 Threat Intel
Threat Intel
When an organisation suffers a data breach it’s usually bad. When an organisation that stores 25 million people’s passwords that’s really bad.
There are multiple risks here at play.
Firstly, when we give people our data, it’s our risk and our choice. I’m ok with that, I chose to give lastPass my data.
My vault data might be gone, but I have a strong master password, how we interpreted the theft of the basically cryptographic materials is a bit like when we full disk encrypt a drive.
If you lose a laptop that’s got FDE do you report this as a data loss to the ICO? Or do you say, it’s encrypted so actually I haven’t lost the data per say, I’ve just lost a random (ish) bunch of 0s an 1s so I don’t count that as an incident? I’m not here to be judge or jury.
What do we know?
Notice of Recent Security Incident – The LastPass Blog
We know that in August 2022 LastPass had a breach and a secondary impact of this was that a threat actor gained access to “cloud storage” and was able to exfiltrate:
- LastPass Account Metadata
- A copy of the vault (encrypted)
- A copy of vault metdata which includes the URL fields
- it’s probable that other metadata was exposed but the details are speculative because LastPass’s comms aren’t very clear
Is my vault safe?
I honestly don’t know. It depends on the master password strength, the strength of the crypto and the capabilities and intent/actions of the threat actor. Some vaults are probably far from safe.
I have a strong (long and random) vault password, am I ok?
Based on what I know, probably. But I am not all knowing. The encrypted data has been stolen.
This metadata (e.g., the URL and account metadata) that doesn’t matter, does it?
Well, no, I mean that really does matter.
What fields does the threat actor have?
Possibly loads, for some bizarre reason the URL field was not encrypted. The fields we know are encrypted for password items include:
- Name
- Folder
- Password
- Notes (internal name is extras)
What can someone do with this?
You can paint a very detailed picture from metadata such as URLs.
Let’s assume we have some basic account information:
Account Owner: Bob
Account email: bob@notrealdomain.local
Account owner address:
Partial Credit Card data
Ok so we can probably now know who “Bob” is and where they live and who they bank with.
Next, we have a load of URLs, let’s take a look at a sample of these:
https://central.sophos.com/manage/login
http://login.microsoftonline.com
https://www.ciscolive.com/online/connect/createAccount.ww
https://share.cisp.org.uk/my.policy
https://raidforums.com/member.php
What can we tell from this sample?
Remember this is just a sample (I also didn’t include any SPICY URLS with guids, parameters and other juicy parts on the end!)
- We can say “Individual” Bob likely works in technology; they interact with the UK governments (NCSC) intelligence sharing platform (CISP).
- We can also see they use various sites (maybe we could password guess against those!)
- We also can build phishing pretexts
- We have some internal IP addresses, so we can start to build a picture of internal networks they interface with
- We can see they use raid forums.. are they a criminal? Or perhaps they work in Cyber and do threat intelligence?
Summary
God this is terrible, Bob is clearly based on me. The data that’s been stolen and LastPass didn’t encrypt alone could cause me serious personal security risks, as well as operational security risks.
I’ve got all kinds of URLS here, why the f*ck were these not encrypted?
Look my master password is randomly generated, I’m ok with the concept that It’s very unlikely my vault will be breached. But the metadata… this is terrible just on its own. Its show’s who I’ve worked/work with, it leaks internal URLs, public URls, it gives away intel on technology (e.g. PHPMYADMIN) it leaks real IP addresses that I’ve obscured using CDNs and proxies, it shows honeypots and other sites I interface with. Expand this out to a million people, then expand it to 25 million people. This is a security nightmare, some peoples master passwords will be weak, but the threat actors don’t even need to worry about that. With the metadata alone they have a map of part of my digital life. I can’t even begin to work out if I need to classify this as an incident! Fuck, let alone if I have reporting requirements in contracts where this would require a report.
