 Defense
Defense
Ok so John and I have been working on this for a while. We have been working with both customers and industry profesionals and there’s a common theme. Understranding the events from this incident are quite challenging because:
- We don’t have sample log output for known bad traffic
- The vulns can be used for data theft and/or backdoors (and further actions on target)
Getting guidance out so far on this has been challenging becuase:
- There is not a public full kill chain POC to do comaprisons to (i’m ok with that)
- We don’t have a pw3d server that has all the indicators from all the routes on
So to try and help people we have made a diagram which we will update as we go.
Essentially you need to perform a weighted analysis to understand if:
- You had recon only
- You had some SSRF
- YOu had SSRF that led to data theft
- You had a webshell planted
Work in profress Diagram
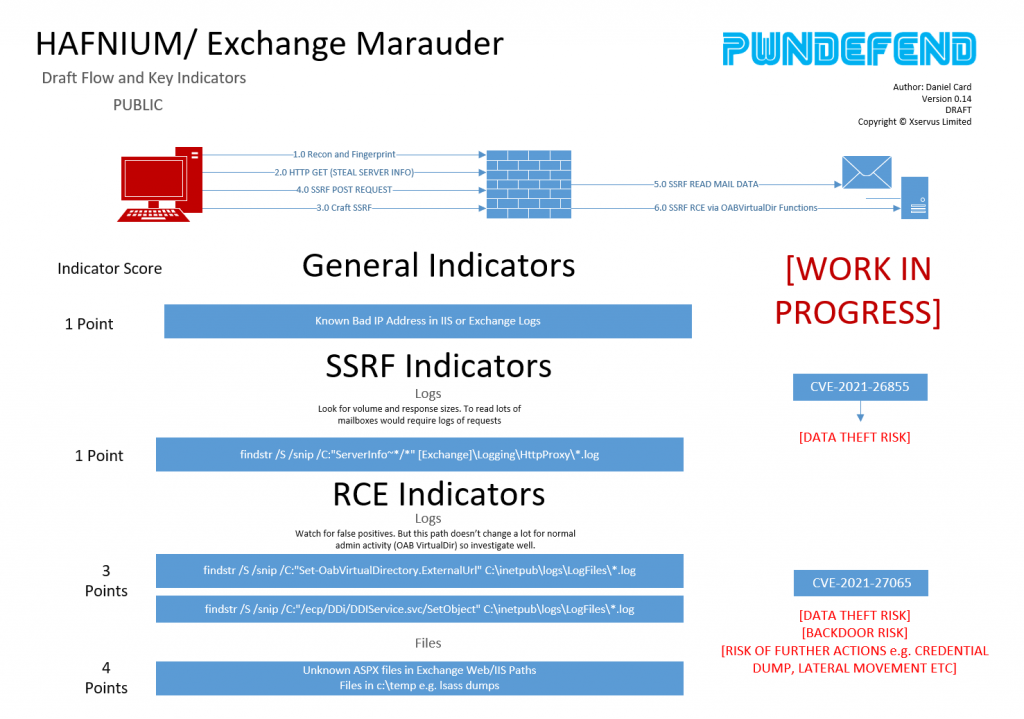
You will need to run the MS script, our script or use a SIEM etc. to get a handle on this, most sysadmins I know do NOT spent their time in these log files.
Key point – this diagram will be updated as we go. We are working on reproducting the kill chain in the lab. We haven’t got there yet but we can see what we need to do.
So check out our previous post for more info on general approach, also read the guidance from Microsoft etc. This is a fast moving scenario and its changing all the time.
- Using cyber security investments as a business enabler
- Avoiding an infinite incident response cycle!
- Disable and Remove Windows Quick Assist
- Making cyber security relatable to people
- Cyber Leadership – Real Life Incidents over the years!
Remember, just patching is NOT enough, you need to validate you are in the clear (that is NOT an easy task for most environments).
Stay posted, we’ll update on twitter/linkedin etc.
Be safe! drink water and take notes as you respond!
mRr3b00t









