 Defence
Defence
Life in the vulnerability and exploit space is never dull
Spotted on twitter (thanks Danny!):
CISA updates the known exploited vulnerabilities list (KEV) yesterday with another 38 updates!
That means an update is required for OFFESNIVE KEV!
|
CVE |
Vendor |
Product |
|
CVE-2022-30525 |
Zyxel |
Multiple Firewalls |
|
CVE-2022-31460 |
Owl Labs |
Meeting Owl Pro and Whiteboard Owl |
|
CVE-2019-7195 |
QNAP |
Photo Station |
|
CVE-2019-7194 |
QNAP |
Photo Station |
|
CVE-2019-7193 |
QNAP |
QTS |
|
CVE-2019-7192 |
QNAP |
Photo Station |
|
CVE-2019-5825 |
|
Chromium V8 Engine |
|
CVE-2019-15271 |
Cisco |
RV Series Routers |
|
CVE-2018-6065 |
|
Chromium V8 Engine |
|
CVE-2018-4990 |
Adobe |
Acrobat and Reader |
|
CVE-2018-17480 |
|
Chromium V8 Engine |
|
CVE-2018-17463 |
|
Chromium V8 Engine |
|
CVE-2017-6862 |
NETGEAR |
Multiple Devices |
|
CVE-2017-5070 |
|
Chromium V8 Engine |
|
CVE-2017-5030 |
|
Chromium V8 Engine |
|
CVE-2016-5198 |
|
Chromium V8 Engine |
|
CVE-2016-1646 |
|
Chromium V8 Engine |
|
CVE-2013-1331 |
Microsoft |
Office |
|
CVE-2012-5054 |
Adobe |
Flash Player |
|
CVE-2012-4969 |
Microsoft |
Internet Explorer |
|
CVE-2012-1889 |
Microsoft |
XML Core Services |
|
CVE-2012-0767 |
Adobe |
Flash Player |
|
CVE-2012-0754 |
Adobe |
Flash Player |
|
CVE-2012-0151 |
Microsoft |
Windows |
|
CVE-2011-2462 |
Adobe |
Acrobat and Reader |
|
CVE-2011-0609 |
Adobe |
Flash Player |
|
CVE-2010-2883 |
Adobe |
Reader and Acrobat |
|
CVE-2010-2572 |
Microsoft |
PowerPoint |
|
CVE-2010-1297 |
Adobe |
Flash Player |
|
CVE-2009-4324 |
Adobe |
Acrobat and Reader |
|
CVE-2009-3953 |
Adobe |
Acrobat and Reader |
|
CVE-2009-1862 |
Adobe |
Acrobat and Reader, Flash Player |
|
CVE-2009-0563 |
Microsoft |
Office |
|
CVE-2009-0557 |
Microsoft |
Office |
|
CVE-2008-0655 |
Adobe |
Acrobat and Reader |
|
CVE-2007-5659 |
Adobe |
Acrobat and Reader |
|
CVE-2006-2492 |
Microsoft |
Word |
|
CVE-2022-26134 |
Atlassian |
Confluence Server/Data Center |
https://www.cisa.gov/known-exploited-vulnerabilities-catalog
you can subscribe to updates on KEV on the CISA site which is super cool.
I’ll look to update OFFENSIVE-KEV tonight with more public exploit/poc intel.
You can see already some of these are metasploit modules
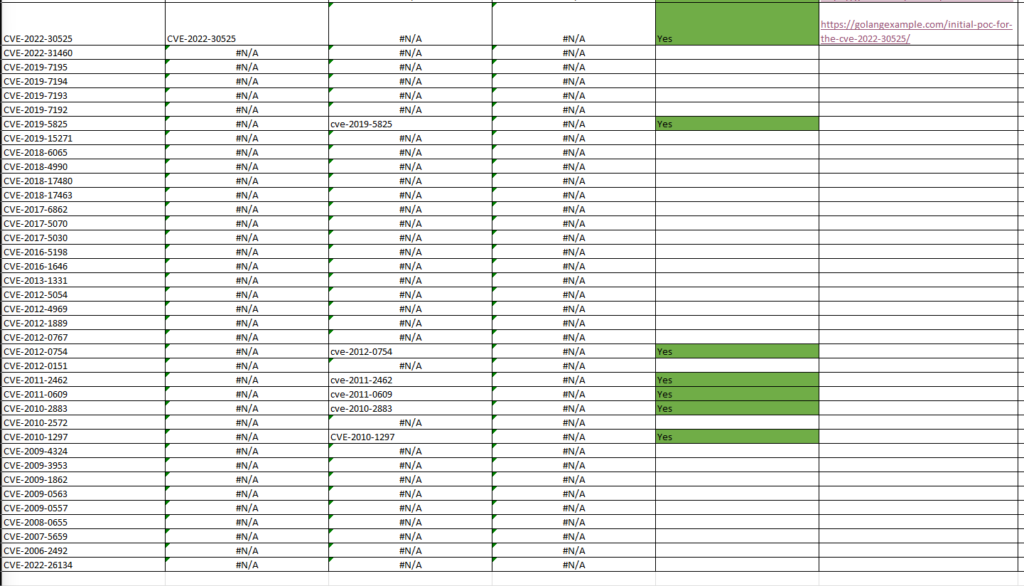
 you know that all the infosec pros have to read every one…. well ones relvent to their environment/scope….
you know that all the infosec pros have to read every one…. well ones relvent to their environment/scope….  x
x 






