 Defense
Defense
Have you ever wanted to see what would occur in an environment if a worm was a make its way in? I often work with customers to show them about lateral movement from a human operated perspective however sometimes it’s useful for people to visualise this better and to demonstrate what could occur if a worm was set loose. A great tool to help with this is Infection Monkey from Guardicore (https://www.guardicore.com/
High Level View
The process steps are as follows:
- Scope Exercise
- Prepare Environment
- Deploy Infection Monkey Server (Monkey Island)
- Configure Server Credentials
- Monkey Configuration
- Release Monkey/s
- Review
- Report
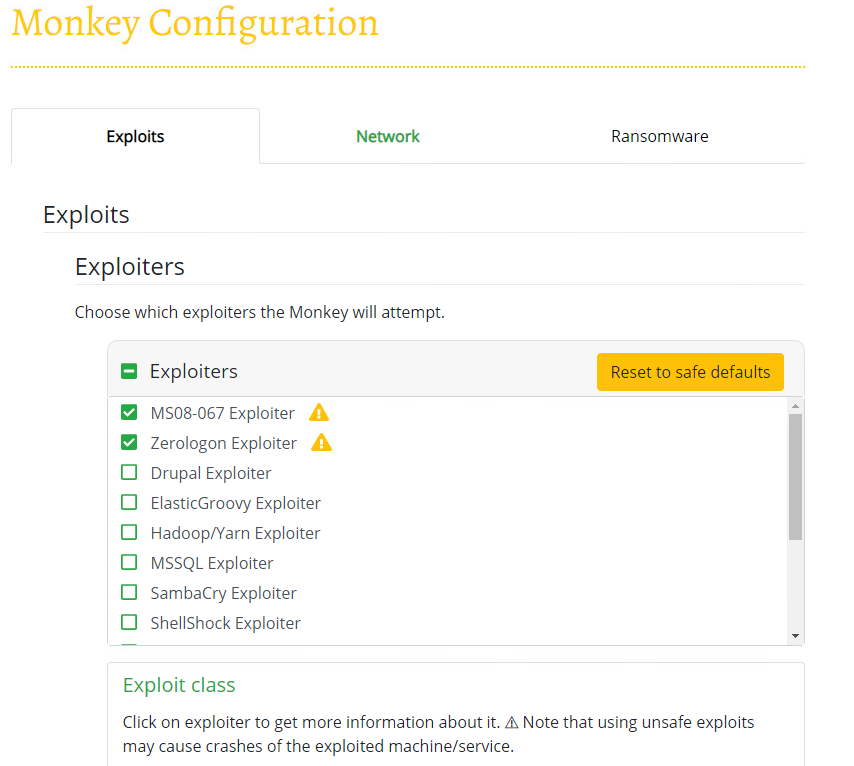
Infection Monkey includes a server side (c2) component which is deployed inside a network. In the lab example I installed it on a domain joined Windows 11 PC (with defender disabled) to act as our initial point of access. Once installed we run through some basic configuration parameters to tune the configuration to suit our environment. One thing to note is that it is quite customisable however even in its default configuration it will likely set of IDS, AV alerts and other telemetry-based alerting, alongside it has a brute force component, so it has the potential to lock out some accounts (a small number of specific usernames by default).
One configured we can then release the monkeys! Now we can do this either using the Island Server as the initial starting position or we can generate agent connection commands to run on other endpoints.
Configuration
For the lab we modified the configuration, there’s no risk as this is a physically isolated lab and as such, we have enabled risky exploits, we have also disabled exploits which are not relevant.
