 Leadership
Leadership
Introduction
This post stated out as a technical post about commonalities found in the field that vary based on business operating model, IT capability and vectors used by threat actors. Whilst writing this it led more into business leadership, governance and investment risks. How do these two subjects’ interface? Well to be honest they are the same thing from a different lens.
In this post we are going to look at:
- Common Technology Deployment Models and the associated threats/risks/vulnerabilities
- Common challenges I find in organisations
- And finally, a question… is this the business outcome that you want
Common Technology Deployment Models
Typically, organisations will have three high level “models” of technology landscape, regardless of vertical, size and scale. These are:
- Cloud first
- Hybrid
- Traditional
Most organizations sit in the hybrid space however there are some key common technology deployments that should be considered. This is important, cyber capabilities must be aligned to the business (much the same as technology capabilities)
Operating Models
Organisations leverage a range of technology and have different operating models:
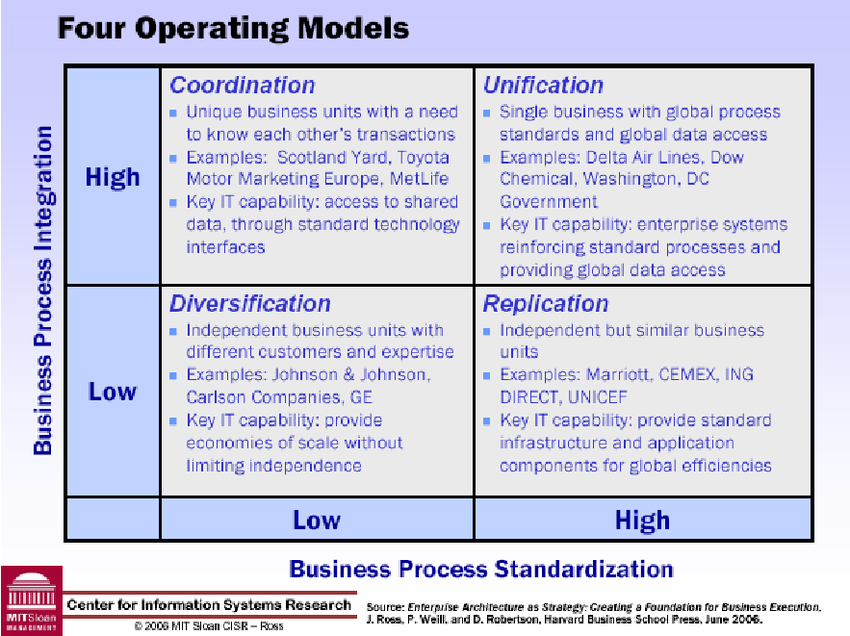
- Coordination
- Unification
- Diversification
- Replication (Franchise)
Commonly the operating model of a business will give an indication as to the technology architecture in play. Based on these generalisations we can produce a high-level threat view based on known common technologies and architectures.
Common Across All models
Almost all organisations will have the following threat vectors:
- Email Based (phishing etc.)
- Social Engineering
- Internet Based Threats (DDoS, Provider Availability
- Web Based (Common web vulnerabilities e.g., SQLi, XSS, CSRF, injections)
Technology Focus
For the scenarios I’m going to look at common corporate and third sector deployments that I’ve seen/worked with in the field. There’s obviously edge cases and unique specifics per organisations, but the aim here is to talk about most of the technology I see.
