 Guides
Guides
New machines means it’s easy right?
Ok, another post on cyber essentials! I talk about this quite a lot (mainly driven by procurement requirements rather than orgs expressing a deep desire to “have better security” (which is a shame)) however, I want to show people what the real world is like and that meeting cyber essentials is a good thing, but also to look at real world challenges of meeting the standards. In this post we look at some thought provoking questions, then we look at an out of the box Windows and MAC device to see if they meet the standard!
Five Technical Control Themes
Cyber essentials spans across these five areas:
- firewalls
- secure configuration
- user access control
- malware protection
- security update management
Key Questions to get you thinking
Ideally please read the actual guidance from the standard, however I’ve tried to boil down this into some areas of thought (these should not be considered THE STANDARD as lots of this requires context to the environment and the official standard, they are however here to get you thinking!)
(The guidance is here: Cyber-Essentials-Requirements-for-Infrastructure-v3-0-January-2022.pdf (ncsc.gov.uk))
- Are all PC/Server OS patches deployed to the latest levels?
- Are all PC/Server applications patched to the latest supported levels?
- Are all critical security patches applied within 14 days to all devices (PC/Servers/Routers/Mobiles/Tablets/Thin Clients etc.)?
- Is the BIOS (Firmware) up to date on PCs?
- Are all deployed software items authorised? (Do you have an inventory of everything?)
- Is at least one of the following deployed?
- Is application “allow” listing used to control application execution on devices, and digital signature execution enforced?
- Is antimalware software deployed in a secure configuration?
- Is application sandboxing leveraged?
- Are URLS checked to see if they are known to be malicious before connecting to them? E.g., SmartScreen or google safe browsing etc.?
- Is all software in the environment licensed and supported?
- Is the host-based firewall enabled?
- Do all PC devices have antimalware enabled?
- Do all PC devices have up to date antimalware signatures?
- Do PC devices have an account lockout policy configured to reduce the likelihood of brute force attacks (lockout must occur after no more than 10 failures)?
- Do PC devices have a password policy that makes passwords difficult to guess?
- Do PC devices have a minimum password length of 12 characters (or is MFA in place for authentication)?
- Are separate accounts for admin activities used?
- Have all default passwords been changed?
- Does it allow risky egress to the internet (e.g., TCP 445)? (Optional)
- Is full disk encryption enabled on all PC devices? (e.g., BITLOCKER)
- Is the perimeter firewalls firmware/software up to date?
Backups
Backup is NOT currently a requirement of the standard however there is now guidance in cyber essentials covering backups.
Looking at a single PC Device
Ok so here is our imaginary “workgroup PC scenario” we have a Windows 11 PC device:
It has windows defender installed by default (which automatically updates) and smart screen is enabled. This meets the minimum requirements for ANTIMALWARE secure configuration.
The single account created during out of the box setup has administrator rights. So, we would need to configure a local admin and a local standard user account (or configure Microsoft accounts in this dual role model)
We would need to re-configure the local password police as by default it is this:
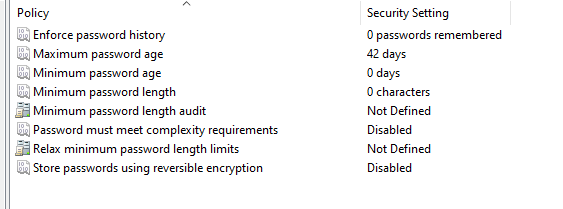
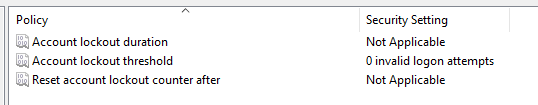
We would also need to configure the account lockout policy as the defaults don’t meet the standard:
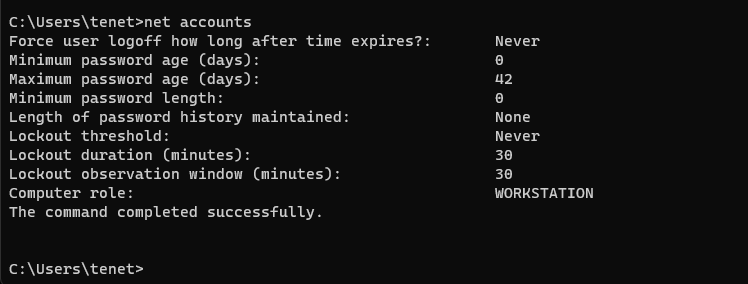
You can check this on the CLI using “net accounts”:
The windows firewall is enabled; however, it does allow risky egress (that is not however a requirement of the standard to block this, however it is good practise).
