 Defense
Defense
Windows DNS Server
This is really a major issues for Active Directory Domain Controllers.
CVE-2020-1350 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350
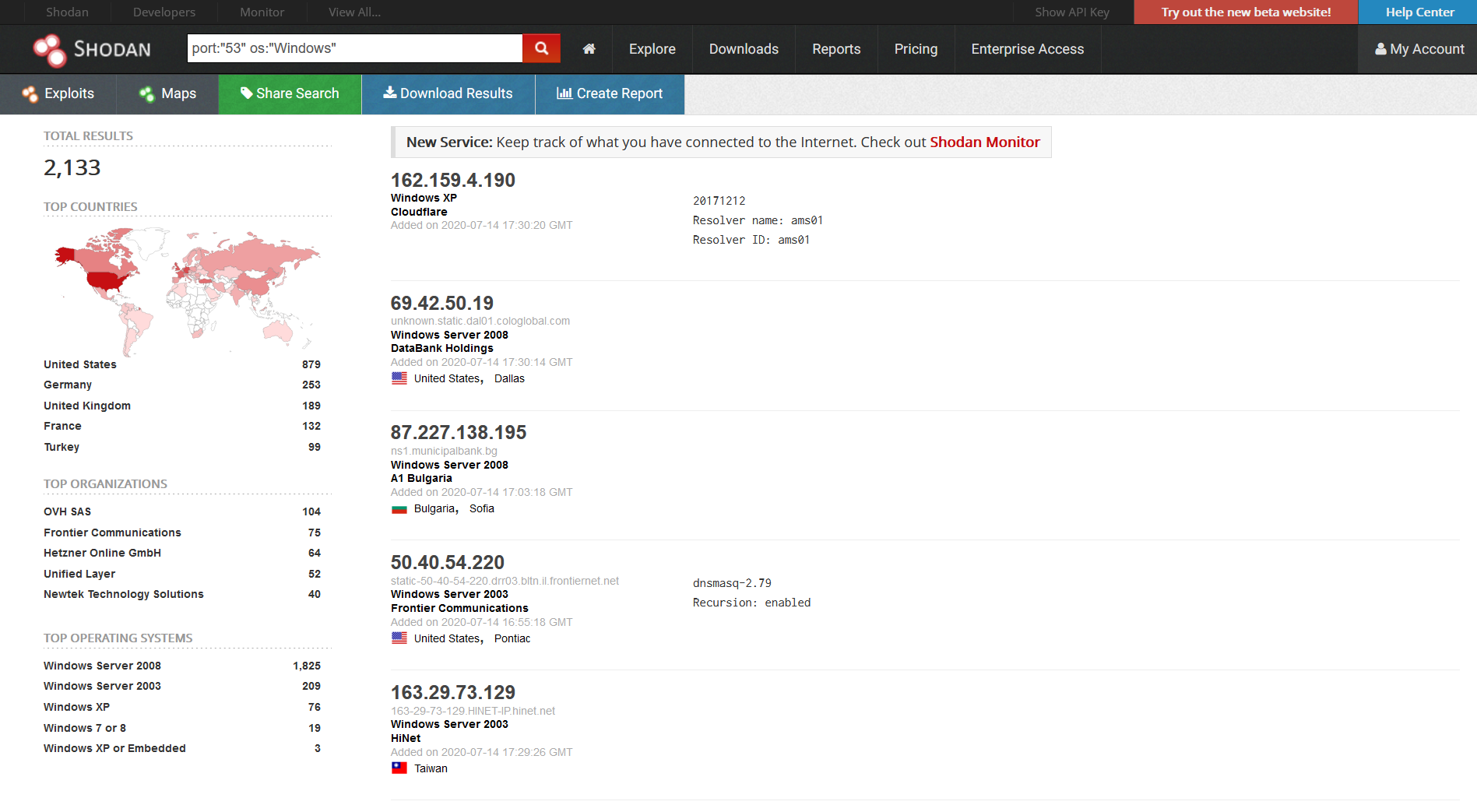
We can see there are 2,133 servers on Shodan that are exposed however this exploit doesn’t rely on exposure, a client request from inside the network to a malicious DNS server could be used to exploit the domain controller.
So basically, any Windows DNS server is vulnerable if it can forward requests to internet facing DNS services. There’s a workaround as well as deploying the patch (the workaround does not require a reboot but does require a DNS server service restart)
Given this is an RCE which likely affects domain controllers, mitigation or patching ASAP is advisable. The good news is there is currently no public exploit. The attackers also requires DNS infrastructure however that is hardly a barrier to entry for ransomare gangs and nation state actors.
And don’t forget this affects all version of Windows listed as 2003-2019 but you never know win2k might also be affected.
The workaround for this is as follows:
Workarounds
The following registry modification has been identified as a workaround for this vulnerability.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters
DWORD = TcpReceivePacketSize
Value = 0xFF00
Note: A restart of the DNS Service is required to take effect.
I’ve made a quick local workaround set of scripts, one is a batch file (why?) and one is PowerShell with a bit of detection logic. Use at own risk etc. (ideally patch)
https://github.com/mr-r3b00t/CVE-2020-1350
Fore more info on the vulnerability please see: https://research.checkpoint.com/2020/resolving-your-way-into-domain-admin-exploiting-a-17-year-old-bug-in-windows-dns-servers/
Hyper-V RemoteFX vGPU
It’s my understanding these require specific configurations to be vulnerable.
CVE-2020-1040 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1040
CVE-2020-1042 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1042
CVE-2020-1043 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1043
CVE-2020-1032 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1032
CVE-2020-1036 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1036
CVE-2020-1041 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1041
.NET Framework, SharePoint Server, and Visual Studio
CVE-2020-1147 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1147
DirectWrite
CVE-2020-1409 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1409
Windows Address Book
CVE-2020-1410 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1410
PerformancePoint Services
CVE-2020-1439 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1439
Microsoft Outlook
CVE-2020-1349 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1349
Remote Desktop Client
CVE-2020-1374 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1374
LNK
CVE-2020-1421 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1421
GDI+
CVE-2020-1435 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1435
Windows Font Library
CVE-2020-1436 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1436
VBScript
CVE-2020-1403 : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1403
ADV200008
Microsoft Guidance for Enabling Request Smuggling Filter on IIS Servers : https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/ADV200008
Summary
Another month, another set of patches, it’s key to stay on top of patching as well as ensuring that your estate operates current and supported operating systems.