Cloud First
|
Identity and Access Management |
Office 365/Azure Directory Services |
|
Configuration Management |
Microsoft Intune (MDM) |
|
Antivirus |
Windows Defender, Sophos, Trend, Webroot |
|
EDR |
Sentinel One, Sophos IX, Microsoft MDE (ATP) |
|
Sales |
Salesforce, Dynamics CRM |
|
Marketing |
HubSpot, WordPress, Hosted Website |
|
Document Management |
SharePoint/SharePoint Online |
|
Mail Security |
Mimecast, Outlook Protection |
|
Internet Access Model |
NAT |
|
Iaas/PaaS |
Azure and AWS |
|
Endpoints |
Largely Windows but with Mac and Linux |
Hybrid
|
Identity and Access Management |
Active Directory Domain Services (ADDS), Azure AD Connect, Office 365/Azure Directory Services |
|
Configuration Management |
Microsoft Intune (MDM), SCCM |
|
Antivirus |
Windows Defender, Sophos, Trend, Webroot |
|
EDR |
Sentinel One, Sophos IX, Microsoft MDE (ATP) |
|
Sales |
Salesforce, Dynamics CRM |
|
Marketing |
HubSpot, WordPress, Hosted Website |
|
Document Management |
SharePoint/SharePoint Online |
|
Mail Security |
Mimecast, Outlook Protection, Exchange, Trend Mail Protection, Barracuda |
|
Internet Access Model |
NAT, on-premises web proxy or cloud proxy (e.g., Zscaler) |
|
Iaas/PaaS |
Azure and AWS |
|
Endpoints |
Largely Windows |
|
VPN |
Edge Device |
Traditional
|
Identity and Access Management |
Office 365/Azure Directory Services |
|
Configuration Management |
Microsoft Intune (MDM) |
|
Antivirus |
Windows Defender, Sophos, Trend, Webroot |
|
EDR |
Sentinel One, Sophos IX, Microsoft MDE (ATP) |
|
Sales |
Salesforce |
|
Marketing |
HubSpot, WordPress |
|
Document Management |
SharePoint |
|
Mail Security |
Mimecast, Outlook Protection, Exchange, Trend Mail Protection, Barracuda |
|
Internet Access Model |
NAT or on-premises web proxy |
|
Iaas/PaaS |
Azure and AWS |
|
Endpoints |
Largely Windows |
|
Servers |
Largely Windows Server with Linux Appliances |
|
VPN |
Edge Device |
Key Areas of Security Consideration
Cloud First
- Phishing
- Business Email Compromise
- Device Compromise (PC and Mobile)
- Credential Compromise leading to Platform compromise
- Internet Facing Web Applications
- Sensitive Data Leakage/Loss
- Office 365
Hybrid
- VPN Devices
- Azure AD Connect
- Active Directory Domain Services
- Microsoft Exchange
- Office 365
- Backup Services
Traditional
- DMZ Hosted Services
- VPN Devices
- Azure AD Connect
- Active Directory Domain Services
- Microsoft Exchange
- Office 365
- Wireless
- Physical (loss of equipment/data/documents)
- Backup Services
Models
Ok so why are these important? Well one of the first rules of security is that you need to know what you are protecting, it’s value, it’s vulnerabilities and who/what might be trying to exploit them. What I’m showing here is commonality in landscape. I’m not going to go into technical details but there are common routes that attackers use to create impact.
“BIG” Risks
There are a ton of risks ranging from cyber through to environmental, all of which can cross the CIA triad, I’m not trying to list every possibility, I’m going to try and focus on the larger scale impact things to consider, such as:
- Business Email Compromise
- Supply Chain Threats/Pivots
- Scammers and Fraud
- Infrastructure and Service Abuse
- SPAM
- BEC/FRAUD pivot
- Proxying attacks via your infrastructure (e.g., Open Redirects or pwned servers)
- Ransomware
- Extortion
- Wipers
- Denial of Service (Dos)
- Intellectual Property and Sensitive Data Theft
- Insider threat
- External Threat (Cybercrime)
- External Threat (Corporate Espionage)
- Contractual Breach
- Legal and/or Regulatory Breaches
- Loss of PII
- Breach of contracts
- Brand and Reputation Damage
- Human Error
- Hardware failures or environmental failures
As you can see there are a lot even when we look at the Macro level. Let’s think about some of the impacts these can cause.
Impacts and Costs
There are a range of areas where cyber events, alerts and incidents cause impact/cost:
- Loss of productivity
- Loss of revenue
- Loss of potential revenue
- Contractual SLA breaches leading to costs
- Contractual reporting and audit requirements
- Legal costs
- Regulatory costs
- Cost of Incident Response
- Cost of countermeasures
- Staff Attrition
Cyber Realities
Often people seem to assume that “Cyber” is just part of the “things the IT department look after”. I’m about to burst a bubble here, but in ~90% of organisations I’ve worked with over the last 20 odd years that simple isn’t the case. Nor is “cyber security” usually in a good state when the “networking team” are responsible for it.
