 Defence
Defence
Working out what exploits to care about is a tough job, kill chains, availability of exploits, complexity, data flows, controls etc. all play a part in understanding a vulnerability and how it affects your organisational risk. To support this effort I’ve started to compile a list of public exploits against CISA Known Exploited Vulnerabilities (KEV). This may be useful for defensive and offensive security pros.
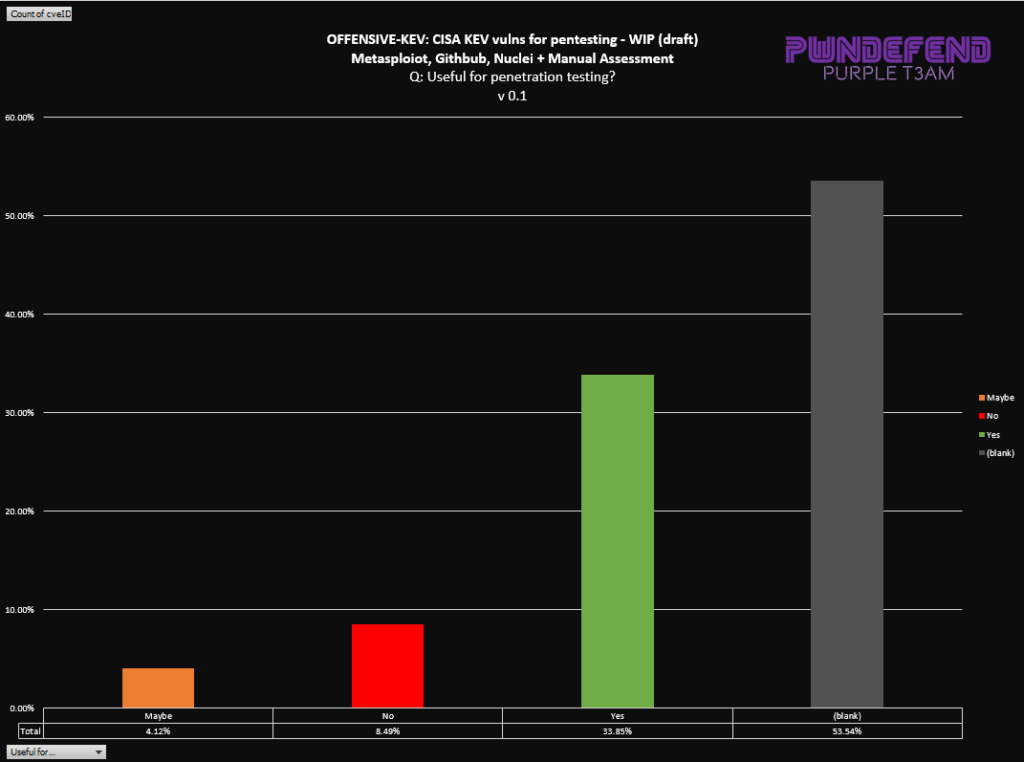
USE AT OWN RISK! I have not validated and vetted any of the links on the workbook!
Thoughts and feedback welcome, hit me up on Twitter!
Be safe!