So As Egress filtering isn’t specifically “in scope” but I could argue it’s contextual we can use this powershell (from here)
to check:
| 1..1024 | % {$test= new-object system.Net.Sockets.TcpClient; $wait = $test.beginConnect(“allports.exposed”,$_,$null,$null); ($wait.asyncwaithandle.waitone(250,$false)); if($test.Connected){echo “$_ open”}else{echo “$_ closed”}} | select-string ” “ |
Ideally no ports will be open, and you are using a proxy, but otherwise you really want to limit egress normally to: TCP 80 and TCP 443. A risky port for example would be TCP 445 or TCP 3389.
Windows update will manage the OS updates so that part is covered to some extent but make sure you audit the configuration:
Get-ChildItem -Path "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto Update" -Recurse
Get-ChildItem -Path "HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU" -RecurseThird party apps are another question!
The firmware of the device likely needs updating (this may be covered by Windows Update) however here is an example from an HP device:
| Get-WmiObject win32_bios | select -Property SMBIOSBIOSVersion |
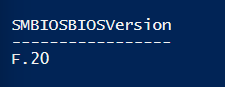
In this example the BIOS is not the latest version.
And we also should check and inventory installed software, this part isn’t very simpe either:
Get-CimInstance -Class Win32_ProductThat will do “some” of the work but you really need to check binaries on the file system etc. as well.
We also need to check for ingress (from the internet) on our public IP so let’s head to GRC SHIEDS Up (I won’t screenshot that here) but we see all ports are STEALTH.
There is an interesting question in the standard it says, “where you are able to do so, have you removed or disabled all software and service that you do not use (including cloud services) day to day”. This area in my experience is very hard to show/do.
So, this PC has overall likely NOT met the standard!
A MAC life for ME!
Dual Accounts & Password Policies/Lockouts
Ok let’s try with a new out of the box (yesterday) MAC
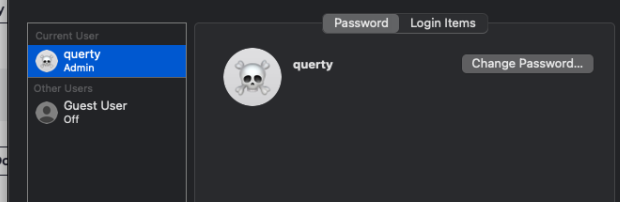
Out of the box our account has administrator rights so we would need to change that (root) to a dual account model.
