 Guides
Guides
Introduction
MFA was the “silver bullet” but friction and security kind of go hand in hand, the idea of a push notification and simple “authorise” is great in theory, but in practise it is vulnerable to brute force and human error. In this post we are going to check out enabling number matching authentication in Azure.
This is just one configuration option, as you can see there are loads of options for methods and specific configurations. Bear in mind the pros and cons for each one, for example SMS based 2FA can be vulnerability to SIM swapping attacks. I’m going to focus on Number Matching in Authenticator for this post:
Procedure
Log into the azure portal
Navigate to the security blade:
https://portal.azure.com/#view/Microsoft_AAD_IAM/SecurityMenuBlade/~/GettingStarted
Navigate to authentication methods:
https://portal.azure.com/#view/Microsoft_AAD_IAM/AuthenticationMethodsMenuBlade/~/AdminAuthMethods
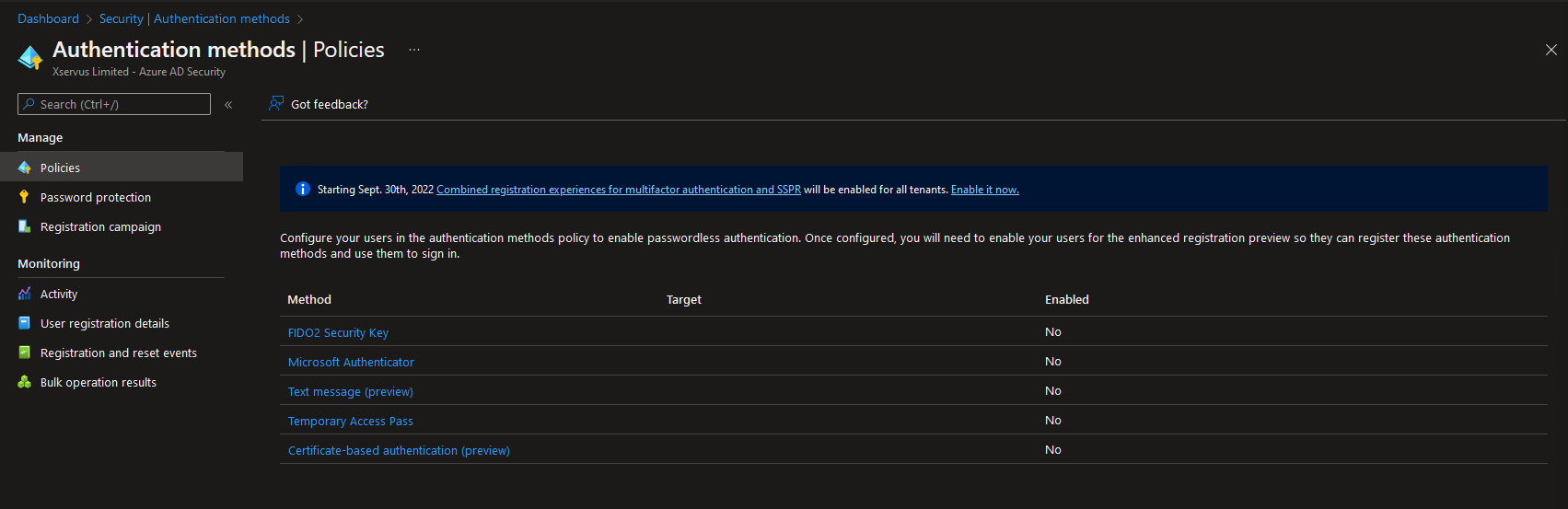
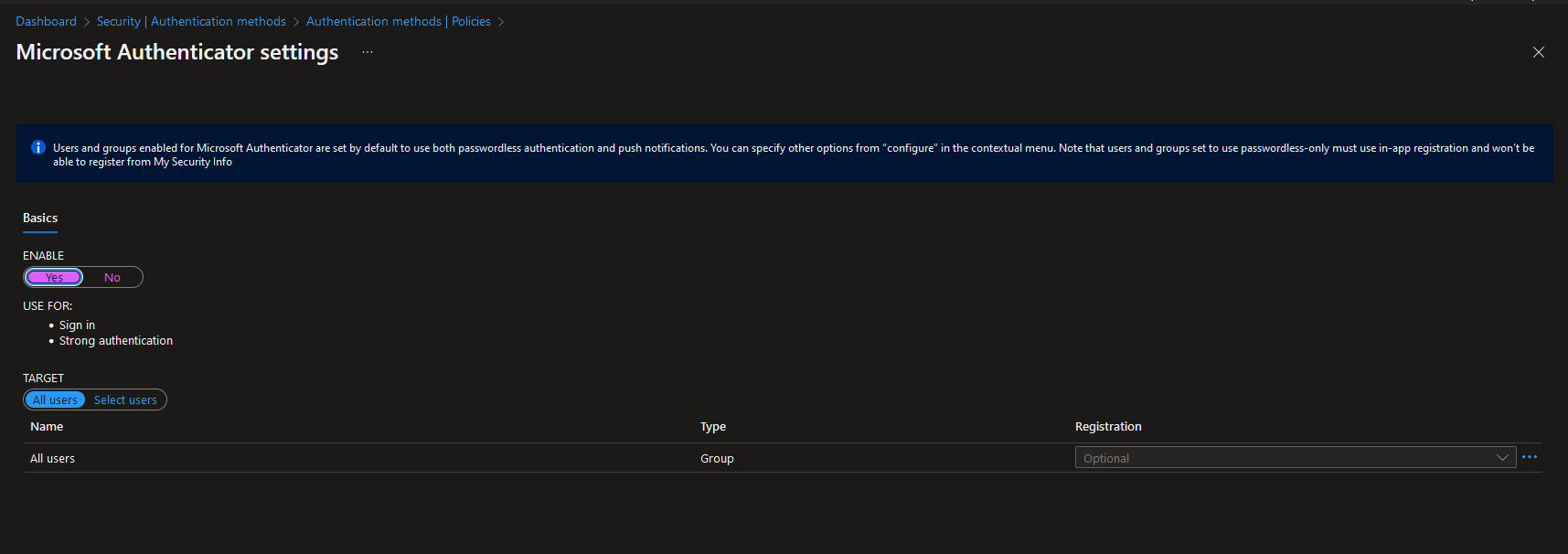
You can then enable MFA
But also, you can configure it on the right-hand side next to Registration there are three dots!
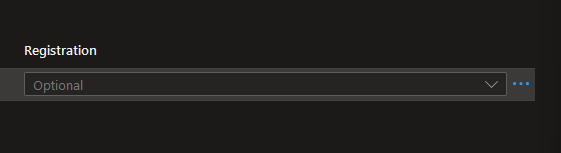
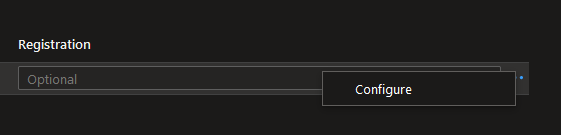
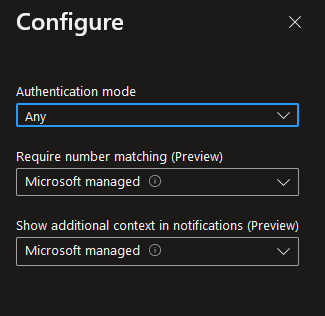
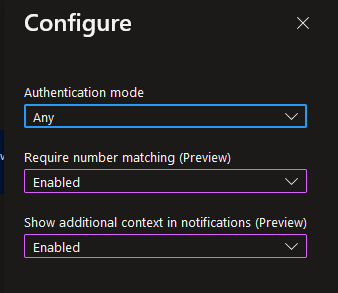
Don’t forget to click SAVE when you are done!