So I’ll post this blog and show the world, because this isn’t my problem, it’s potentially the problem for 25 million people, it’s also not a problem just in this instance, it’s a problem globally. So whilst I feel for the LastPass security team, whilst I believe my vault is “probably” ok, I believe that I’m at risk, that others are at risk and that the metadata alone is a major problem globally.
- Did I choose to use LastPass? Yes, so accountability for my data is well, on me.
- Did I expect them to have any parts of their “Zero knowledge fuck whatever architecture” not encrypted? Hell no
- Did they take adequate and reasonable steps to secure the data? Honestly, not in my book.
Do I feel for the Security teams at Lastpass? Absolutely. I can’t even answer the question about deleting my account, I don’t think that’s important. I’m now going to have to work out what the risks are to me, my customers, and family/friends. And I can already see loads of ways criminals (or hostile nation states) could abuse the metadata alone.
Yesterday I strove to take a balanced view, I’m hoping my view today is still balanced. My next steps, change passwords based on priority, probably re-ip a load of stuff and then throw a laptop in the Thames because I can’t even begin to understand what impact this has to me right now. Happy Christmas… except not so happy for the victims, we’ll be pissing about analysing metadata and taking pre-emptied steps. The note I took yesterday still stand, the logic still makes sense, the assessment of risk… is bloody complicated and time consuming. I can’t downplay that, the metadata loss is a bloody problem!
Checking your URLS
you can export your records from LastPass or you can use other tools, exporting the records puts all the creds into clear text on your disk. But that’s possibly the only way people will be able to even begin to understand the potential risks… this is so complicated.
Going Xtreme
Ok so my vault metadata doesn’t really make me lose sleep. Sure i’d rather it wasn’t pwn3d but it tell people:
- I’m a cyber nerd
- I work with healthcare
- I do some UK Gov stuff