You can also see the password policy and account lockout policies are not in alignment with the standard, the STIGs have good guidance on this:
The macOS system must enforce a minimum 15-character password length. (stigviewer.com)
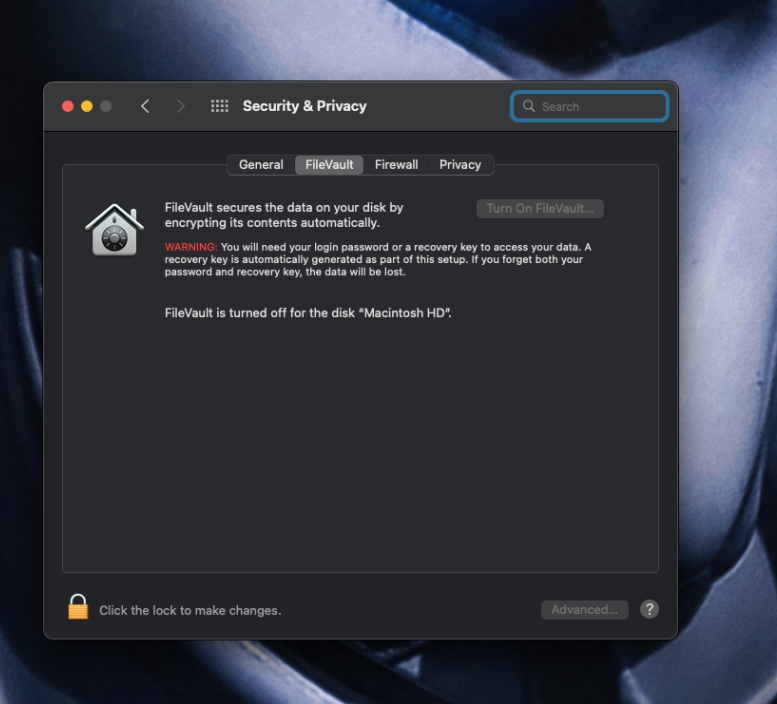
Disk Encryption
Disk encryption whilst not in the standard is a good practise, by default it is not enabled:
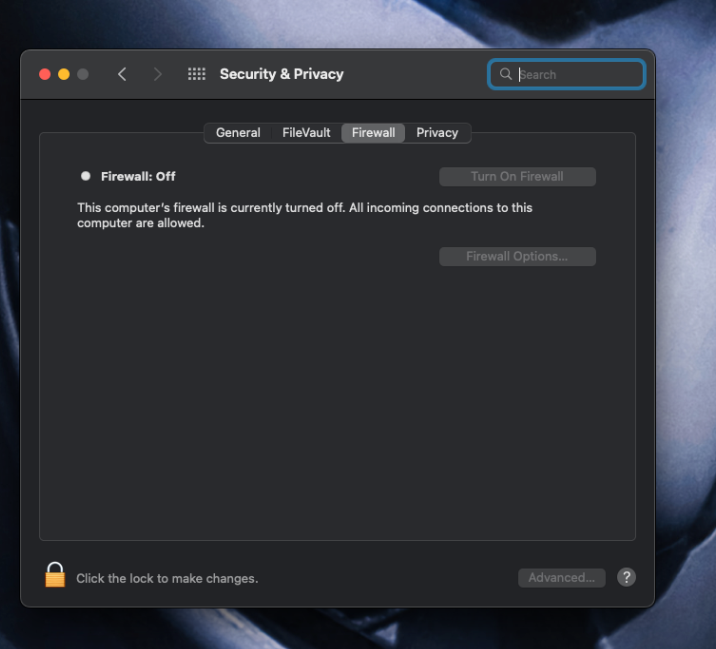
Firewall
By default, on OS X the firewall is NOT enabled:
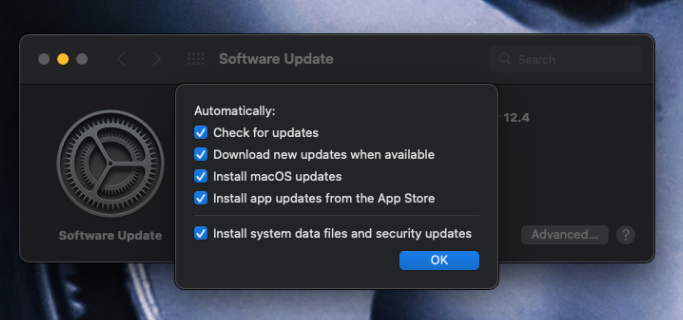
Software Updates
By default, software updates for the hardware and OS “should be ok”
Antimalware
- Antimalware is not included with OS X.
