 Defense
Defense
“And I looked and behold a pale horse: and his name that sat on him was Death, and Hell followed with him.”
Firstly, Kudos to @j0nh4t for finding this!
I woke up this morning to see twitter fun with a LPE discovered in the Razer driver installation. Basically, when you plug a Razer mouse into a Windows machine, it will download (via windows update) and execute a process as system which has user interaction. This interface includes an install path selector, with this a right click + SHIFT (LULZ) on whitespace will allow you to launch a command prompt/PowerShell window (as SYSTEM).


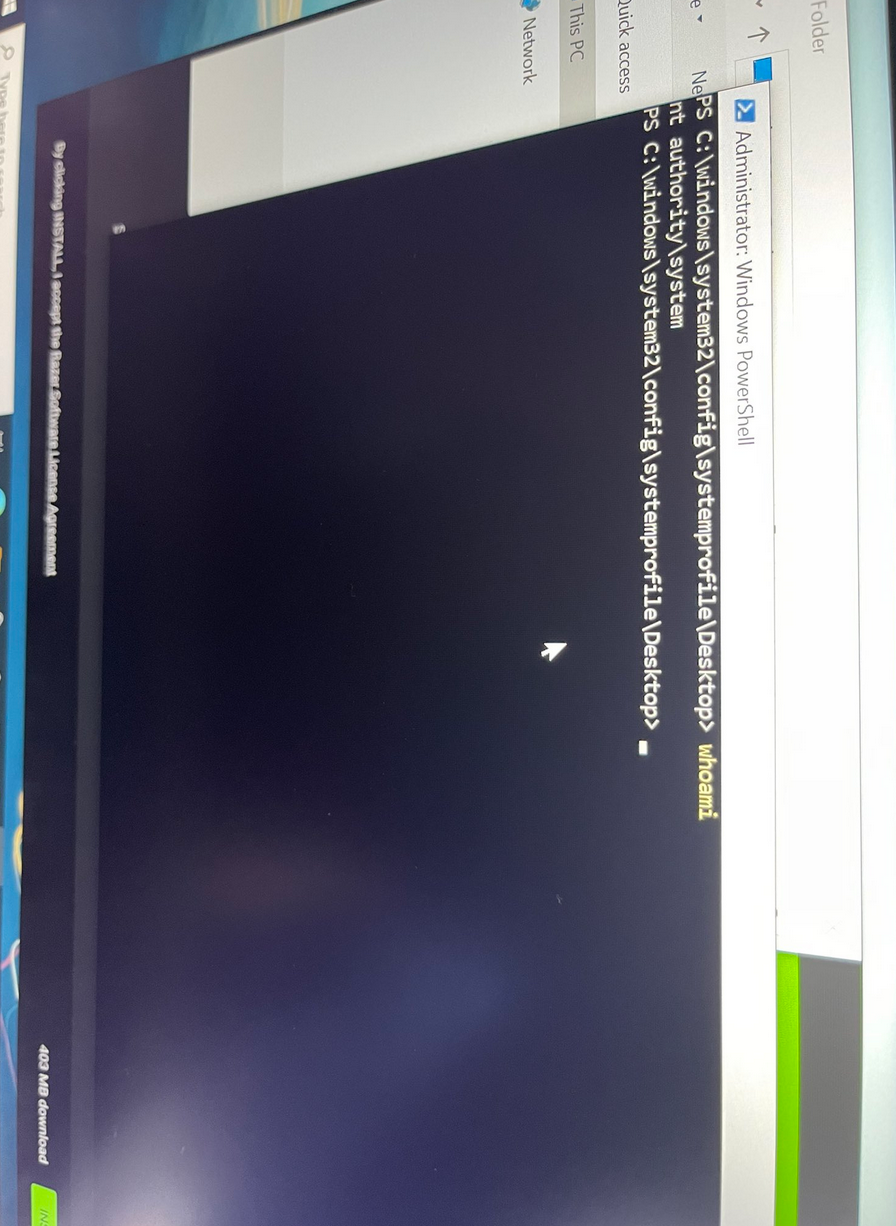
As you can see there it is. from zero to SYSTEM using only the power of a USB device. So, before everyone runs around going mad. we must think about this from a threat model perspective.
You need to be able to have physical or emulated physical access to a device. You need to be able to use a razer device or emulate it’s PNP ID. You need internet access and Windows update must be configured to allow downloading of drivers.
I’ve not tested this but you can probably avoid this by disabling driver installs via Windows update.
So, you need quite a few things in play to do this, in some environments I would be worried about this… in most I probably wouldn’t lose much sleep over this. You’ve got LAPS deployed anyway, right? Remember your threat models are yours, act if you need to.
(FYI to test this using vmware workstation you can edit the vmx file and add the following two lines:
usb.generic.allowHID = “TRUE”
usb.generic.allowLastHID = “TRUE”
you will need to have a second mouse or you will lock your device inside the vm – unless you reboot the PC)








