 Guides
Guides
Introduction
I come from a heavy Windows background, in fact I started my computer experience on an Amstrad however not long after I was using DOS and then Windows 3.11 for Workgroups. So, I’m a heavy Windows head, I’ve deployed all kinds of services and applications within business environments using common technologies such as:
- CISCO/DELL/HP Networking switches and routers
- ISA/TMG/UAG/Checkpoint firewalls
- Palo Alto Firewalls
- Microsoft Windows Client (Windows 3.11-Windows 11)
- Microsoft Windows Server (NT4 – Windows Server 2022)
- Vmware vSphere/ESXi
- Random Linux Security appliances and VPN devices
One thing that I’ve noticed in my travels so far is that Linux deployments in enterprise environments in the back office/corp nets are often appliance based or “black boxes”. This creates a bit of a fun scenario whereby some system administrators and operations teams aren’t particularly comfortable with using UNIX/Linus systems. So, I thought I’d try and write some content to show how to do common tasks using the command line interface (CLI). This isn’t designed as an indepth guide, this is really just to try and give people a view of some of the things that you will need to be aware of. This isn’t mean’t to be “academic” or replace manuals and technical docs so it’s brief and to the point (as far as that is possible).
Major Changes for Windows People
In Windows many things are case insensitive, such as usernames. In UNIX/Linux the file system is case sensitive. Running Uname will error vs uname which will show the OS version. This means some scenarios are case sensitive (file system access is for sure) but also usernames in some systems are as well.
Distributions
Linux comes in a ton of flavours there is even a Hannah Montanna flavour. Common distibutions are:
Red Had Enterprise Linux (RHEL)
- CentOS
- Debian
- Fedora
- Ubuntu
- MINT
- ARCH
Patching and Backporting
Patching and Upgrading in Linux is a bit bit different than Windows because there’s this thing called Backporting:
You need to watch out for this as version based enumeration can lead to false positives when conducting asset enumeration and vulnerability identification through version identification. Backporting is where a security fix or patch is backported into an older version of software. So the banner may say version 7.8 however the security fixes may have been incorporated and deployed (the ones that are in 7.9) so there’s some work to do to check and validate (and also demonstrate) things are patched.
Boot Types
- BIOS (BASIC INPUT OUTPUT SYSTEM)
- UEFI
https://wiki.ubuntu.com/UEFI/SecureBoot
Boot Loaders
The most common boot loader is GRUB.
There are others such as:
- BURG
- LILO
- SYSLINUX
https://en.wikipedia.org/wiki/Comparison_of_boot_loaders
File Systems
The common files systems are:
- EXT2
- EXT3
- EXT4
Other file systems include:
- XFS
- ZFS
There are other systems that can also be used.
A common disk encryption system is LUKS:
https://www.redhat.com/sysadmin/disk-encryption-luks
Volume manaement can be handled by Logical Volume Manager (LVM). LVM allows for dynamic volume management (thin of this a bit like using DYNAMIC disks in Windows).
File System Structure
Unlike Windows GNU/Linux systems use files for everything. There’s no concept of the registry like there is in Windows. In Linux configurations, metadata and data are stored in files. Some systems/application may use databases for configurations e.g., mySQL, postgres etc.
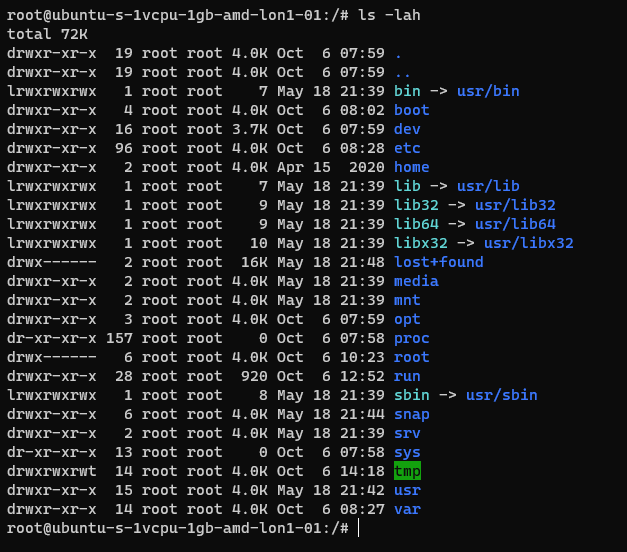
Here’s an example from an Ubuntu system:
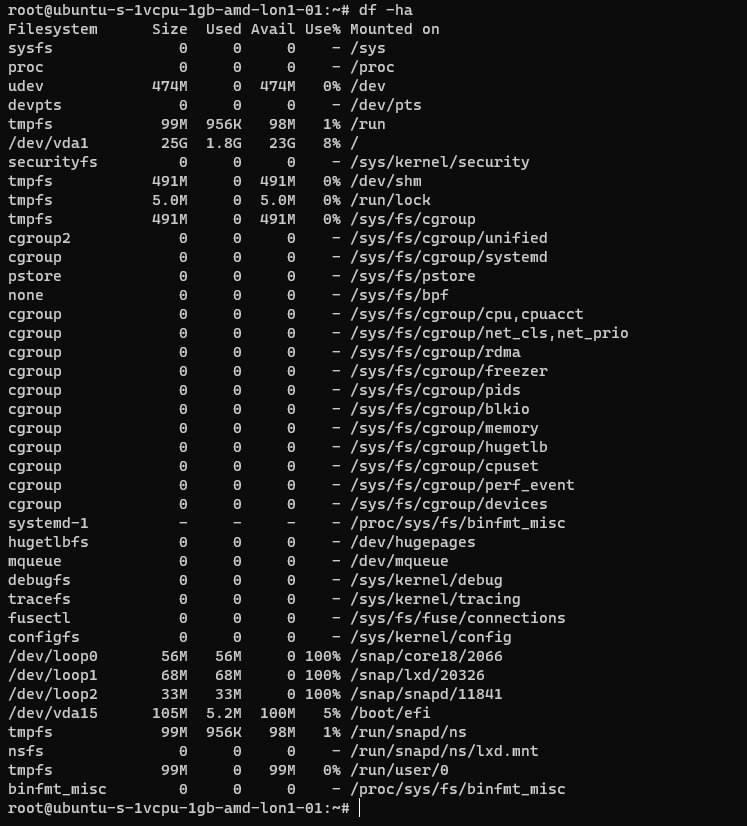
The following table is a summary of some common areas:
| Path | Purpose | Notes |
| / | Root | |
| /bin | Binaries for commands (Essential bins) | |
| /dev | Device files/devices | |
| /etc | System wide configuration | |
| /etc/opt | Optional Configurations | |
| /home | Home folders | |
| /lib | Libraries for binaries | |
| /media | Removable Media | |
| /mnt | Temporary File System Mount Points | |
| /opt | Software Packages | |
| /proc | A virtual file system for process and kernel usage | |
| /root | Root users home folder | |
| /run | Run-time variable data for users and daemons | |
| /sbin | System Binaries | |
| /srv | ||
| /sys | ||
| /tmp | Temporary files | |
| /usr | Read only user data | |
| /usr/bin | Non-essential binaries | |
| /usr/include | ||
| /usr/lib32 | User Libraries e.g. 32 bit | |
| /usr/local | Host specific data | |
| /usr/sbin | Non essential system binaries | |
| /usr/share | Shared data | |
| /usr/src | Source code and headers | |
| /var | Variable files e.g. log files | |
| /var/cache | Cache | |
| /var/lib/ | ||
| /var/lock | Lock files | |
| /var/log | Log files e.g. Apache, system etc. | |
| /var/mail | Mailbox data | |
| /var/opt | Optional variable data | |
| /var/run | Variable run time data | |
| /var/spool | Spools for mail and printers | |
| /var/tmp | Temporary files that remain between reboots |
Common Shells and Terminal Emulators
- Bash
- Oh My ZSH (ZSH)
- TMUX
- Konsole
- Terminator
Now when using ssh etc. the sessions are not resumable or sharable. So, you will see some cool tools here in the shape of:
- TMUX
- DVTM
- ABDUCO
- SCREEN
Package Managers
In Windows you have the Windows Installer Database and Windows Updates. In modern version of Windows you also have Windows Store and Chocolatey etc.
However, in Linux there is the concept of package managers. Common package managers include:
- DPKG
- RPM
Alongside package managers are dependancy resolvers (thanks Alex for this and other bits!)
- PACMAN
- YUM/DNF
- APT
Common Networking Protocols
- SSH
- SAMBA (Unix SMB/CIFS)
- FTP
- SFTP
- OpenLDAP
- VNC
- RDP
Desktop Window Systems (GUI)
Common guis (Windows Managers) include:
- GNOME
- KDE
There are quite a few of these get your google on!
Key Security Features
- Services
- CHROOT Jails
- Creates a false root directory for sandboxing
- Pluggable Authenticaiton Modules (PAM)
- Superuser Do/Substitute User Do (SUDO) – Like Windows Runas
- Access Control Lists
- IPTABLES
- UFW (Firewall)
- Audit D
- Malware Detection
- CLAM AV
- Remote Administration
- TELNET
- SSH
- VNC
- Remote Desktop Protocol
- SELinux
Common Administration Tasks
I’m using Ubuntu here, some distributions may use slightly different commands e.g. Arch uses PACMAN, Red Hat uses Yum.
| Task | command | Notes |
| Clear the screen | clear | Shortcut CTRL+L |
| List files | ls | |
| Switch User | su | |
| Run as root/other user | sudo | “super user do” was the traditional name now it’s “substitute user do” |
| Change directory | cd | |
| Make a directory | mk | |
| Move a file/directory | mv | |
| Remove a file | rm | |
| Remove a directory | rmdir | |
| Copy a file/folder | cp | |
| List OS Version | uname | |
| Read Help | help | |
| Read a manual | man | |
| Update Repositories | apt update | |
| Upgrade packages | apt upgrade | |
| Create an empty file | touch | |
| List directories and files | tree | |
| List disk space/usage | du | List estimated file usage |
| List | df | List file system usage |
| Change permissions | chmod | |
| Add a user | useradd | This is a very basic utility for creating users that only creates the user object |
| Add a user | adduser | This has more features and will create things such as the home drive |
| Delete a user | deluser | |
| Create a group | addgroup | |
| Delete a group | delgroup | |
| Modify a user | usermod | |
| Modify a group | groupmod | |
| List processes | ps | Common is: ps aux |
| Show the time | date | |
| Kill a process | kill | |
| List suspended processes | jobs | |
| Foreground a process | fg | |
| Edit text | vi or nano | |
| Show the current user | whoami | |
| Show the current date and time | date | date -d now |
| Display the top of a file | head | |
| Display the end of a file | tail | |
| Display a file in real time | tail -f | tail -f access.log |
| Print the working directory | pwd | |
| Set a variable | set | |
| List logged on users | w | |
| List logged on users with IP details | who | |
| Send a message to all logged on users | wall | |
| Output data to session | echo | |
| Send message to a user | write | |
| Reboot the system | reboot | |
| Power off the system | poweroff | |
| List the contents of a file | cat | |
| Ssh to another system | ssh@192.168.0.1 | You can use -I to specify private keys |
| See running processes and performance information | top |
Scheduled Tasks
Tasks in UNIX/LINUX are managed using CRON.
Parsing and Manipulating Text and Files
- cat
- sed
- awk
- grep
- find
- locate
- sort
- uniq
Daemons
A daemon is a background process, these are commonly used for services. E.g.
- SSHD is the Secure Shell Daemon.
