 Defense
Defense
Introduction
Recently I decided to do the Red Team Operator: Privilege Escalation in Windows Course by Sektor7 (thanks for the recommendation Justin!). I thought I’d write some notes but also create a quick blog covering some of the Windows fundamental areas. It’s easy to actually forget how this stuff is at a detailed level so figured it helps both myself and the world to share a snippet. I’m litterally listening to the course as I type this, I’ve just imported an OVA to vmware workstation so this is litterally live! (I’m 7 video modules in!)
There’s some key parts around Windows Security Architecture that is important to know, the course does cover this off at the start so I thought I’d share a tiny bit of my notes.Windows Security
Resources
- Files
- Registry
Resources have security descriptors and access controls lists
Kernel
Security Reference Model (SRM)
Processes
- Running processes using various access levels (Access Tokens).
- Process have an integrity level.
- Resources have an integrity level.
Processes and Threads
Processes are contained elements that can execute a program. A process can have a single thread or many threads.
Threads are a component of a process.
Integrity Levels
- Low (such as browser sandboxes)
- Medium (normal access)
- High (Admin rights)
- SYSTEM
Privileges vs Access Rights
- Privileges are where permission to run an action or activity are granted.
- Assigned to users & groups
- Access Rights are Permissions (Access rights) to access objects (e.g., files, registry, tokens, shares etc.)
- Assigned to objects
User Access Control (UAC)
- Secure Desktop
- Process Integrity Level Management
Type of Privileges
Non-Admin User (low integrity)
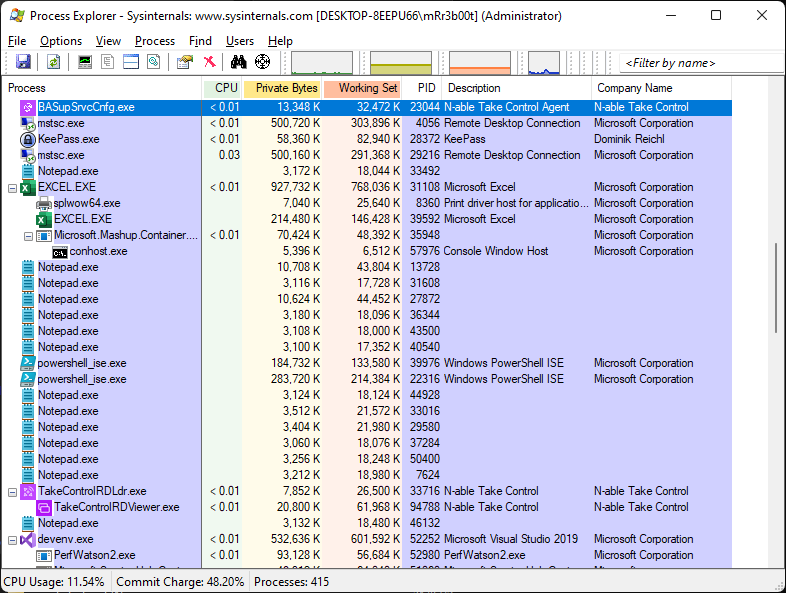
We can use Process Explorer to view this process (conhost.exe)
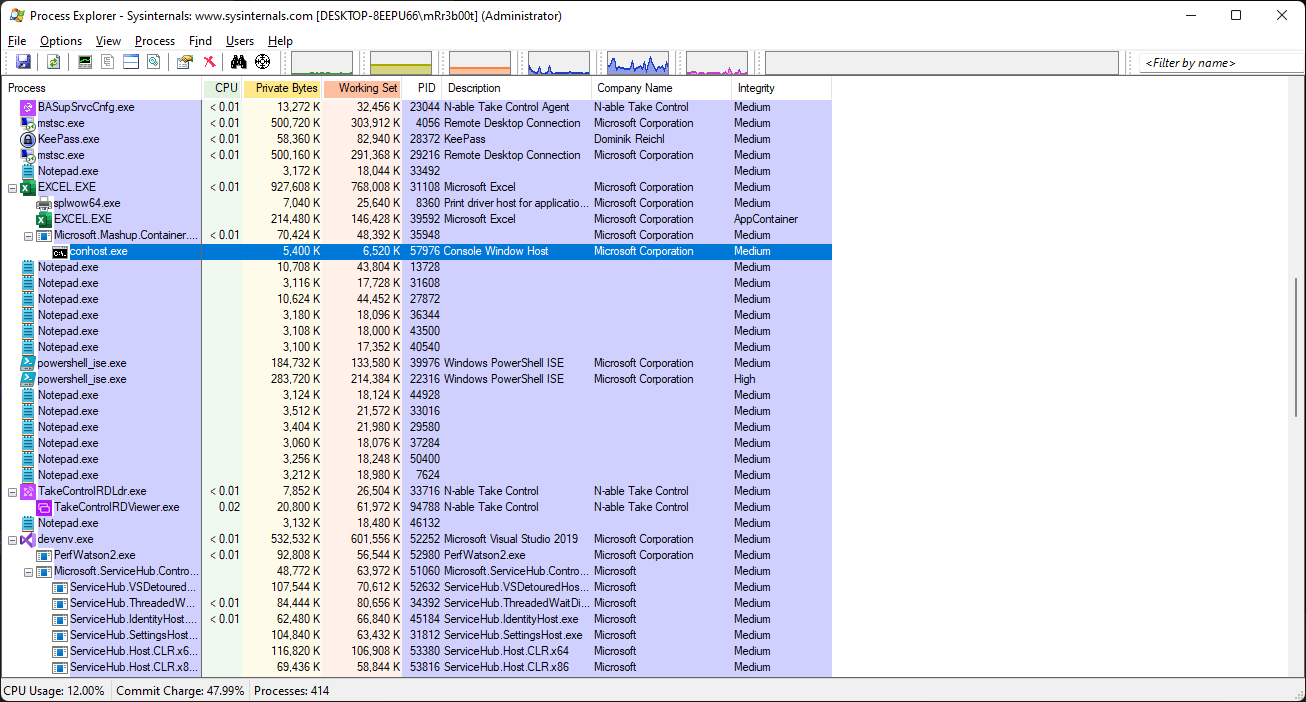
We can add the integrity level to the columns view. We can see here normal processes are loaded with medium integrity level.