- Egress filtering with safari does however come with Safe Browse enabled
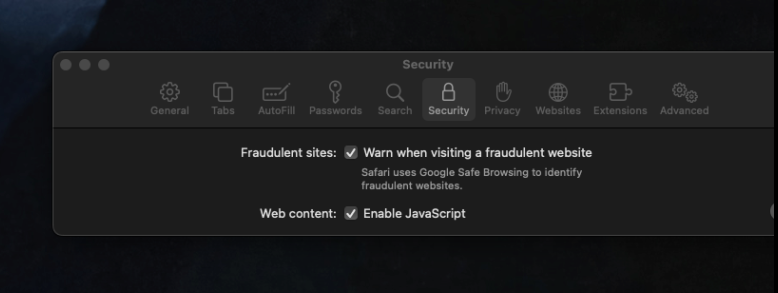
Software Inventory
We can inventory applications via the CLI:
ls -la /Applications/To get all the version we can use the SYSTEM information report (click on the APPLE ICON – “about this mac” and then SYSTEM REPORT)
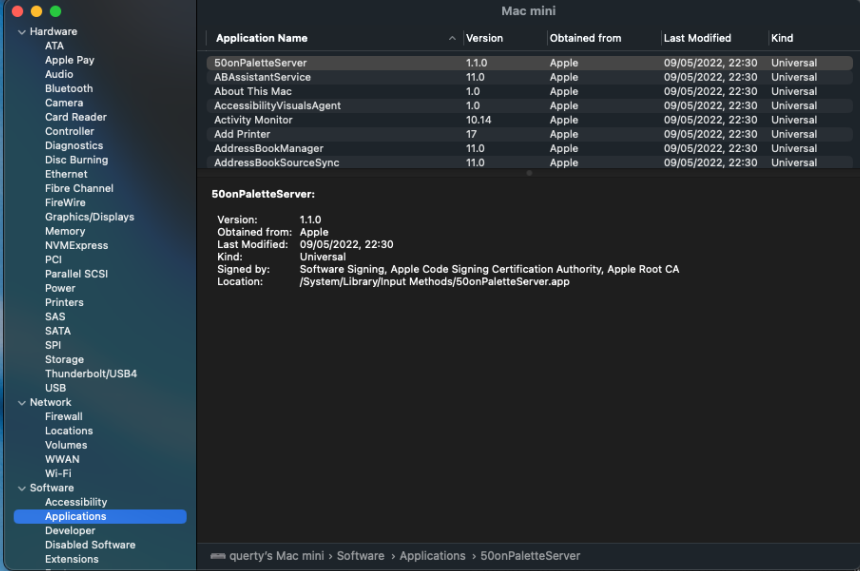
You can also run the system profiler command:
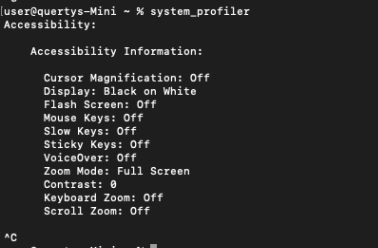
You can also enumerate via other CLI methods using cat grep etc.
Summary
As you can see, I’ve got two devices here in the lab that fail, and that out of the box, both with a PC device running windows or OS X, both don’t come out of the box meeting “cyber essentials”. I’ve not looked at the network but I bet if we zoomed around lots of orgs and home working environments we would find routers and devices with default admin creds and risky ingress in some (random thing, I did some research once and found thousands of people with firewalls (with residential IPs) that restrict ingress inside an org so that was good). So really, what does this show? Well it show’s that CYBE ESSENTIALS is not always simple or easy (that’s a good thing) and it also show’s that auditing for CE requirements isn’t just a tick box affair (it actually required work.. shocker right!) and it shows how at scale organisations should take a proactive approach for cyber security and technology management.
Cyber essentials is a good starting bar for improved cyber security posture, it’s improved over the years as well and I hope it continues to expand and include more capabilities such as backup being part of the standard! CE is positive for the industry and community because it’s helping make a difference, I just worry that orgs use it as a goalpost rather than aiming for better security both to meet but also exceed “the essentials”.








