 Guides
Guides
Ever stuck in an environment where your internet access isn’t what you want it to be? Ever need to exfilrate data and bypass some DLP? Obviously I’m talking like a pentester (don’t use this if it beaks policies on anohers assets) so this is useful for some scenarios in testing but also in real life!
How to Guide
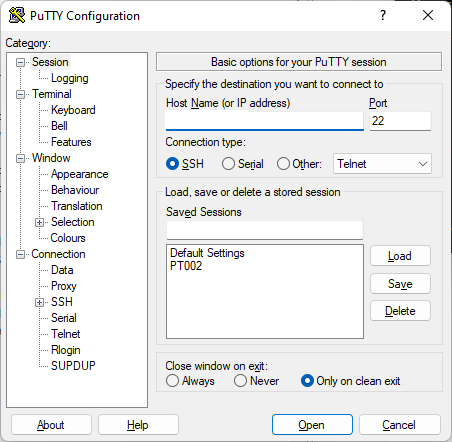
- Run Putty
- Configure an SSH Session
- OPSEC note, if you save the session it leaves evidence, might sound obvious but you know fingerprints are real!
- Goto SSH > Tunnels and configure as required
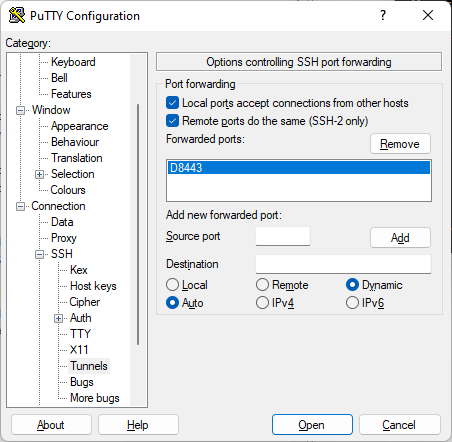
- Key point here is to use DYNAMIC for destination and to configure a source PORT e.g., 1337 (TCP)
- Finaly when you are happy with the configuration click Add
- Now connect to the SSH Server
- Reconfigure your browser/system to use the SOCKS5 proxy 127.0.0.1:1337
- Browse the internet
You can use a service like https://ipinfo.io to check your ip address.
You can also use PLINK!
https://www.chiark.greenend.org.uk/~sgtatham/putty/
Remember a SOCKS proxy works with TCP and UDP (works for DNS etc) so you can use them to pivot around networks as well as evade traffic controls (in some instances).