- FTPD is the File Transfer Protocol Daemon.
System Service Control
systemctl list-units –type service
systemctl disable [service] –now
systemctl enable [service] –now
Common Networking Commands
- netstat
- ss
- tcpdump
- ufw
- iptables
- ip a (ifconfig on older systems)
- route
- nslookup
- traceroute
Common Linux Virtualisation Solutions/Platforms
- KVM
- Virtual Box
- ProxMox
- Vmware Workstation
- QEMU
Creating a new User
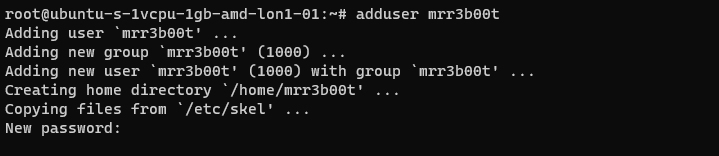
Using adduser we create a new user account. This utility also creates a new group and a home directory.
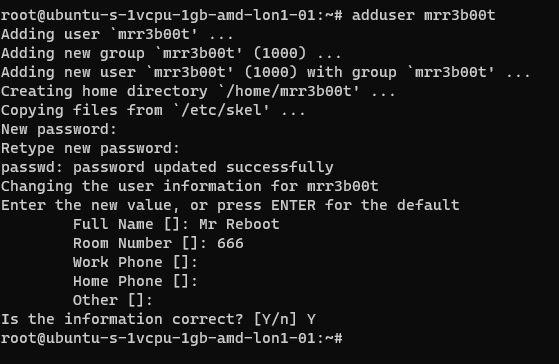
If we cat /etc/passwd we can see the new user:
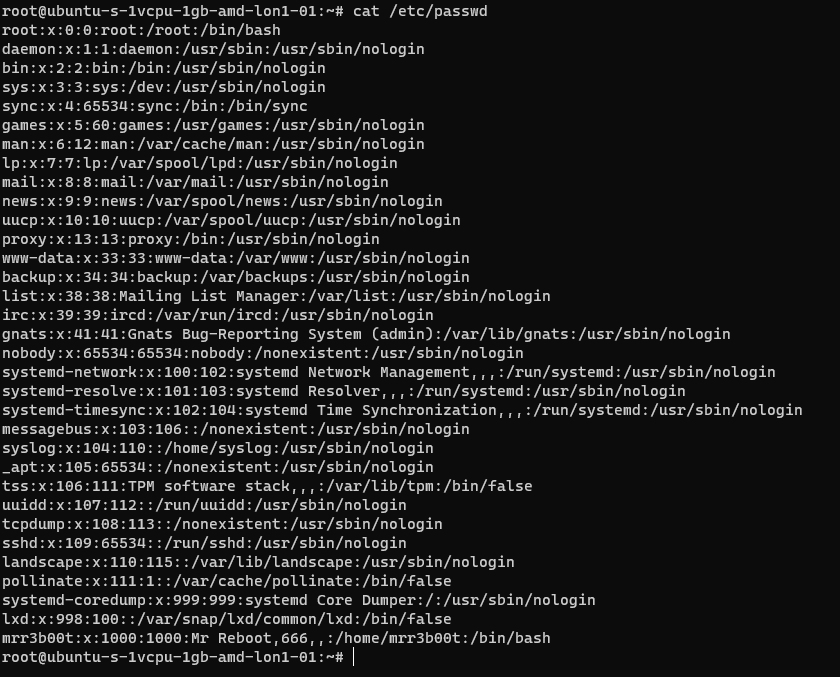
If we cat /etc/group
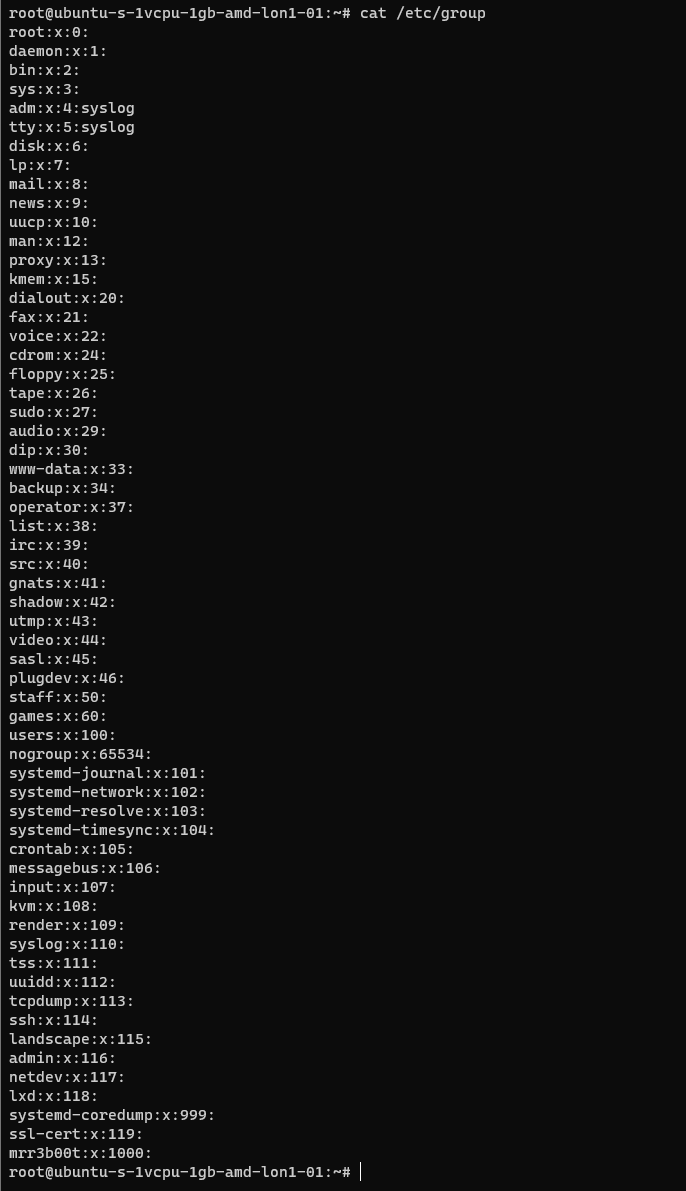
We can see the new group.
If we wanted to add mrr3b00t to root we would run:
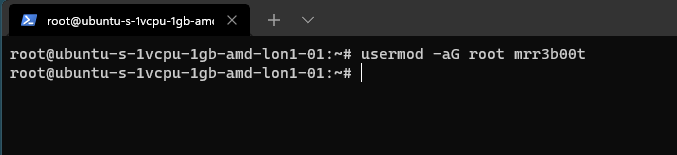
To remove the user from the group “root” we would run:
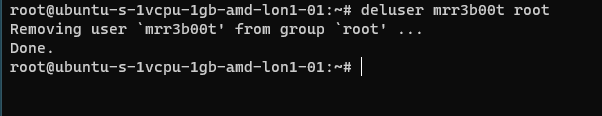
Using “su” we can switch to mRr3b00t:
File Permissions
Now the ACLs on Windows are slightly different. Let’s step through some permissions:
Permission Groups
- Owner
- Group
- All Users/Others
Permission Types
- Read (4)
- Write (2)
- Execute (1)
When we see permissions in Linux we see them in the following format:
[permission flag]rwxrwxrwx 1 owner group
Permission flags can be:
_ = nothing
d = directory
l = symbolic link
SETUID/SETGID and Sticky Bit
s = setuid or setgid (this is shown over [r] rather than in the first character)
t = sticky bit
Permissions are shown as:
Read [r] Write [w] execute[e]
These are important when we consider privilidge escalation. If these bits are set they will look like:
RWSRWSRWT
Or a variation of that pattern with S S and T
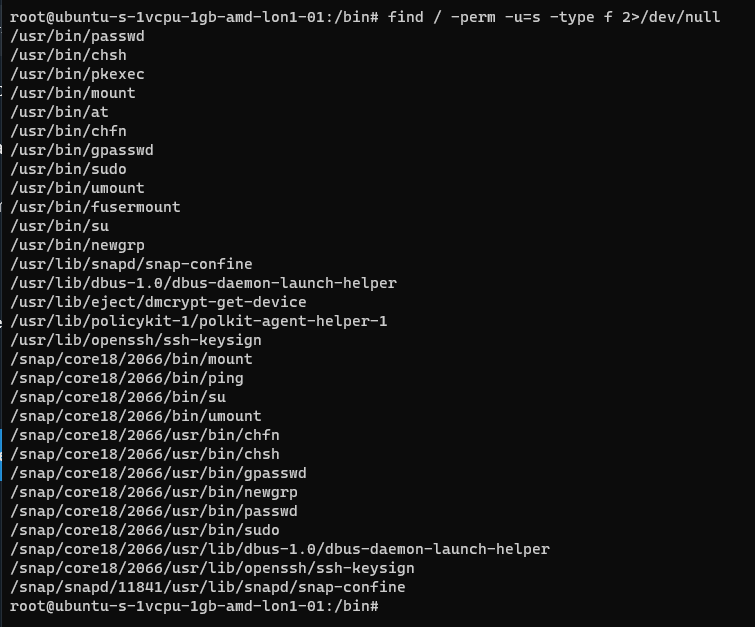
You can search for SUID bits using the following command:
| find / -perm -u=s -type f 2>/dev/null |
This will find any file (-type f) permissions with the SUID bit set and if there’s any errors e.g. access denied it will output them to /dev/null so you don’t have a screen full of errors.
Without going into detail, some binaries are set to run as root because they need high privilege access. Sometimes there are vulnerabilities in the binaries or custom bins/applications that mean you can use abuse these. On this system here’s all the files with SUID bits set.
This can also be set on directories which will affect files created:
https://web.mit.edu/rhel-doc/3/rhel-rg-en-3/s1-users-groups-private-groups.html
There is a whole subject for this but hopefully this is a quick taster on a gotcha and a potential privesc route.
Going back to our example for permissions:
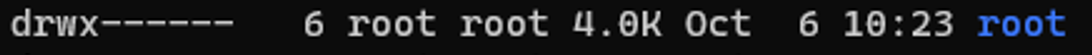
In this example the /root directory is:
A directory shown by: d
The object owner (root) has read, write, and execute
the group (root) has no access.
Other users have no other permissions are set.
In our demo we are going to switch to mRr3b00t:
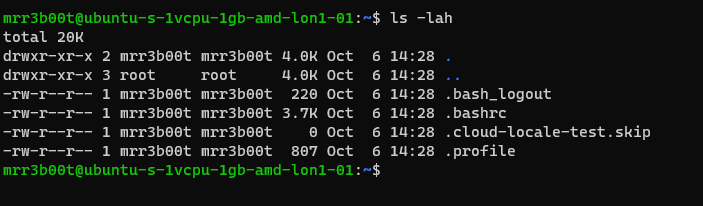
We touch a file “readme”
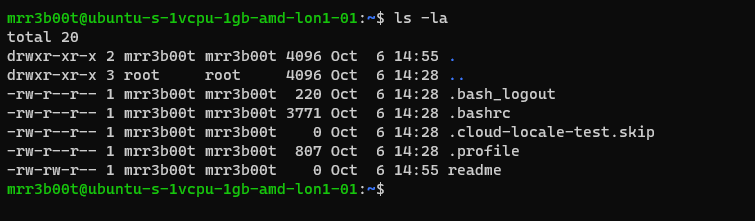
Now we switch back to root and create a new user called “QWERTY”
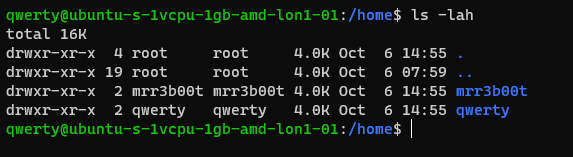
Now as querty we have read access to mRr3b00t’s files.
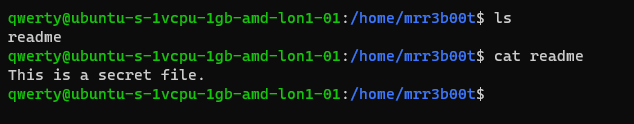
Why is that?
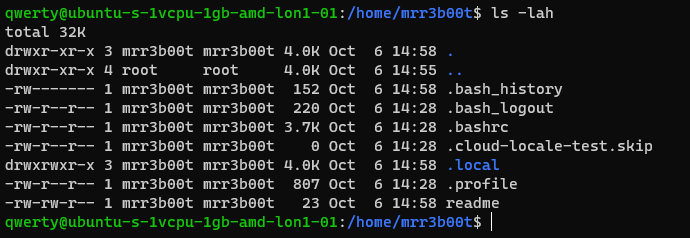
It’s because OTHER users have the read attribute set.
This won’t apply to all distributions but in Ubuntu this is out of the box defaults.
Let’s fix this (I’m going to set RWX and RW then RWX and RWX so you can see the change)
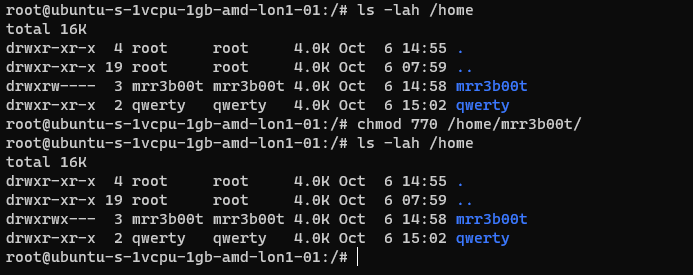
Here we set:
Owner 7 (rwx)
Group 7 (rw)
Others 0 (nothing)
Now we switch to qwerty and we can’t access mrreb00ts files:
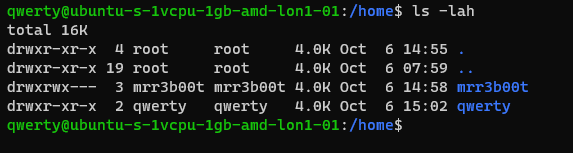
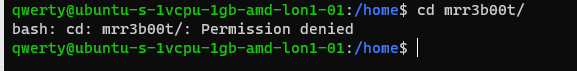
We set the following on mRr3b00ts home directory:
| chmod 770 /home/mrr3b00t/ |
Remember, Owner, Group, Others.
We can change the permissions for all users home directory as follows:
| sudo chmod 750 /home/* |
If our distro isn’t protecting by default, we can set this in the /etc/adduser.conf but you can look that one up!
Scratching the Surface
Ok so we’ve started to scratch the surface and show some of the areas to consider on Linux systems. I started just writing this as I sometimes do, I’m not even sure why but then I figured people might like to read this. So here is the first bash (haha) at trying to write something. I’m going to just post this on the blog and see if people find it useful. I think there’s a better way to carve stuff like this up into exercises. Key things:
- Google is your friend!
- Man pages are your friends!
- VMs in safe environment are your friends!
- –help is your friend!
Let me know if this is useful. Haha It’s useful for me just writing this stuff down, I do as we know, have a memory like a goldfish! If you think there’s something major I’ve missed or anything that I’ve messed up please shout, I woke up at 0300 and I’m like a zombie!
I also might try making a few “how to’s” for common activities because the subject area is huge and what’s probably more useful for people is. “i want to see how to review the apache access logs and how to configure rotation and log shipping etc.”
Introduction
I come from a heavy Windows background, in fact I started my computer experience on an Amstrad however not long after I was using DOS and then Windows 3.11 for Workgroups. So, I’m a heavy Windows head, I’ve deployed all kinds of services and applications within business environments using common technologies such as:
- CISCO/DELL/HP Networking switches and routers
- ISA/TMG/UAG/Checkpoint firewalls
- Palo Alto Firewalls
- Microsoft Windows Client (Windows 3.11-Windows 11)
- Microsoft Windows Server (NT4 – Windows Server 2022)
- Vmware vSphere/ESXi
- Random Linux Security appliances and VPN devices
One thing that I’ve noticed in my travels so far is that Linux deployments in enterprise environments in the back office/corp nets are often appliance based or “black boxes”. This creates a bit of a fun scenario whereby some system administrators and operations teams aren’t particularly comfortable with using UNIX/Linus systems. So, I thought I’d try and write some content to show how to do common tasks using the command line interface (CLI). This isn’t designed as an indepth guide, this is really just to try and give people a view of some of the things that you will need to be aware of. This isn’t mean’t to be “academic” or replace manuals and technical docs so it’s brief and to the point (as far as that is possible).
Major Changes for Windows People
In Windows many things are case insensitive, such as usernames. In UNIX/Linux the file system is case sensitive. Running Uname will error vs uname which will show the OS version. This means some scenarios are case sensitive (file system access is for sure) but also usernames in some systems are as well.
Distributions
Linux comes in a ton of flavours there is even a Hannah Montanna flavour. Common distibutions are:
Red Had Enterprise Linux (RHEL)
- CentOS
- Debian
- Fedora
- Ubuntu
- MINT
- ARCH
Patching and Backporting
Patching and Upgrading in Linux is a bit bit different than Windows because there’s this thing called Backporting:
You need to watch out for this as version based enumeration can lead to false positives when conducting asset enumeration and vulnerability identification through version identification. Backporting is where a security fix or patch is backported into an older version of software. So the banner may say version 7.8 however the security fixes may have been incorporated and deployed (the ones that are in 7.9) so there’s some work to do to check and validate (and also demonstrate) things are patched.
Boot Types
- BIOS (BASIC INPUT OUTPUT SYSTEM)
- UEFI
https://wiki.ubuntu.com/UEFI/SecureBoot
Boot Loaders
The most common boot loader is GRUB.
There are others such as:
- BURG
- LILO
- SYSLINUX
https://en.wikipedia.org/wiki/Comparison_of_boot_loaders
File Systems
The common files systems are:
- EXT2
- EXT3
- EXT4
Other file systems include:
- XFS
- ZFS
There are other systems that can also be used.
A common disk encryption system is LUKS:
https://www.redhat.com/sysadmin/disk-encryption-luks
Volume manaement can be handled by Logical Volume Manager (LVM). LVM allows for dynamic volume management (thin of this a bit like using DYNAMIC disks in Windows).
File System Structure
Unlike Windows GNU/Linux systems use files for everything. There’s no concept of the registry like there is in Windows. In Linux configurations, metadata and data are stored in files. Some systems/application may use databases for configurations e.g., mySQL, postgres etc.
Here’s an example from an Ubuntu system:

The following table is a summary of some common areas:
| Path | Purpose | Notes |
| / | Root | |
| /bin | Binaries for commands (Essential bins) | |
| /dev | Device files/devices | |
| /etc | System wide configuration | |
| /etc/opt | Optional Configurations | |
| /home | Home folders | |
| /lib | Libraries for binaries | |
| /media | Removable Media | |
| /mnt | Temporary File System Mount Points | |
| /opt | Software Packages | |
| /proc | A virtual file system for process and kernel usage | |
| /root | Root users home folder | |
| /run | Run-time variable data for users and daemons | |
| /sbin | System Binaries | |
| /srv | ||
| /sys | ||
| /tmp | Temporary files | |
| /usr | Read only user data | |
| /usr/bin | Non-essential binaries | |
| /usr/include | ||
| /usr/lib32 | User Libraries e.g. 32 bit | |
| /usr/local | Host specific data | |
| /usr/sbin | Non essential system binaries | |
| /usr/share | Shared data | |
| /usr/src | Source code and headers | |
| /var | Variable files e.g. log files | |
| /var/cache | Cache | |
| /var/lib/ | ||
| /var/lock | Lock files | |
| /var/log | Log files e.g. Apache, system etc. | |
| /var/mail | Mailbox data | |
| /var/opt | Optional variable data | |
| /var/run | Variable run time data | |
| /var/spool | Spools for mail and printers | |
| /var/tmp | Temporary files that remain between reboots |
Common Shells and Terminal Emulators
- Bash
- Oh My ZSH (ZSH)
- TMUX
- Konsole
- Terminator
Now when using ssh etc. the sessions are not resumable or sharable. So, you will see some cool tools here in the shape of:
- TMUX
- DVTM
- ABDUCO
- SCREEN
Package Managers
In Windows you have the Windows Installer Database and Windows Updates. In modern version of Windows you also have Windows Store and Chocolatey etc.
However, in Linux there is the concept of package managers. Common package managers include:
- DPKG
- RPM
Alongside package managers are dependancy resolvers (thanks Alex for this and other bits!)
- PACMAN
- YUM/DNF
- APT
Common Networking Protocols
- SSH
- SAMBA (Unix SMB/CIFS)
- FTP
- SFTP
- OpenLDAP
- VNC
- RDP
Desktop Window Systems (GUI)
Common guis (Windows Managers) include:
- GNOME
- KDE
There are quite a few of these get your google on!
Key Security Features
- Services
- CHROOT Jails
- Creates a false root directory for sandboxing
- Pluggable Authenticaiton Modules (PAM)
- Superuser Do/Substitute User Do (SUDO) – Like Windows Runas
- Access Control Lists
- IPTABLES
- UFW (Firewall)
- Audit D
- Malware Detection
- CLAM AV
- Remote Administration
- TELNET
- SSH
- VNC
- Remote Desktop Protocol
- SELinux
Common Administration Tasks
I’m using Ubuntu here, some distributions may use slightly different commands e.g. Arch uses PACMAN, Red Hat uses Yum.
| Task | command | Notes |
| Clear the screen | clear | Shortcut CTRL+L |
| List files | ls | |
| Switch User | su | |
| Run as root/other user | sudo | “super user do” was the traditional name now it’s “substitute user do” |
| Change directory | cd | |
| Make a directory | mk | |
| Move a file/directory | mv | |
| Remove a file | rm | |
| Remove a directory | rmdir | |
| Copy a file/folder | cp | |
| List OS Version | uname | |
| Read Help | help | |
| Read a manual | man | |
| Update Repositories | apt update | |
| Upgrade packages | apt upgrade | |
| Create an empty file | touch | |
| List directories and files | tree | |
| List disk space/usage | du | List estimated file usage |
| List | df | List file system usage |
| Change permissions | chmod | |
| Add a user | useradd | This is a very basic utility for creating users that only creates the user object |
| Add a user | adduser | This has more features and will create things such as the home drive |
| Delete a user | deluser | |
| Create a group | addgroup | |
| Delete a group | delgroup | |
| Modify a user | usermod | |
| Modify a group | groupmod | |
| List processes | ps | Common is: ps aux |
| Show the time | date | |
| Kill a process | kill | |
| List suspended processes | jobs | |
| Foreground a process | fg | |
| Edit text | vi or nano | |
| Show the current user | whoami | |
| Show the current date and time | date | date -d now |
| Display the top of a file | head | |
| Display the end of a file | tail | |
| Display a file in real time | tail -f | tail -f access.log |
| Print the working directory | pwd | |
| Set a variable | set | |
| List logged on users | w | |
| List logged on users with IP details | who | |
| Send a message to all logged on users | wall | |
| Output data to session | echo | |
| Send message to a user | write | |
| Reboot the system | reboot | |
| Power off the system | poweroff | |
| List the contents of a file | cat | |
| Ssh to another system | ssh@192.168.0.1 | You can use -I to specify private keys |
| See running processes and performance information | top |
Scheduled Tasks
Tasks in UNIX/LINUX are managed using CRON.