- I visit crime forums
- I like pizza
- I have way too many SOCKs
- It leaks some honeypots etc.
most of this stuff is public knowledge and my security model isn’t based on obscurity… however… (this doesn’t make me ok with it, it doesn’t make it right, but it is what it is…)
think about this theoretical scenario:
- you are a politician
you have URls which include:
- PornHub
- Ashley Madison
- Dark Web Drug Forums
you now are probably in a different position and someone might be able to extort you…
The Fields!
Ok this was from a nice chap on LI:
“The following fields are encrypted using a AES-256-CBC key derived from PBKDF2 with 100,100 iterations of the Master Password:
Name, Folder, Notes, Username, Password”
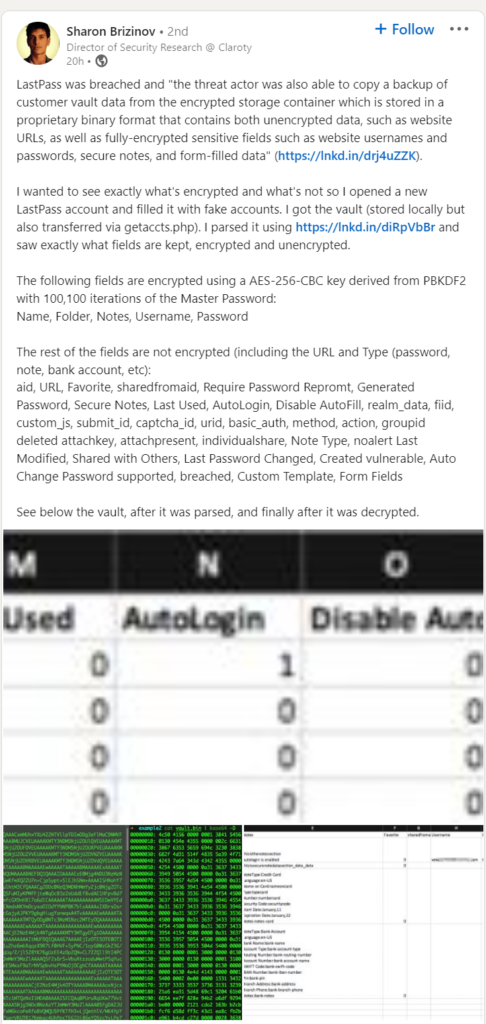
The following are NOT ENCRYPTED (WTF)
The rest of the fields are not encrypted (including the URL and Type (password, note, bank account, etc):
aid, URL, Favorite, sharedfromaid, Require Password Repromt, Generated Password, Secure Notes, Last Used, AutoLogin, Disable AutoFill, realm_data, fiid, custom_js, submit_id, captcha_id, urid, basic_auth, method, action, groupid deleted attachkey, attachpresent, individualshare, Note Type, noalert Last Modified, Shared with Others, Last Password Changed, Created vulnerable, Auto Change Password supported, breached, Custom Template, Form Fields
cfbao/lastpass-vault-parser: Parse your LastPass vault and export to CSV files (github.com)
I’m going to spin up a demo account…
Because:
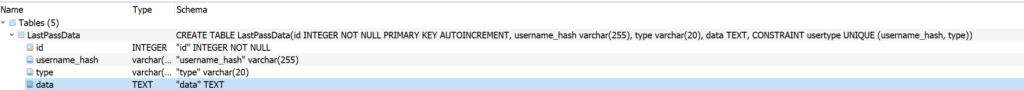
This is the database structure…
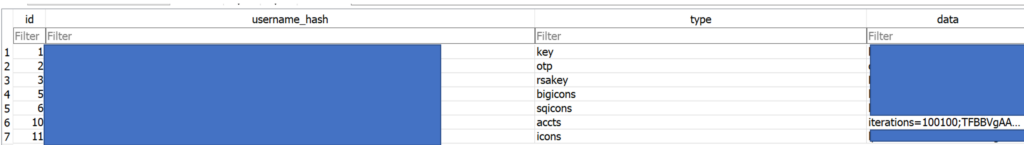
if we look at the data this is what is inside the “LastPassData” table…
ok……
this isn’t a vault…. it’s something else…. it’s an open ish book with some encrypted lines….
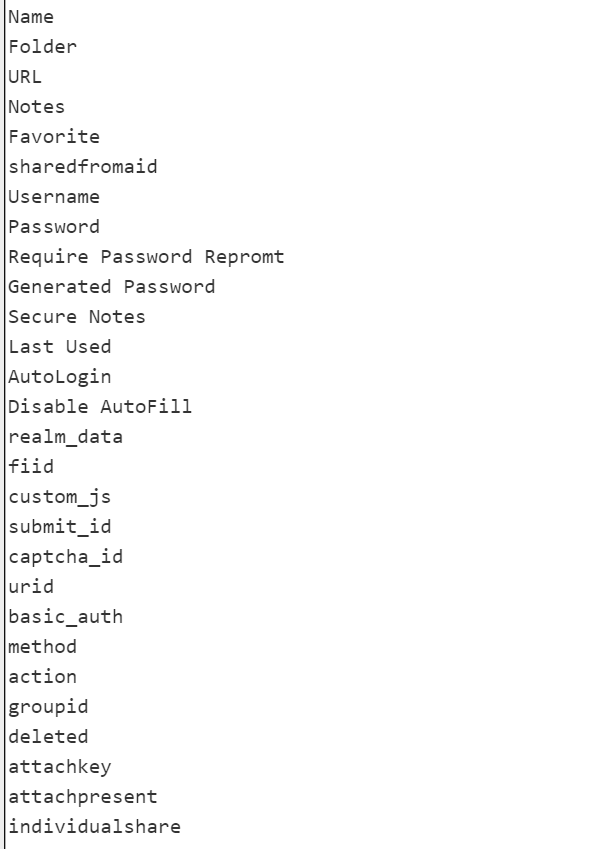
I am out of energy… the VAULT is really not one… the encrypted data might be safe… the metadata (and there is quite a lot of it) is not…..
I’m out! Time to go tear down other options! It’s time for me to #LeaveLastPass
Merry Christmas all! I wonder what other Cyber Gifts we shall get? #Ducks








