 Guides
Guides
From Zero to DA using ‘PetitPotam’
Introduction
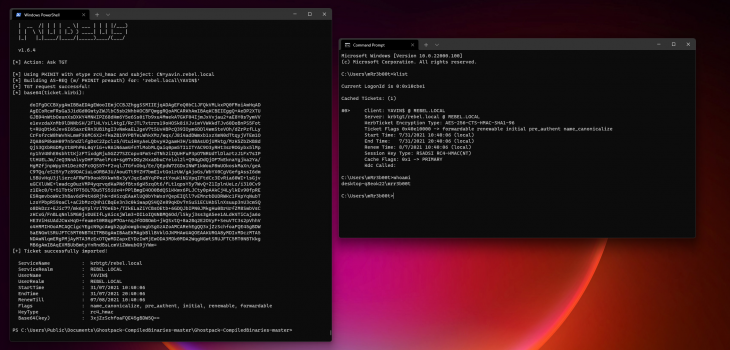
Whilst I was on ‘holiday’ (seriously even when on holiday I almost always must do some work!) a few Windows vulnerabilities were published. Great work by Gilles Lionel, Benjamin Delpy and many many others!
Lab Setup
- A Domain Controller
- A Separate ADCS Install with Web Enrolment or two DCs one with ADCS installed.
- A windows Client Device (non-domain joined)
- An attacker device (I used Kali)
You do not need any domain credentials to conduct this exploit chain, so from a network adjacent unauthenticated position you can get DA with the right circumstances (default configuration). Read more “From Zero to DA using ‘PetitPotam’”