Parsing and Manipulating Text and Files
- cat
- sed
- awk
- grep
- find
- locate
- sort
- uniq
Daemons
A daemon is a background process, these are commonly used for services. E.g.
- SSHD is the Secure Shell Daemon.
- FTPD is the File Transfer Protocol Daemon.
System Service Control
systemctl list-units –type service
systemctl disable [service] –now
systemctl enable [service] –now
Common Networking Commands
- netstat
- ss
- tcpdump
- ufw
- iptables
- ip a (ifconfig on older systems)
- route
- nslookup
- traceroute
Common Linux Virtualisation Solutions/Platforms
- KVM
- Virtual Box
- ProxMox
- Vmware Workstation
- QEMU
Creating a new User

Using adduser we create a new user account. This utility also creates a new group and a home directory.

If we cat /etc/passwd we can see the new user:

If we cat /etc/group

We can see the new group.
If we wanted to add mrr3b00t to root we would run:

To remove the user from the group “root” we would run:

Using “su” we can switch to mRr3b00t:

File Permissions

Now the ACLs on Windows are slightly different. Let’s step through some permissions:
Permission Groups
- Owner
- Group
- All Users/Others
Permission Types
- Read (4)
- Write (2)
- Execute (1)
When we see permissions in Linux we see them in the following format:
[permission flag]rwxrwxrwx 1 owner group
Permission flags can be:
_ = nothing
d = directory
l = symbolic link
SETUID/SETGID and Sticky Bit
s = setuid or setgid (this is shown over [r] rather than in the first character)
t = sticky bit
Permissions are shown as:
Read [r] Write [w] execute[e]
These are important when we consider privilidge escalation. If these bits are set they will look like:
RWSRWSRWT
Or a variation of that pattern with S S and T
You can search for SUID bits using the following command:
| find / -perm -u=s -type f 2>/dev/null |
This will find any file (-type f) permissions with the SUID bit set and if there’s any errors e.g. access denied it will output them to /dev/null so you don’t have a screen full of errors.
Without going into detail, some binaries are set to run as root because they need high privilege access. Sometimes there are vulnerabilities in the binaries or custom bins/applications that mean you can use abuse these. On this system here’s all the files with SUID bits set.

This can also be set on directories which will affect files created:
https://web.mit.edu/rhel-doc/3/rhel-rg-en-3/s1-users-groups-private-groups.html
There is a whole subject for this but hopefully this is a quick taster on a gotcha and a potential privesc route.
Going back to our example for permissions:

In this example the /root directory is:
A directory shown by: d
The object owner (root) has read, write, and execute
the group (root) has no access.
Other users have no other permissions are set.
In our demo we are going to switch to mRr3b00t:

We touch a file “readme”

Now we switch back to root and create a new user called “QWERTY”


Now as querty we have read access to mRr3b00t’s files.

Why is that?

It’s because OTHER users have the read attribute set.
This won’t apply to all distributions but in Ubuntu this is out of the box defaults.
Let’s fix this (I’m going to set RWX and RW then RWX and RWX so you can see the change)

Here we set:
Owner 7 (rwx)
Group 7 (rw)
Others 0 (nothing)
Now we switch to qwerty and we can’t access mrreb00ts files:


We set the following on mRr3b00ts home directory:
| chmod 770 /home/mrr3b00t/ |
Remember, Owner, Group, Others.
We can change the permissions for all users home directory as follows:
| sudo chmod 750 /home/* |
If our distro isn’t protecting by default, we can set this in the /etc/adduser.conf but you can look that one up!
Scratching the Surface
Ok so we’ve started to scratch the surface and show some of the areas to consider on Linux systems. I started just writing this as I sometimes do, I’m not even sure why but then I figured people might like to read this. So here is the first bash (haha) at trying to write something. I’m going to just post this on the blog and see if people find it useful. I think there’s a better way to carve stuff like this up into exercises. Key things:
- Google is your friend!
- Man pages are your friends!
- VMs in safe environment are your friends!
- –help is your friend!
Let me know if this is useful. Haha It’s useful for me just writing this stuff down, I do as we know, have a memory like a goldfish! If you think there’s something major I’ve missed or anything that I’ve messed up please shout, I woke up at 0300 and I’m like a zombie!
I also might try making a few “how to’s” for common activities because the subject area is huge and what’s probably more useful for people is. “i want to see how to review the apache access logs and how to configure rotation and log shipping etc.”
Introduction
I come from a heavy Windows background, in fact I started my computer experience on an Amstrad however not long after I was using DOS and then Windows 3.11 for Workgroups. So, I’m a heavy Windows head, I’ve deployed all kinds of services and applications within business environments using common technologies such as:
- CISCO/DELL/HP Networking switches and routers
- ISA/TMG/UAG/Checkpoint firewalls
- Palo Alto Firewalls
- Microsoft Windows Client (Windows 3.11-Windows 11)
- Microsoft Windows Server (NT4 – Windows Server 2022)
- Vmware vSphere/ESXi
- Random Linux Security appliances and VPN devices
One thing that I’ve noticed in my travels so far is that Linux deployments in enterprise environments in the back office/corp nets are often appliance based or “black boxes”. This creates a bit of a fun scenario whereby some system administrators and operations teams aren’t particularly comfortable with using UNIX/Linus systems. So, I thought I’d try and write some content to show how to do common tasks using the command line interface (CLI). This isn’t designed as an indepth guide, this is really just to try and give people a view of some of the things that you will need to be aware of. This isn’t mean’t to be “academic” or replace manuals and technical docs so it’s brief and to the point (as far as that is possible).
Major Changes for Windows People
In Windows many things are case insensitive, such as usernames. In UNIX/Linux the file system is case sensitive. Running Uname will error vs uname which will show the OS version. This means some scenarios are case sensitive (file system access is for sure) but also usernames in some systems are as well.
Distributions
Linux comes in a ton of flavours there is even a Hannah Montanna flavour. Common distibutions are:
Red Had Enterprise Linux (RHEL)
- CentOS
- Debian
- Fedora
- Ubuntu
- MINT
- ARCH
Patching and Backporting
Patching and Upgrading in Linux is a bit bit different than Windows because there’s this thing called Backporting:
You need to watch out for this as version based enumeration can lead to false positives when conducting asset enumeration and vulnerability identification through version identification. Backporting is where a security fix or patch is backported into an older version of software. So the banner may say version 7.8 however the security fixes may have been incorporated and deployed (the ones that are in 7.9) so there’s some work to do to check and validate (and also demonstrate) things are patched.
Boot Types
- BIOS (BASIC INPUT OUTPUT SYSTEM)
- UEFI
https://wiki.ubuntu.com/UEFI/SecureBoot
Boot Loaders
The most common boot loader is GRUB.
There are others such as:
- BURG
- LILO
- SYSLINUX
https://en.wikipedia.org/wiki/Comparison_of_boot_loaders
File Systems
The common files systems are:
- EXT2
- EXT3
- EXT4
Other file systems include:
- XFS
- ZFS
There are other systems that can also be used.
A common disk encryption system is LUKS:
https://www.redhat.com/sysadmin/disk-encryption-luks
Volume manaement can be handled by Logical Volume Manager (LVM). LVM allows for dynamic volume management (thin of this a bit like using DYNAMIC disks in Windows).
File System Structure
Unlike Windows GNU/Linux systems use files for everything. There’s no concept of the registry like there is in Windows. In Linux configurations, metadata and data are stored in files. Some systems/application may use databases for configurations e.g., mySQL, postgres etc.
Here’s an example from an Ubuntu system:

The following table is a summary of some common areas:
| Path | Purpose | Notes |
| / | Root | |
| /bin | Binaries for commands (Essential bins) | |
| /dev | Device files/devices | |
| /etc | System wide configuration | |
| /etc/opt | Optional Configurations | |
| /home | Home folders | |
| /lib | Libraries for binaries | |
| /media | Removable Media | |
| /mnt | Temporary File System Mount Points | |
| /opt | Software Packages | |
| /proc | A virtual file system for process and kernel usage | |
| /root | Root users home folder | |
| /run | Run-time variable data for users and daemons | |
| /sbin | System Binaries | |
| /srv | ||
| /sys | ||
| /tmp | Temporary files | |
| /usr | Read only user data | |
| /usr/bin | Non-essential binaries | |
| /usr/include | ||
| /usr/lib32 | User Libraries e.g. 32 bit | |
| /usr/local | Host specific data | |
| /usr/sbin | Non essential system binaries | |
| /usr/share | Shared data | |
| /usr/src | Source code and headers | |
| /var | Variable files e.g. log files | |
| /var/cache | Cache | |
| /var/lib/ | ||
| /var/lock | Lock files | |
| /var/log | Log files e.g. Apache, system etc. | |
| /var/mail | Mailbox data | |
| /var/opt | Optional variable data | |
| /var/run | Variable run time data | |
| /var/spool | Spools for mail and printers | |
| /var/tmp | Temporary files that remain between reboots |
Common Shells and Terminal Emulators
- Bash
- Oh My ZSH (ZSH)
- TMUX
- Konsole
- Terminator
Now when using ssh etc. the sessions are not resumable or sharable. So, you will see some cool tools here in the shape of:
- TMUX
- DVTM
- ABDUCO
- SCREEN
Package Managers
In Windows you have the Windows Installer Database and Windows Updates. In modern version of Windows you also have Windows Store and Chocolatey etc.
However, in Linux there is the concept of package managers. Common package managers include:
- DPKG
- RPM
Alongside package managers are dependancy resolvers (thanks Alex for this and other bits!)
- PACMAN
- YUM/DNF
- APT
Common Networking Protocols
- SSH
- SAMBA (Unix SMB/CIFS)
- FTP
- SFTP
- OpenLDAP
- VNC
- RDP
Desktop Window Systems (GUI)
Common guis (Windows Managers) include:
- GNOME
- KDE
There are quite a few of these get your google on!
Key Security Features
- Services
- CHROOT Jails
- Creates a false root directory for sandboxing
- Pluggable Authenticaiton Modules (PAM)
- Superuser Do/Substitute User Do (SUDO) – Like Windows Runas
- Access Control Lists
- IPTABLES
- UFW (Firewall)
- Audit D
- Malware Detection
- CLAM AV
- Remote Administration
- TELNET
- SSH
- VNC
- Remote Desktop Protocol
- SELinux
Common Administration Tasks
I’m using Ubuntu here, some distributions may use slightly different commands e.g. Arch uses PACMAN, Red Hat uses Yum.
| Task | command | Notes |
| Clear the screen | clear | Shortcut CTRL+L |
| List files | ls | |
| Switch User | su | |
| Run as root/other user | sudo | “super user do” was the traditional name now it’s “substitute user do” |
| Change directory | cd | |
| Make a directory | mk | |
| Move a file/directory | mv | |
| Remove a file | rm | |
| Remove a directory | rmdir | |
| Copy a file/folder | cp | |
| List OS Version | uname | |
| Read Help | help | |
| Read a manual | man | |
| Update Repositories | apt update | |
| Upgrade packages | apt upgrade | |
| Create an empty file | touch | |
| List directories and files | tree | |
| List disk space/usage | du | List estimated file usage |
| List | df | List file system usage |
| Change permissions | chmod | |
| Add a user | useradd | This is a very basic utility for creating users that only creates the user object |
| Add a user | adduser | This has more features and will create things such as the home drive |
| Delete a user | deluser | |
| Create a group | addgroup | |
| Delete a group | delgroup | |
| Modify a user | usermod | |
| Modify a group | groupmod | |
| List processes | ps | Common is: ps aux |
| Show the time | date | |
| Kill a process | kill | |
| List suspended processes | jobs | |
| Foreground a process | fg | |
| Edit text | vi or nano | |
| Show the current user | whoami | |
| Show the current date and time | date | date -d now |
| Display the top of a file | head | |
| Display the end of a file | tail | |
| Display a file in real time | tail -f | tail -f access.log |
| Print the working directory | pwd | |
| Set a variable | set | |
| List logged on users | w | |
| List logged on users with IP details | who | |
| Send a message to all logged on users | wall | |
| Output data to session | echo | |
| Send message to a user | write | |
| Reboot the system | reboot | |
| Power off the system | poweroff | |
| List the contents of a file | cat | |
| Ssh to another system | ssh@192.168.0.1 | You can use -I to specify private keys |
| See running processes and performance information | top |
Scheduled Tasks
Tasks in UNIX/LINUX are managed using CRON.

Parsing and Manipulating Text and Files
- cat
- sed
- awk
- grep
- find
- locate
- sort
- uniq
Daemons
A daemon is a background process, these are commonly used for services. E.g.
- SSHD is the Secure Shell Daemon.
- FTPD is the File Transfer Protocol Daemon.
System Service Control
systemctl list-units –type service
systemctl disable [service] –now
systemctl enable [service] –now
Common Networking Commands
- netstat
- ss
- tcpdump
- ufw
- iptables
- ip a (ifconfig on older systems)
- route
- nslookup
- traceroute
Common Linux Virtualisation Solutions/Platforms
- KVM
- Virtual Box
- ProxMox
- Vmware Workstation
- QEMU
Creating a new User

Using adduser we create a new user account. This utility also creates a new group and a home directory.

If we cat /etc/passwd we can see the new user:

If we cat /etc/group

We can see the new group.
If we wanted to add mrr3b00t to root we would run:

To remove the user from the group “root” we would run:

Using “su” we can switch to mRr3b00t:

File Permissions

Now the ACLs on Windows are slightly different. Let’s step through some permissions:
Permission Groups
- Owner
- Group
- All Users/Others
Permission Types
- Read (4)
- Write (2)
- Execute (1)
When we see permissions in Linux we see them in the following format:
[permission flag]rwxrwxrwx 1 owner group
Permission flags can be:
_ = nothing
d = directory
l = symbolic link
SETUID/SETGID and Sticky Bit
s = setuid or setgid (this is shown over [r] rather than in the first character)
t = sticky bit
Permissions are shown as:
Read [r] Write [w] execute[e]
These are important when we consider privilidge escalation. If these bits are set they will look like:
RWSRWSRWT
Or a variation of that pattern with S S and T
You can search for SUID bits using the following command:
| find / -perm -u=s -type f 2>/dev/null |
This will find any file (-type f) permissions with the SUID bit set and if there’s any errors e.g. access denied it will output them to /dev/null so you don’t have a screen full of errors.
Without going into detail, some binaries are set to run as root because they need high privilege access. Sometimes there are vulnerabilities in the binaries or custom bins/applications that mean you can use abuse these. On this system here’s all the files with SUID bits set.

This can also be set on directories which will affect files created:
https://web.mit.edu/rhel-doc/3/rhel-rg-en-3/s1-users-groups-private-groups.html
There is a whole subject for this but hopefully this is a quick taster on a gotcha and a potential privesc route.
Going back to our example for permissions:

In this example the /root directory is:
A directory shown by: d
The object owner (root) has read, write, and execute
the group (root) has no access.
Other users have no other permissions are set.
In our demo we are going to switch to mRr3b00t:

We touch a file “readme”

Now we switch back to root and create a new user called “QWERTY”


Now as querty we have read access to mRr3b00t’s files.

Why is that?

It’s because OTHER users have the read attribute set.
This won’t apply to all distributions but in Ubuntu this is out of the box defaults.
Let’s fix this (I’m going to set RWX and RW then RWX and RWX so you can see the change)

Here we set:
Owner 7 (rwx)
Group 7 (rw)
Others 0 (nothing)
Now we switch to qwerty and we can’t access mrreb00ts files:


We set the following on mRr3b00ts home directory:
| chmod 770 /home/mrr3b00t/ |
Remember, Owner, Group, Others.
We can change the permissions for all users home directory as follows:
| sudo chmod 750 /home/* |
If our distro isn’t protecting by default, we can set this in the /etc/adduser.conf but you can look that one up!
Scratching the Surface
Ok so we’ve started to scratch the surface and show some of the areas to consider on Linux systems. I started just writing this as I sometimes do, I’m not even sure why but then I figured people might like to read this. So here is the first bash (haha) at trying to write something. I’m going to just post this on the blog and see if people find it useful. I think there’s a better way to carve stuff like this up into exercises. Key things:
- Google is your friend!
- Man pages are your friends!
- VMs in safe environment are your friends!
- –help is your friend!
Let me know if this is useful. Haha It’s useful for me just writing this stuff down, I do as we know, have a memory like a goldfish! If you think there’s something major I’ve missed or anything that I’ve messed up please shout, I woke up at 0300 and I’m like a zombie!
I also might try making a few “how to’s” for common activities because the subject area is huge and what’s probably more useful for people is. “i want to see how to review the apache access logs and how to configure rotation and log shipping etc.”
Introduction
I come from a heavy Windows background, in fact I started my computer experience on an Amstrad however not long after I was using DOS and then Windows 3.11 for Workgroups. So, I’m a heavy Windows head, I’ve deployed all kinds of services and applications within business environments using common technologies such as:
- CISCO/DELL/HP Networking switches and routers
- ISA/TMG/UAG/Checkpoint firewalls
- Palo Alto Firewalls
- Microsoft Windows Client (Windows 3.11-Windows 11)
- Microsoft Windows Server (NT4 – Windows Server 2022)
- Vmware vSphere/ESXi
- Random Linux Security appliances and VPN devices
One thing that I’ve noticed in my travels so far is that Linux deployments in enterprise environments in the back office/corp nets are often appliance based or “black boxes”. This creates a bit of a fun scenario whereby some system administrators and operations teams aren’t particularly comfortable with using UNIX/Linus systems. So, I thought I’d try and write some content to show how to do common tasks using the command line interface (CLI). This isn’t designed as an indepth guide, this is really just to try and give people a view of some of the things that you will need to be aware of. This isn’t mean’t to be “academic” or replace manuals and technical docs so it’s brief and to the point (as far as that is possible).
Major Changes for Windows People
In Windows many things are case insensitive, such as usernames. In UNIX/Linux the file system is case sensitive. Running Uname will error vs uname which will show the OS version. This means some scenarios are case sensitive (file system access is for sure) but also usernames in some systems are as well.
Distributions
Linux comes in a ton of flavours there is even a Hannah Montanna flavour. Common distibutions are:
Red Had Enterprise Linux (RHEL)
- CentOS
- Debian
- Fedora
- Ubuntu
- MINT
- ARCH
Patching and Backporting
Patching and Upgrading in Linux is a bit bit different than Windows because there’s this thing called Backporting:
You need to watch out for this as version based enumeration can lead to false positives when conducting asset enumeration and vulnerability identification through version identification. Backporting is where a security fix or patch is backported into an older version of software. So the banner may say version 7.8 however the security fixes may have been incorporated and deployed (the ones that are in 7.9) so there’s some work to do to check and validate (and also demonstrate) things are patched.
Boot Types
- BIOS (BASIC INPUT OUTPUT SYSTEM)
- UEFI
https://wiki.ubuntu.com/UEFI/SecureBoot
Boot Loaders
The most common boot loader is GRUB.
There are others such as:
- BURG
- LILO
- SYSLINUX
https://en.wikipedia.org/wiki/Comparison_of_boot_loaders
File Systems
The common files systems are:
- EXT2
- EXT3
- EXT4
Other file systems include:
- XFS
- ZFS
There are other systems that can also be used.
A common disk encryption system is LUKS:
https://www.redhat.com/sysadmin/disk-encryption-luks
Volume manaement can be handled by Logical Volume Manager (LVM). LVM allows for dynamic volume management (thin of this a bit like using DYNAMIC disks in Windows).
File System Structure
Unlike Windows GNU/Linux systems use files for everything. There’s no concept of the registry like there is in Windows. In Linux configurations, metadata and data are stored in files. Some systems/application may use databases for configurations e.g., mySQL, postgres etc.
Here’s an example from an Ubuntu system:

The following table is a summary of some common areas:
| Path | Purpose | Notes |
| / | Root | |
| /bin | Binaries for commands (Essential bins) | |
| /dev | Device files/devices | |
| /etc | System wide configuration | |
| /etc/opt | Optional Configurations | |
| /home | Home folders | |
| /lib | Libraries for binaries | |
| /media | Removable Media | |
| /mnt | Temporary File System Mount Points | |
| /opt | Software Packages | |
| /proc | A virtual file system for process and kernel usage | |
| /root | Root users home folder | |
| /run | Run-time variable data for users and daemons | |
| /sbin | System Binaries | |
| /srv | ||
| /sys | ||
| /tmp | Temporary files | |
| /usr | Read only user data | |
| /usr/bin | Non-essential binaries | |
| /usr/include | ||
| /usr/lib32 | User Libraries e.g. 32 bit | |
| /usr/local | Host specific data | |
| /usr/sbin | Non essential system binaries | |
| /usr/share | Shared data | |
| /usr/src | Source code and headers | |
| /var | Variable files e.g. log files | |
| /var/cache | Cache | |
| /var/lib/ | ||
| /var/lock | Lock files | |
| /var/log | Log files e.g. Apache, system etc. | |
| /var/mail | Mailbox data | |
| /var/opt | Optional variable data | |
| /var/run | Variable run time data | |
| /var/spool | Spools for mail and printers | |
| /var/tmp | Temporary files that remain between reboots |
Common Shells and Terminal Emulators
- Bash
- Oh My ZSH (ZSH)
- TMUX
- Konsole
- Terminator
Now when using ssh etc. the sessions are not resumable or sharable. So, you will see some cool tools here in the shape of:
- TMUX
- DVTM
- ABDUCO
- SCREEN
Package Managers
In Windows you have the Windows Installer Database and Windows Updates. In modern version of Windows you also have Windows Store and Chocolatey etc.
However, in Linux there is the concept of package managers. Common package managers include:
- DPKG
- RPM
Alongside package managers are dependancy resolvers (thanks Alex for this and other bits!)
- PACMAN
- YUM/DNF
- APT
Common Networking Protocols
- SSH
- SAMBA (Unix SMB/CIFS)
- FTP
- SFTP
- OpenLDAP
- VNC
- RDP
Desktop Window Systems (GUI)
Common guis (Windows Managers) include:
- GNOME
- KDE
There are quite a few of these get your google on!
Key Security Features
- Services
- CHROOT Jails
- Creates a false root directory for sandboxing
- Pluggable Authenticaiton Modules (PAM)
- Superuser Do/Substitute User Do (SUDO) – Like Windows Runas
- Access Control Lists
- IPTABLES
- UFW (Firewall)
- Audit D
- Malware Detection
- CLAM AV
- Remote Administration
- TELNET
- SSH
- VNC
- Remote Desktop Protocol
- SELinux
Common Administration Tasks
I’m using Ubuntu here, some distributions may use slightly different commands e.g. Arch uses PACMAN, Red Hat uses Yum.
| Task | command | Notes |
| Clear the screen | clear | Shortcut CTRL+L |
| List files | ls | |
| Switch User | su | |
| Run as root/other user | sudo | “super user do” was the traditional name now it’s “substitute user do” |
| Change directory | cd | |
| Make a directory | mk | |
| Move a file/directory | mv | |
| Remove a file | rm | |
| Remove a directory | rmdir | |
| Copy a file/folder | cp | |
| List OS Version | uname | |
| Read Help | help | |
| Read a manual | man | |
| Update Repositories | apt update | |
| Upgrade packages | apt upgrade | |
| Create an empty file | touch | |
| List directories and files | tree | |
| List disk space/usage | du | List estimated file usage |
| List | df | List file system usage |
| Change permissions | chmod | |
| Add a user | useradd | This is a very basic utility for creating users that only creates the user object |
| Add a user | adduser | This has more features and will create things such as the home drive |
| Delete a user | deluser | |
| Create a group | addgroup | |
| Delete a group | delgroup | |
| Modify a user | usermod | |
| Modify a group | groupmod | |
| List processes | ps | Common is: ps aux |
| Show the time | date | |
| Kill a process | kill | |
| List suspended processes | jobs | |
| Foreground a process | fg | |
| Edit text | vi or nano | |
| Show the current user | whoami | |
| Show the current date and time | date | date -d now |
| Display the top of a file | head | |
| Display the end of a file | tail | |
| Display a file in real time | tail -f | tail -f access.log |
| Print the working directory | pwd | |
| Set a variable | set | |
| List logged on users | w | |
| List logged on users with IP details | who | |
| Send a message to all logged on users | wall | |
| Output data to session | echo | |
| Send message to a user | write | |
| Reboot the system | reboot | |
| Power off the system | poweroff | |
| List the contents of a file | cat | |
| Ssh to another system | ssh@192.168.0.1 | You can use -I to specify private keys |
| See running processes and performance information | top |
Scheduled Tasks
Tasks in UNIX/LINUX are managed using CRON.

Parsing and Manipulating Text and Files
- cat
- sed
- awk
- grep
- find
- locate
- sort
- uniq
Daemons
A daemon is a background process, these are commonly used for services. E.g.
- SSHD is the Secure Shell Daemon.
- FTPD is the File Transfer Protocol Daemon.
System Service Control
systemctl list-units –type service
systemctl disable [service] –now
systemctl enable [service] –now
Common Networking Commands
- netstat
- ss
- tcpdump
- ufw
- iptables
- ip a (ifconfig on older systems)
- route
- nslookup
- traceroute
Common Linux Virtualisation Solutions/Platforms
- KVM
- Virtual Box
- ProxMox
- Vmware Workstation
- QEMU
Creating a new User

Using adduser we create a new user account. This utility also creates a new group and a home directory.

If we cat /etc/passwd we can see the new user:

If we cat /etc/group

We can see the new group.
If we wanted to add mrr3b00t to root we would run:

To remove the user from the group “root” we would run:

Using “su” we can switch to mRr3b00t:

File Permissions

Now the ACLs on Windows are slightly different. Let’s step through some permissions:
Permission Groups
- Owner
- Group
- All Users/Others
Permission Types
- Read (4)
- Write (2)
- Execute (1)
When we see permissions in Linux we see them in the following format:
[permission flag]rwxrwxrwx 1 owner group
Permission flags can be:
_ = nothing
d = directory
l = symbolic link
SETUID/SETGID and Sticky Bit
s = setuid or setgid (this is shown over [r] rather than in the first character)
t = sticky bit
Permissions are shown as:
Read [r] Write [w] execute[e]
These are important when we consider privilidge escalation. If these bits are set they will look like:
RWSRWSRWT
Or a variation of that pattern with S S and T
You can search for SUID bits using the following command:
| find / -perm -u=s -type f 2>/dev/null |
This will find any file (-type f) permissions with the SUID bit set and if there’s any errors e.g. access denied it will output them to /dev/null so you don’t have a screen full of errors.
Without going into detail, some binaries are set to run as root because they need high privilege access. Sometimes there are vulnerabilities in the binaries or custom bins/applications that mean you can use abuse these. On this system here’s all the files with SUID bits set.

This can also be set on directories which will affect files created:
https://web.mit.edu/rhel-doc/3/rhel-rg-en-3/s1-users-groups-private-groups.html
There is a whole subject for this but hopefully this is a quick taster on a gotcha and a potential privesc route.
Going back to our example for permissions:

In this example the /root directory is:
A directory shown by: d
The object owner (root) has read, write, and execute
the group (root) has no access.
Other users have no other permissions are set.
In our demo we are going to switch to mRr3b00t:

We touch a file “readme”

Now we switch back to root and create a new user called “QWERTY”


Now as querty we have read access to mRr3b00t’s files.

Why is that?

It’s because OTHER users have the read attribute set.
This won’t apply to all distributions but in Ubuntu this is out of the box defaults.
Let’s fix this (I’m going to set RWX and RW then RWX and RWX so you can see the change)

Here we set:
Owner 7 (rwx)
Group 7 (rw)
Others 0 (nothing)
Now we switch to qwerty and we can’t access mrreb00ts files:


We set the following on mRr3b00ts home directory:
| chmod 770 /home/mrr3b00t/ |
Remember, Owner, Group, Others.
We can change the permissions for all users home directory as follows:
| sudo chmod 750 /home/* |
If our distro isn’t protecting by default, we can set this in the /etc/adduser.conf but you can look that one up!
Scratching the Surface
Ok so we’ve started to scratch the surface and show some of the areas to consider on Linux systems. I started just writing this as I sometimes do, I’m not even sure why but then I figured people might like to read this. So here is the first bash (haha) at trying to write something. I’m going to just post this on the blog and see if people find it useful. I think there’s a better way to carve stuff like this up into exercises. Key things:
- Google is your friend!
- Man pages are your friends!
- VMs in safe environment are your friends!
- –help is your friend!
Let me know if this is useful. Haha It’s useful for me just writing this stuff down, I do as we know, have a memory like a goldfish! If you think there’s something major I’ve missed or anything that I’ve messed up please shout, I woke up at 0300 and I’m like a zombie!
I also might try making a few “how to’s” for common activities because the subject area is huge and what’s probably more useful for people is. “i want to see how to review the apache access logs and how to configure rotation and log shipping etc.”
Introduction
I come from a heavy Windows background, in fact I started my computer experience on an Amstrad however not long after I was using DOS and then Windows 3.11 for Workgroups. So, I’m a heavy Windows head, I’ve deployed all kinds of services and applications within business environments using common technologies such as:
- CISCO/DELL/HP Networking switches and routers
- ISA/TMG/UAG/Checkpoint firewalls
- Palo Alto Firewalls
- Microsoft Windows Client (Windows 3.11-Windows 11)
- Microsoft Windows Server (NT4 – Windows Server 2022)
- Vmware vSphere/ESXi
- Random Linux Security appliances and VPN devices
One thing that I’ve noticed in my travels so far is that Linux deployments in enterprise environments in the back office/corp nets are often appliance based or “black boxes”. This creates a bit of a fun scenario whereby some system administrators and operations teams aren’t particularly comfortable with using UNIX/Linus systems. So, I thought I’d try and write some content to show how to do common tasks using the command line interface (CLI). This isn’t designed as an indepth guide, this is really just to try and give people a view of some of the things that you will need to be aware of. This isn’t mean’t to be “academic” or replace manuals and technical docs so it’s brief and to the point (as far as that is possible).
Major Changes for Windows People
In Windows many things are case insensitive, such as usernames. In UNIX/Linux the file system is case sensitive. Running Uname will error vs uname which will show the OS version. This means some scenarios are case sensitive (file system access is for sure) but also usernames in some systems are as well.
Distributions
Linux comes in a ton of flavours there is even a Hannah Montanna flavour. Common distibutions are:
Red Had Enterprise Linux (RHEL)
- CentOS
- Debian
- Fedora
- Ubuntu
- MINT
- ARCH
Patching and Backporting
Patching and Upgrading in Linux is a bit bit different than Windows because there’s this thing called Backporting:
You need to watch out for this as version based enumeration can lead to false positives when conducting asset enumeration and vulnerability identification through version identification. Backporting is where a security fix or patch is backported into an older version of software. So the banner may say version 7.8 however the security fixes may have been incorporated and deployed (the ones that are in 7.9) so there’s some work to do to check and validate (and also demonstrate) things are patched.
Boot Types
- BIOS (BASIC INPUT OUTPUT SYSTEM)
- UEFI
https://wiki.ubuntu.com/UEFI/SecureBoot
Boot Loaders
The most common boot loader is GRUB.
There are others such as:
- BURG
- LILO
- SYSLINUX
https://en.wikipedia.org/wiki/Comparison_of_boot_loaders
File Systems
The common files systems are:
- EXT2
- EXT3
- EXT4
Other file systems include:
- XFS
- ZFS
There are other systems that can also be used.
A common disk encryption system is LUKS:
https://www.redhat.com/sysadmin/disk-encryption-luks
Volume manaement can be handled by Logical Volume Manager (LVM). LVM allows for dynamic volume management (thin of this a bit like using DYNAMIC disks in Windows).
File System Structure
Unlike Windows GNU/Linux systems use files for everything. There’s no concept of the registry like there is in Windows. In Linux configurations, metadata and data are stored in files. Some systems/application may use databases for configurations e.g., mySQL, postgres etc.
Here’s an example from an Ubuntu system:

The following table is a summary of some common areas:
| Path | Purpose | Notes |
| / | Root | |
| /bin | Binaries for commands (Essential bins) | |
| /dev | Device files/devices | |
| /etc | System wide configuration | |
| /etc/opt | Optional Configurations | |
| /home | Home folders | |
| /lib | Libraries for binaries | |
| /media | Removable Media | |
| /mnt | Temporary File System Mount Points | |
| /opt | Software Packages | |
| /proc | A virtual file system for process and kernel usage | |
| /root | Root users home folder | |
| /run | Run-time variable data for users and daemons | |
| /sbin | System Binaries | |
| /srv | ||
| /sys | ||
| /tmp | Temporary files | |
| /usr | Read only user data | |
| /usr/bin | Non-essential binaries | |
| /usr/include | ||
| /usr/lib32 | User Libraries e.g. 32 bit | |
| /usr/local | Host specific data | |
| /usr/sbin | Non essential system binaries | |
| /usr/share | Shared data | |
| /usr/src | Source code and headers | |
| /var | Variable files e.g. log files | |
| /var/cache | Cache | |
| /var/lib/ | ||
| /var/lock | Lock files | |
| /var/log | Log files e.g. Apache, system etc. | |
| /var/mail | Mailbox data | |
| /var/opt | Optional variable data | |
| /var/run | Variable run time data | |
| /var/spool | Spools for mail and printers | |
| /var/tmp | Temporary files that remain between reboots |
Common Shells and Terminal Emulators
- Bash
- Oh My ZSH (ZSH)
- TMUX
- Konsole
- Terminator
Now when using ssh etc. the sessions are not resumable or sharable. So, you will see some cool tools here in the shape of:
- TMUX
- DVTM
- ABDUCO
- SCREEN
Package Managers
In Windows you have the Windows Installer Database and Windows Updates. In modern version of Windows you also have Windows Store and Chocolatey etc.
However, in Linux there is the concept of package managers. Common package managers include:
- DPKG
- RPM
Alongside package managers are dependancy resolvers (thanks Alex for this and other bits!)
- PACMAN
- YUM/DNF
- APT
Common Networking Protocols
- SSH
- SAMBA (Unix SMB/CIFS)
- FTP
- SFTP
- OpenLDAP
- VNC
- RDP
Desktop Window Systems (GUI)
Common guis (Windows Managers) include:
- GNOME
- KDE
There are quite a few of these get your google on!
Key Security Features
- Services
- CHROOT Jails
- Creates a false root directory for sandboxing
- Pluggable Authenticaiton Modules (PAM)
- Superuser Do/Substitute User Do (SUDO) – Like Windows Runas
- Access Control Lists
- IPTABLES
- UFW (Firewall)
- Audit D
- Malware Detection
- CLAM AV
- Remote Administration
- TELNET
- SSH
- VNC
- Remote Desktop Protocol
- SELinux
Common Administration Tasks
I’m using Ubuntu here, some distributions may use slightly different commands e.g. Arch uses PACMAN, Red Hat uses Yum.
| Task | command | Notes |
| Clear the screen | clear | Shortcut CTRL+L |
| List files | ls | |
| Switch User | su | |
| Run as root/other user | sudo | “super user do” was the traditional name now it’s “substitute user do” |
| Change directory | cd | |
| Make a directory | mk | |
| Move a file/directory | mv | |
| Remove a file | rm | |
| Remove a directory | rmdir | |
| Copy a file/folder | cp | |
| List OS Version | uname | |
| Read Help | help | |
| Read a manual | man | |
| Update Repositories | apt update | |
| Upgrade packages | apt upgrade | |
| Create an empty file | touch | |
| List directories and files | tree | |
| List disk space/usage | du | List estimated file usage |
| List | df | List file system usage |
| Change permissions | chmod | |
| Add a user | useradd | This is a very basic utility for creating users that only creates the user object |
| Add a user | adduser | This has more features and will create things such as the home drive |
| Delete a user | deluser | |
| Create a group | addgroup | |
| Delete a group | delgroup | |
| Modify a user | usermod | |
| Modify a group | groupmod | |
| List processes | ps | Common is: ps aux |
| Show the time | date | |
| Kill a process | kill | |
| List suspended processes | jobs | |
| Foreground a process | fg | |
| Edit text | vi or nano | |
| Show the current user | whoami | |
| Show the current date and time | date | date -d now |
| Display the top of a file | head | |
| Display the end of a file | tail | |
| Display a file in real time | tail -f | tail -f access.log |
| Print the working directory | pwd | |
| Set a variable | set | |
| List logged on users | w | |
| List logged on users with IP details | who | |
| Send a message to all logged on users | wall | |
| Output data to session | echo | |
| Send message to a user | write | |
| Reboot the system | reboot | |
| Power off the system | poweroff | |
| List the contents of a file | cat | |
| Ssh to another system | ssh@192.168.0.1 | You can use -I to specify private keys |
| See running processes and performance information | top |
Scheduled Tasks
Tasks in UNIX/LINUX are managed using CRON.

Parsing and Manipulating Text and Files
- cat
- sed
- awk
- grep
- find
- locate
- sort
- uniq
Daemons
A daemon is a background process, these are commonly used for services. E.g.
- SSHD is the Secure Shell Daemon.
- FTPD is the File Transfer Protocol Daemon.
System Service Control
systemctl list-units –type service
systemctl disable [service] –now
systemctl enable [service] –now
Common Networking Commands
- netstat
- ss
- tcpdump
- ufw
- iptables
- ip a (ifconfig on older systems)
- route
- nslookup
- traceroute
Common Linux Virtualisation Solutions/Platforms
- KVM
- Virtual Box
- ProxMox
- Vmware Workstation
- QEMU
Creating a new User

Using adduser we create a new user account. This utility also creates a new group and a home directory.

If we cat /etc/passwd we can see the new user:

If we cat /etc/group

We can see the new group.
If we wanted to add mrr3b00t to root we would run:

To remove the user from the group “root” we would run:

Using “su” we can switch to mRr3b00t:

File Permissions

Now the ACLs on Windows are slightly different. Let’s step through some permissions:
Permission Groups
- Owner
- Group
- All Users/Others
Permission Types
- Read (4)
- Write (2)
- Execute (1)
When we see permissions in Linux we see them in the following format:
[permission flag]rwxrwxrwx 1 owner group
Permission flags can be:
_ = nothing
d = directory
l = symbolic link
SETUID/SETGID and Sticky Bit
s = setuid or setgid (this is shown over [r] rather than in the first character)
t = sticky bit
Permissions are shown as:
Read [r] Write [w] execute[e]
These are important when we consider privilidge escalation. If these bits are set they will look like:
RWSRWSRWT
Or a variation of that pattern with S S and T
You can search for SUID bits using the following command:
| find / -perm -u=s -type f 2>/dev/null |
This will find any file (-type f) permissions with the SUID bit set and if there’s any errors e.g. access denied it will output them to /dev/null so you don’t have a screen full of errors.
Without going into detail, some binaries are set to run as root because they need high privilege access. Sometimes there are vulnerabilities in the binaries or custom bins/applications that mean you can use abuse these. On this system here’s all the files with SUID bits set.

This can also be set on directories which will affect files created:
https://web.mit.edu/rhel-doc/3/rhel-rg-en-3/s1-users-groups-private-groups.html
There is a whole subject for this but hopefully this is a quick taster on a gotcha and a potential privesc route.
Going back to our example for permissions:

In this example the /root directory is:
A directory shown by: d
The object owner (root) has read, write, and execute
the group (root) has no access.
Other users have no other permissions are set.
In our demo we are going to switch to mRr3b00t:

We touch a file “readme”

Now we switch back to root and create a new user called “QWERTY”


Now as querty we have read access to mRr3b00t’s files.

Why is that?

It’s because OTHER users have the read attribute set.
This won’t apply to all distributions but in Ubuntu this is out of the box defaults.
Let’s fix this (I’m going to set RWX and RW then RWX and RWX so you can see the change)

Here we set:
Owner 7 (rwx)
Group 7 (rw)
Others 0 (nothing)
Now we switch to qwerty and we can’t access mrreb00ts files:


We set the following on mRr3b00ts home directory:
| chmod 770 /home/mrr3b00t/ |
Remember, Owner, Group, Others.
We can change the permissions for all users home directory as follows:
| sudo chmod 750 /home/* |
If our distro isn’t protecting by default, we can set this in the /etc/adduser.conf but you can look that one up!
Scratching the Surface
Ok so we’ve started to scratch the surface and show some of the areas to consider on Linux systems. I started just writing this as I sometimes do, I’m not even sure why but then I figured people might like to read this. So here is the first bash (haha) at trying to write something. I’m going to just post this on the blog and see if people find it useful. I think there’s a better way to carve stuff like this up into exercises. Key things:
- Google is your friend!
- Man pages are your friends!
- VMs in safe environment are your friends!
- –help is your friend!
Let me know if this is useful. Haha It’s useful for me just writing this stuff down, I do as we know, have a memory like a goldfish! If you think there’s something major I’ve missed or anything that I’ve messed up please shout, I woke up at 0300 and I’m like a zombie!
I also might try making a few “how to’s” for common activities because the subject area is huge and what’s probably more useful for people is. “i want to see how to review the apache access logs and how to configure rotation and log shipping etc.”
Introduction
I come from a heavy Windows background, in fact I started my computer experience on an Amstrad however not long after I was using DOS and then Windows 3.11 for Workgroups. So, I’m a heavy Windows head, I’ve deployed all kinds of services and applications within business environments using common technologies such as:
- CISCO/DELL/HP Networking switches and routers
- ISA/TMG/UAG/Checkpoint firewalls
- Palo Alto Firewalls
- Microsoft Windows Client (Windows 3.11-Windows 11)
- Microsoft Windows Server (NT4 – Windows Server 2022)
- Vmware vSphere/ESXi
- Random Linux Security appliances and VPN devices
One thing that I’ve noticed in my travels so far is that Linux deployments in enterprise environments in the back office/corp nets are often appliance based or “black boxes”. This creates a bit of a fun scenario whereby some system administrators and operations teams aren’t particularly comfortable with using UNIX/Linus systems. So, I thought I’d try and write some content to show how to do common tasks using the command line interface (CLI). This isn’t designed as an indepth guide, this is really just to try and give people a view of some of the things that you will need to be aware of. This isn’t mean’t to be “academic” or replace manuals and technical docs so it’s brief and to the point (as far as that is possible).
Major Changes for Windows People
In Windows many things are case insensitive, such as usernames. In UNIX/Linux the file system is case sensitive. Running Uname will error vs uname which will show the OS version. This means some scenarios are case sensitive (file system access is for sure) but also usernames in some systems are as well.
Distributions
Linux comes in a ton of flavours there is even a Hannah Montanna flavour. Common distibutions are:
Red Had Enterprise Linux (RHEL)
- CentOS
- Debian
- Fedora
- Ubuntu
- MINT
- ARCH
Patching and Backporting
Patching and Upgrading in Linux is a bit bit different than Windows because there’s this thing called Backporting:
You need to watch out for this as version based enumeration can lead to false positives when conducting asset enumeration and vulnerability identification through version identification. Backporting is where a security fix or patch is backported into an older version of software. So the banner may say version 7.8 however the security fixes may have been incorporated and deployed (the ones that are in 7.9) so there’s some work to do to check and validate (and also demonstrate) things are patched.
Boot Types
- BIOS (BASIC INPUT OUTPUT SYSTEM)
- UEFI
https://wiki.ubuntu.com/UEFI/SecureBoot
Boot Loaders
The most common boot loader is GRUB.
There are others such as:
- BURG
- LILO
- SYSLINUX
https://en.wikipedia.org/wiki/Comparison_of_boot_loaders
File Systems
The common files systems are:
- EXT2
- EXT3
- EXT4
Other file systems include:
- XFS
- ZFS
There are other systems that can also be used.
A common disk encryption system is LUKS:
https://www.redhat.com/sysadmin/disk-encryption-luks
Volume manaement can be handled by Logical Volume Manager (LVM). LVM allows for dynamic volume management (thin of this a bit like using DYNAMIC disks in Windows).
File System Structure
Unlike Windows GNU/Linux systems use files for everything. There’s no concept of the registry like there is in Windows. In Linux configurations, metadata and data are stored in files. Some systems/application may use databases for configurations e.g., mySQL, postgres etc.
Here’s an example from an Ubuntu system:

The following table is a summary of some common areas:
| Path | Purpose | Notes |
| / | Root | |
| /bin | Binaries for commands (Essential bins) | |
| /dev | Device files/devices | |
| /etc | System wide configuration | |
| /etc/opt | Optional Configurations | |
| /home | Home folders | |
| /lib | Libraries for binaries | |
| /media | Removable Media | |
| /mnt | Temporary File System Mount Points | |
| /opt | Software Packages | |
| /proc | A virtual file system for process and kernel usage | |
| /root | Root users home folder | |
| /run | Run-time variable data for users and daemons | |
| /sbin | System Binaries | |
| /srv | ||
| /sys | ||
| /tmp | Temporary files | |
| /usr | Read only user data | |
| /usr/bin | Non-essential binaries | |
| /usr/include | ||
| /usr/lib32 | User Libraries e.g. 32 bit | |
| /usr/local | Host specific data | |
| /usr/sbin | Non essential system binaries | |
| /usr/share | Shared data | |
| /usr/src | Source code and headers | |
| /var | Variable files e.g. log files | |
| /var/cache | Cache | |
| /var/lib/ | ||
| /var/lock | Lock files | |
| /var/log | Log files e.g. Apache, system etc. | |
| /var/mail | Mailbox data | |
| /var/opt | Optional variable data | |
| /var/run | Variable run time data | |
| /var/spool | Spools for mail and printers | |
| /var/tmp | Temporary files that remain between reboots |
Common Shells and Terminal Emulators
- Bash
- Oh My ZSH (ZSH)
- TMUX
- Konsole
- Terminator
Now when using ssh etc. the sessions are not resumable or sharable. So, you will see some cool tools here in the shape of:
- TMUX
- DVTM
- ABDUCO
- SCREEN
Package Managers
In Windows you have the Windows Installer Database and Windows Updates. In modern version of Windows you also have Windows Store and Chocolatey etc.
However, in Linux there is the concept of package managers. Common package managers include:
- DPKG
- RPM
Alongside package managers are dependancy resolvers (thanks Alex for this and other bits!)
- PACMAN
- YUM/DNF
- APT
Common Networking Protocols
- SSH
- SAMBA (Unix SMB/CIFS)
- FTP
- SFTP
- OpenLDAP
- VNC
- RDP
Desktop Window Systems (GUI)
Common guis (Windows Managers) include:
- GNOME
- KDE
There are quite a few of these get your google on!
Key Security Features
- Services
- CHROOT Jails
- Creates a false root directory for sandboxing
- Pluggable Authenticaiton Modules (PAM)
- Superuser Do/Substitute User Do (SUDO) – Like Windows Runas
- Access Control Lists
- IPTABLES
- UFW (Firewall)
- Audit D
- Malware Detection
- CLAM AV
- Remote Administration
- TELNET
- SSH
- VNC
- Remote Desktop Protocol
- SELinux
Common Administration Tasks
I’m using Ubuntu here, some distributions may use slightly different commands e.g. Arch uses PACMAN, Red Hat uses Yum.
| Task | command | Notes |
| Clear the screen | clear | Shortcut CTRL+L |
| List files | ls | |
| Switch User | su | |
| Run as root/other user | sudo | “super user do” was the traditional name now it’s “substitute user do” |
| Change directory | cd | |
| Make a directory | mk | |
| Move a file/directory | mv | |
| Remove a file | rm | |
| Remove a directory | rmdir | |
| Copy a file/folder | cp | |
| List OS Version | uname | |
| Read Help | help | |
| Read a manual | man | |
| Update Repositories | apt update | |
| Upgrade packages | apt upgrade | |
| Create an empty file | touch | |
| List directories and files | tree | |
| List disk space/usage | du | List estimated file usage |
| List | df | List file system usage |
| Change permissions | chmod | |
| Add a user | useradd | This is a very basic utility for creating users that only creates the user object |
| Add a user | adduser | This has more features and will create things such as the home drive |
| Delete a user | deluser | |
| Create a group | addgroup | |
| Delete a group | delgroup | |
| Modify a user | usermod | |
| Modify a group | groupmod | |
| List processes | ps | Common is: ps aux |
| Show the time | date | |
| Kill a process | kill | |
| List suspended processes | jobs | |
| Foreground a process | fg | |
| Edit text | vi or nano | |
| Show the current user | whoami | |
| Show the current date and time | date | date -d now |
| Display the top of a file | head | |
| Display the end of a file | tail | |
| Display a file in real time | tail -f | tail -f access.log |
| Print the working directory | pwd | |
| Set a variable | set | |
| List logged on users | w | |
| List logged on users with IP details | who | |
| Send a message to all logged on users | wall | |
| Output data to session | echo | |
| Send message to a user | write | |
| Reboot the system | reboot | |
| Power off the system | poweroff | |
| List the contents of a file | cat | |
| Ssh to another system | ssh@192.168.0.1 | You can use -I to specify private keys |
| See running processes and performance information | top |
Scheduled Tasks
Tasks in UNIX/LINUX are managed using CRON.

Parsing and Manipulating Text and Files
- cat
- sed
- awk
- grep
- find
- locate
- sort
- uniq
Daemons
A daemon is a background process, these are commonly used for services. E.g.
- SSHD is the Secure Shell Daemon.
- FTPD is the File Transfer Protocol Daemon.
System Service Control
systemctl list-units –type service
systemctl disable [service] –now
systemctl enable [service] –now
Common Networking Commands
- netstat
- ss
- tcpdump
- ufw
- iptables
- ip a (ifconfig on older systems)
- route
- nslookup
- traceroute
Common Linux Virtualisation Solutions/Platforms
- KVM
- Virtual Box
- ProxMox
- Vmware Workstation
- QEMU
Creating a new User

Using adduser we create a new user account. This utility also creates a new group and a home directory.

If we cat /etc/passwd we can see the new user:

If we cat /etc/group

We can see the new group.
If we wanted to add mrr3b00t to root we would run:

To remove the user from the group “root” we would run:

Using “su” we can switch to mRr3b00t:

File Permissions

Now the ACLs on Windows are slightly different. Let’s step through some permissions:
Permission Groups
- Owner
- Group
- All Users/Others
Permission Types
- Read (4)
- Write (2)
- Execute (1)
When we see permissions in Linux we see them in the following format:
[permission flag]rwxrwxrwx 1 owner group
Permission flags can be:
_ = nothing
d = directory
l = symbolic link
SETUID/SETGID and Sticky Bit
s = setuid or setgid (this is shown over [r] rather than in the first character)
t = sticky bit
Permissions are shown as:
Read [r] Write [w] execute[e]
These are important when we consider privilidge escalation. If these bits are set they will look like:
RWSRWSRWT
Or a variation of that pattern with S S and T
You can search for SUID bits using the following command:
| find / -perm -u=s -type f 2>/dev/null |
This will find any file (-type f) permissions with the SUID bit set and if there’s any errors e.g. access denied it will output them to /dev/null so you don’t have a screen full of errors.
Without going into detail, some binaries are set to run as root because they need high privilege access. Sometimes there are vulnerabilities in the binaries or custom bins/applications that mean you can use abuse these. On this system here’s all the files with SUID bits set.

This can also be set on directories which will affect files created:
https://web.mit.edu/rhel-doc/3/rhel-rg-en-3/s1-users-groups-private-groups.html
There is a whole subject for this but hopefully this is a quick taster on a gotcha and a potential privesc route.
Going back to our example for permissions:

In this example the /root directory is:
A directory shown by: d
The object owner (root) has read, write, and execute
the group (root) has no access.
Other users have no other permissions are set.
In our demo we are going to switch to mRr3b00t:

We touch a file “readme”

Now we switch back to root and create a new user called “QWERTY”


Now as querty we have read access to mRr3b00t’s files.

Why is that?

It’s because OTHER users have the read attribute set.
This won’t apply to all distributions but in Ubuntu this is out of the box defaults.
Let’s fix this (I’m going to set RWX and RW then RWX and RWX so you can see the change)

Here we set:
Owner 7 (rwx)
Group 7 (rw)
Others 0 (nothing)
Now we switch to qwerty and we can’t access mrreb00ts files:


We set the following on mRr3b00ts home directory:
| chmod 770 /home/mrr3b00t/ |
Remember, Owner, Group, Others.
We can change the permissions for all users home directory as follows:
| sudo chmod 750 /home/* |
If our distro isn’t protecting by default, we can set this in the /etc/adduser.conf but you can look that one up!
Scratching the Surface
Ok so we’ve started to scratch the surface and show some of the areas to consider on Linux systems. I started just writing this as I sometimes do, I’m not even sure why but then I figured people might like to read this. So here is the first bash (haha) at trying to write something. I’m going to just post this on the blog and see if people find it useful. I think there’s a better way to carve stuff like this up into exercises. Key things:
- Google is your friend!
- Man pages are your friends!
- VMs in safe environment are your friends!
- –help is your friend!
Let me know if this is useful. Haha It’s useful for me just writing this stuff down, I do as we know, have a memory like a goldfish! If you think there’s something major I’ve missed or anything that I’ve messed up please shout, I woke up at 0300 and I’m like a zombie!
I also might try making a few “how to’s” for common activities because the subject area is huge and what’s probably more useful for people is. “i want to see how to review the apache access logs and how to configure rotation and log shipping etc.”