Commonly I see these realities:
- Weak external postures
- Shockingly weak Active Directory Domain Services and associated services (e.g., ADCS, AD Connect, Exchange, SharePoint) security postures
- Weak endpoint security
- Flat networks
- Flat Clouds (a single tenant/account deployed to hold “all the things”
- Lack of logging, monitoring or alerting across the enterprise technology stack
- Lack of Incident Response planning and capabilities
- Reliance upon alerts from Antivirus tools
- A lack of web content filtering
- Weak supply chain security assurance
- Unpatched software vulnerabilities
- Insecure and out of support firmware and hardware
- Weak egress controls
- Security configurations deployed in a “hostile to administer” model, yet without stopping real life threat vectors
- BYO nightmares (BYO is normally a security nightmare)
- Lack of strong authentication controls (e.g., MFA)
- Weak passwords
- Poor operational security practises
Challenges
The challenges I see in organisations can be summarised as:
- Lack of a business aligned IT Strategy
- Lack of Cyber Strategy and certainly a lack of business alignment to tactical controls
- Lack of Cyber Budget and Portfolio management
- Lack of understanding from boards on the investments, ROI and value delivered (or potential to deliver) from cyber capabilities
- Overstretched IT teams
- Under resourced IT teams
- A significant shortfall on specialist training, yet a focus on delving CBT to tell people to “stop clicking on malicious links (like someone can really tell all the time!)
- A absence of security team or a security “team of one”
At the heart of a cyber security strategy is the following:
- Leadership Support and Commitment
- Resources (money, tools, facilities)
- People (skilled, motivated and dedicated personnel)
The cost of “Cost Avoidance”
When I work with organisations I try and understand the following:
- What is the current state landscape?
- What is the posture?
- How did it get this way?
- The historic reasons for current state are important context to ensuring the target state does not suffer the same issues (in the negative current posture scenarios, which is MOST organisations current state)
- Where is the business heading?
- What does the business need to succeed in that journey?
- How do we enable cyber security to be aligned to the business and deliver ROI beyond “simply an insurance policy”?
Largely I find two major themes:
- Risk acceptance through ignorance (Not wilful)
- Cost avoidance
The challenge is, that approach may have been ok in the late 90s and early to mid-2000s. The reality today is that the threat landscape has changed, cybercrime is a HUGE business, and the targets of these threat actors are simply, anyone they can pwn. It’s not about “we have nothing of value” (seriously if that’s your business value pitch it’s a problem elsewhere!).
Outside of external threats and direct costs, there’s also large impact to cyber security incidents from an indirect cost perspective. There are also legal considerations (and an evolving regulatory requirement in many sectors). For the UK we must consider:
- Data Protection Act 2018
- PECR
- The GDPR
- Contractual Requirements
- Regulatory Fines
- Brand Damage
- Legal Costs
The world is increasingly reliant upon digital services, your organisation is reliant upon digital services. A strong security posture doesn’t occur by default or naturally, it requires work. You also need to have a diverse set of views; you don’t want everyone marking their own homework and feeding your corporate governance mechanisms a rose-tinted view on the world. Your corporate risk numbers may be far higher than your board or investors would really be comfortable with. This can affect the organisation in many ways, especially if you operate in the mergers and acquisition state, let alone from an insurance and customer due diligence perspective.
Summary
Cyber security isn’t a bolt on to business, it’s integrated into the world of digital business which every organisation these days is part of, from mobile devices, online banking, emails, web services through to VPNs, internal infrastructure, hosted applications etc. every organisation has a cyber security cost and impact, even when cost avoidance is the primary strategy or risk acceptance is the “commonly accepted” mode of operation.
There’s a lot more to Cyber Security value than simply insurance, it can be a business enabler through increased efficiency, increased productivity, reduced compliance, increased market presence, competitive advantage. Simply the value of cyber is business intelligence alongside risk reduction. Sure, cost avoidance and “hope” might work for a while, but the longer the avoidance, the harder the impact will likely bite. You wouldn’t let your car go to rot, nor want untrained mechanics working on it, so why are so many organisations’ leadership failing to invest in their cyber future?