Now let’s test this:
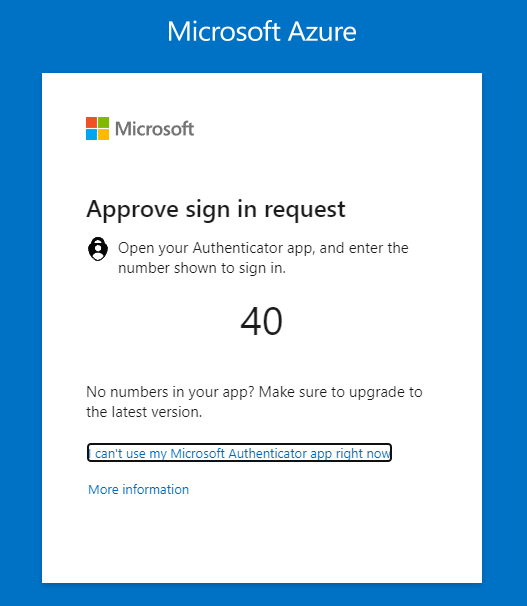
Now we can review more context information:
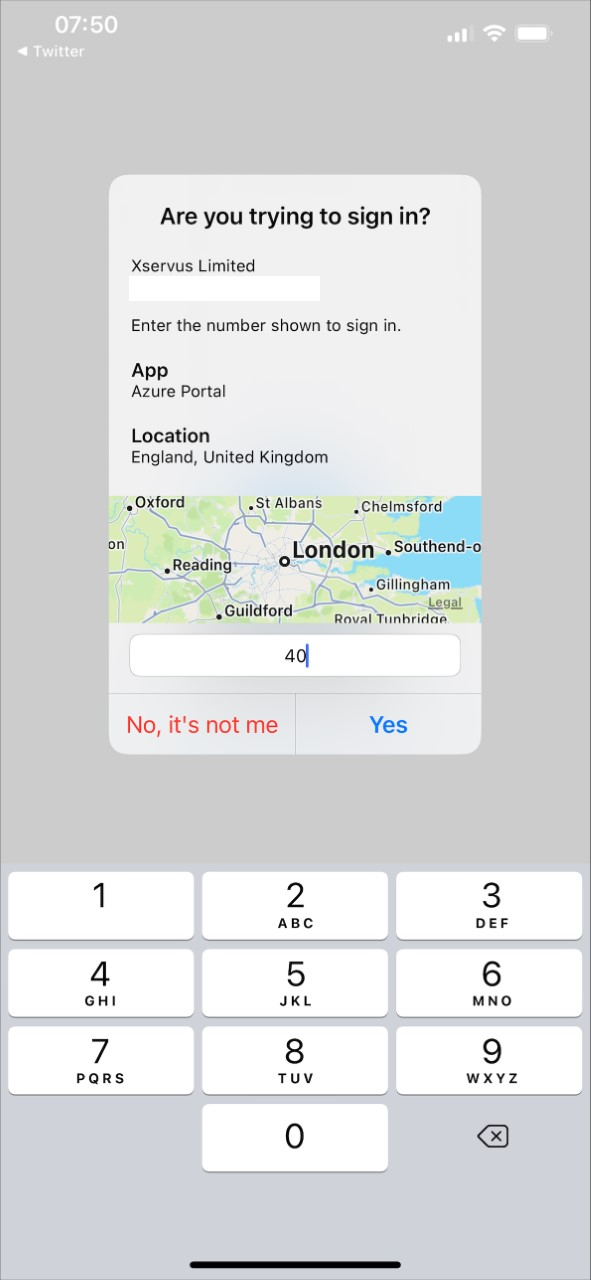
Summary
This is improving our attack surface, it’s making it harder to just “accept” and it’s providing us context for the sign in, fantastic! This is really a great feature improvement, it’s becoming the default and will help protect your organisation. What are you waiting for? Start working on those stakeholders and getting comms going ready to roll this out, it might be the barrier between you and a cyber incident!
There’s tons of features and configurations possible in Azure, keep working on improving your security configurations and enabling security visability, trust me, it’s more fun than responding to incidents!
References
And here’s some links to show that it’s not just me saying this
https://docs.microsoft.com/en-us/azure/active-directory/authentication/how-to-mfa-number-match