Administrator Access (high integrity level)
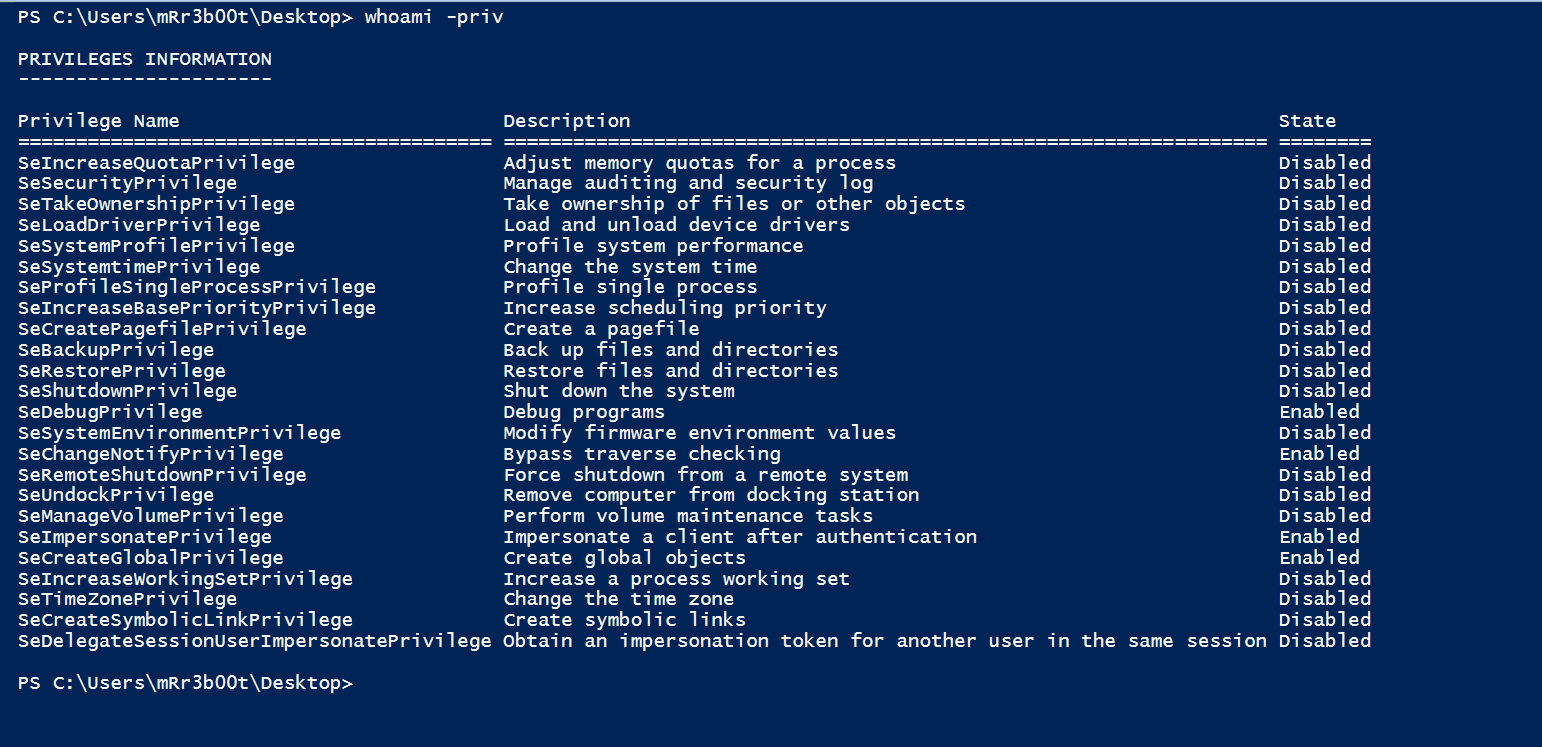
We run the same command with an elevated prompt.
![]()
We can see here that this is in a high integrity space.
Privilege Escalation
Methods
- Clear Text Passwords
- Text Files
- System Files (e.g., Unattend.xml)
- Registry
- Backups
- Registry Hives
- OneDrive, GDrive etc.
- Windows Credential Manager
- Browser Password Databases
- Windows Autologon
- Insecure Services
- Insecure Service Paths
- UAC Bypasses
- Path exploitation
- Scheduled Task Abuse
- DLL Hijacking
- Windows Installer Always Install Elevated
- Token Abuse
- Named Pipe Exploitation
The scenarios this covers are:
| Starting Point | Non-Admin | Admin | Non-Admin | Admin |
| Process Integrity | Medium | Medium | ||
| Known Password? | No Password Known | No Password | ||
| Target | Non-Admin | Admin | Admin | Admin |
| Process Integrity | Medium | Medium | High | High |
| Known Password? | Known Password | Password |
Summary
I love trying out new materials from different companies/people/groups etc. I’ve got a backlog at the minute which includes:
- Antisocial Engineer’s Training platform
- She Hacks Purple’s Application Security Training
- TCM Security PNPT
- RTO by RastaMouse
Let’s hope I can find some time to get the backlog list smaller soon!