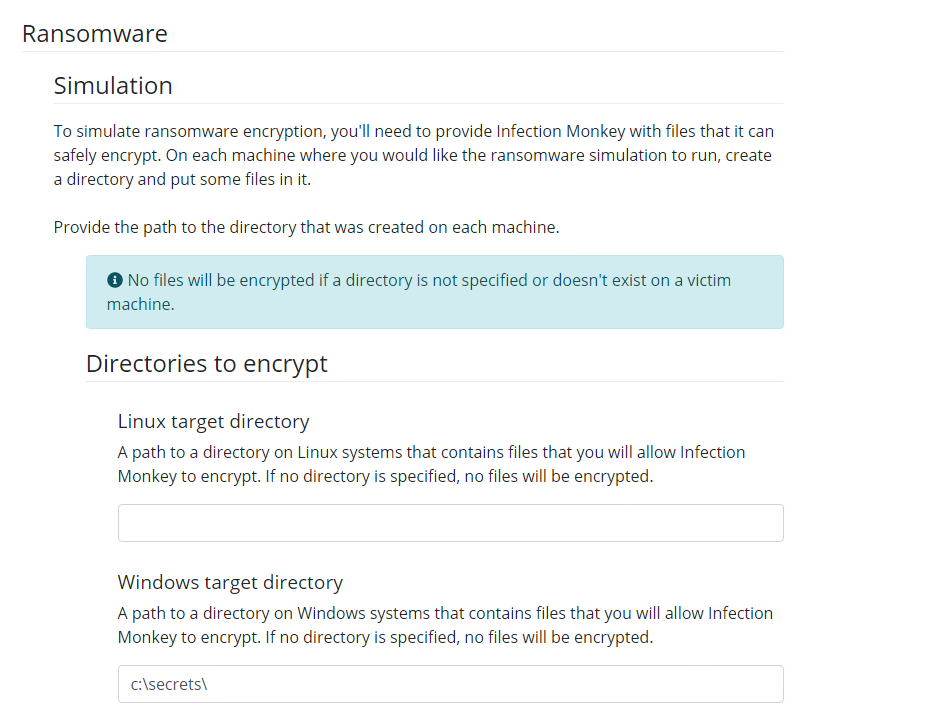
For this lab we deployed with a path specified for testing file encryption:
Release the Monkey
Once our configuration is good, we now are ready to release the monkey (Run Monkey)
Reporting
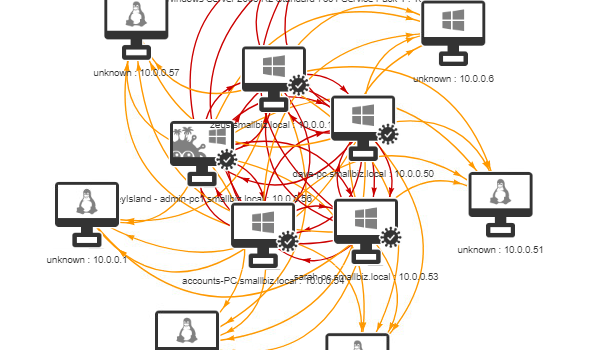
The reporting from this tool is comprehensive:
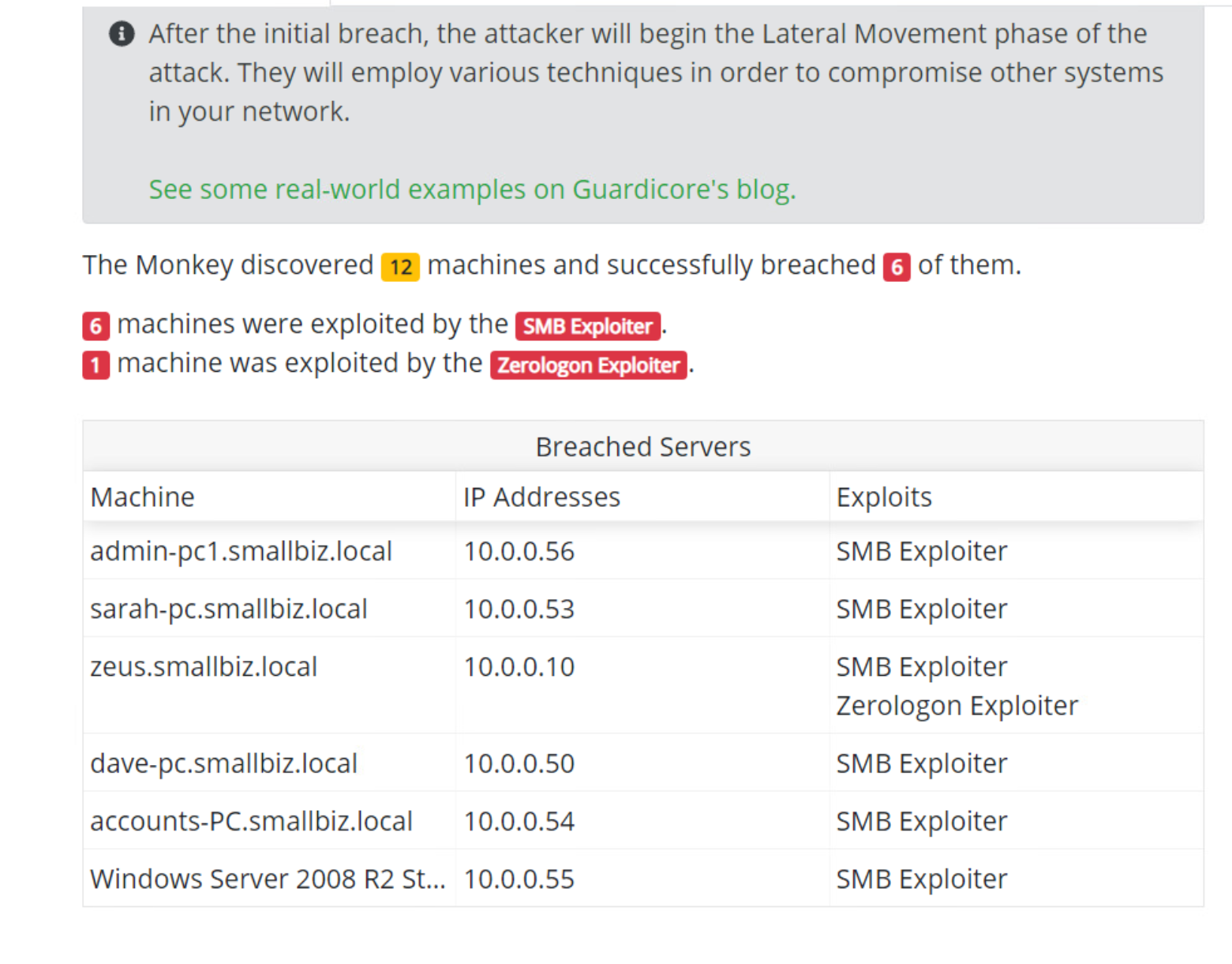
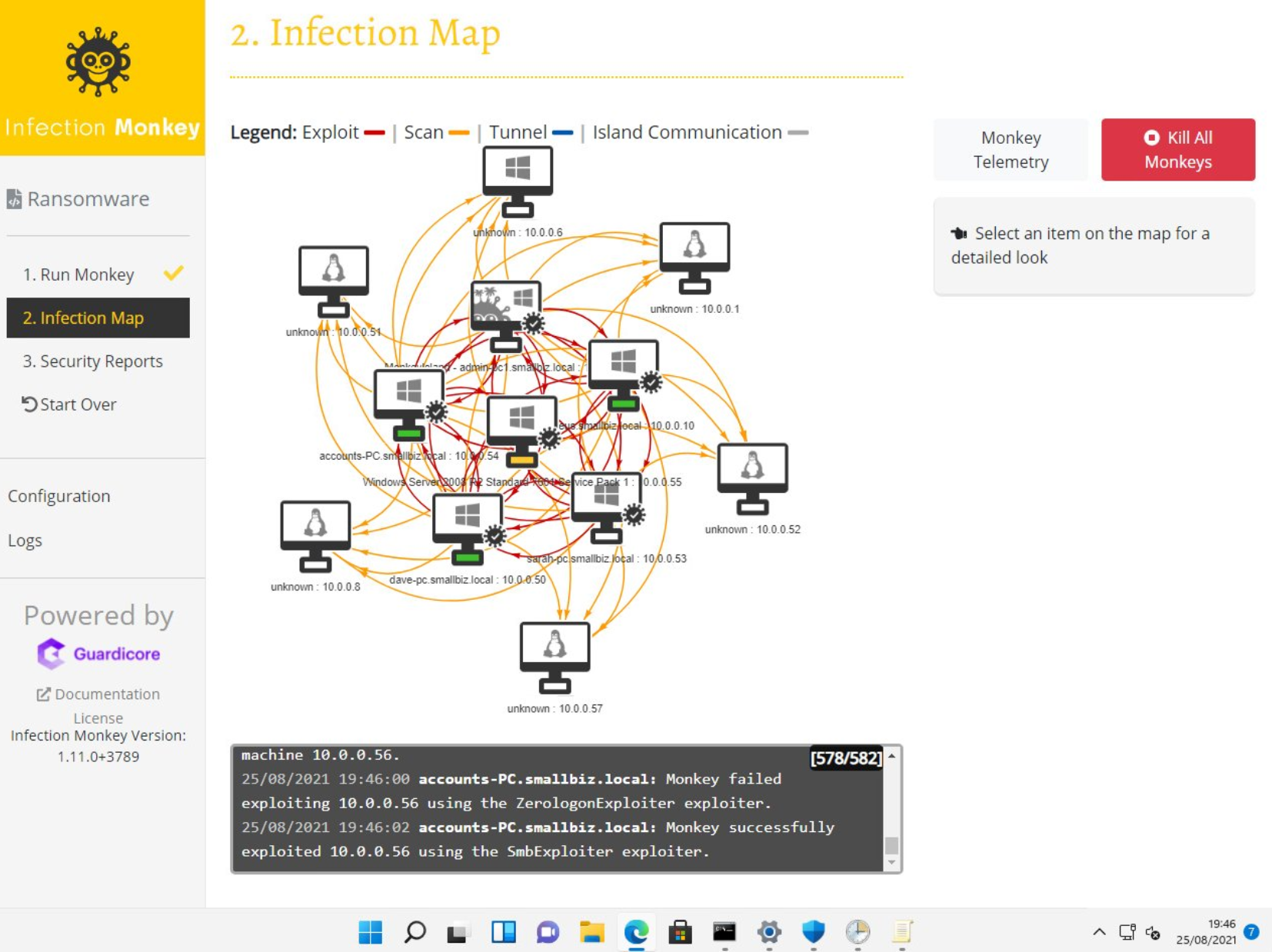
In this lab we can see that there was a great deal of lateral movement over SMB. We can also see that ZeroLogon was successful against a domain controller.
Summary
We can see from the Infection map alone that the environment has a very weak security posture (not a surprise since I built it rapidly without hardening or patching), however unfortunately this isn’t so different from a lot of networks I see. Even in defended networks, lateral movement and privilege escalation is possible I’d say about 90% of the time!
I’ve used this tool on a production network before, but before you just deploy you need to make sure you understand what the tool does, how it works and what the potential impact might be. Also, you will 100% want to ensure you have authorisation to do so. That being said this is a great tool for the kit bag, it can be used not only to find vulnerabilities, demonstrate impact but also is nice tool to see how you protect, detect, alert and respond practises hold up. This does test a specific set of vulnerabilities, so don’t stop with just these there are usually tons more than criminals can exploit!
This isn’t Skynet so it’s not going to replicate a human operated attack, it does however work as a cool tool to not only test a range of scenarios but also can be great as a risk communication tool. The reporting and style are easy to consume.
These vectors shouldn’t really be exploitable, but sadly and too often they are, ransomware both automated and human operated continues to demonstrate this to organisations all over the world. Through knowledge of offense, we can drive defensive improvements and reduce business risk, what’s great with this is we can do it with a smile knowing that a monkey helped us!






